|
Offensive Programming
Offensive programming is a name used for the branch of defensive programming that expressly departs from defensive principles when dealing with errors resulting from software bugs. Although the name is a reaction to extreme interpretations of defensive programming, the two are not fundamentally in conflict. Rather, offensive programming adds an explicit priority of not tolerating errors in wrong places: the point where it departs from extreme interpretations of defensive programming is in preferring the presence of errors from within the program's line of defense to be blatantly obvious over the hypothetical safety benefit of tolerating them. This preference is also what justifies using assertions. Distinguishing errors The premise for offensive programming is to distinguish between expectable errors, coming from outside the program's line of defense, however improbable, versus preventable internal errors that shall not happen if all its software components behave as expected. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Defensive Programming
Defensive programming is a form of defensive design intended to develop programs that are capable of detecting potential security abnormalities and make predetermined responses. It ensures the continuing function of a piece of software under unforeseen circumstances. Defensive programming practices are often used where high availability, safety, or security is needed. Defensive programming is an approach to improve software and source code, in terms of: * General quality – reducing the number of software bugs and problems. * Making the source code comprehensible – the source code should be readable and understandable so it is approved in a code audit. * Making the software behave in a predictable manner despite unexpected inputs or user actions. Overly defensive programming, however, may safeguard against errors that will never be encountered, thus incurring run-time and maintenance costs. Secure programming Secure programming is the subset of defensive programming con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bug
A software bug is a design defect ( bug) in computer software. A computer program with many or serious bugs may be described as ''buggy''. The effects of a software bug range from minor (such as a misspelled word in the user interface) to severe (such as frequent crashing). In 2002, a study commissioned by the US Department of Commerce's National Institute of Standards and Technology concluded that "software bugs, or errors, are so prevalent and so detrimental that they cost the US economy an estimated $59 billion annually, or about 0.6 percent of the gross domestic product". Since the 1950s, some computer systems have been designed to detect or auto-correct various software errors during operations. History Terminology ''Mistake metamorphism'' (from Greek ''meta'' = "change", ''morph'' = "form") refers to the evolution of a defect in the final stage of software deployment. Transformation of a ''mistake'' committed by an analyst in the early stages of the softw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fault Tolerance
Fault tolerance is the ability of a system to maintain proper operation despite failures or faults in one or more of its components. This capability is essential for high-availability, mission-critical, or even life-critical systems. Fault tolerance specifically refers to a system's capability to handle faults without any degradation or downtime. In the event of an error, end-users remain unaware of any issues. Conversely, a system that experiences errors with some interruption in service or graceful degradation of performance is termed 'resilient'. In resilience, the system adapts to the error, maintaining service but acknowledging a certain impact on performance. Typically, fault tolerance describes computer systems, ensuring the overall system remains functional despite hardware or software issues. Non-computing examples include structures that retain their integrity despite damage from fatigue, corrosion or impact. History The first known fault-tolerant computer was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Assertion (software Development)
In computer programming, specifically when using the imperative programming paradigm, an assertion is a predicate (a Boolean-valued function over the state space, usually expressed as a logical proposition using the variables of a program) connected to a point in the program, that always should evaluate to true at that point in code execution. Assertions can help a programmer read the code, help a compiler compile it, or help the program detect its own defects. For the latter, some programs check assertions by actually evaluating the predicate as they run. Then, if it is not in fact true – an assertion failure – the program considers itself to be broken and typically deliberately crashes or throws an assertion failure exception. Details The following code contains two assertions, x > 0 and x > 1, and they are indeed true at the indicated points during execution: x = 1; assert x > 0; x++; assert x > 1; Programmers can use assertions to help specify programs and to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enumerated Type
In computer programming, an enumerated type (also called enumeration, enum, or factor in the R (programming language), R programming language, a status variable in the JOVIAL programming language, and a categorical variable in statistics) is a data type consisting of a set of named value (computer science), values called ''elements'', ''members'', ''enumeral'', or ''enumerators'' of the type. The enumerator names are usually Identifier (computer languages), identifiers that behave as constant (programming), constants in the language. An enumerated type can be seen as a degenerate tagged union of unit type. A variable (computer science), variable that has been declaration (computer science), declared as having an enumerated type can be assigned any of the enumerators as a value. In other words, an enumerated type has values that are different from each other, and that can be compared and assigned, but are not generally specified by the programmer as having any particular concrete re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Null Pointer
In computing, a null pointer (sometimes shortened to nullptr or null) or null reference is a value saved for indicating that the Pointer (computer programming), pointer or reference (computer science), reference does not refer to a valid Object (computer science), object. Programs routinely use null pointers to represent conditions such as the end of a List (computing), list of unknown length or the failure to perform some action; this use of null pointers can be compared to nullable types and to the ''Nothing'' value in an option type. A null pointer should not be confused with an uninitialized variable, uninitialized pointer: a null pointer is guaranteed to compare unequal to any pointer that points to a valid object. However, in general, most languages do not offer such guarantee for uninitialized pointers. It might compare equal to other, valid pointers; or it might compare equal to null pointers. It might do both at different times; or the comparison might be undefined behavio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Design By Contract
Design by contract (DbC), also known as contract programming, programming by contract and design-by-contract programming, is an approach for designing software. It prescribes that software designers should define formal, precise and verifiable interface specifications for software components, which extend the ordinary definition of abstract data types with preconditions, postconditions and invariants. These specifications are referred to as "contracts", in accordance with a conceptual metaphor with the conditions and obligations of business contracts. The DbC approach assumes all ''client components'' that invoke an operation on a ''server component'' will meet the preconditions specified as required for that operation. Where this assumption is considered too risky (as in multi-channel or distributed computing), the inverse approach is taken, meaning that the ''server component'' tests that all relevant preconditions hold true (before, or while, processing the ''client co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Factory Acceptance Testing
In engineering and its various subdisciplines, acceptance testing is a test conducted to determine if the requirements of a specification or contract are met. It may involve chemical tests, physical tests, or performance tests. In systems engineering, it may involve black-box testing performed on a system (for example: a piece of software, lots of manufactured mechanical parts, or batches of chemical products) prior to its delivery. In software testing, the ISTQB defines ''acceptance testing'' as: The final test in the QA lifecycle, user acceptance testing, is conducted just before the final release to assess whether the product or application can handle real-world scenarios. By replicating user behavior, it checks if the system satisfies business requirements and rejects changes if certain criteria are not met. Some forms of acceptance testing are, user acceptance testing (UAT), end-user testing, operational acceptance testing (OAT), acceptance test-driven development (ATD ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
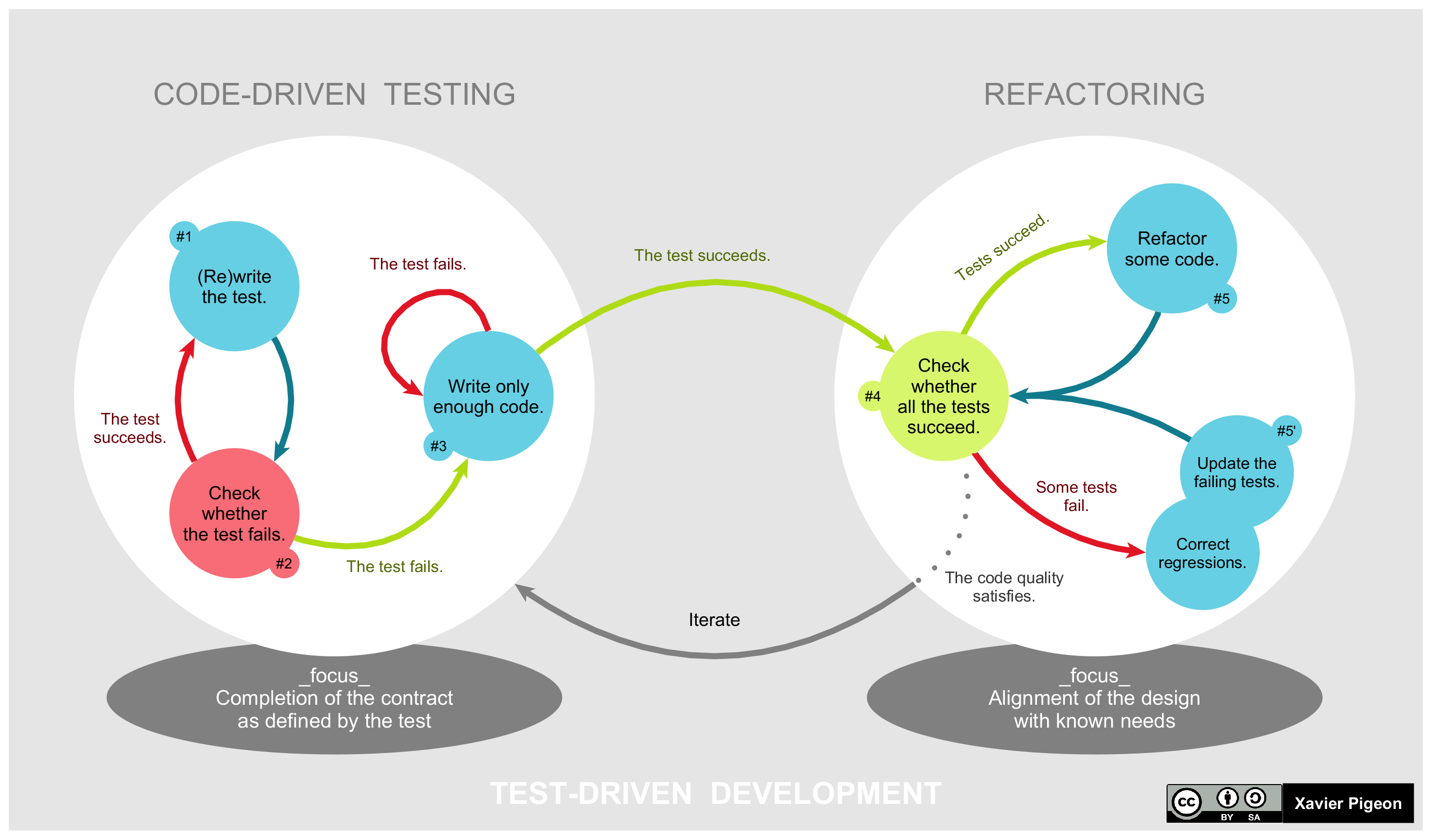
Test Driven Development
Test-driven development (TDD) is a way of writing code that involves writing an automated unit-level test case that fails, then writing just enough code to make the test pass, then refactoring both the test code and the production code, then repeating with another new test case. Alternative approaches to writing automated tests is to write all of the production code before starting on the test code or to write all of the test code before starting on the production code. With TsDD, both are written together, therefore shortening debugging time necessities. TDD is related to the test-first programming concepts of extreme programming, begun in 1999, but more recently has created more general interest in its own right.Newkirk, JW and Vorontsov, AA. ''Test-Driven Development in Microsoft .NET'', Microsoft Press, 2004. Programmers also apply the concept to improving and debugging legacy code developed with older techniques.Feathers, M. Working Effectively with Legacy Code, Prentice H ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unit Tests
Unit testing, component or module testing, is a form of software testing by which isolated source code is tested to validate expected behavior. Unit testing describes tests that are run at the unit-level to contrast testing at the integration or system level. History Unit testing, as a principle for testing separately smaller parts of large software systems, dates back to the early days of software engineering. In June 1956 at US Navy's Symposium on Advanced Programming Methods for Digital Computers, H.D. Benington presented the SAGE project. It featured a specification-based approach where the coding phase was followed by "parameter testing" to validate component subprograms against their specification, followed then by an "assembly testing" for parts put together. In 1964, a similar approach is described for the software of the Mercury project, where individual units developed by different programmes underwent "unit tests" before being integrated together. In 1969, t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Strategy Pattern
In computer programming, the strategy pattern (also known as the policy pattern) is a behavioral software design pattern that enables selecting an algorithm at runtime. Instead of implementing a single algorithm directly, code receives runtime instructions as to which in a family of algorithms to use. Strategy lets the algorithm vary independently from clients that use it. Strategy is one of the patterns included in the influential book '' Design Patterns'' by Gamma et al. that popularized the concept of using design patterns to describe how to design flexible and reusable object-oriented software. Deferring the decision about which algorithm to use until runtime allows the calling code to be more flexible and reusable. For instance, a class that performs validation on incoming data may use the strategy pattern to select a validation algorithm depending on the type of data, the source of the data, user choice, or other discriminating factors. These factors are not known until runt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fail-fast System
In systems design, a fail-fast system is one that immediately reports at its interface any condition that is likely to indicate a failure. Fail-fast systems are usually designed to stop normal operation rather than attempt to continue a possibly flawed process. Such designs often check the system's state at several points in an operation, so that any failures can be detected early. The responsibility of a fail-fast module is detecting errors, and then letting the next-highest level of the system handle them. Hardware and software Fail-fast systems or modules are desirable in several circumstances: * Fail-fast architectures are based on an error handling policy where any detected error or non-contemplated state makes the system fail (fast). In some sense, the error-handling policy is the opposite of that used in a fault-tolerant system. In a fault-tolerant system, an error handling policy is established to have redundant components and move computation requests to alive componen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |