|
Prolexic
Prolexic Technologies was a US-based provider of security solutions for protecting websites, data centers, and enterprise IP applications from Distributed Denial of Service (DDoS) attacks at the network, transport, and application layers. It operated a DDoS mitigation platform and a global network of traffic scrubbing centers. Real-time monitoring and mitigation services were provided by a 24/7 security operations control center (SOCC). Prolexic indicated its DDoS mitigation services make websites, data centers and enterprise IP applications harder to take down via DDoS attacks. In February 2014, cybersecurity and cloud services company Akamai Technologies acquired Prolexic Technologies. History In 2003 Prolexic Technologies was founded by Barrett Lyon and was the subject of the book '' Fatal System Error'' by Joseph Menn. Prolexic protects organizations in the following markets: airlines/hospitality, e-commerce, energy, financial services, gambling, gaming, public sector, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Prolexic Logo
Prolexic Technologies was a US-based provider of security solutions for protecting websites, data centers, and enterprise IP applications from Distributed Denial of Service (DDoS) attacks at the Computer network, network, transport, and application layers. It operated a DDoS mitigation platform and a global network of traffic scrubbing centers. Real-time monitoring and mitigation services were provided by a 24/7 security operations control center (SOCC). Prolexic indicated its DDoS mitigation services make websites, data centers and enterprise IP applications harder to take down via DDoS attacks. In February 2014, cybersecurity and cloud services company Akamai Technologies acquired Prolexic Technologies. History In 2003 Prolexic Technologies was founded by Barrett Lyon and was the subject of the book ''Fatal System Error'' by Joseph Menn. Prolexic protects organizations in the following markets: airlines/hospitality, e-commerce, energy, financial services, gambling, online ga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Barrett Lyon
Barrett Gibson Lyon (born March 18, 1978) is an American Internet entrepreneur. Early life and education The son of a lawyer, Lyon was raised in Auburn, California. Although he initially struggled in school due to dyslexia, in middle school he became fascinated with computers. He soon found that the methods he used to overcome dyslexia allowed him to quickly gain an expert knowledge of computers. While in high school, he set up Linux servers to host webpages for friends and also managed his school's computer network. In 1995, while investigating a possible vulnerability in Network Solutions he accidentally caused AOL's website to go down for three days. After high school, Lyon enrolled at California State University, Sacramento and studied philosophy and photography. He has a wife named Simone Lyon and a daughter named Isabella Lyon. Opte Project Lyon is the creator of the Opte Project, which is an Internet mapping project that seeks to make an accurate representation of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack, as simply attempting to block a single source is insufficient because there are multiple sources. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade. Criminal perpetrators of DoS attacks ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
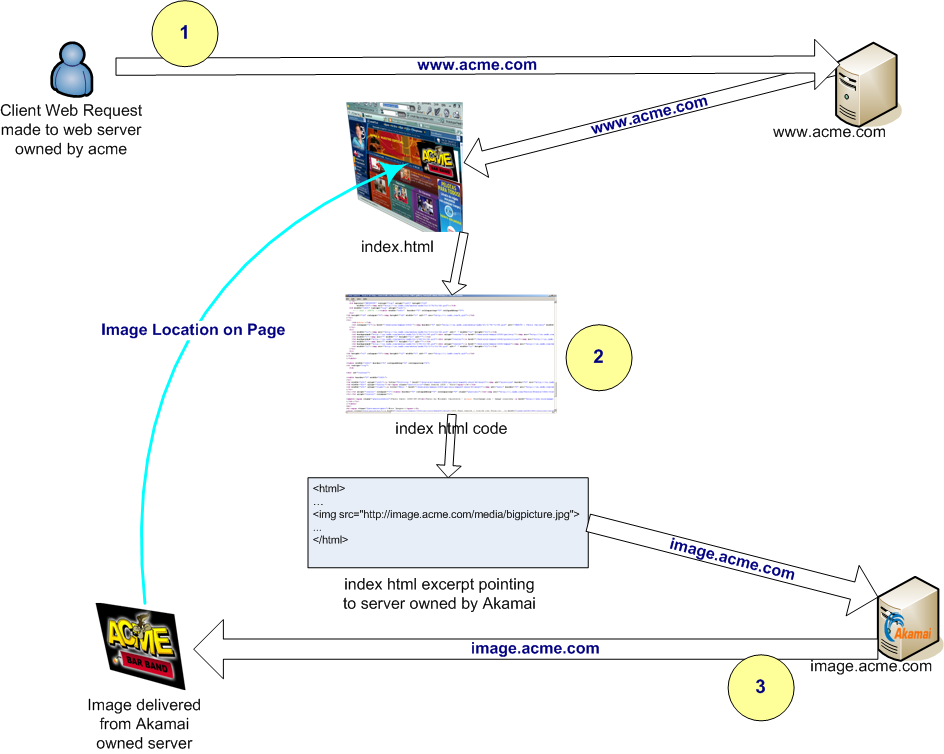
Akamai Technologies
Akamai Technologies, Inc. is an American content delivery networkJ. Dilley, B. Maggs, J. Parikh, H. Prokop, R. Sitaraman, and B. Weihl. (CDN), cybersecurity, and cloud service company, providing web and Internet security services. Akamai's Intelligent Edge Platform is a distributed computing platform. The company operates a network of servers worldwide and rents capacity of the servers to customers wanting increase effiency of their websites by using Akamai owned servers located near the user. When a user navigates to the URL of an Akamai customer, their browser is directed by Akamai's domain name systemKyle Schomp, Onkar Bhardwaj, Eymen Kurdoglu, Mashooq Muhaimen, and Ramesh K. Sitaraman. to a proximal edge server that can serve the requested content. Akamai's mapping system assigns each user to a proximal edge server using sophisticated algorithms such as stable matching and consistent hashing, enabling more reliable and faster web downloads. Further, Akamai implements DDoS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kennet Partners
Kennet Partners is a private equity investment firm that provides growth capital to software, Internet and technology-enabled business services companies in Europe and the US. Kennet Partners is headquartered in London, England, and has an office in San Francisco, California. The firm raised its fourth fund in 2014, bringing total capital under management to $700 million. Founding / history Kennet was founded in 1997 as Kennet Capital, a joint venture between technology investment bank Broadview International and asset management firm Electra Partners. In 2000, Kennet became a wholly owned subsidiary of Broadview. In 2003 the partners of Kennet completed a management buy-out and became independent. Kennet's first fund was primarily targeted at early-stage technology investments in Europe. With its second fund, Kennet began making growth equity investments in both Europe and the U.S., and this has remained the firm’s exclusive strategy to this day. Funds and investme ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-day Attack
A zero-day (also known as a 0-day) is a computer-software vulnerability previously unknown to those who should be interested in its mitigation, like the vendor of the target software. Until the vulnerability is mitigated, hackers can exploit it to adversely affect programs, data, additional computers or a network. An exploit taking advantage of a zero-day is called a zero-day exploit, or zero-day attack. The term "zero-day" originally referred to the number of days since a new piece of software was released to the public, so "zero-day software" was obtained by hacking into a developer's computer before release. Eventually the term was applied to the vulnerabilities that allowed this hacking, and to the number of days that the vendor has had to fix them. Once the vendors learn of the vulnerability, they will usually create patches or advise workarounds to mitigate it. The more recently that the vendor has become aware of the vulnerability, the more likely it is that no fix or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SYN Flood
A SYN flood is a form of denial-of-service attack in which an attacker rapidly initiates a connection to a server without finalizing the connection. The server has to spend resources waiting for half-opened connections, which can consume enough resources to make the system unresponsive to legitimate traffic. The packet that the attacker sends is the SYN packet, a part of TCP's three-way handshake used to establish a connection. Technical details When a client attempts to start a TCP connection to a server, the client and server exchange a series of messages which normally runs like this: #The client requests a connection by sending a SYN (''synchronize'') message to the server. #The server ''acknowledges'' this request by sending SYN-ACK back to the client. #The client responds with an ACK, and the connection is established. This is called the TCP three-way handshake, and is the foundation for every connection established using the TCP protocol. A SYN flood attack wor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Payment Card Industry Security Standards Council
The Payment Card Industry Security Standards Council (PCI SSC) was formed by American Express, Discover Financial Services, JCB International, MasterCard and Visa Inc. on September 7, 2006, with the goal of managing the ongoing evolution of the Payment Card Industry Data Security Standard. The Payment Card Industry Data Security Standard (PCI DSS) consists of twelve significant requirements including multiple sub-requirements, which contain numerous directives against which businesses may measure their own payment card security policies, procedures and guidelines. To address rising cybersecurity risks to the payment ecosystem, the PCI SSC currently manages 15 standards for payment security, which are variously applicable to payment card issuers, merchants and service providers, vendors and solution providers, and acquirers and processors. More recently, the PCI SSC has collaborated witEMVCo to provide the security requirements, testing procedures and assessor training to suppo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UDP Flood Attack
A UDP flood attack is a volumetric denial-of-service (DoS) attack using the User Datagram Protocol (UDP), a sessionless/connectionless computer networking protocol. Using UDP for denial-of-service attacks is not as straightforward as with the Transmission Control Protocol (TCP). However, a UDP flood attack can be initiated by sending a large number of UDP packets to random ports on a remote host. As a result, the distant host will: * Check for the application listening at that port; * See that no application listens at that port; * Reply with an ICMP Destination Unreachable packet. Thus, for a large number of UDP packets, the victimized system will be forced into sending many ICMP packets, eventually leading it to be unreachable by other clients. The attacker(s) may also spoof the IP address of the UDP packets, ensuring that the excessive ICMP return packets do not reach them, and anonymizing their network location(s). Most operating systems mitigate this part of the attack by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telstra
Telstra Group Limited is an Australian telecommunications company that builds and operates telecommunications networks and markets voice, mobile, internet access, pay television and other products and services. It is a member of the S&P/ASX 20 and Australia's largest telecommunications company by market share. Telstra is the largest wireless carrier in Australia, with 18.8 million subscribers as of 2020. Telstra has a long history in Australia, originating together with Australia Post as the Postmaster-General's Department upon federation in 1901. Telstra has transitioned from a state-owned enterprise to a fully privatised company and has recently focused on diversified products and emerging technologies. History Australia's telecommunications services were originally controlled by the Postmaster-General's Department (PMG), formed in 1901 as a result of Australian Federation. Prior to 1901, telecommunications were administered by each colony. On 1 July 1975, sepa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Level 3 Communications
Level 3 Communications was an American multinational telecommunications and Internet service provider company headquartered in Broomfield, Colorado. It ultimately became a part of CenturyLink (now Lumen Technologies), where Level 3 President and CEO Jeff Storey was installed as Chief Operating Officer, becoming CEO of CenturyLink one year later in a prearranged succession plan. Level 3 operated a Tier 1 network. The company provided core transport, IP, voice, video, and content delivery for medium-to-large Internet carriers in North America, Latin America, Europe, and selected cities in Asia. Level 3 was also the largest competitive local exchange carrier (CLEC) and the 3rd largest provider of fiber-optic internet access (based on coverage) in the United States. On October 31, 2016, CenturyLink announced an agreement to acquire Level 3 Communications in a cash and stock transaction. Level 3 became part of CenturyLink on November 1, 2017. History 1985 to 2000 In 1985, Pe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |