|
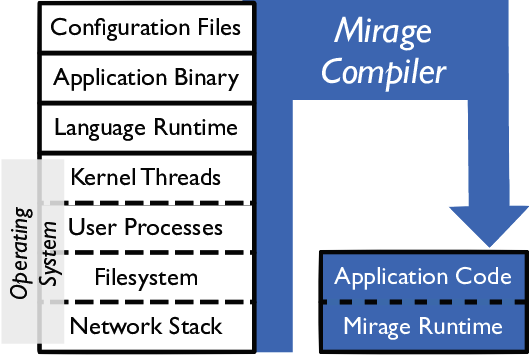
Unikernel Mirage Example
A unikernel is a specialised, single address space machine image constructed by using library operating systems. A developer selects, from a modular stack, the minimal set of libraries which correspond to the OS constructs required for the application to run. These libraries are then compiled with the application and configuration code to build sealed, fixed-purpose images (unikernels) which run directly on a hypervisor or hardware without an intervening OS such as Linux or Windows. The first such systems were Exokernel and Nemesis in the late 1990s. Design In a library operating system, protection boundaries are pushed to the lowest hardware layers, resulting in: # a set of libraries that implement mechanisms such as those needed to drive hardware or talk network protocols; # a set of policies that enforce access control and isolation in the application layer. The library OS architecture has several advantages and disadvantages compared with conventional OS designs. One o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtualization
In computing, virtualization or virtualisation (sometimes abbreviated v12n, a numeronym) is the act of creating a virtual (rather than actual) version of something at the same abstraction level, including virtual computer hardware platforms, storage devices, and computer network resources. Virtualization began in the 1960s, as a method of logically dividing the system resources provided by mainframe computers between different applications. An early and successful example is IBM CP/CMS. The control program CP provided each user with a simulated stand-alone System/360 computer. Since then, the meaning of the term has broadened. Hardware virtualization ''Hardware virtualization'' or ''platform virtualization'' refers to the creation of a virtual machine that acts like a real computer with an operating system. Software executed on these virtual machines is separated from the underlying hardware resources. For example, a computer that is running Arch Linux may host a virtual ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rump Kernel
The NetBSD rump kernel is the first implementation of the "anykernel" concept where device driver, drivers either can be compiled into or run in the monolithic kernel or in user space on top of a light-weight kernel. The NetBSD drivers can be used on top of the rump kernel on a wide range of POSIX operating systems, such as the Hurd, Linux, NetBSD, DragonFly BSD, Solaris (operating system), Solaris kernels and even Cygwin, along with the file system utilities built with the rump libraries. The rump kernels can also run without POSIX directly on top of the Xen hypervisor, an L4 microkernel using the Genode, Genode OS Framework or even on "OS-less" bare machine, bare metal. Anykernel An anykernel is different in concept from microkernels, exokernels, Separation kernel, partitioned kernels or hybrid kernels in that it tries to preserve the advantages of a monolithic kernel, while still enabling the faster driver development and added security in user space. The "anykernel" concept r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Container (virtualization)
OS-level virtualization is an operating system (OS) paradigm in which the kernel allows the existence of multiple isolated user space instances, called ''containers'' (LXC, Solaris containers, Docker, Podman), ''zones'' ( Solaris containers), ''virtual private servers'' ( OpenVZ), ''partitions'', ''virtual environments'' (VEs), ''virtual kernels'' ( DragonFly BSD), or ''jails'' ( FreeBSD jail or chroot jail). Such instances may look like real computers from the point of view of programs running in them. A computer program running on an ordinary operating system can see all resources (connected devices, files and folders, network shares, CPU power, quantifiable hardware capabilities) of that computer. However, programs running inside of a container can only see the container's contents and devices assigned to the container. On Unix-like operating systems, this feature can be seen as an advanced implementation of the standard chroot mechanism, which changes the apparent roo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microkernel
In computer science, a microkernel (often abbreviated as μ-kernel) is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system (OS). These mechanisms include low-level address space management, thread management, and inter-process communication (IPC). If the hardware provides multiple rings or CPU modes, the microkernel may be the only software executing at the most privileged level, which is generally referred to as supervisor or kernel mode. Traditional operating system functions, such as device drivers, protocol stacks and file systems, are typically removed from the microkernel itself and are instead run in user space. In terms of the source code size, microkernels are often smaller than monolithic kernels. The MINIX 3 microkernel, for example, has only approximately 12,000 lines of code. History Microkernels trace their roots back to Danish computer pioneer Per Brinch Hansen and his tenure in Danish computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microservices
A microservice architecture – a variant of the service-oriented architecture structural style – is an architectural pattern that arranges an application as a collection of loosely-coupled, fine-grained services, communicating through lightweight protocols. One of its goals is that teams can develop and deploy their services independently of others. This is achieved by the reduction of several dependencies in the code base, allowing for developers to evolve their services with limited restrictions from users, and for additional complexity to be hidden from users. As a consequence, organizations are able to develop software with fast growth and size, as well as use off-the-shelf services more easily. Communication requirements are reduced. These benefits come at a cost to maintaining the decoupling. Interfaces need to be designed carefully and treated as a public API. One technique that is used is having multiple interfaces on the same service, or multiple versions of the s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service Oriented Architecture
In software engineering, service-oriented architecture (SOA) is an architectural style that focuses on discrete services instead of a monolithic design. By consequence, it is also applied in the field of software design where services are provided to the other components by application components, through a communication protocol over a network. A service is a discrete unit of functionality that can be accessed remotely and acted upon and updated independently, such as retrieving a credit card statement online. SOA is also intended to be independent of vendors, products and technologies. Service orientation is a way of thinking in terms of services and service-based development and the outcomes of services. A service has four properties according to one of many definitions of SOA: # It logically represents a repeatable business activity with a specified outcome. # It is self-contained. # It is a black box for its consumers, meaning the consumer does not have to be aware of the se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Surface
The attack surface of a software environment is the sum of the different points (for " attack vectors") where an unauthorized user (the "attacker") can try to enter data to or extract data from an environment. Keeping the attack surface as small as possible is a basic security measure. Elements of an attack surface Worldwide digital change has accelerated the size, scope, and composition of an organization’s attack surface. The size of an attack surface may fluctuate over time, adding and subtracting assets and digital systems (e.g. websites, hosts, cloud and mobile apps, etc). Attack surface sizes can change rapidly as well. Digital assets eschew the physical requirements of traditional network devices, servers, data centers, and on-premise networks. This leads to attack surfaces changing rapidly, based on the organization’s needs and the availability of digital services to accomplish it. Attack surface scope also varies from organization to organization. With the rise ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-copy
"Zero-copy" describes computer operations in which the CPU does not perform the task of copying data from one memory area to another or in which unnecessary data copies are avoided. This is frequently used to save CPU cycles and memory bandwidth in many time consuming tasks, such as when transmitting a file at high speed over a network, etc., thus improving performances of programs (processes) executed by a computer. Principle Zero-copy programming techniques can be used when exchanging data within a user space process (i.e. between two or more threads, etc.) and/or between two or more processes (see also producer–consumer problem) and/or when data has to be accessed / copied / moved inside kernel space or between a user space process and kernel space portions of operating systems (OS). Usually when a user space process has to execute system operations like reading or writing data from/to a device (i.e. a disk, a NIC, etc.) through their high level software interfaces ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Single Address Space Operating System
In computer science, a single address space operating system (or SASOS) is an operating system that provides only one globally shared address space for all processes. In a single address space operating system, numerically identical (virtual memory) logical addresses in different processes all refer to exactly the same byte of data. Single address-space operating systems offer certain advantages. In a traditional OS with private per-process address space, memory protection is based on address space boundaries ("address space isolation"). Single address-space operating systems use a different approach for memory protection that is just as strong. One advantage is that the same virtual-to-physical map page table can be used with every process (and in some SASOS, the kernel as well). This makes context switches on a SASOS faster than on operating systems that must change the page table and flush the TLB caches on every context switch. SASOS projects include the following: * Amiga fa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Context Switch
In computing, a context switch is the process of storing the state of a process or thread, so that it can be restored and resume execution at a later point, and then restoring a different, previously saved, state. This allows multiple processes to share a single central processing unit (CPU), and is an essential feature of a multitasking operating system. The precise meaning of the phrase "context switch" varies. In a multitasking context, it refers to the process of storing the system state for one task, so that task can be paused and another task resumed. A context switch can also occur as the result of an interrupt, such as when a task needs to access disk storage, freeing up CPU time for other tasks. Some operating systems also require a context switch to move between user mode and kernel mode tasks. The process of context switching can have a negative impact on system performance. Cost Context switches are usually computationally intensive, and much of the design of op ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nemesis (operating System)
Nemesis was an operating system that was designed by the University of Cambridge, the University of Glasgow, the Swedish Institute of Computer Science and Citrix Systems. Nemesis was conceived with multimedia uses in mind. It was designed with a small lightweight kernel, using shared libraries to perform functions that most operating systems perform in the kernel. This reduces the processing that is performed in the kernel on behalf of application processes, transferring the activity to the processes themselves and facilitating accounting for resource usage. The ISAs that Nemesis supports include x86 ( Intel i486, Pentium, Pentium Pro, and Pentium II), Alpha and ARM (StrongARM SA–110). Nemesis also runs on evaluation boards (21064 and 21164). See also * Exokernel * Xen Xen (pronounced ) is a type-1 hypervisor, providing services that allow multiple computer operating systems to execute on the same computer hardware concurrently. It was originally developed by the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |