The Enigma machine is a
cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is ''encipherment''. To encipher or encode i ...
device developed and used in the early- to mid-20th century to protect
commercial, diplomatic, and military communication. It was employed extensively by
Nazi Germany
Nazi Germany, officially known as the German Reich and later the Greater German Reich, was the German Reich, German state between 1933 and 1945, when Adolf Hitler and the Nazi Party controlled the country, transforming it into a Totalit ...
during
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
, in all branches of the
German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages.
The Enigma has an electromechanical
rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of the 26 lights above the keyboard illuminated at each key press. If
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
is entered, the illuminated letters are the
ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress.
The security of the system depends on machine settings that were generally changed daily, based on secret key lists distributed in advance, and on other settings that were changed for each message. The receiving station would have to know and use the exact settings employed by the transmitting station to decrypt a message.
Although Nazi Germany introduced a series of improvements to the Enigma over the years that hampered decryption efforts,
cryptanalysis of the Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies of World War II, Allies in World War II to read substantial amounts of Morse code, Morse-coded radio communications of the Axis powers that had been enciphered using Enigm ...
enabled
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It extends from the Baltic Sea in the north to the Sudetes and Carpathian Mountains in the south, bordered by Lithuania and Russia to the northeast, Belarus and Ukrai ...
to first crack the machine as early as December 1932 and to read messages prior to and into the war. Poland's sharing of their achievements enabled the
Allies
An alliance is a relationship among people, groups, or states that have joined together for mutual benefit or to achieve some common purpose, whether or not an explicit agreement has been worked out among them. Members of an alliance are calle ...
to exploit Enigma-enciphered messages as a major source of intelligence. Many commentators say the flow of
Ultra
Ultra may refer to:
Science and technology
* Ultra (cryptography), the codename for cryptographic intelligence obtained from signal traffic in World War II
* Adobe Ultra, a vector-keying application
* Sun Ultra series, a brand of computer work ...
communications intelligence
Signals intelligence (SIGINT) is the act and field of intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly u ...
from the decrypting of Enigma,
Lorenz
Lorenz is an originally German name derived from the Roman surname Laurentius, which means "from Laurentum".
Given name
People with the given name Lorenz include:
* Prince Lorenz of Belgium (born 1955), member of the Belgian royal family by h ...
, and other ciphers shortened the war substantially and may even have altered its outcome.
History
The Enigma machine was invented by German engineer
Arthur Scherbius at the end of
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
.
The German firm Scherbius & Ritter, co-founded by Scherbius, patented ideas for a cipher machine in 1918 and began marketing the finished product under the brand name ''Enigma'' in 1923, initially targeted at commercial markets. Early models were used commercially from the early 1920s, and adopted by military and government services of several countries, most notably
Nazi Germany
Nazi Germany, officially known as the German Reich and later the Greater German Reich, was the German Reich, German state between 1933 and 1945, when Adolf Hitler and the Nazi Party controlled the country, transforming it into a Totalit ...
before and during
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
.
Several Enigma models were produced, but the
German military models, having a
plugboard
A plugboard or control panel (the term used depends on the application area) is an array of jack (connector), jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are som ...
, were the most complex. Japanese and Italian models were also in use. With its adoption (in slightly modified form) by the German Navy in 1926 and the German Army and Air Force soon after, the name ''Enigma'' became widely known in military circles. Pre-war German military planning emphasized fast, mobile forces and tactics, later known as
blitzkrieg
''Blitzkrieg'(Lightning/Flash Warfare)'' is a word used to describe a combined arms surprise attack, using a rapid, overwhelming force concentration that may consist of armored and motorized or mechanized infantry formations, together with ...
, which depended on radio communication for command and coordination. Since adversaries would likely intercept radio signals, messages had to be protected with secure encipherment. Compact and easily portable, the Enigma machine filled that need.
Breaking Enigma
Hans-Thilo Schmidt was a
German
German(s) may refer to:
* Germany, the country of the Germans and German things
**Germania (Roman era)
* Germans, citizens of Germany, people of German ancestry, or native speakers of the German language
** For citizenship in Germany, see also Ge ...
who spied for the
French, obtaining access to German cipher materials that included the daily keys used in September and October 1932. Those keys included the plugboard settings. The French passed the material to
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It extends from the Baltic Sea in the north to the Sudetes and Carpathian Mountains in the south, bordered by Lithuania and Russia to the northeast, Belarus and Ukrai ...
. Around December 1932,
Marian Rejewski
Marian Adam Rejewski (; 16 August 1905 – 13 February 1980) was a Polish people, Polish mathematician and Cryptography, cryptologist who in late 1932 reconstructed the sight-unseen German military Enigma machine, Enigma cipher machine, aided ...
, a Polish mathematician and
cryptologist
This is a list of cryptographers. Cryptography is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
Pre twentieth century
* Al-Khalil ibn Ahmad al-Farahidi: wrote a (now lost) book ...
at the
Polish Cipher Bureau, used the theory of permutations, and flaws in the German military-message encipherment procedures, to break message keys of the plugboard Enigma machine. Rejewski used the French supplied material and the message traffic that took place in September and October to solve for the unknown rotor wiring. Consequently, the Polish mathematicians were able to build their own Enigma machines, dubbed "
Enigma doubles". Rejewski was aided by fellow mathematician-cryptologists
Jerzy Różycki and
Henryk Zygalski, both of whom had been recruited with Rejewski from
Poznań University, which had been selected for its students' knowledge of the German language, since that area was held by
Germany
Germany, officially the Federal Republic of Germany, is a country in Central Europe. It lies between the Baltic Sea and the North Sea to the north and the Alps to the south. Its sixteen States of Germany, constituent states have a total popu ...
prior to World War I. The Polish Cipher Bureau developed techniques to defeat the plugboard and find all components of the daily key, which enabled the Cipher Bureau to read German Enigma messages starting from January 1933.
Over time, the German cryptographic procedures improved, and the Cipher Bureau developed techniques and designed mechanical devices to continue reading Enigma traffic. As part of that effort, the Poles exploited quirks of the rotors, compiled catalogues, built a
cyclometer (invented by Rejewski) to help make a catalogue with 100,000 entries, invented and produced
Zygalski sheets, and built the electromechanical cryptologic
''bomba'' (invented by Rejewski) to search for rotor settings. In 1938 the Poles had six ''bomby'' (plural of ''bomba''), but when that year the Germans added two more rotors, ten times as many ''bomby'' would have been needed to read the traffic.
On 26 and 27 July 1939, in
Pyry, just south of
Warsaw
Warsaw, officially the Capital City of Warsaw, is the capital and List of cities and towns in Poland, largest city of Poland. The metropolis stands on the Vistula, River Vistula in east-central Poland. Its population is officially estimated at ...
, the Poles initiated French and British
military intelligence
Military intelligence is a military discipline that uses information collection and analysis List of intelligence gathering disciplines, approaches to provide guidance and direction to assist Commanding officer, commanders in decision making pr ...
representatives into the Polish
Enigma-decryption techniques and equipment, including Zygalski sheets and the cryptologic bomb, and promised each delegation a Polish-reconstructed Enigma (the devices were soon delivered).
In September 1939, British Military Mission 4, which included
Colin Gubbins and
Vera Atkins, went to Poland, intending to evacuate cipher-breakers
Marian Rejewski
Marian Adam Rejewski (; 16 August 1905 – 13 February 1980) was a Polish people, Polish mathematician and Cryptography, cryptologist who in late 1932 reconstructed the sight-unseen German military Enigma machine, Enigma cipher machine, aided ...
,
Jerzy Różycki, and
Henryk Zygalski from the country. The cryptologists, however, had been evacuated by their own superiors into Romania, at the time a Polish-allied country. On the way, for security reasons, the Polish Cipher Bureau personnel had deliberately destroyed their records and equipment. From Romania they traveled on to France, where they resumed their cryptological work, collaborating by teletype with the
British
British may refer to:
Peoples, culture, and language
* British people, nationals or natives of the United Kingdom, British Overseas Territories and Crown Dependencies.
* British national identity, the characteristics of British people and culture ...
, who began work on decrypting German Enigma messages, using the Polish equipment and techniques.
Gordon Welchman
William Gordon Welchman OBE (15 June 1906 – 8 October 1985) was an English mathematician. During World War II, he worked at Britain's secret decryption centre at Bletchley Park, where he was one of the most important contributors. In 1948, a ...
, who became head of
Hut 6 at Bletchley Park, wrote: "Hut 6
Ultra
Ultra may refer to:
Science and technology
* Ultra (cryptography), the codename for cryptographic intelligence obtained from signal traffic in World War II
* Adobe Ultra, a vector-keying application
* Sun Ultra series, a brand of computer work ...
would never have got off the ground if we had not learned from the Poles, in the nick of time, the details both of the German military version of the commercial Enigma machine, and of the operating procedures that were in use." The Polish transfer of theory and technology at Pyry formed the crucial basis for the subsequent World War II British Enigma-decryption effort at
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the S ...
, where Welchman worked.
During the war, British cryptologists decrypted a vast number of messages enciphered on Enigma. The intelligence gleaned from this source, codenamed "
Ultra
Ultra may refer to:
Science and technology
* Ultra (cryptography), the codename for cryptographic intelligence obtained from signal traffic in World War II
* Adobe Ultra, a vector-keying application
* Sun Ultra series, a brand of computer work ...
" by the British, was a substantial aid to the
Allied war effort.
Though Enigma had some cryptographic weaknesses, in practice it was German procedural flaws, operator mistakes, failure to systematically introduce changes in encipherment procedures, and Allied capture of key tables and hardware that, during the war, enabled Allied cryptologists to succeed.
The
Abwehr
The (German language, German for ''resistance'' or ''defence'', though the word usually means ''counterintelligence'' in a military context) ) was the German military intelligence , military-intelligence service for the ''Reichswehr'' and the ...
used different versions of Enigma machines. In November 1942, during
Operation Torch
Operation Torch (8–16 November 1942) was an Allies of World War II, Allied invasion of French North Africa during the Second World War. Torch was a compromise operation that met the British objective of securing victory in North Africa whil ...
, a machine was captured which had no plugboard and the three rotors had been changed to rotate 11, 15, and 19 times rather than once every 26 letters, plus a plate on the left acted as a fourth rotor.
The Abwehr code had been broken on 8 December 1941 by
Dilly Knox
Alfred Dillwyn "Dilly" Knox, CMG (23 July 1884 – 27 February 1943) was an English classics scholar and papyrologist at King's College, Cambridge and a codebreaker. As a member of the Room 40 codebreaking unit he helped decrypt the Zimme ...
. Agents sent messages to the Abwehr in a simple code which was then sent on using an Enigma machine. The simple codes were broken and helped break the daily Enigma cipher. This breaking of the code enabled the
Double-Cross System
The Double-Cross System or XX System was a World War II counter-espionage and deception operation of the British Security Service ( MI5). Nazi agents in Britain – real and false – were captured, turned themselves in or simply announced themse ...
to operate.
From October 1944, the German Abwehr used the
Schlüsselgerät 41 in limited quantities.
Design
Like other rotor machines, the Enigma machine is a combination of mechanical and electrical subsystems. The mechanical subsystem consists of a
keyboard; a set of rotating disks called ''rotors'' arranged adjacently along a
spindle; one of various stepping components to turn at least one rotor with each key press, and a series of lamps, one for each letter. These design features are the reason that the Enigma machine was originally referred to as the rotor-based cipher machine during its intellectual inception in 1915.
Electrical pathway

An electrical pathway is a route for current to travel. By manipulating this phenomenon the Enigma machine was able to scramble messages.
The mechanical parts act by forming a varying
electrical circuit
An electrical network is an interconnection of electrical components (e.g., battery (electricity), batteries, resistors, inductors, capacitors, switches, transistors) or a model of such an interconnection, consisting of electrical elements (e. ...
. When a key is pressed, one or more rotors rotate on the spindle. On the sides of the rotors are a series of electrical contacts that, after rotation, line up with contacts on the other rotors or fixed wiring on either end of the spindle. When the rotors are properly aligned, each key on the keyboard is connected to a unique electrical pathway through the series of contacts and internal wiring. Current, typically from a battery, flows through the pressed key, into the newly configured set of circuits and back out again, ultimately lighting one display
lamp, which shows the output letter. For example, when encrypting a message starting ''ANX...'', the operator would first press the ''A'' key, and the ''Z'' lamp might light, so ''Z'' would be the first letter of the
ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
. The operator would next press ''N'', and then ''X'' in the same fashion, and so on.

Current flows from the battery (1) through a depressed bi-directional keyboard switch (2) to the plugboard (3). Next, it passes through the (unused in this instance, so shown closed) plug "A" (3) via the entry wheel (4), through the wiring of the three (Wehrmacht Enigma) or four (''
Kriegsmarine
The (, ) was the navy of Nazi Germany from 1935 to 1945. It superseded the Imperial German Navy of the German Empire (1871–1918) and the inter-war (1919–1935) of the Weimar Republic. The was one of three official military branch, branche ...
'' M4 and ''Abwehr'' variants) installed rotors (5), and enters the reflector (6). The reflector returns the current, via an entirely different path, back through the rotors (5) and entry wheel (4), proceeding through plug "S" (7) connected with a cable (8) to plug "D", and another bi-directional switch (9) to light the appropriate lamp.
[Rijmenants, Dirk]
Technical details of the Enigma machine
Cipher Machines & Cryptology
The repeated changes of electrical path through an Enigma scrambler implement a
polyalphabetic substitution cipher that provides Enigma's security. The diagram on the right shows how the electrical pathway changes with each key depression, which causes rotation of at least the right-hand rotor. Current passes into the set of rotors, into and back out of the reflector, and out through the rotors again. The greyed-out lines are other possible paths within each rotor; these are hard-wired from one side of each rotor to the other. The letter ''A'' encrypts differently with consecutive key presses, first to ''G'', and then to ''C''. This is because the right-hand rotor steps (rotates one position) on each key press, sending the signal on a completely different route. Eventually other rotors step with a key press.
Rotors

The rotors (alternatively ''wheels'' or ''drums'', ''Walzen'' in German) form the heart of an Enigma machine. Each rotor is a disc approximately in diameter made from
Ebonite or
Bakelite
Bakelite ( ), formally , is a thermosetting polymer, thermosetting phenol formaldehyde resin, formed from a condensation reaction of phenol with formaldehyde. The first plastic made from synthetic components, it was developed by Belgian chemist ...
with 26
brass
Brass is an alloy of copper and zinc, in proportions which can be varied to achieve different colours and mechanical, electrical, acoustic and chemical properties, but copper typically has the larger proportion, generally copper and zinc. I ...
, spring-loaded,
electrical contact
An electrical contact is an Electronic component, electrical circuit component found in electrical switches, relays, Electrical connector, connectors and circuit breakers. Each contact is a piece of electrically conductive material, typically meta ...
pins arranged in a circle on one face, with the other face housing 26 corresponding electrical contacts in the form of circular plates. The pins and contacts represent the
alphabet
An alphabet is a standard set of letter (alphabet), letters written to represent particular sounds in a spoken language. Specifically, letters largely correspond to phonemes as the smallest sound segments that can distinguish one word from a ...
— typically the 26 letters A–Z, as will be assumed for the rest of this description. When the rotors are mounted side by side on the spindle, the pins of one rotor rest against the plate contacts of the neighbouring rotor, forming an electrical connection. Inside the body of the rotor, 26 wires connect each pin on one side to a contact on the other in a complex pattern. Most of the rotors are identified by Roman numerals, and each issued copy of rotor I, for instance, is wired identically to all others. The same is true for the special thin beta and gamma rotors used in the
M4 naval variant.
By itself, a rotor performs only a very simple type of
encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the inf ...
, a simple
substitution cipher
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single letters (the most common), pairs of letters, t ...
. For example, the pin corresponding to the letter ''E'' might be wired to the contact for letter ''T'' on the opposite face, and so on. Enigma's security comes from using several rotors in series (usually three or four) and the regular stepping movement of the rotors, thus implementing a polyalphabetic substitution cipher.
Each rotor can be set to one of 26 starting positions when placed in an Enigma machine. After insertion, a rotor can be turned to the correct position by hand, using the grooved finger-wheel which protrudes from the internal Enigma cover when closed. In order for the operator to know the rotor's position, each has an ''alphabet tyre'' (or letter ring) attached to the outside of the rotor disc, with 26 characters (typically letters); one of these is visible through the window for that slot in the cover, thus indicating the rotational position of the rotor. In early models, the alphabet ring was fixed to the rotor disc. A later improvement was the ability to adjust the alphabet ring relative to the rotor disc. The position of the ring was known as the ''Ringstellung'' ("ring setting"), and that setting was a part of the initial setup needed prior to an operating session. In modern terms it was a part of the
initialization vector
In cryptography, an initialization vector (IV) or starting variable is an input to a cryptographic primitive being used to provide the initial state. The IV is typically required to be random or pseudorandom, but sometimes an IV only needs to be un ...
.

Each rotor contains one or more notches that control rotor stepping. In the military variants, the notches are located on the alphabet ring.
The Army and Air Force Enigmas were used with several rotors, initially three. On 15 December 1938, this changed to five, from which three were chosen for a given session. Rotors were marked with
Roman numerals
Roman numerals are a numeral system that originated in ancient Rome and remained the usual way of writing numbers throughout Europe well into the Late Middle Ages. Numbers are written with combinations of letters from the Latin alphabet, eac ...
to distinguish them: I, II, III, IV and V, all with single turnover notches located at different points on the alphabet ring. This variation was probably intended as a security measure, but ultimately allowed the Polish
Clock Method and British
Banburismus
Banburismus was a Cryptanalysis, cryptanalytic process developed by Alan Turing at Bletchley Park in United Kingdom, Britain during the Second World War. It was used by Bletchley Park's Hut 8 to help break German ''Kriegsmarine'' (naval) message ...
attacks.
The Naval version of the ''
Wehrmacht
The ''Wehrmacht'' (, ) were the unified armed forces of Nazi Germany from 1935 to 1945. It consisted of the German Army (1935–1945), ''Heer'' (army), the ''Kriegsmarine'' (navy) and the ''Luftwaffe'' (air force). The designation "''Wehrmac ...
'' Enigma had always been issued with more rotors than the other services: At first six, then seven, and finally eight. The additional rotors were marked VI, VII and VIII, all with different wiring, and had two notches, resulting in more frequent turnover. The four-rotor Naval Enigma (M4) machine accommodated an extra rotor in the same space as the three-rotor version. This was accomplished by replacing the original reflector with a thinner one and by adding a thin fourth rotor. That fourth rotor was one of two types, ''Beta'' or ''Gamma'', and never stepped, but could be manually set to any of 26 positions. One of the 26 made the machine perform identically to the three-rotor machine.
Stepping
To avoid merely implementing a simple (solvable) substitution cipher, every key press caused one or more rotors to step by one twenty-sixth of a full rotation, before the electrical connections were made. This changed the substitution alphabet used for encryption, ensuring that the cryptographic substitution was different at each new rotor position, producing a more formidable polyalphabetic substitution cipher. The stepping mechanism varied slightly from model to model. The right-hand rotor stepped once with each keystroke, and other rotors stepped less frequently.
Turnover
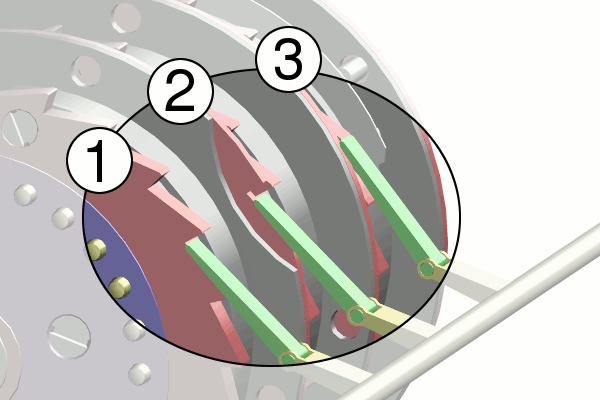
The advancement of a rotor other than the left-hand one was called a ''turnover'' by the British. This was achieved by a
ratchet and pawl mechanism. Each rotor had a ratchet with 26 teeth and every time a key was pressed, the set of spring-loaded pawls moved forward in unison, trying to engage with a ratchet. The alphabet ring of the rotor to the right normally prevented this. As this ring rotated with its rotor, a notch machined into it would eventually align itself with the pawl, allowing it to engage with the ratchet, and advance the rotor on its left. The right-hand pawl, having no rotor and ring to its right, stepped its rotor with every key depression.
For a single-notch rotor in the right-hand position, the middle rotor stepped once for every 26 steps of the right-hand rotor. Similarly for rotors two and three. For a two-notch rotor, the rotor to its left would turn over twice for each rotation.
The first five rotors to be introduced (I–V) contained one notch each, while the additional naval rotors VI, VII and VIII each had two notches. The position of the notch on each rotor was determined by the letter ring which could be adjusted in relation to the core containing the interconnections. The points on the rings at which they caused the next wheel to move were as follows.
The design also included a feature known as ''double-stepping''. This occurred when each pawl aligned with both the ratchet of its rotor and the rotating notched ring of the neighbouring rotor. If a pawl engaged with a ratchet through alignment with a notch, as it moved forward it pushed against both the ratchet and the notch, advancing both rotors. In a three-rotor machine, double-stepping affected rotor two only. If, in moving forward, the ratchet of rotor three was engaged, rotor two would move again on the subsequent keystroke, resulting in two consecutive steps. Rotor two also pushes rotor one forward after 26 steps, but since rotor one moves forward with every keystroke anyway, there is no double-stepping.
This double-stepping caused the rotors to deviate from
odometer
An odometer or odograph is an instrument used for measuring the distance traveled by a vehicle, such as a bicycle or car. The device may be electronic, mechanical, or a combination of the two (electromechanical). The noun derives from ancient Gr ...
-style regular motion.
With three wheels and only single notches in the first and second wheels, the machine had a period of 26×25×26 = 16,900 (not 26×26×26, because of double-stepping).
Historically, messages were limited to a few hundred letters, and so there was no chance of repeating any combined rotor position during a single session, denying cryptanalysts valuable clues.
To make room for the Naval fourth rotors, the reflector was made much thinner. The fourth rotor fitted into the space made available. No other changes were made, which eased the changeover. Since there were only three pawls, the fourth rotor never stepped, but could be manually set into one of 26 possible positions.
A device that was designed, but not implemented before the war's end, was the ''Lückenfüllerwalze'' (gap-fill wheel) that implemented irregular stepping. It allowed field configuration of notches in all 26 positions. If the number of notches was a
relative prime of 26 and the number of notches were different for each wheel, the stepping would be more unpredictable. Like the Umkehrwalze-D it also allowed the internal wiring to be reconfigured.
Entry wheel
The current entry wheel (''Eintrittswalze'' in German), or entry
stator
The stator is the stationary part of a rotary system, found in electric generators, electric motors, sirens, mud motors, or biological rotors (such as bacterial flagella or ATP synthase). Energy flows through a stator to or from the rotat ...
, connects the
plugboard
A plugboard or control panel (the term used depends on the application area) is an array of jack (connector), jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are som ...
to the rotor assembly. If the plugboard is not present, the entry wheel instead connects the keyboard and lampboard to the rotor assembly. While the exact wiring used is of comparatively little importance to security, it proved an obstacle to Rejewski's progress during his study of the rotor wirings. The commercial Enigma connects the keys in the order of their sequence on a
QWERTZ
The QWERTZ ( ) QWERTZU ( ), or QWERTZUIOP keyboard is a typewriter and keyboard layout widely used in Central and Southeast Europe. The name comes from the first six letters at the top left of the keyboard: ( ).
Overview
The main differ ...
keyboard: ''Q''→''A'', ''W''→''B'', ''E''→''C'' and so on. The military Enigma connects them in straight alphabetical order: ''A''→''A'', ''B''→''B'', ''C''→''C'', and so on. It took inspired guesswork for Rejewski to penetrate the modification.
Reflector

With the exception of models ''A'' and ''B'', the last rotor came before a 'reflector' (German: ''Umkehrwalze'', meaning 'reversal rotor'), a patented feature
unique to Enigma among the period's various rotor machines. The reflector connected outputs of the last rotor in pairs, redirecting current back through the rotors by a different route. The reflector ensured that Enigma would be
self-reciprocal; thus, with two identically configured machines, a message could be encrypted on one and decrypted on the other, without the need for a bulky mechanism to switch between encryption and decryption modes. The reflector allowed a more compact design, but it also gave Enigma the property that no letter ever encrypted to itself. This was a severe cryptological flaw that was subsequently exploited by codebreakers.
In Model 'C', the reflector could be inserted in one of two different positions. In Model 'D', the reflector could be set in 26 possible positions, although it did not move during encryption. In the ''Abwehr'' Enigma, the reflector stepped during encryption in a manner similar to the other wheels.
In the German Army and Air Force Enigma, the reflector was fixed and did not rotate; there were four versions. The original version was marked 'A', and was replaced by ''Umkehrwalze B'' on 1 November 1937. A third version, ''Umkehrwalze C'' was used briefly in 1940, possibly by mistake, and was solved by
Hut 6. The fourth version, first observed on 2 January 1944, had a rewireable reflector, called ''Umkehrwalze D'', nick-named Uncle Dick by the British, allowing the Enigma operator to alter the connections as part of the key settings.
Plugboard

The plugboard (''Steckerbrett'' in German) permitted variable wiring that could be reconfigured by the operator. It was introduced on German Army versions in 1928, and was soon adopted by the ''
Reichsmarine'' (German Navy). The plugboard contributed more cryptographic strength than an extra rotor, as it had 150 trillion possible settings (see below).
Enigma without a plugboard (known as ''unsteckered Enigma'') could be solved relatively straightforwardly using hand methods; these techniques were generally defeated by the plugboard, driving Allied cryptanalysts to develop special machines to solve it.
A cable placed onto the plugboard connected letters in pairs; for example, ''E'' and ''Q'' might be a steckered pair. The effect was to swap those letters before and after the main rotor scrambling unit. For example, when an operator pressed ''E'', the signal was diverted to ''Q'' before entering the rotors. Up to 13 steckered pairs might be used at one time, although only 10 were normally used.
Current flowed from the keyboard through the plugboard, and proceeded to the entry-rotor or ''Eintrittswalze''. Each letter on the plugboard had two jacks. Inserting a plug disconnected the upper jack (from the keyboard) and the lower jack (to the entry-rotor) of that letter. The plug at the other end of the crosswired cable was inserted into another letter's jacks, thus switching the connections of the two letters.
Accessories

Other features made various Enigma machines more secure or more convenient.
''Schreibmax''
Some M4 Enigmas used the ''Schreibmax'', a small
printer that could print the 26 letters on a narrow paper ribbon. This eliminated the need for a second operator to read the lamps and transcribe the letters. The ''Schreibmax'' was placed on top of the Enigma machine and was connected to the lamp panel. To install the printer, the lamp cover and light bulbs had to be removed. It improved both convenience and operational security; the printer could be installed remotely such that the signal officer operating the machine no longer had to see the decrypted
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
.
''Fernlesegerät''
Another accessory was the remote lamp panel ''Fernlesegerät''. For machines equipped with the extra panel, the wooden case of the Enigma was wider and could store the extra panel. A lamp panel version could be connected afterwards, but that required, as with the ''Schreibmax'', that the lamp panel and light bulbs be removed.
The remote panel made it possible for a person to read the decrypted plaintext without the operator seeing it.
''Uhr''

In 1944, the ''Luftwaffe'' introduced a plugboard switch, called the ''Uhr'' (clock), a small box containing a switch with 40 positions. It replaced the standard plugs. After connecting the plugs, as determined in the daily key sheet, the operator turned the switch into one of the 40 positions, each producing a different combination of plug wiring. Most of these plug connections were, unlike the default plugs, not pair-wise.
In one switch position, the ''Uhr'' did not swap letters, but simply emulated the 13 stecker wires with plugs.
Mathematical analysis
The Enigma transformation for each letter can be specified mathematically as a product of
permutation
In mathematics, a permutation of a set can mean one of two different things:
* an arrangement of its members in a sequence or linear order, or
* the act or process of changing the linear order of an ordered set.
An example of the first mean ...
s. Assuming a three-rotor German Army/Air Force Enigma, let denote the plugboard transformation, denote that of the reflector (
), and , , denote those of the left, middle and right rotors respectively. Then the encryption can be expressed as
:
After each key press, the rotors turn, changing the transformation. For example, if the right-hand rotor is rotated positions, the transformation becomes
:
where is the
cyclic permutation
In mathematics, and in particular in group theory, a cyclic permutation is a permutation consisting of a single cycle. In some cases, cyclic permutations are referred to as cycles; if a cyclic permutation has ''k'' elements, it may be called a ''k ...
mapping A to B, B to C, and so forth. Similarly, the middle and left-hand rotors can be represented as and rotations of and . The encryption transformation can then be described as
:
Combining three rotors from a set of five, each of the 3 rotor settings with 26 positions, and the plugboard with ten pairs of letters connected, the military Enigma has 158,962,555,217,826,360,000 different settings (nearly 159
quintillion
Depending on context (e.g. language, culture, region), some large numbers have names that allow for describing large quantities in a textual form; not mathematical. For very large values, the text is generally shorter than a decimal numeric repres ...
or about 67
bit
The bit is the most basic unit of information in computing and digital communication. The name is a portmanteau of binary digit. The bit represents a logical state with one of two possible values. These values are most commonly represented as ...
s).
* Choose 3 rotors from a set of 5 rotors = 5 x 4 x 3 = 60
* 26 positions per rotor = 26 x 26 x 26 = 17,576
* Plugboard = 26! / ( 6! x 10! x 2^10) = 150,738,274,937,250
* Multiply each of the above = 158,962,555,217,826,360,000
Operation
Basic operation
A German Enigma operator would be given a plaintext message to encrypt. After setting up his machine, he would type the message on the Enigma keyboard. For each letter pressed, one lamp lit indicating a different letter according to a
pseudo-random
A pseudorandom sequence of numbers is one that appears to be statistically random, despite having been produced by a completely deterministic and repeatable process. Pseudorandom number generators are often used in computer programming, as tradi ...
substitution determined by the electrical pathways inside the machine. The letter indicated by the lamp would be recorded, typically by a second operator, as the
cyphertext letter. The action of pressing a key also moved one or more rotors so that the next key press used a different electrical pathway, and thus a different substitution would occur even if the same plaintext letter were entered again. For each key press there was rotation of at least the right hand rotor and less often the other two, resulting in a different
substitution alphabet being used for every letter in the message. This process continued until the message was completed. The cyphertext recorded by the second operator would then be transmitted, usually by radio in
Morse code
Morse code is a telecommunications method which Character encoding, encodes Written language, text characters as standardized sequences of two different signal durations, called ''dots'' and ''dashes'', or ''dits'' and ''dahs''. Morse code i ...
, to an operator of another Enigma machine. This operator would type in the cyphertext and — as long as all the settings of the deciphering machine were identical to those of the enciphering machine — for every key press the reverse substitution would occur and the plaintext message would emerge.
Details


In use, the Enigma required a list of daily key settings and auxiliary documents. In German military practice, communications were divided into separate networks, each using different settings. These communication nets were termed ''keys'' at
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the S ...
, and were assigned
code name
A code name, codename, call sign, or cryptonym is a code word or name used, sometimes clandestinely, to refer to another name, word, project, or person. Code names are often used for military purposes, or in espionage. They may also be used in ...
s, such as ''Red'', ''Chaffinch'', and ''Shark''. Each unit operating in a network was given the same settings list for its Enigma, valid for a period of time. The procedures for German Naval Enigma were more elaborate and more secure than those in other services and employed auxiliary
codebook
A codebook is a type of document used for gathering and storing cryptography codes. Originally, codebooks were often literally , but today "codebook" is a byword for the complete record of a series of codes, regardless of physical format.
Cr ...
s. Navy codebooks were printed in red, water-soluble ink on pink paper so that they could easily be destroyed if they were endangered or if the vessel was sunk.
An Enigma machine's setting (its
cryptographic key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm
In mathematics and computer science, an algorithm () is a finite sequenc ...
in modern terms; ''Schlüssel'' in German) specified each operator-adjustable aspect of the machine:
* Wheel order (''Walzenlage'') – the choice of rotors and the order in which they are fitted.
* Ring settings (''Ringstellung'') – the position of each alphabet ring relative to its rotor wiring.
* Plug connections (''Steckerverbindungen'') – the pairs of letters in the plugboard that are connected together.
* In very late versions, the wiring of the reconfigurable reflector.
* Starting position of the rotors (''Grundstellung'') – chosen by the operator, should be different for each message.
For a message to be correctly encrypted and decrypted, both sender and receiver had to configure their Enigma in the same way; rotor selection and order, ring positions, plugboard connections and starting rotor positions must be identical. Except for the starting positions, these settings were established beforehand, distributed in key lists and changed daily. For example, the settings for the 18th day of the month in the German Luftwaffe Enigma key list number 649 (see image) were as follows:
* Wheel order: IV, II, V
* Ring settings: 15, 23, 26
* Plugboard connections: EJ OY IV AQ KW FX MT PS LU BD
* Reconfigurable reflector wiring: IU AS DV GL FT OX EZ CH MR KN BQ PW
* Indicator groups: lsa zbw vcj rxn
Enigma was designed to be secure even if the rotor wiring was known to an opponent, although in practice considerable effort protected the wiring configuration. If the wiring is secret, the total number of possible configurations has been calculated to be around (approximately 380 bits); with known wiring and other operational constraints, this is reduced to around (76 bits).
Because of the large number of possibilities, users of Enigma were confident of its security; it was not then feasible for an adversary to even begin to try a
brute-force attack
In cryptography, a brute-force attack or exhaustive key search is a cryptanalytic attack that consists of an attacker submitting many possible keys or passwords with the hope of eventually guessing correctly. This strategy can theoretically be ...
.
Indicator
Most of the key was kept constant for a set time period, typically a day. A different initial rotor position was used for each message, a concept similar to an
initialisation vector in modern cryptography. The reason is that encrypting many messages with identical or near-identical settings (termed in cryptanalysis as being ''in
depth''), would enable an attack using a statistical procedure such as
Friedman's Index of coincidence
In cryptography, coincidence counting is the technique (invented by William F. Friedman) of putting two texts side-by-side and counting the number of times that identical letters appear in the same position in both texts. This count, either as a r ...
. The starting position for the rotors was transmitted just before the ciphertext, usually after having been enciphered. The exact method used was termed the ''indicator procedure''. Design weakness and operator sloppiness in these indicator procedures were two of the main weaknesses that made cracking Enigma possible.

One of the earliest ''indicator procedures'' for the Enigma was cryptographically flawed and allowed Polish cryptanalysts to make the initial breaks into the plugboard Enigma. The procedure had the operator set his machine in accordance with the secret settings that all operators on the net shared. The settings included an initial position for the rotors (the ''Grundstellung''), say, ''AOH''. The operator turned his rotors until ''AOH'' was visible through the rotor windows. At that point, the operator chose his own arbitrary starting position for the message he would send. An operator might select ''EIN'', and that became the ''message setting'' for that encryption session. The operator then typed ''EIN'' into the machine twice, this producing the encrypted indicator, for example ''XHTLOA''. This was then transmitted, at which point the operator would turn the rotors to his message settings, ''EIN'' in this example, and then type the plaintext of the message.
At the receiving end, the operator set the machine to the initial settings (''AOH'') and typed in the first six letters of the message (''XHTLOA''). In this example, ''EINEIN'' emerged on the lamps, so the operator would learn the ''message setting'' that the sender used to encrypt this message. The receiving operator would set his rotors to ''EIN'', type in the rest of the ciphertext, and get the deciphered message.
This indicator scheme had two weaknesses. First, the use of a global initial position (''Grundstellung'') meant all message keys used the same polyalphabetic substitution. In later indicator procedures, the operator selected his initial position for encrypting the indicator and sent that initial position in the clear. The second problem was the repetition of the indicator, which was a serious security flaw. The message setting was encoded twice, resulting in a relation between first and fourth, second and fifth, and third and sixth character. These security flaws enabled the Polish Cipher Bureau to break into the pre-war Enigma system as early as 1932. The early indicator procedure was subsequently described by German cryptanalysts as the "faulty indicator technique".
During World War II, codebooks were only used each day to set up the rotors, their ring settings and the plugboard. For each message, the operator selected a random start position, let's say ''WZA'', and a random message key, perhaps ''SXT''. He moved the rotors to the ''WZA'' start position and encoded the message key ''SXT''. Assume the result was ''UHL''. He then set up the message key, ''SXT'', as the start position and encrypted the message. Next, he transmitted the start position, ''WZA'', the encoded message key, ''UHL'', and then the ciphertext. The receiver set up the start position according to the first trigram, ''WZA'', and decoded the second trigram, ''UHL'', to obtain the ''SXT'' message setting. Next, he used this ''SXT'' message setting as the start position to decrypt the message. This way, each ground setting was different and the new procedure avoided the security flaw of double encoded message settings.
This procedure was used by ''Heer'' and ''Luftwaffe'' only. The ''Kriegsmarine'' procedures for sending messages with the Enigma were far more complex and elaborate. Prior to encryption the message was encoded using the ''
Kurzsignalheft'' code book. The ''Kurzsignalheft'' contained tables to convert sentences into four-letter groups. A great many choices were included, for example, logistic matters such as refuelling and rendezvous with supply ships, positions and grid lists, harbour names, countries, weapons, weather conditions, enemy positions and ships, date and time tables. Another codebook contained the ''
Kenngruppen'' and ''Spruchschlüssel'': the key identification and message key.
Additional details
The Army Enigma machine used only the 26 alphabet characters. Punctuation was replaced with rare character combinations. A space was omitted or replaced with an X. The X was generally used as full-stop.
Some punctuation marks were different in other parts of the armed forces. The ''Wehrmacht'' replaced a comma with ZZ and the question mark with FRAGE or FRAQ.
The ''Kriegsmarine'' replaced the comma with Y and the question mark with UD. The combination CH, as in "''Acht''" (eight) or "''Richtung''" (direction), was replaced with Q (AQT, RIQTUNG). Two, three and four zeros were replaced with CENTA, MILLE and MYRIA.
The ''Wehrmacht'' and the ''Luftwaffe'' transmitted messages in groups of five characters and counted the letters.
The ''Kriegsmarine'' used four-character groups and counted those groups.
Frequently used names or words were varied as much as possible. Words like ''Minensuchboot'' (minesweeper) could be written as MINENSUCHBOOT, MINBOOT or MMMBOOT. To make cryptanalysis harder, messages were limited to 250 characters. Longer messages were divided into several parts, each using a different message key.
Example enciphering process
The character substitutions by the Enigma machine as a whole can be expressed as a string of letters with each position occupied by the character that will replace the character at the corresponding position in the alphabet. For example, a given machine configuration that enciphered A to L, B to U, C to S, ..., and Z to J could be represented compactly as
LUSHQOXDMZNAIKFREPCYBWVGTJ
and the enciphering of a particular character by that configuration could be represented by highlighting the enciphered character as in
D > LUS(H)QOXDMZNAIKFREPCYBWVGTJ
Since the operation of an Enigma machine enciphering a message is a series of such configurations, each associated with a single character being enciphered, a sequence of such representations can be used to represent the operation of the machine as it enciphers a message. For example, the process of enciphering the first sentence of the main body of the famous "Dönitz message" to
RBBF PMHP HGCZ XTDY GAHG UFXG EWKB LKGJ
can be represented as
0001 F > KGWNT(R)BLQPAHYDVJIFXEZOCSMU CDTK 25 15 16 26
0002 O > UORYTQSLWXZHNM(B)VFCGEAPIJDK CDTL 25 15 16 01
0003 L > HLNRSKJAMGF(B)ICUQPDEYOZXWTV CDTM 25 15 16 02
0004 G > KPTXIG(F)MESAUHYQBOVJCLRZDNW CDUN 25 15 17 03
0005 E > XDYB(P)WOSMUZRIQGENLHVJTFACK CDUO 25 15 17 04
0006 N > DLIAJUOVCEXBN(M)GQPWZYFHRKTS CDUP 25 15 17 05
0007 D > LUS(H)QOXDMZNAIKFREPCYBWVGTJ CDUQ 25 15 17 06
0008 E > JKGO(P)TCIHABRNMDEYLZFXWVUQS CDUR 25 15 17 07
0009 S > GCBUZRASYXVMLPQNOF(H)WDKTJIE CDUS 25 15 17 08
0010 I > XPJUOWIY(G)CVRTQEBNLZMDKFAHS CDUT 25 15 17 09
0011 S > DISAUYOMBPNTHKGJRQ(C)LEZXWFV CDUU 25 15 17 10
0012 T > FJLVQAKXNBGCPIRMEOY(Z)WDUHST CDUV 25 15 17 11
0013 S > KTJUQONPZCAMLGFHEW(X)BDYRSVI CDUW 25 15 17 12
0014 O > ZQXUVGFNWRLKPH(T)MBJYODEICSA CDUX 25 15 17 13
0015 F > XJWFR(D)ZSQBLKTVPOIEHMYNCAUG CDUY 25 15 17 14
0016 O > FSKTJARXPECNUL(Y)IZGBDMWVHOQ CDUZ 25 15 17 15
0017 R > CEAKBMRYUVDNFLTXW(G)ZOIJQPHS CDVA 25 15 18 16
0018 T > TLJRVQHGUCXBZYSWFDO(A)IEPKNM CDVB 25 15 18 17
0019 B > Y(H)LPGTEBKWICSVUDRQMFONJZAX CDVC 25 15 18 18
0020 E > KRUL(G)JEWNFADVIPOYBXZCMHSQT CDVD 25 15 18 19
0021 K > RCBPQMVZXY(U)OFSLDEANWKGTIJH CDVE 25 15 18 20
0022 A > (F)CBJQAWTVDYNXLUSEZPHOIGMKR CDVF 25 15 18 21
0023 N > VFTQSBPORUZWY(X)HGDIECJALNMK CDVG 25 15 18 22
0024 N > JSRHFENDUAZYQ(G)XTMCBPIWVOLK CDVH 25 15 18 23
0025 T > RCBUTXVZJINQPKWMLAY(E)DGOFSH CDVI 25 15 18 24
0026 Z > URFXNCMYLVPIGESKTBOQAJZDH(W) CDVJ 25 15 18 25
0027 U > JIOZFEWMBAUSHPCNRQLV(K)TGYXD CDVK 25 15 18 26
0028 G > ZGVRKO(B)XLNEIWJFUSDQYPCMHTA CDVL 25 15 18 01
0029 E > RMJV(L)YQZKCIEBONUGAWXPDSTFH CDVM 25 15 18 02
0030 B > G(K)QRFEANZPBMLHVJCDUXSOYTWI CDWN 25 15 19 03
0031 E > YMZT(G)VEKQOHPBSJLIUNDRFXWAC CDWO 25 15 19 04
0032 N > PDSBTIUQFNOVW(J)KAHZCEGLMYXR CDWP 25 15 19 05
where the letters following each mapping are the letters that appear at the windows at that stage (the only state changes visible to the operator) and the numbers show the underlying physical position of each rotor.
The character mappings for a given configuration of the machine are in turn the result of a series of such mappings applied by each pass through a component of the machine: the enciphering of a character resulting from the application of a given component's mapping serves as the input to the mapping of the subsequent component. For example, the 4th step in the enciphering above can be expanded to show each of these stages using the same representation of mappings and highlighting for the enciphered character:
G > ABCDEF(G)HIJKLMNOPQRSTUVWXYZ
P EFMQAB(G)UINKXCJORDPZTHWVLYS AE.BF.CM.DQ.HU.JN.LX.PR.SZ.VW
1 OFRJVM(A)ZHQNBXPYKCULGSWETDI N 03 VIII
2 (N)UKCHVSMDGTZQFYEWPIALOXRJB U 17 VI
3 XJMIYVCARQOWH(L)NDSUFKGBEPZT D 15 V
4 QUNGALXEPKZ(Y)RDSOFTVCMBIHWJ C 25 β
R RDOBJNTKVEHMLFCWZAXGYIPS(U)Q c
4 EVTNHQDXWZJFUCPIAMOR(B)SYGLK β
3 H(V)GPWSUMDBTNCOKXJIQZRFLAEY V
2 TZDIPNJESYCUHAVRMXGKB(F)QWOL VI
1 GLQYW(B)TIZDPSFKANJCUXREVMOH VIII
P E(F)MQABGUINKXCJORDPZTHWVLYS AE.BF.CM.DQ.HU.JN.LX.PR.SZ.VW
F < KPTXIG(F)MESAUHYQBOVJCLRZDNW
Here the enciphering begins trivially with the first "mapping" representing the keyboard (which has no effect), followed by the plugboard, configured as AE.BF.CM.DQ.HU.JN.LX.PR.SZ.VW which has no effect on 'G', followed by the VIII rotor in the 03 position, which maps G to A, then the VI rotor in the 17 position, which maps A to N, ..., and finally the plugboard again, which maps B to F, producing the overall mapping indicated at the final step: G to F.
This model has 4 rotors (lines 1 through 4) and the reflector (line R) also permutes (garbles) letters.
Models
The Enigma family included multiple designs. The earliest were commercial models dating from the early 1920s. Starting in the mid-1920s, the German military began to use Enigma, making a number of security-related changes. Various nations either adopted or adapted the design for their own cipher machines.
An estimated 40,000 Enigma machines were constructed. After the end of World War II, the Allies sold captured Enigma machines, still widely considered secure, to developing countries.
Commercial Enigma

On 23 February 1918,
Arthur Scherbius applied for a
patent
A patent is a type of intellectual property that gives its owner the legal right to exclude others from making, using, or selling an invention for a limited period of time in exchange for publishing an sufficiency of disclosure, enabling discl ...
for a ciphering machine that used
rotors. Scherbius and
E. Richard Ritter founded the firm of Scherbius & Ritter. They approached the
German Navy
The German Navy (, ) is part of the unified (Federal Defense), the German Armed Forces. The German Navy was originally known as the ''Bundesmarine'' (Federal Navy) from 1956 to 1995, when ''Deutsche Marine'' (German Navy) became the official ...
and Foreign Office with their design, but neither agency was interested. Scherbius & Ritter then assigned the patent rights to Gewerkschaft Securitas, who founded the ''Chiffriermaschinen Aktien-Gesellschaft'' (Cipher Machines Stock Corporation) on 9 July 1923; Scherbius and Ritter were on the board of directors.
Enigma Handelsmaschine (1923)
Chiffriermaschinen AG began advertising a rotor machine, ''Enigma Handelsmaschine'', which was exhibited at the Congress of the
International Postal Union in 1924. The machine was heavy and bulky, incorporating a
typewriter
A typewriter is a Machine, mechanical or electromechanical machine for typing characters. Typically, a typewriter has an array of Button (control), keys, and each one causes a different single character to be produced on paper by striking an i ...
. It measured 65×45×38 cm and weighed about .
Schreibende Enigma (1924)
This was also a model with a type writer. There were a number of problems associated with the printer and the construction was not stable until 1926. Both early versions of Enigma lacked the reflector and had to be switched between enciphering and deciphering.
Glühlampenmaschine, Enigma A (1924)
The reflector, suggested by Scherbius' colleague Willi Korn,
was introduced with the glow lamp version.
The machine was also known as the military Enigma. It had two rotors and a manually rotatable reflector. The typewriter was omitted and glow lamps were used for output. The operation was somewhat different from later models. Before the next key pressure, the operator had to press a button to advance the right rotor one step.
Enigma B (1924)
Enigma ''model B'' was introduced late in 1924, and was of a similar construction. While bearing the Enigma name, both models ''A'' and ''B'' were quite unlike later versions: They differed in physical size and shape, but also cryptographically, in that they lacked the reflector. This model of Enigma machine was referred to as the Glowlamp Enigma or ''Glühlampenmaschine'' since it produced its output on a lamp panel rather than paper. This method of output was much more reliable and cost effective. Hence this machine was 1/8th the price of its predecessor.
Enigma C (1926)
''Model C'' was the third model of the so-called ″glowlamp Enigmas″ (after A and B) and it again lacked a typewriter.
Enigma D (1927)
The ''Enigma C'' quickly gave way to ''Enigma D'' (1927). This version was widely used, with shipments to Sweden, the Netherlands, United Kingdom, Japan, Italy, Spain, United States and Poland. In 1927
Hugh Foss at the British
Government Code and Cypher School
The Government Code and Cypher School (GC&CS) was a British signals intelligence agency set up in 1919. During the First World War, the British Army and Royal Navy had separate signals intelligence agencies, MI1b and NID25 (initially known as R ...
was able to show that commercial Enigma machines could be broken, provided suitable cribs were available. Soon, the Enigma D would pioneer the use of a standard keyboard layout to be used in German computing. This "QWERTZ" layout is very similar to the American
QWERTY
QWERTY ( ) is a keyboard layout for Latin-script alphabets. The name comes from the order of the first six Computer keyboard keys#Types, keys on the top letter row of the keyboard: . The QWERTY design is based on a layout included in the Sh ...
keyboard format used in many languages.
= "Navy Cipher D"
=
Other countries used Enigma machines. The
Italian Navy
The Italian Navy (; abbreviated as MM) is one of the four branches of Italian Armed Forces and was formed in 1946 from what remained of the ''Regia Marina'' (Royal Navy) after World War II. , the Italian Navy had a strength of 30,923 active per ...
adopted the commercial Enigma as "Navy Cipher D". The Spanish also used commercial Enigma machines during their
Civil War
A civil war is a war between organized groups within the same Sovereign state, state (or country). The aim of one side may be to take control of the country or a region, to achieve independence for a region, or to change government policies.J ...
. British codebreakers succeeded in breaking these machines, which lacked a plugboard. Enigma machines were also used by diplomatic services.
Enigma H (1929)

There was also a large, eight-rotor printing model, the ''Enigma H'', called ''Enigma II'' by the ''
Reichswehr
''Reichswehr'' (; ) was the official name of the German armed forces during the Weimar Republic and the first two years of Nazi Germany. After Germany was defeated in World War I, the Imperial German Army () was dissolved in order to be reshaped ...
''. In 1933 the Polish Cipher Bureau detected that it was in use for high-level military communication, but it was soon withdrawn, as it was unreliable and jammed frequently.
Enigma K
The Swiss used a version of Enigma called ''Model K'' or ''Swiss K'' for military and diplomatic use, which was very similar to commercial
Enigma D. The machine's code was cracked by Poland, France, the United Kingdom and the United States; the latter code-named it INDIGO. An ''Enigma T'' model, code-named ''Tirpitz'', was used by Japan.
Military Enigma
The various services of the
Wehrmacht
The ''Wehrmacht'' (, ) were the unified armed forces of Nazi Germany from 1935 to 1945. It consisted of the German Army (1935–1945), ''Heer'' (army), the ''Kriegsmarine'' (navy) and the ''Luftwaffe'' (air force). The designation "''Wehrmac ...
used various Enigma versions, and replaced them frequently, sometimes with ones adapted from other services. Enigma seldom carried high-level strategic messages, which when not urgent went by courier, and when urgent went by other cryptographic systems including the
Geheimschreiber.
Funkschlüssel C
The Reichsmarine was the first military branch to adopt Enigma. This version, named ''Funkschlüssel C'' ("Radio cipher C"), had been put into production by 1925 and was introduced into service in 1926.
The keyboard and lampboard contained 29 letters — A-Z, Ä, Ö and Ü — that were arranged alphabetically, as opposed to the QWERTZUI ordering. The rotors had 28 contacts, with the letter ''X'' wired to bypass the rotors unencrypted. Three rotors were chosen from a set of five and the reflector could be inserted in one of four different positions, denoted α, β, γ and δ. The machine was revised slightly in July 1933.
Enigma G (1928–1930)
By 15 July 1928, the German Army (''
Reichswehr
''Reichswehr'' (; ) was the official name of the German armed forces during the Weimar Republic and the first two years of Nazi Germany. After Germany was defeated in World War I, the Imperial German Army () was dissolved in order to be reshaped ...
'') had introduced their own exclusive version of the Enigma machine, the ''Enigma G''.
The ''
Abwehr
The (German language, German for ''resistance'' or ''defence'', though the word usually means ''counterintelligence'' in a military context) ) was the German military intelligence , military-intelligence service for the ''Reichswehr'' and the ...
'' used the ''Enigma G''. This Enigma variant was a four-wheel unsteckered machine with multiple notches on the rotors. This model was equipped with a counter that incremented upon each key press, and so is also known as the "counter machine" or the ''Zählwerk'' Enigma.
Wehrmacht Enigma I (1930–1938)
Enigma machine G was modified to the ''Enigma I'' by June 1930. Enigma I is also known as the ''Wehrmacht'', or "Services" Enigma, and was used extensively by German military services and other government organisations (such as the
railways
Rail transport (also known as train transport) is a means of transport using wheeled vehicles running in tracks, which usually consist of two parallel steel rails. Rail transport is one of the two primary means of land transport, next to roa ...
) before and during
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
.
The major difference between ''Enigma I'' (German Army version from 1930), and commercial Enigma models was the addition of a plugboard to swap pairs of letters, greatly increasing cryptographic strength.
Other differences included the use of a fixed reflector and the relocation of the stepping notches from the rotor body to the movable letter rings. The machine measured and weighed around .
In August 1935, the Air Force introduced the Wehrmacht Enigma for their communications.
M3 (1934)
By 1930, the Reichswehr had suggested that the Navy adopt their machine, citing the benefits of increased security (with the plugboard) and easier interservice communications. The Reichsmarine eventually agreed and in 1934 brought into service the Navy version of the Army Enigma, designated ''Funkschlüssel'' ' or ''M3''. While the Army used only three rotors at that time, the Navy specified a choice of three from a possible five.
Two extra rotors (1938)
In December 1938, the Army issued two extra rotors so that the three rotors were chosen from a set of five. In 1938, the Navy added two more rotors, and then another in 1939 to allow a choice of three rotors from a set of eight.
M4 (1942)
A four-rotor Enigma was introduced by the Navy for U-boat traffic on 1 February 1942, called ''
M4'' (the network was known as ''Triton'', or ''Shark'' to the Allies). The extra rotor was fitted in the same space by splitting the reflector into a combination of a thin reflector and a thin fourth rotor.
File:Enigma-G.jpg, Enigma G, used by the ''Abwehr
The (German language, German for ''resistance'' or ''defence'', though the word usually means ''counterintelligence'' in a military context) ) was the German military intelligence , military-intelligence service for the ''Reichswehr'' and the ...
'', had four rotors, no plugboard, and multiple notches on the rotors.
File:Enigma-IMG 0484-black.jpg, The German-made Enigma-K used by the Swiss Army had three rotors and a reflector, but no plugboard. It had locally re-wired rotors and an additional lamp panel.
File:Four-rotor-enigma.jpg, An Enigma model T (Tirpitz), a modified commercial Enigma K manufactured for use by the Japanese
File:Enigma Decoder Machine.jpg, An Enigma machine in the UK's Imperial War Museum
File:Bundesarchiv Bild 101I-241-2173-06, Russland, Verschlüsselungsgerät Enigma.jpg, Enigma in use in Russia
File:Bundesarchiv Bild 146-2006-0188, Verschlüsselungsgerät "Enigma".jpg, Enigma in radio car of the 7th Panzer Div. staff, August 1941

Surviving machines
The effort to break the Enigma was not disclosed until 1973. Since then, interest in the Enigma machine has grown. Enigmas are on public display in museums around the world, and several are in the hands of private collectors and computer history enthusiasts.
[Ng, David]
"Enigma machine from World War II finds unlikely home in Beverly Hills"
''Los Angeles Times
The ''Los Angeles Times'' is an American Newspaper#Daily, daily newspaper that began publishing in Los Angeles, California, in 1881. Based in the Greater Los Angeles city of El Segundo, California, El Segundo since 2018, it is the List of new ...
''. 22 January 2015.
The ''
Deutsches Museum
The Deutsches Museum (''German Museum'', officially (English: ''German Museum of Masterpieces of Science and Technology'')) in Munich, Germany, is the world's largest museum of science museum, science and technology museum, technology, with a ...
'' in
Munich
Munich is the capital and most populous city of Bavaria, Germany. As of 30 November 2024, its population was 1,604,384, making it the third-largest city in Germany after Berlin and Hamburg. Munich is the largest city in Germany that is no ...
has both the three- and four-rotor German military variants, as well as several civilian versions. The ''
Deutsches Spionagemuseum'' in
Berlin
Berlin ( ; ) is the Capital of Germany, capital and largest city of Germany, by both area and List of cities in Germany by population, population. With 3.7 million inhabitants, it has the List of cities in the European Union by population withi ...
also showcases two military variants. Enigma machines are also exhibited at the
National Codes Centre in
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the S ...
, the
Government Communications Headquarters
Government Communications Headquarters (GCHQ) is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primari ...
, the
Science Museum
A science museum is a museum devoted primarily to science. Older science museums tended to concentrate on static displays of objects related to natural history, paleontology, geology, Industry (manufacturing), industry and Outline of industrial ...
in
London
London is the Capital city, capital and List of urban areas in the United Kingdom, largest city of both England and the United Kingdom, with a population of in . London metropolitan area, Its wider metropolitan area is the largest in Wester ...
,
Discovery Park of America in Tennessee, the
Polish Army Museum in Warsaw, the
Swedish Army Museum
The Swedish Army Museum () is a museum of military history located in the district of Östermalm in Stockholm. It reopened in 2002 after a long period of closure, and was awarded the title of the best museum of Stockholm in 2005. Its displays il ...
(''Armémuseum'') in Stockholm, the Military Museum of
A Coruña
A Coruña (; ; also informally called just Coruña; historical English: Corunna or The Groyne) is a city and municipality in Galicia, Spain. It is Galicia's second largest city, behind Vigo. The city is the provincial capital of the province ...
in Spain, the Nordland Red Cross War Memorial Museum in
Narvik
() is the third-largest List of municipalities of Norway, municipality in Nordland Counties of Norway, county, Norway, by population. The administrative centre of the municipality is the Narvik (town), town of Narvik. Some of the notable villag ...
, Norway,
The Artillery, Engineers and Signals Museum in
Hämeenlinna
Hämeenlinna (; ; ; or ''Croneburgum'') is a city in Finland and the regional capital of Kanta-Häme. It is located in the southern interior of the country and on the shores of Vanajavesi, Lake Vanajavesi. The population of Hämeenlinna is appr ...
, Finland the
Technical University of Denmark
The Technical University of Denmark (), often simply referred to as DTU, is a polytechnic university and school of engineering. It was founded in 1829 at the initiative of Hans Christian Ørsted as Denmark's first polytechnic, and it is today ran ...
in Lyngby, Denmark, in
Skanderborg Bunkerne at Skanderborg, Denmark, and at the
Australian War Memorial
The Australian War Memorial (AWM) is a national war memorial, war museum, museum and archive dedicated to all Australians who died as a result of war, including peacekeeping duties. The AWM is located in Campbell, Australian Capital Territory, C ...
and in the foyer of the
Australian Signals Directorate
The Australian Signals Directorate (ASD), formerly the Defence Signals Directorate, is a statutory agency of the Government of Australia responsible for signals intelligence, providing intelligence support to Australian military operations, con ...
, both in
Canberra
Canberra ( ; ) is the capital city of Australia. Founded following the Federation of Australia, federation of the colonies of Australia as the seat of government for the new nation, it is Australia's list of cities in Australia, largest in ...
, Australia. The Jozef Pilsudski Institute in London exhibited a rare
Polish Enigma double assembled in France in 1940. In 2020, thanks to the support of the Ministry of Culture and National Heritage, it became the property of the Polish History Museum.

In the United States, Enigma machines can be seen at the
Computer History Museum
The Computer History Museum (CHM) is a computer museum in Mountain View, California. The museum presents stories and artifacts of Silicon Valley and the Information Age, and explores the Digital Revolution, computing revolution and its impact ...
in
Mountain View, California
Mountain View is a city in Santa Clara County, California, United States, part of the San Francisco Bay Area. Named for its views of the Santa Cruz Mountains, the population was 82,376 at the 2020 United States census, 2020 census.
Mountain V ...
, and at the
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
's
National Cryptologic Museum
The National Cryptologic Museum (NCM) is an American museum of cryptologic history that is affiliated with the National Security Agency (NSA). The first public museum in the U.S. Intelligence Community, NCM is located in the former Colony Sev ...
in
Fort Meade
Fort George G. Meade is a United States Army installation located in Maryland, that includes the Defense Information School, the Defense Media Activity, the United States military bands#Army Field Band, United States Army Field Band, and the head ...
, Maryland, where visitors can try their hand at enciphering and deciphering messages. Two machines that were acquired after the capture of during World War II are on display alongside the submarine at the
Museum of Science and Industry in
Chicago
Chicago is the List of municipalities in Illinois, most populous city in the U.S. state of Illinois and in the Midwestern United States. With a population of 2,746,388, as of the 2020 United States census, 2020 census, it is the List of Unite ...
, Illinois. A three-rotor Enigma is on display at
Discovery Park of America in
Union City, Tennessee. A four-rotor device is on display in the ANZUS Corridor of the
Pentagon
In geometry, a pentagon () is any five-sided polygon or 5-gon. The sum of the internal angles in a simple polygon, simple pentagon is 540°.
A pentagon may be simple or list of self-intersecting polygons, self-intersecting. A self-intersecting ...
on the second floor, A ring, between corridors 8 and 9. This machine is on loan from Australia. The United States Air Force Academy in Colorado Springs has a machine on display in the Computer Science Department. There is also a machine located at
The National WWII Museum
The National WWII Museum, formerly known as The National D-Day Museum, is a military history museum located in the Central Business District of New Orleans, Louisiana, U.S., on Andrew Higgins Drive between Camp Street and Magazine Street. The ...
in New Orleans.
The International Museum of World War II near Boston has seven Enigma machines on display, including a U-boat four-rotor model, one of three surviving examples of an Enigma machine with a printer, one of fewer than ten surviving ten-rotor code machines, an example blown up by a retreating German Army unit, and two three-rotor Enigmas that visitors can operate to encode and decode messages.
Mimms Museum of Technology and Art in
Roswell, Georgia
Roswell is a city in northern Fulton County, Georgia, United States. At the official 2020 census, the city had a population of 92,883, making Roswell the state's ninth largest city. A suburb of Atlanta, Roswell has an affluent National Registe ...
has a three-rotor model with two additional rotors. The machine is fully restored and CMoA has the original paperwork for the purchase on 7 March 1936 by the German Army. The
National Museum of Computing
The National Museum of Computing is a UK-based museum that is dedicated to collecting and restoring History of computing hardware, historic computer systems, and is home to the world's largest collection of working historic computers. The muse ...
also contains surviving Enigma machines in Bletchley, England.

In Canada, a Swiss Army issue Enigma-K, is in Calgary, Alberta. It is on permanent display at the Naval Museum of Alberta inside the Military Museums of Calgary. A four-rotor Enigma machine is on display at the
Military Communications and Electronics Museum at
Canadian Forces Base (CFB) Kingston in
Kingston, Ontario
Kingston is a city in Ontario, Canada, on the northeastern end of Lake Ontario. It is at the beginning of the St. Lawrence River and at the mouth of the Cataraqui River, the south end of the Rideau Canal. Kingston is near the Thousand Islands, ...
.
Occasionally, Enigma machines are sold at auction; prices have in recent years ranged from US$40,000 to US$547,500 in 2017. Replicas are available in various forms, including an exact reconstructed copy of the Naval M4 model, an Enigma implemented in electronics (Enigma-E), various simulators and paper-and-scissors analogues.
A rare ''Abwehr'' Enigma machine, designated G312, was stolen from the
Bletchley Park museum on 1 April 2000. In September, a man identifying himself as "The Master" sent a note demanding £25,000 and threatening to destroy the machine if the ransom was not paid. In early October 2000, Bletchley Park officials announced that they would pay the ransom, but the stated deadline passed with no word from the blackmailer. Shortly afterward, the machine was sent anonymously to BBC journalist
Jeremy Paxman
Jeremy Dickson Paxman (born 11 May 1950) is an English former broadcaster, journalist and author, born in Yorkshire.
Born in Leeds, Paxman was educated at Malvern College and St Catharine's College, Cambridge, where he edited the undergraduate ...
, missing three rotors.

In November 2000, an antiques dealer named Dennis Yates was arrested after telephoning ''
The Sunday Times
''The Sunday Times'' is a British Sunday newspaper whose circulation makes it the largest in Britain's quality press market category. It was founded in 1821 as ''The New Observer''. It is published by Times Newspapers Ltd, a subsidiary of N ...
'' to arrange the return of the missing parts. The Enigma machine was returned to Bletchley Park after the incident. In October 2001, Yates was sentenced to ten months in prison and served three months.
In October 2008, the Spanish daily newspaper ''
El País
(; ) is a Spanish-language daily newspaper in Spain. is based in the capital city of Madrid and it is owned by the Spanish media conglomerate PRISA.
It is the second-most circulated daily newspaper in Spain . is the most read newspaper in ...
'' reported that 28 Enigma machines had been discovered by chance in an attic of Army headquarters in Madrid. These four-rotor commercial machines had helped Franco's Nationalists win the
Spanish Civil War
The Spanish Civil War () was a military conflict fought from 1936 to 1939 between the Republican faction (Spanish Civil War), Republicans and the Nationalist faction (Spanish Civil War), Nationalists. Republicans were loyal to the Left-wing p ...
, because, though the British cryptologist
Alfred Dilwyn Knox in 1937 broke the cipher generated by Franco's Enigma machines, this was not disclosed to the Republicans, who failed to break the cipher. The Nationalist government continued using its 50 Enigmas into the 1950s. Some machines have gone on display in Spanish military museums, including one at the National Museum of Science and Technology (MUNCYT) in La Coruña and one at the
Spanish Army Museum. Two have been given to Britain's GCHQ.
The
Bulgaria
Bulgaria, officially the Republic of Bulgaria, is a country in Southeast Europe. It is situated on the eastern portion of the Balkans directly south of the Danube river and west of the Black Sea. Bulgaria is bordered by Greece and Turkey t ...
n military used Enigma machines with a
Cyrillic
The Cyrillic script ( ) is a writing system used for various languages across Eurasia. It is the designated national script in various Slavic, Turkic, Mongolic, Uralic, Caucasian and Iranic-speaking countries in Southeastern Europe, Ea ...
keyboard; one is on display in the
National Museum of Military History in
Sofia
Sofia is the Capital city, capital and List of cities and towns in Bulgaria, largest city of Bulgaria. It is situated in the Sofia Valley at the foot of the Vitosha mountain, in the western part of the country. The city is built west of the Is ...
.
On 3 December 2020, German divers working on behalf of the
World Wide Fund for Nature
The World Wide Fund for Nature (WWF) is a Swiss-based international non-governmental organization founded in 1961 that works in the field of wilderness preservation and the reduction of human impact on the environment. It was formerly named th ...
discovered a destroyed Enigma machine in
Flensburg Firth (part of the
Baltic Sea
The Baltic Sea is an arm of the Atlantic Ocean that is enclosed by the countries of Denmark, Estonia, Finland, Germany, Latvia, Lithuania, Poland, Russia, Sweden, and the North European Plain, North and Central European Plain regions. It is the ...
) which is believed to be from a scuttled U-boat. This Enigma machine will be restored by and be the property of the Archaeology Museum of
Schleswig Holstein.
An M4 Enigma was salvaged in the 1980s from the German minesweeper R15, which was sunk off the
Istria
Istria ( ; Croatian language, Croatian and Slovene language, Slovene: ; Italian language, Italian and Venetian language, Venetian: ; ; Istro-Romanian language, Istro-Romanian: ; ; ) is the largest peninsula within the Adriatic Sea. Located at th ...
n coast in 1945. The machine was put on display in the
Pivka Park of Military History
Pivka (, , ) is a small town in Slovenia in the Pivka Basin in the Karst Plateau, Karst region. It is the seat of the Municipality of Pivka. It belongs to the traditional region of Inner Carniola.
Name
Pivka was first mentioned in 1300 as ''villa ...
in
Slovenia
Slovenia, officially the Republic of Slovenia, is a country in Central Europe. It borders Italy to the west, Austria to the north, Hungary to the northeast, Croatia to the south and southeast, and a short (46.6 km) coastline within the Adriati ...
on 13 April 2023.
Derivatives
The Enigma was influential in the field of cipher machine design, spinning off other
rotor machine
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use from ...
s. Once the British discovered Enigma's principle of operation, they created the
Typex rotor cipher, which the Germans believed to be unsolvable. Typex was originally derived from the Enigma patents;
Typex even includes features from the patent descriptions that were omitted from the actual Enigma machine. The British paid no royalties for the use of the patents.
In the United States, cryptologist
William Friedman designed the
M-325 machine,
starting in 1936, that is logically similar.
Machines like the
SIGABA,
NEMA
The National Electrical Manufacturers Association (NEMA) is the largest trade association of electrical equipment manufacturers in the United States. Founded in 1926, it advocates for the industry and publishes standards for electrical product ...
, Typex, and so forth, are not considered to be Enigma derivatives as their internal ciphering functions are not mathematically identical to the Enigma transform.
A unique rotor machine called Cryptograph was constructed in 2002 by Netherlands-based Tatjana van Vark. This device makes use of 40-point rotors, allowing letters, numbers and some punctuation to be used; each rotor contains 509 parts.
[van Vark, Tatjana ]
The coding machine
'
File:Japanese secure teletype 2.jpg, A Japanese Enigma clone, codenamed GREEN by American cryptographers
File:Tatjavanavark-machine.jpg, Tatjana van Vark's Enigma-inspired rotor machine
File:Enigma simulator-IMG 0515-black.jpg, Electronic implementation of an Enigma machine, sold at the Bletchley Park souvenir shop
Simulators
See also
*
Alastair Denniston
Commander Alexander "Alastair" Guthrie Denniston (1 December 1881 – 1 January 1961) was a Scottish codebreaker, deputy head of the Government Code and Cypher School (GC&CS) and hockey player. Denniston was appointed operational head of GC&CS ...
*
Arlington Hall
Arlington Hall (also called Arlington Hall Station) is a historic building in Arlington, Virginia. Originally it was a girls' school and later the headquarters of the United States Army's Signal Intelligence Service (SIS) cryptography operations ...
*
Arne Beurling
Arne Carl-August Beurling (3 February 1905 – 20 November 1986) was a Sweden, Swedish mathematician and professor of mathematics at Uppsala University (1937–1954) and later at the Institute for Advanced Study in Princeton, New Jersey. Beurling ...
*
Beaumanor Hall, a stately home used during the Second World War for military intelligence
*
Cryptanalysis of the Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies of World War II, Allies in World War II to read substantial amounts of Morse code, Morse-coded radio communications of the Axis powers that had been enciphered using Enigm ...
*
Erhard Maertens—investigated Enigma security
*
Erich Fellgiebel
*
ECM Mark II—cipher machine used by the Americans in the Second World War
*
Fritz Thiele
Fritz Thiele (14 April 1894 – 4 September 1944) was a member of the German resistance to Nazism, German resistance who also served as the communications chief of the German Army (1935-1945), German Army during World War II. Life
Thiele was bor ...
*
Gisbert Hasenjaeger—responsible for Enigma security
*
United States Naval Computing Machine Laboratory
*
Typex—cipher machine used by the British in the Second World War, based on the principles of the commercial Enigma machine
Explanatory notes
References
Citations
General and cited references
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
Further reading
*
*
*
*
* Heath, Nick
Hacking the Nazis: The secret story of the women who broke Hitler's codesTechRepublic, 27 March 2015
*
*
*
* Marks, Philip. "Umkehrwalze D: Enigma's Rewirable Reflector — Part I", ''Cryptologia'' 25(2), April 2001, pp. 101–141.
* Marks, Philip. "Umkehrwalze D: Enigma's Rewirable Reflector — Part II", ''Cryptologia'' 25(3), July 2001, pp. 177–212.
* Marks, Philip. "Umkehrwalze D: Enigma's Rewirable Reflector — Part III", ''Cryptologia'' 25(4), October 2001, pp. 296–310.
*
*
* Perera, Tom. ''The Story of the ENIGMA: History, Technology and Deciphering'', 2nd Edition, CD-ROM, 2004, Artifax Books,
* Rebecca Ratcliff: Searching for Security. The German Investigations into Enigma's security. In: Intelligence and National Security 14 (1999) Issue 1 (Special Issue) S. 146–167.
*
*
Rejewski, Marian"How Polish Mathematicians Deciphered the Enigma", ''Annals of the History of Computing 3'', 1981. This article is regarded by
Andrew Hodges, Alan Turing's biographer, as "the definitive account" (see Hodges' ''
Alan Turing: The Enigma'', Walker and Company, 2000 paperback edition, p. 548, footnote 4.5).
*
*
* Ulbricht, Heinz. Enigma Uhr, ''Cryptologia'', 23(3), April 1999, pp. 194–205.
*
*
Untold Story of Enigma Code-Breaker — The Ministry of Defence (U.K.)
External links
Gordon Corera, Poland's overlooked Enigma codebreakers, BBC News Magazine, 4 July 2014Long-running list of places with Enigma machines on displayBletchley Park National Code Centre Home of the British codebreakers during the Second World War
Enigma machines on the Crypto Museum Web site
*
ttp://www.cgisecurity.net/2008/04/getting-to-see-an-enigma-machine-at-rsa-2008-.html Enigma Pictures and Demonstration by NSA Employee at RSAKenngruppenheftProcess of building an Enigma M4 replica
Breaking German Navy Ciphers
{{Authority control
Broken stream ciphers
Cryptographic hardware
Encryption devices
Military communications of Germany
Military equipment introduced in the 1920s
Products introduced in 1918
Rotor machines
Signals intelligence of World War II
World War II military equipment of Germany
 The rotors (alternatively ''wheels'' or ''drums'', ''Walzen'' in German) form the heart of an Enigma machine. Each rotor is a disc approximately in diameter made from Ebonite or
The rotors (alternatively ''wheels'' or ''drums'', ''Walzen'' in German) form the heart of an Enigma machine. Each rotor is a disc approximately in diameter made from Ebonite or  Each rotor contains one or more notches that control rotor stepping. In the military variants, the notches are located on the alphabet ring.
The Army and Air Force Enigmas were used with several rotors, initially three. On 15 December 1938, this changed to five, from which three were chosen for a given session. Rotors were marked with
Each rotor contains one or more notches that control rotor stepping. In the military variants, the notches are located on the alphabet ring.
The Army and Air Force Enigmas were used with several rotors, initially three. On 15 December 1938, this changed to five, from which three were chosen for a given session. Rotors were marked with  The advancement of a rotor other than the left-hand one was called a ''turnover'' by the British. This was achieved by a ratchet and pawl mechanism. Each rotor had a ratchet with 26 teeth and every time a key was pressed, the set of spring-loaded pawls moved forward in unison, trying to engage with a ratchet. The alphabet ring of the rotor to the right normally prevented this. As this ring rotated with its rotor, a notch machined into it would eventually align itself with the pawl, allowing it to engage with the ratchet, and advance the rotor on its left. The right-hand pawl, having no rotor and ring to its right, stepped its rotor with every key depression. For a single-notch rotor in the right-hand position, the middle rotor stepped once for every 26 steps of the right-hand rotor. Similarly for rotors two and three. For a two-notch rotor, the rotor to its left would turn over twice for each rotation.
The first five rotors to be introduced (I–V) contained one notch each, while the additional naval rotors VI, VII and VIII each had two notches. The position of the notch on each rotor was determined by the letter ring which could be adjusted in relation to the core containing the interconnections. The points on the rings at which they caused the next wheel to move were as follows.
The design also included a feature known as ''double-stepping''. This occurred when each pawl aligned with both the ratchet of its rotor and the rotating notched ring of the neighbouring rotor. If a pawl engaged with a ratchet through alignment with a notch, as it moved forward it pushed against both the ratchet and the notch, advancing both rotors. In a three-rotor machine, double-stepping affected rotor two only. If, in moving forward, the ratchet of rotor three was engaged, rotor two would move again on the subsequent keystroke, resulting in two consecutive steps. Rotor two also pushes rotor one forward after 26 steps, but since rotor one moves forward with every keystroke anyway, there is no double-stepping. This double-stepping caused the rotors to deviate from
The advancement of a rotor other than the left-hand one was called a ''turnover'' by the British. This was achieved by a ratchet and pawl mechanism. Each rotor had a ratchet with 26 teeth and every time a key was pressed, the set of spring-loaded pawls moved forward in unison, trying to engage with a ratchet. The alphabet ring of the rotor to the right normally prevented this. As this ring rotated with its rotor, a notch machined into it would eventually align itself with the pawl, allowing it to engage with the ratchet, and advance the rotor on its left. The right-hand pawl, having no rotor and ring to its right, stepped its rotor with every key depression. For a single-notch rotor in the right-hand position, the middle rotor stepped once for every 26 steps of the right-hand rotor. Similarly for rotors two and three. For a two-notch rotor, the rotor to its left would turn over twice for each rotation.
The first five rotors to be introduced (I–V) contained one notch each, while the additional naval rotors VI, VII and VIII each had two notches. The position of the notch on each rotor was determined by the letter ring which could be adjusted in relation to the core containing the interconnections. The points on the rings at which they caused the next wheel to move were as follows.
The design also included a feature known as ''double-stepping''. This occurred when each pawl aligned with both the ratchet of its rotor and the rotating notched ring of the neighbouring rotor. If a pawl engaged with a ratchet through alignment with a notch, as it moved forward it pushed against both the ratchet and the notch, advancing both rotors. In a three-rotor machine, double-stepping affected rotor two only. If, in moving forward, the ratchet of rotor three was engaged, rotor two would move again on the subsequent keystroke, resulting in two consecutive steps. Rotor two also pushes rotor one forward after 26 steps, but since rotor one moves forward with every keystroke anyway, there is no double-stepping. This double-stepping caused the rotors to deviate from  With the exception of models ''A'' and ''B'', the last rotor came before a 'reflector' (German: ''Umkehrwalze'', meaning 'reversal rotor'), a patented feature unique to Enigma among the period's various rotor machines. The reflector connected outputs of the last rotor in pairs, redirecting current back through the rotors by a different route. The reflector ensured that Enigma would be self-reciprocal; thus, with two identically configured machines, a message could be encrypted on one and decrypted on the other, without the need for a bulky mechanism to switch between encryption and decryption modes. The reflector allowed a more compact design, but it also gave Enigma the property that no letter ever encrypted to itself. This was a severe cryptological flaw that was subsequently exploited by codebreakers.
In Model 'C', the reflector could be inserted in one of two different positions. In Model 'D', the reflector could be set in 26 possible positions, although it did not move during encryption. In the ''Abwehr'' Enigma, the reflector stepped during encryption in a manner similar to the other wheels.
In the German Army and Air Force Enigma, the reflector was fixed and did not rotate; there were four versions. The original version was marked 'A', and was replaced by ''Umkehrwalze B'' on 1 November 1937. A third version, ''Umkehrwalze C'' was used briefly in 1940, possibly by mistake, and was solved by Hut 6. The fourth version, first observed on 2 January 1944, had a rewireable reflector, called ''Umkehrwalze D'', nick-named Uncle Dick by the British, allowing the Enigma operator to alter the connections as part of the key settings.
With the exception of models ''A'' and ''B'', the last rotor came before a 'reflector' (German: ''Umkehrwalze'', meaning 'reversal rotor'), a patented feature unique to Enigma among the period's various rotor machines. The reflector connected outputs of the last rotor in pairs, redirecting current back through the rotors by a different route. The reflector ensured that Enigma would be self-reciprocal; thus, with two identically configured machines, a message could be encrypted on one and decrypted on the other, without the need for a bulky mechanism to switch between encryption and decryption modes. The reflector allowed a more compact design, but it also gave Enigma the property that no letter ever encrypted to itself. This was a severe cryptological flaw that was subsequently exploited by codebreakers.
In Model 'C', the reflector could be inserted in one of two different positions. In Model 'D', the reflector could be set in 26 possible positions, although it did not move during encryption. In the ''Abwehr'' Enigma, the reflector stepped during encryption in a manner similar to the other wheels.
In the German Army and Air Force Enigma, the reflector was fixed and did not rotate; there were four versions. The original version was marked 'A', and was replaced by ''Umkehrwalze B'' on 1 November 1937. A third version, ''Umkehrwalze C'' was used briefly in 1940, possibly by mistake, and was solved by Hut 6. The fourth version, first observed on 2 January 1944, had a rewireable reflector, called ''Umkehrwalze D'', nick-named Uncle Dick by the British, allowing the Enigma operator to alter the connections as part of the key settings.
 The plugboard (''Steckerbrett'' in German) permitted variable wiring that could be reconfigured by the operator. It was introduced on German Army versions in 1928, and was soon adopted by the '' Reichsmarine'' (German Navy). The plugboard contributed more cryptographic strength than an extra rotor, as it had 150 trillion possible settings (see below). Enigma without a plugboard (known as ''unsteckered Enigma'') could be solved relatively straightforwardly using hand methods; these techniques were generally defeated by the plugboard, driving Allied cryptanalysts to develop special machines to solve it.
A cable placed onto the plugboard connected letters in pairs; for example, ''E'' and ''Q'' might be a steckered pair. The effect was to swap those letters before and after the main rotor scrambling unit. For example, when an operator pressed ''E'', the signal was diverted to ''Q'' before entering the rotors. Up to 13 steckered pairs might be used at one time, although only 10 were normally used.
Current flowed from the keyboard through the plugboard, and proceeded to the entry-rotor or ''Eintrittswalze''. Each letter on the plugboard had two jacks. Inserting a plug disconnected the upper jack (from the keyboard) and the lower jack (to the entry-rotor) of that letter. The plug at the other end of the crosswired cable was inserted into another letter's jacks, thus switching the connections of the two letters.
The plugboard (''Steckerbrett'' in German) permitted variable wiring that could be reconfigured by the operator. It was introduced on German Army versions in 1928, and was soon adopted by the '' Reichsmarine'' (German Navy). The plugboard contributed more cryptographic strength than an extra rotor, as it had 150 trillion possible settings (see below). Enigma without a plugboard (known as ''unsteckered Enigma'') could be solved relatively straightforwardly using hand methods; these techniques were generally defeated by the plugboard, driving Allied cryptanalysts to develop special machines to solve it.
A cable placed onto the plugboard connected letters in pairs; for example, ''E'' and ''Q'' might be a steckered pair. The effect was to swap those letters before and after the main rotor scrambling unit. For example, when an operator pressed ''E'', the signal was diverted to ''Q'' before entering the rotors. Up to 13 steckered pairs might be used at one time, although only 10 were normally used.
Current flowed from the keyboard through the plugboard, and proceeded to the entry-rotor or ''Eintrittswalze''. Each letter on the plugboard had two jacks. Inserting a plug disconnected the upper jack (from the keyboard) and the lower jack (to the entry-rotor) of that letter. The plug at the other end of the crosswired cable was inserted into another letter's jacks, thus switching the connections of the two letters.
 Other features made various Enigma machines more secure or more convenient.
Other features made various Enigma machines more secure or more convenient.
 In 1944, the ''Luftwaffe'' introduced a plugboard switch, called the ''Uhr'' (clock), a small box containing a switch with 40 positions. It replaced the standard plugs. After connecting the plugs, as determined in the daily key sheet, the operator turned the switch into one of the 40 positions, each producing a different combination of plug wiring. Most of these plug connections were, unlike the default plugs, not pair-wise. In one switch position, the ''Uhr'' did not swap letters, but simply emulated the 13 stecker wires with plugs.
In 1944, the ''Luftwaffe'' introduced a plugboard switch, called the ''Uhr'' (clock), a small box containing a switch with 40 positions. It replaced the standard plugs. After connecting the plugs, as determined in the daily key sheet, the operator turned the switch into one of the 40 positions, each producing a different combination of plug wiring. Most of these plug connections were, unlike the default plugs, not pair-wise. In one switch position, the ''Uhr'' did not swap letters, but simply emulated the 13 stecker wires with plugs.

 In use, the Enigma required a list of daily key settings and auxiliary documents. In German military practice, communications were divided into separate networks, each using different settings. These communication nets were termed ''keys'' at
In use, the Enigma required a list of daily key settings and auxiliary documents. In German military practice, communications were divided into separate networks, each using different settings. These communication nets were termed ''keys'' at  One of the earliest ''indicator procedures'' for the Enigma was cryptographically flawed and allowed Polish cryptanalysts to make the initial breaks into the plugboard Enigma. The procedure had the operator set his machine in accordance with the secret settings that all operators on the net shared. The settings included an initial position for the rotors (the ''Grundstellung''), say, ''AOH''. The operator turned his rotors until ''AOH'' was visible through the rotor windows. At that point, the operator chose his own arbitrary starting position for the message he would send. An operator might select ''EIN'', and that became the ''message setting'' for that encryption session. The operator then typed ''EIN'' into the machine twice, this producing the encrypted indicator, for example ''XHTLOA''. This was then transmitted, at which point the operator would turn the rotors to his message settings, ''EIN'' in this example, and then type the plaintext of the message.
At the receiving end, the operator set the machine to the initial settings (''AOH'') and typed in the first six letters of the message (''XHTLOA''). In this example, ''EINEIN'' emerged on the lamps, so the operator would learn the ''message setting'' that the sender used to encrypt this message. The receiving operator would set his rotors to ''EIN'', type in the rest of the ciphertext, and get the deciphered message.
This indicator scheme had two weaknesses. First, the use of a global initial position (''Grundstellung'') meant all message keys used the same polyalphabetic substitution. In later indicator procedures, the operator selected his initial position for encrypting the indicator and sent that initial position in the clear. The second problem was the repetition of the indicator, which was a serious security flaw. The message setting was encoded twice, resulting in a relation between first and fourth, second and fifth, and third and sixth character. These security flaws enabled the Polish Cipher Bureau to break into the pre-war Enigma system as early as 1932. The early indicator procedure was subsequently described by German cryptanalysts as the "faulty indicator technique".
During World War II, codebooks were only used each day to set up the rotors, their ring settings and the plugboard. For each message, the operator selected a random start position, let's say ''WZA'', and a random message key, perhaps ''SXT''. He moved the rotors to the ''WZA'' start position and encoded the message key ''SXT''. Assume the result was ''UHL''. He then set up the message key, ''SXT'', as the start position and encrypted the message. Next, he transmitted the start position, ''WZA'', the encoded message key, ''UHL'', and then the ciphertext. The receiver set up the start position according to the first trigram, ''WZA'', and decoded the second trigram, ''UHL'', to obtain the ''SXT'' message setting. Next, he used this ''SXT'' message setting as the start position to decrypt the message. This way, each ground setting was different and the new procedure avoided the security flaw of double encoded message settings.
This procedure was used by ''Heer'' and ''Luftwaffe'' only. The ''Kriegsmarine'' procedures for sending messages with the Enigma were far more complex and elaborate. Prior to encryption the message was encoded using the '' Kurzsignalheft'' code book. The ''Kurzsignalheft'' contained tables to convert sentences into four-letter groups. A great many choices were included, for example, logistic matters such as refuelling and rendezvous with supply ships, positions and grid lists, harbour names, countries, weapons, weather conditions, enemy positions and ships, date and time tables. Another codebook contained the '' Kenngruppen'' and ''Spruchschlüssel'': the key identification and message key.
One of the earliest ''indicator procedures'' for the Enigma was cryptographically flawed and allowed Polish cryptanalysts to make the initial breaks into the plugboard Enigma. The procedure had the operator set his machine in accordance with the secret settings that all operators on the net shared. The settings included an initial position for the rotors (the ''Grundstellung''), say, ''AOH''. The operator turned his rotors until ''AOH'' was visible through the rotor windows. At that point, the operator chose his own arbitrary starting position for the message he would send. An operator might select ''EIN'', and that became the ''message setting'' for that encryption session. The operator then typed ''EIN'' into the machine twice, this producing the encrypted indicator, for example ''XHTLOA''. This was then transmitted, at which point the operator would turn the rotors to his message settings, ''EIN'' in this example, and then type the plaintext of the message.
At the receiving end, the operator set the machine to the initial settings (''AOH'') and typed in the first six letters of the message (''XHTLOA''). In this example, ''EINEIN'' emerged on the lamps, so the operator would learn the ''message setting'' that the sender used to encrypt this message. The receiving operator would set his rotors to ''EIN'', type in the rest of the ciphertext, and get the deciphered message.
This indicator scheme had two weaknesses. First, the use of a global initial position (''Grundstellung'') meant all message keys used the same polyalphabetic substitution. In later indicator procedures, the operator selected his initial position for encrypting the indicator and sent that initial position in the clear. The second problem was the repetition of the indicator, which was a serious security flaw. The message setting was encoded twice, resulting in a relation between first and fourth, second and fifth, and third and sixth character. These security flaws enabled the Polish Cipher Bureau to break into the pre-war Enigma system as early as 1932. The early indicator procedure was subsequently described by German cryptanalysts as the "faulty indicator technique".
During World War II, codebooks were only used each day to set up the rotors, their ring settings and the plugboard. For each message, the operator selected a random start position, let's say ''WZA'', and a random message key, perhaps ''SXT''. He moved the rotors to the ''WZA'' start position and encoded the message key ''SXT''. Assume the result was ''UHL''. He then set up the message key, ''SXT'', as the start position and encrypted the message. Next, he transmitted the start position, ''WZA'', the encoded message key, ''UHL'', and then the ciphertext. The receiver set up the start position according to the first trigram, ''WZA'', and decoded the second trigram, ''UHL'', to obtain the ''SXT'' message setting. Next, he used this ''SXT'' message setting as the start position to decrypt the message. This way, each ground setting was different and the new procedure avoided the security flaw of double encoded message settings.
This procedure was used by ''Heer'' and ''Luftwaffe'' only. The ''Kriegsmarine'' procedures for sending messages with the Enigma were far more complex and elaborate. Prior to encryption the message was encoded using the '' Kurzsignalheft'' code book. The ''Kurzsignalheft'' contained tables to convert sentences into four-letter groups. A great many choices were included, for example, logistic matters such as refuelling and rendezvous with supply ships, positions and grid lists, harbour names, countries, weapons, weather conditions, enemy positions and ships, date and time tables. Another codebook contained the '' Kenngruppen'' and ''Spruchschlüssel'': the key identification and message key.
 On 23 February 1918, Arthur Scherbius applied for a
On 23 February 1918, Arthur Scherbius applied for a  There was also a large, eight-rotor printing model, the ''Enigma H'', called ''Enigma II'' by the ''
There was also a large, eight-rotor printing model, the ''Enigma H'', called ''Enigma II'' by the '' In the United States, Enigma machines can be seen at the
In the United States, Enigma machines can be seen at the  In Canada, a Swiss Army issue Enigma-K, is in Calgary, Alberta. It is on permanent display at the Naval Museum of Alberta inside the Military Museums of Calgary. A four-rotor Enigma machine is on display at the Military Communications and Electronics Museum at Canadian Forces Base (CFB) Kingston in
In Canada, a Swiss Army issue Enigma-K, is in Calgary, Alberta. It is on permanent display at the Naval Museum of Alberta inside the Military Museums of Calgary. A four-rotor Enigma machine is on display at the Military Communications and Electronics Museum at Canadian Forces Base (CFB) Kingston in  In November 2000, an antiques dealer named Dennis Yates was arrested after telephoning ''
In November 2000, an antiques dealer named Dennis Yates was arrested after telephoning ''