|
IT Process Automation
IT process automation (ITPA) is a series of processes which facilitate the orchestration and integration of tools, people and processes through automated workflows. ITPA software applications can be programmed to perform any repeatable pattern, task or business workflow that was once handled manually by humans. Description ITPA is often used interchangeably with the term run book automation (RBA). IT departments in organizations of every size and industry can employ ITPA technology to specify certain criteria and outcomes for almost any task or process currently being performed. When a system event occurs, the appropriate workflow is triggered and executed to automatically address and remediate the problem. This is often seen in IT service management or ESM during the ticketing process, it is becoming much more commonplace in daily business functions. Advanced ITPA software is intuitive enough to automate complex processes across multiple systems with or without the need f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Orchestration (computing)
In system administration, orchestration is the automated configuration, coordination, deployment, development, and management of computer systems and software. Many tools exist to automate server configuration and management. Usage Orchestration is often discussed in the context of service-oriented architecture, virtualization, provisioning, converged infrastructure and dynamic data center topics. Orchestration in this sense is about aligning the business request with the applications, data, and infrastructure. In the context of cloud computing, the main difference between workflow automation and orchestration is that workflows are processed and completed as processes within a single domain for automation purposes, whereas orchestration includes a workflow and provides a directed action towards larger goals and objectives. In this context, and with the overall aim to achieve specific goals and objectives (described through the quality of service parameters), for example, m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Infrastructure
Infrastructure is the set of facilities and systems that serve a country, city, or other area, and encompasses the services and facilities necessary for its economy, households and firms to function. Infrastructure is composed of public and private physical structures such as roads, railways, bridges, airports, public transit systems, tunnels, water supply, sewers, electrical grids, and telecommunications (including Internet connectivity and broadband access). In general, infrastructure has been defined as "the physical components of interrelated systems providing commodities and services essential to enable, sustain, or enhance societal living conditions" and maintain the surrounding environment. Especially in light of the massive societal transformations needed to mitigate and adapt to climate change, contemporary infrastructure conversations frequently focus on sustainable development and green infrastructure. Acknowledging this importance, the international co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Self-service
Self-service is a system whereby customers acquire (or serve) themselves goods or services, paying for the items at a point-of-sale, as opposed to a shop assistant or clerk acquiring goods or providing services in addition to taking payment. Common examples include ATMs, coin-operated laundrettes, self-service checkouts, self-service petrol stations, and buffet restaurants. History Grocery stores and supermarkets Before the 20th century many businesses such as grocery stores had clerks or assistants who would serve customers individually, taking required items from the shelves, before adding up the total at the till. Some products such as ham, cheese, and bacon were sliced to order, while dry goods such as flour would be weighed out from large barrels. On September 6th 1916 the first Piggly Wiggly opened in Memphis, Tennessee by Clarence Saunders, the world's first self-service grocery store. Customers would pick up a wicker basket upon entering the store, and then w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
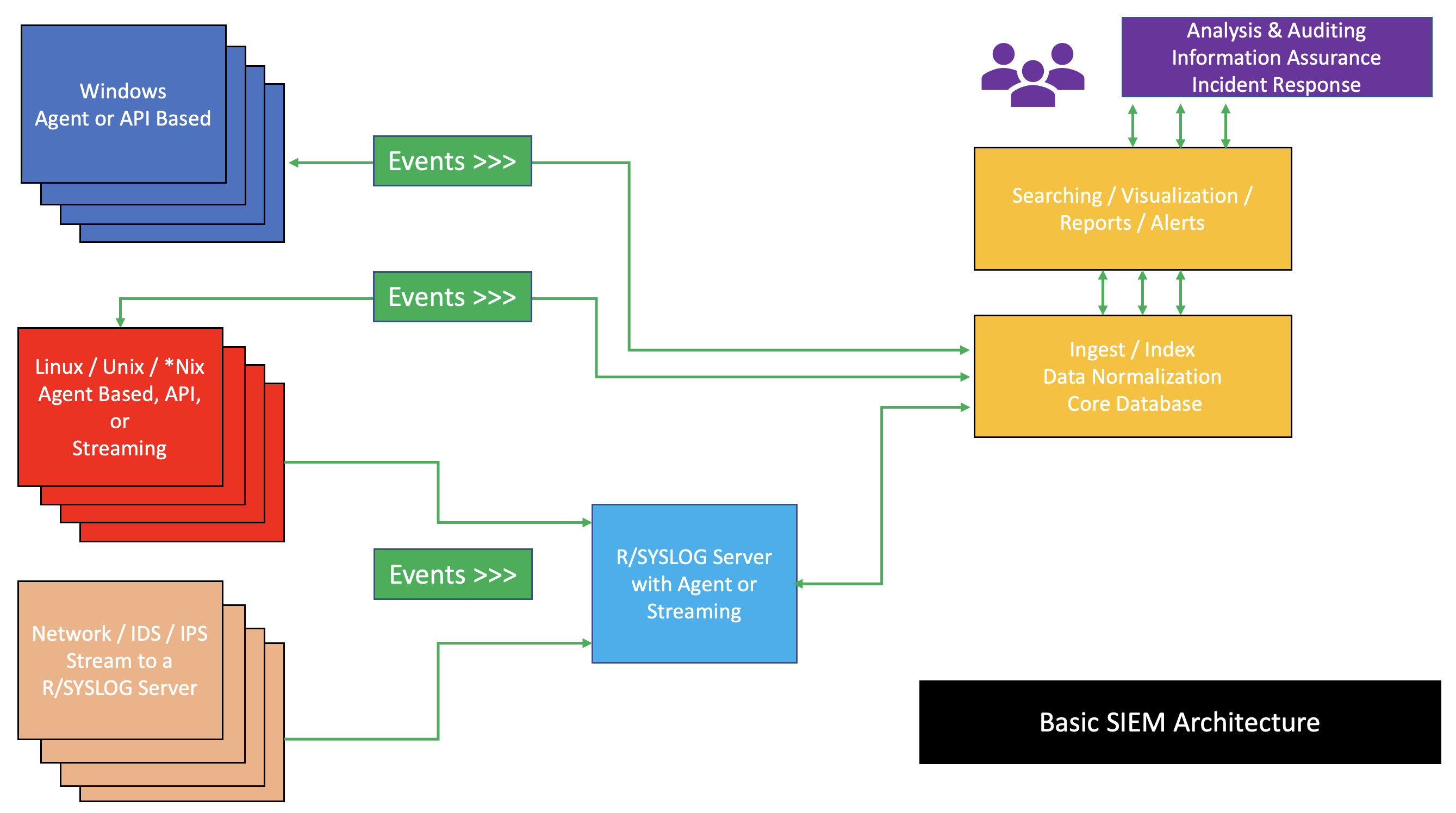
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security Operations Center
An information security operations center (ISOC or SOC) is a facility where enterprise information systems (web sites, application software, applications, databases, data centers and server (computing), servers, computer network, networks, client (computing), desktops and other endpoints) are monitored, assessed, and defended. Objective A SOC is related to the people, processes and technologies that provide situational awareness through the detection, containment, and remediation of IT threats in order to manage and enhance an organization's security posture. A SOC will handle, on behalf of an institution or company, any threatening IT incident, and will ensure that it is properly identified, analyzed, communicated, investigated and reported. The SOC also monitors applications to identify a possible cyber-attack or intrusion (event), and determines if it is a genuine malicious threat (incident), and if it could affect business. Regulatory requirements Establishing and operat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |