|
Chosen Plaintext Attack
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts.Ross Anderson, ''Security Engineering: A Guide to Building Dependable Distributed Systems''. The first edition (2001): http://www.cl.cam.ac.uk/~rja14/book.html The goal of the attack is to gain information that reduces the security of the encryption scheme. Modern ciphers aim to provide semantic security, also known as ''ciphertext indistinguishability under chosen-plaintext attack'', and they are therefore, by design, generally immune to chosen-plaintext attacks if correctly implemented. Introduction In a chosen-plaintext attack the Adversary (cryptography), adversary can (possibly Adaptive algorithm, adaptively) ask for the ciphertexts of arbitrary plaintext messages. This is formalized by allowing the adversary to interact with an encryption Oracle machine, oracle, viewed as a black box. The attacker’s goal is to reveal all ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Model
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a Cryptanalysis, cryptanalyst has to a system under attack when attempting to "break" an Encryption, encrypted message (also known as ''ciphertext'') generated by the system. The greater the access the cryptanalyst has to the system, the more useful information they can get to utilize for breaking the cypher. In cryptography, a sending party uses a cipher to encryption, encrypt (transform) a secret ''plaintext'' into a ''ciphertext'', which is sent over an insecure communication channel to the receiving party. The receiving party uses an inverse cipher to decryption, decrypt the ciphertext to obtain the plaintext. A secret knowledge is required to apply the inverse cipher to the ciphertext. This secret knowledge is usually a short number or string called a ''cryptographic key, key''. In a cryptographic attack a third party cryptanalyst analyzes the ciphertex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information-theoretically Secure
A cryptosystem is considered to have information-theoretic security (also called unconditional security) if the system is secure against adversaries with unlimited computing resources and time. In contrast, a system which depends on the computational cost of cryptanalysis to be secure (and thus can be broken by an attack with unlimited computation) is called computationally secure or conditionally secure. Overview An encryption protocol with information-theoretic security is impossible to break even with infinite computational power. Protocols proven to be information-theoretically secure are resistant to future developments in computing. The concept of information-theoretically secure communication was introduced in 1949 by American mathematician Claude Shannon, one of the founders of classical information theory, who used it to prove the one-time pad system was secure. Information-theoretically secure cryptosystems have been used for the most sensitive governmental communica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known-plaintext Attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Symmetric-key Algorithm
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption (also known as asymmetric-key encryption). However, symmetric-key encryption algorithms are usually better for bulk encryption. With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption. Types Symmetric-key encryption can use either stream ciphers or block ci ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seaman
Seaman may refer to: * Sailor, a member of a marine watercraft's crew * Seaman (rank), a military rank in some navies * Seaman (name) (including a list of people with the name) * ''Seaman'' (video game), a 1999 simulation video game for the Sega Dreamcast * Seaman (dog), on the Lewis and Clark Expedition * USS ''Seaman'' (DD-791), a destroyer * Seaman, Ohio, a village in the United States * Seaman, a character from ''South Park'' See also * Seaman Range, a mountain range in Nevada, United States * Seaman Reservoir, northwest of Fort Collins, Colorado, United States * Seaman High School, Kansas * Seaman's Furniture, an American chain of furniture stores * Seaman's Hospital, Hong Kong, closed in 1873 * Seaman Stadium, a sports venue in Okotoks, Alberta, Canada * Seaman Farm, Dix Hills, New York, on the National Register of Historic Places * Seamans (other) * Seeman (surname), list of people with the surname * Semen Semen, also known as seminal fluid, is a bodil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted. Overview With the advent of computing, the term ''plaintext'' expanded beyond human-readable documents to mean any data, including binary files, in a form that can be viewed or used without requiring a key or other decryption device. Information—a message, document, file, etc.—if to be communicated or stored in an unencrypted form is referred to as plaintext. Plaintext is used as input to an encryption algorithm; the output is usually termed ciphertext, particularly when the algorithm is a cipher. Codetext is less often used, and almost always only when the algorithm involved is actually a code. Some systems use multiple layers of encryption, with the output of one encryption algorithm becoming "plaintext" input for the next. Secure handling Insecure handling of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Juan Pujol García
Juan Pujol García (; 14 February 1912 – 10 October 1988), also known as Joan Pujol i García (), was a Spanish spy who acted as a double agent loyal to Great Britain against Nazi Germany during World War II, when he relocated to Britain to carry out fictitious spying activities for the Germans. He was given the codename Garbo by the British; their German counterparts codenamed him Alaric and referred to his non-existent spy network as "Arabal". After developing a loathing of political extremism of all sorts during the Spanish Civil War, Pujol decided to become a spy for Britain as a way to do something "for the good of humanity." Pujol and his wife#Seaman, Seaman (2004). p. 56 "Pujol's wife called upon the US Embassy without informing her husband" contacted the British Embassy in Madrid which rejected his offer. Undeterred, he created a false Identity (social science), identity as a fanatically pro-Nazi Spanish government official and successfully became a German agent. H ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gardening (cryptanalysis)
In cryptanalysis, gardening is the act of encouraging a target to use known plaintext in an encrypted message, typically by performing some action the target is sure to report. It was a term used during World War II at the British Government Code and Cypher School at Bletchley Park, England, for schemes to entice the Germans to include particular words, which the British called " cribs", in their encrypted messages. This term presumably came from RAF minelaying missions, or "gardening" sorties. "Gardening" was standard RAF slang for sowing mines in rivers, ports and oceans from low heights, possibly because each sea area around the European coasts was given a code-name of flowers or vegetables. The technique is claimed to have been most effective against messages produced by the German Navy's Enigma machines. If the Germans had recently swept a particular area for mines, and analysts at Bletchley Park were in need of some cribs, they might (and apparently did on several occas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enigma Machine
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the Wehrmacht, German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages. The Enigma has an electromechanical Rotor machine, rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of the 26 lights above the keyboard illuminated at each key press. If plaintext is entered, the illuminated letters are the ciphertext. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress. The security of the system depends on machine settings that were generally changed daily, based ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Royal Air Force
The Royal Air Force (RAF) is the Air force, air and space force of the United Kingdom, British Overseas Territories and Crown Dependencies. It was formed towards the end of the World War I, First World War on 1 April 1918, on the merger of the Royal Flying Corps (RFC) and the Royal Naval Air Service (RNAS). Following the Allies of World War I, Allied victory over the Central Powers in 1918, the RAF emerged as the largest air force in the world at the time. Since its formation, the RAF has played History of the Royal Air Force, a significant role in Military history of the United Kingdom, British military history. In particular, during the Second World War, the RAF established Air supremacy, air superiority over Nazi Germany's Luftwaffe during the Battle of Britain, and led the Allied strategic bombing effort. The RAF's mission is to support the objectives of the British Ministry of Defence (United Kingdom), Ministry of Defence (MOD), which are to "provide the capabilities nee ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
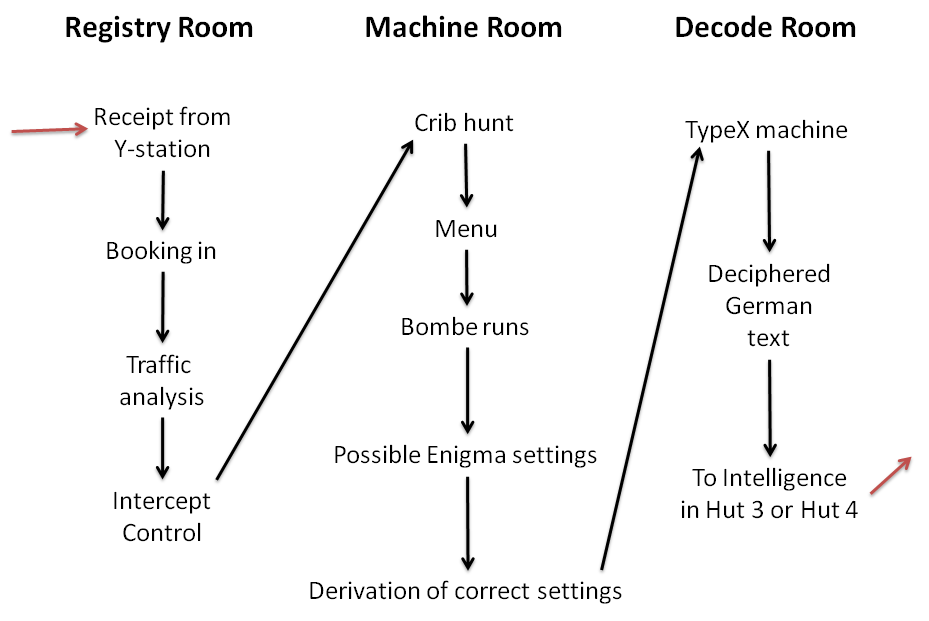
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Battle Of Midway
The Battle of Midway was a major naval battle in the Pacific Ocean theater of World War II, Pacific Theater of World War II that took place on 4–7 June 1942, six months after Japan's attack on Pearl Harbor and one month after the Battle of the Coral Sea. The Japanese Combined Fleet under the command of Isoroku Yamamoto suffered a decisive defeat by the United States Pacific Fleet, U.S. Pacific Fleet near Midway Atoll, about northwest of Oahu. Yamamoto had intended to capture Midway and lure out and destroy the U.S. Pacific Fleet, especially the aircraft carriers which had escaped damage at Pearl Harbor. Before the battle, Japan desired to extend its Pacific defense perimeter, especially after the Doolittle Raid, Doolittle air raid of Tokyo in April 1942, and to clear the seas for attacks on Midway, Fiji, Samoa, and Hawaii. A related Japanese Aleutian Islands campaign, attack on the Aleutian Islands began one day earlier, on 3 June. The Japanese strike force at Midway, known ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |