|
Intelligence Collection Management
Intelligence collection management is the process of managing and organizing the Intelligence (information gathering), collection of intelligence from various sources. The collection department of an intelligence organization may attempt basic validation of what it collects, but is not supposed to analyze its significance. There is debate in U.S. intelligence community on the difference between validation and analysis, where the National Security Agency may (in the opinion of the Central Intelligence Agency or the Defense Intelligence Agency) try to interpret information when such interpretation is the job of another agency. Collection disciplines Disciplines which postprocess raw data more than collect it are: *Cyber intelligence (CYBINT) *Financial intelligence (FININT) *Geospatial intelligence, Geo-spatial intelligence (GEOINT) *Human intelligence (espionage), Human intelligence (HUMINT) *Imagery intelligence (IMINT) *Measurement and signature intelligence (MASINT) *Open-so ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence (information Gathering)
Intelligence assessment, is a specific phase of the intelligence cycle which oversees the development of behavior forecasts or recommended courses of action to the leadership of an organization, based on wide ranges of available overt and covert intelligence (also known as "intel"). There are two types of assessment; * In the beginning of the intelligence cycle, during the direction phase (also known as tasking or planning), intelligence officers assess past intelligence, identify gaps in information, and determine what new intelligence is needed. * Intelligence assessment also occurs toward the end of the intelligence cycle, during the analysis & production phase. This phase comes after collection and processing but before dissemination to policymakers. Assessments develop in response to leadership declaration requirements to inform decision-making. Assessment may be executed on behalf of a state, military or commercial organisation with ranges of information sources availa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
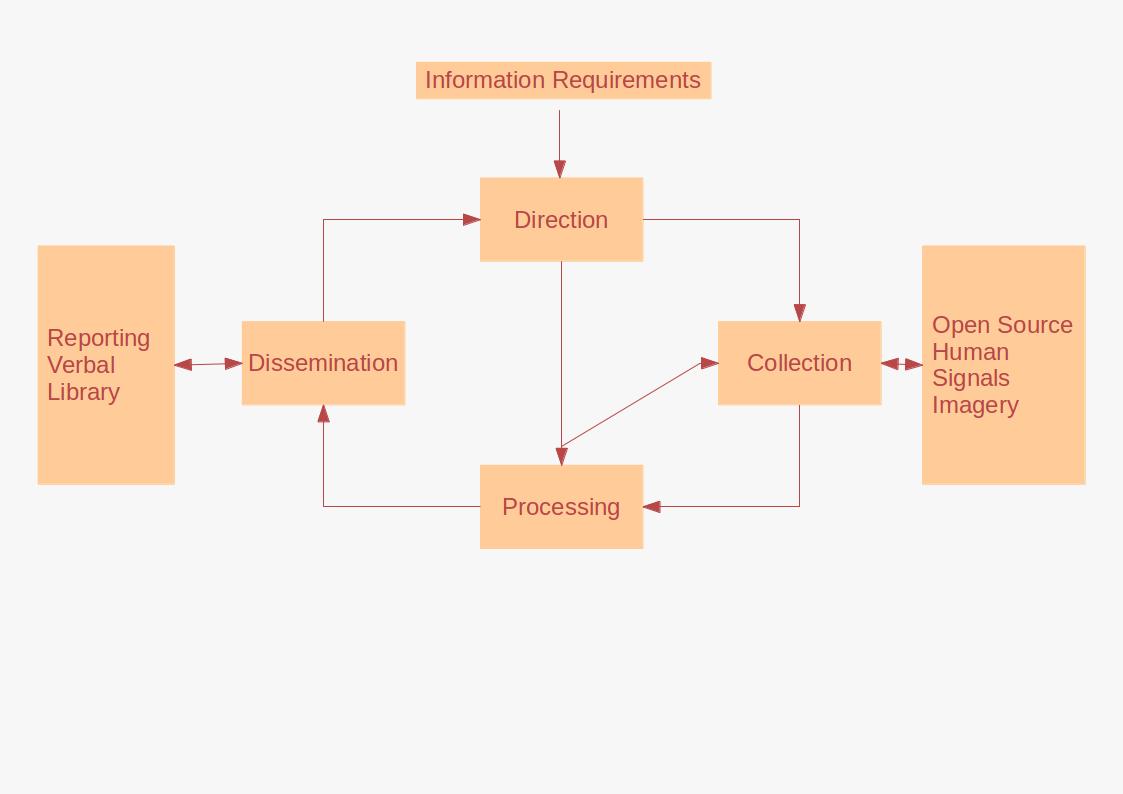
ISTAR
ISTAR stands for Military intelligence, intelligence, surveillance, target acquisition, and reconnaissance. In its macroscopic sense, #ISTAR, ISTAR is a practice that links several battlefield functions together to assist a combat force in employing its sensors and managing the information they gather. Information is collected on the battlefield through systematic observation by deployed soldiers and a variety of electronic sensors. ''Surveillance'', ''target acquisition'' and ''reconnaissance'' are methods of obtaining this information. The information is then passed to intelligence personnel for analysis, and then to the commander and their staff for the formulation of battle plans. Military intelligence, Intelligence is processed information that is relevant and contributes to an understanding of the ground, and of enemy dispositions and intents. Intelligence failures can happen. ISR (Intelligence, surveillance and reconnaissance) ISR is the coordinated and integrated acq ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
JN-25
The vulnerability of Japanese naval codes and ciphers was crucial to the conduct of World War II, and had an important influence on foreign relations between Japan and the west in the years leading up to the war as well. Every Japanese code was eventually broken, and the intelligence gathered made possible such operations as the victorious American ambush of the Japanese Navy at Battle of Midway, Midway in 1942 (by breaking code JN-25b) and the shooting down of Japanese admiral Isoroku Yamamoto a year later in Operation Vengeance. The Imperial Japanese Navy (IJN) used many codes and ciphers. All of these cryptosystems were known differently by different organizations; the names listed below are those given by Western cryptanalytic operations. Red code The Red Book code was an IJN code book system used in World War I and after. It was called "Red Book" because the American photographs made of it were bound in red covers.Greg Goebel"US Codebreakers In The Shadow Of War" 2018. It sh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Infrasound
Infrasound, sometimes referred to as low frequency sound or incorrectly subsonic (subsonic being a descriptor for "less than the speed of sound"), describes sound waves with a Audio frequency, frequency below the lower limit of human audibility (generally 20 Hertz, Hz, as defined by the ANSI/ASA S1.1-2013 standard). Hearing becomes gradually less sensitive as frequency decreases, so for humans to perceive infrasound, the sound pressure must be sufficiently high. Although the ear is the primary organ for sensing low sound, at higher intensities it is possible to feel infrasound vibrations in various parts of the body. The study of such sound waves is sometimes referred to as infrasonics, covering sounds beneath 20 Hz down to 0.1 Hz (and rarely to 0.001 Hz). People use this frequency range for monitoring earthquakes and volcanoes, charting rock and petroleum formations below the earth, and also in ballistocardiography and seismocardiography to study the mechanics of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Code Name
A code name, codename, call sign, or cryptonym is a code word or name used, sometimes clandestinely, to refer to another name, word, project, or person. Code names are often used for military purposes, or in espionage. They may also be used in industrial counter-espionage to protect secret projects and the like from business rivals, or to give names to projects whose marketing name has not yet been determined. Another reason for the use of names and phrases in the military is that they transmit with a lower level of cumulative errors over a walkie-talkie or radio link than actual names. Origins Achaemenid Empire The Achaemenid Empire under Darius I employed a network of spies called the King’s Eye or the King’s Ear. These agents operated under anonymity, and “King’s Eye” was not a specific person but rather a code name for the intelligence network that reported directly to the king. Punic Wars The Carthaginian general Hannibal Barca reportedly used coded re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disinformation
Disinformation is misleading content deliberately spread to deceive people, or to secure economic or political gain and which may cause public harm. Disinformation is an orchestrated adversarial activity in which actors employ strategic deceptions and media manipulation tactics to advance political, military, or commercial goals. Disinformation is implemented through coordinated campaigns that "weaponize multiple rhetorical strategies and forms of knowing—including not only falsehoods but also truths, half-truths, and value judgements—to exploit and amplify culture wars and other identity-driven controversies." In contrast, ''misinformation'' refers to inaccuracies that stem from inadvertent error. Misinformation can be used to create disinformation when known misinformation is purposefully and intentionally disseminated. " Fake news" has sometimes been categorized as a type of disinformation, but scholars have advised not using these two terms interchangeably or us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ultra (cryptography)
Ultra was the designation adopted by United Kingdom, British military intelligence in June 1941 for wartime signals intelligence obtained by breaking high-level encrypted enemy radio and teleprinter communications at the Government Code and Cypher School (GC&CS) at Bletchley Park. ''Ultra'' eventually became the standard designation among the western Allies of World War II, Allies for all such intelligence. The name arose because the intelligence obtained was considered more important than that designated by the highest British Classified information, security classification then used (''Most Secret'' and so was regarded as being ''Ultra Secret''. Several other cryptonyms had been used for such intelligence. The code name "Boniface" was used as a cover name for ''Ultra''. In order to ensure that the successful code-breaking did not become apparent to the Germans, British intelligence created a fictional MI6 master spy, Boniface, who controlled a fictional series of agents throug ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enigma Machine
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the Wehrmacht, German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages. The Enigma has an electromechanical Rotor machine, rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of the 26 lights above the keyboard illuminated at each key press. If plaintext is entered, the illuminated letters are the ciphertext. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress. The security of the system depends on machine settings that were generally changed daily, based ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Net2
NET may refer to: Broadcast media United States * National Educational Television, the predecessor of the Public Broadcasting Service (PBS) in the United States * National Empowerment Television, a politically conservative cable TV network, now defunct, also known as "America's Voice" * Nebraska Educational Telecommunications, a state network of Television (PBS) and Radio Stations (NPR) in Nebraska, United States * New Evangelization Television, a Christian-oriented TV channel based in New York, United States Elsewhere * NET (telecommunications), a Brazilian cable television operator * MDTV (Indonesian TV network), an Indonesian television network formerly known as NET * NET (Maltese TV channel), a Maltese television station * NET 5, a Dutch television station * Net 25, a Philippine television station * New Hellenic Television, a Greek television network, currently known as ERT2 * Nihon Educational Television, former name of TV Asahi Science and technology * Noise- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NATO Collection Guidance
The North Atlantic Treaty Organization (NATO ; , OTAN), also called the North Atlantic Alliance, is an intergovernmental organization, intergovernmental Transnationalism, transnational military alliance of 32 Member states of NATO, member states—30 European and 2 North American. Established in the aftermath of World War II, the organization implements the North Atlantic Treaty, signed in Washington, D.C., on 4 April 1949. NATO is a collective security system: its independent member states agree to defend each other against attacks by third parties. During the Cold War, NATO operated as a check on the threat posed by the Soviet Union. The alliance remained in place after the dissolution of the Soviet Union and the Warsaw Pact, and has been involved in military operations in the Balkans, the Middle East, South Asia, and Africa. The organization's motto is . The organization's strategic concepts include Deterrence theory, deterrence. NATO headquarters, NATO's main headquarter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Customer Relationship Management
Customer relationship management (CRM) is a strategic process that organizations use to manage, analyze, and improve their interactions with customers. By leveraging data-driven insights, CRM helps businesses optimize communication, enhance customer satisfaction, and drive sustainable growth. CRM systems compile data from a range of different communication channels, including a company's website, telephone (which many services come with a softphone), email, live chat, marketing materials and more recently, social media. They allow businesses to learn more about their target audiences and how to better cater to their needs, thus retaining customers and driving sales growth. CRM may be used with past, present or potential customers. The concepts, procedures, and rules that a corporation follows when communicating with its consumers are referred to as CRM. This complete connection covers direct contact with customers, such as sales and service-related operations, forecasting, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Allied Rapid Reaction Corps
The Allied Rapid Reaction Corps (ARRC) is a rapid reaction force maintained by NATO. It is capable of deploying a High Readiness Force (Land) Headquarters at short notice for operations and crisis response. History The ARRC was created on 1 October 1992 in Bielefeld based on the former I (British) Corps (I (BR) Corps). It was originally created as the rapid reaction corps sized land force of the Reaction Forces Concept that emerged after the end of the Cold War, with a mission to redeploy and reinforce within Allied Command Europe (ACE) and to conduct Petersberg missions out of NATO territory. The first commander, appointed in 1992 was General Sir Jeremy Mackenzie. From 1994 the ARRC was based in the Rheindahlen Military Complex, Germany. It commanded the Land Forces of NATO's first ever deployment as part of the Implementation Force operation in Bosnia in 1995/6 and was again deployed as the headquarters commanding Land Forces during the Kosovo War in 1999. In 1997 ass ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |