|
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted. Overview With the advent of computing, the term ''plaintext'' expanded beyond human-readable documents to mean any data, including binary files, in a form that can be viewed or used without requiring a key or other decryption device. Information—a message, document, file, etc.—if to be communicated or stored in an unencrypted form is referred to as plaintext. Plaintext is used as input to an encryption algorithm; the output is usually termed ciphertext, particularly when the algorithm is a cipher. Codetext is less often used, and almost always only when the algorithm involved is actually a code. Some systems use multiple layers of encryption, with the output of one encryption algorithm becoming "plaintext" input for the next. Secure handling Insecure handling of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known Plaintext
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Codetext
In cryptology, a code is a method used to Encryption, encrypt a message that operates at the level of meaning; that is, words or phrases are converted into something else. A code might transform "change" into "CVGDK" or "cocktail lounge". The U.S. National Security Agency defined a code as "A substitution cryptosystem in which the plaintext elements are primarily words, phrases, or sentences, and the code equivalents (called "code groups") typically consist of letters or digits (or both) in otherwise meaningless combinations of identical length."A History of U.S. Communications Security; the David G. Boak Lectures , National Security Agency (NSA), Volumes I, 1973, Volumes II 1981, partially released 2008, additional portions declassified October 14, 201 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Remanence
Data remanence is the residual representation of digital data that remains even after attempts have been made to remove or erase the data. This residue may result from data being left intact by a nominal file deletion operation, by reformatting of storage media that does not remove data previously written to the media, or through physical properties of the storage media that allow previously written data to be recovered. Data remanence may make inadvertent disclosure of sensitive information possible should the storage media be released into an uncontrolled environment (''e.g.'', thrown in the bin (trash) or lost). Various techniques have been developed to counter data remanence. These techniques are classified as clearing, purging/sanitizing, or destruction. Specific methods include overwriting, degaussing, encryption, and media destruction. Effective application of countermeasures can be complicated by several factors, including media that are inaccessible, media that c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peter Gutmann (computer Scientist)
Peter Claus Gutmann is a computer scientist in the Department of Computer Science at the University of Auckland, Auckland, New Zealand. He has a Ph.D. in computer science from the University of Auckland. His Ph.D. thesis and a book based on the thesis were about a cryptographic security architecture. He is interested in computer security issues, including security architecture, security usability (or more usually the lack thereof), and hardware security; he has discovered several flaws in publicly released cryptosystems and protocols. He is the developer of the cryptlib open source software security library and contributed to PGP version 2. In 1994 he developed the Secure FileSystem (SFS). He is also known for his analysis of data deletion on electronic memory media, magnetic and otherwise, and devised the Gutmann method for erasing data from a hard drive more or less securely. These analyses have gained great popularity, although they are based on numerous inaccuracies an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keydrives
A flash drive (also thumb drive, memory stick, and pen drive/pendrive) is a data storage device that includes flash memory with an integrated USB interface. A typical USB drive is removable, rewritable, and smaller than an optical disc, and usually weighs less than . Since first offered for sale in late 2000, the storage capacities of USB drives range from 8 megabytes to 256 gigabytes (GB), 512 GB and 1 terabyte (TB). As of 2024, 4 TB flash drives were the largest currently in production. Some allow up to 100,000 write/erase cycles, depending on the exact type of memory chip used, and are thought to physically last between 10 and 100 years under normal circumstances ( shelf storage time). Common uses of USB flash drives are for storage, supplementary back-ups, and transferring of computer files. Compared with floppy disks or CDs, they are smaller, faster, have significantly more capacity, and are more durable due to a lack of moving parts. Additionally, they ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Padding (cryptography)
In cryptography, padding is any of a number of distinct practices which all include adding data to the beginning, middle, or end of a message prior to encryption. In classical cryptography, padding may include adding nonsense phrases to a message to obscure the fact that many messages end in predictable ways, e.g. ''sincerely yours''. Classical cryptography Official messages often start and end in predictable ways: ''My dear ambassador, Weather report, Sincerely yours'', etc. The primary use of padding with classical ciphers is to prevent the cryptanalyst from using that predictability to find known plaintext that aids in breaking the encryption. Random length padding also prevents an attacker from knowing the exact length of the plaintext message. A famous example of classical padding which caused a great misunderstanding is " the world wonders" incident, which nearly caused an Allied loss at the World War II Battle off Samar, part of the larger Battle of Leyte Gulf. In that e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chosen Plaintext
Chosen or The Chosen may refer to: Books *The Chosen (Potok novel), ''The Chosen'' (Potok novel), a 1967 novel by Chaim Potok * ''The Chosen'', a 1997 novel by L. J. Smith (author), L. J. Smith *The Chosen (Pinto novel), ''The Chosen'' (Pinto novel), a 1999 novel by Ricardo Pinto *The Chosen (Karabel book), ''The Chosen'' (Karabel book), a book by Jerome Karabel *Chosen (Dekker novel), ''Chosen'' (Dekker novel), a 2007 novel by Ted Dekker *Chosen (Cast novel), ''Chosen'' (Cast novel), a novel in the ''House of Night'' fantasy series *Chosen (Image Comics), ''Chosen'' (Image Comics), a comic book series by Mark Millar Film and television *''Holocaust 2000'', also released as ''The Chosen'', a 1977 horror film starring Kirk Douglas *The Chosen (1981 film), ''The Chosen'' (1981 film), a film based on Potok's novel *The Chosen (2015 film), ''The Chosen'' (2015 film), a film starring YouTube personality Kian Lawley *The Chosen (2016 film), ''The Chosen'' (2016 film), by Antonio Chavarr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Loss Of United Kingdom Child Benefit Data (2007)
Loss may refer to: * Economic loss * Grief, an emotional response to loss ** Animal loss, grief over the loss of an animal Mathematics, science, and technology * Angular misalignment loss, power loss caused by the deviation from optimum angular alignment * Bridging loss, the loss that results when an impedance is connected across a transmission line * Coupling loss, the loss that occurs when energy is transferred from one circuit, optical device, or medium to another * Insertion loss, the decrease in transmitted signal power resulting from the insertion of a device in a transmission line or optical fiber * Dielectric loss, a dielectric material's inherent dissipation of electromagnetic energy * Loss function, in statistics, a function representing the cost associated with an event * Path loss, the attenuation undergone by an electromagnetic wave in transit from a transmitter to a receiver ** Free-space path loss, the loss in signal strength that would result if all influences wer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Encryption
Disk encryption is a technology which protects information by converting it into code that cannot be deciphered easily by unauthorized people or processes. Disk encryption uses disk encryption software or disk encryption hardware, hardware to encryption, encrypt every bit of data that goes on a disk storage, disk or disk volume (computing), volume. It is used to prevent unauthorized access to data storage. The expression ''full disk encryption (FDE)'' (or ''whole disk encryption'') signifies that everything on the disk is encrypted, but the master boot record (MBR), or similar area of a bootable disk, with code that starts the operating system loading sequence, is not encrypted. Some hardware-based full disk encryption systems can truly encrypt an entire boot disk, including the MBR. Transparent encryption Transparent encryption, also known as real-time encryption and on-the-fly encryption (OTFE), is a method used by some disk encryption software. "Transparent" refers to the fact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
British Secret Service
The Secret Intelligence Service (SIS), commonly known as MI6 (MI numbers, Military Intelligence, Section 6), is the foreign intelligence service of the United Kingdom, tasked mainly with the covert overseas collection and analysis of Human intelligence (intelligence gathering), human intelligence on foreign nationals in support of its Five Eyes partners. SIS is one of the British intelligence agencies and the Chief of the Secret Intelligence Service ("C") is directly accountable to the Foreign Secretary (United Kingdom), Foreign Secretary. Formed in 1909 as the foreign section of the Secret Service Bureau, the section grew greatly during the World War I, First World War, officially adopting its current name around 1920. The name "MI6" originated as a convenient label during the World War II, Second World War, when SIS was known by many names. It is still commonly used today. The existence of SIS was not officially acknowledged until 1994. That year the Intelligence Services A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
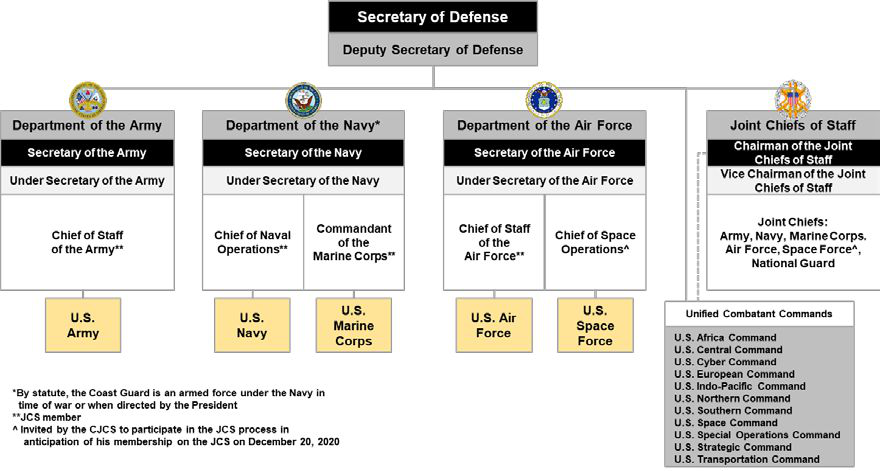
US Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an executive department of the U.S. federal government charged with coordinating and supervising the six U.S. armed services: the Army, Navy, Marines, Air Force, Space Force, the Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provide the military forces needed to deter war and ensure our nation's security". The current Secretary of Defense is Pete Hegseth. The Department of Defense is headed by the secretary of defense, a cabinet-level head who reports directly to the president of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |