|
Trusted Computer System Evaluation Criteria
Trusted Computer System Evaluation Criteria (TCSEC) is a United States Government Department of Defense (DoD) standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system. The TCSEC was used to evaluate, classify, and select computer systems being considered for the processing, storage, and retrieval of sensitive or classified information. The TCSEC, frequently referred to as the Orange Book, is the centerpiece of the DoD ''Rainbow Series'' publications. Initially issued in 1983 by the National Computer Security Center (NCSC), an arm of the National Security Agency, and then updated in 1985, TCSEC was eventually replaced by the Common Criteria international standard, originally published in 2005. History By the late 1960s, government agencies, like other computer users, had gone far in the transition from batch processing to multiuser and time-sharing systems. The US Department of Defense (DoD) Advanced Resear ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Systems Center
The Electronic Systems Center was a product center of Air Force Materiel Command (AFMC) headquartered at Hanscom Air Force Base, Massachusetts. Its mission was to develop and acquire command and control, communications, computer, and intelligence systems. ESC consisted of professional teams specializing in engineering, computer science, and business management. The teams supervised the design, development, testing, production, and deployment of command and control systems. Two of ESC's most well-known developments were the Boeing E-3 Sentry Airborne Warning and Control System (AWACS), developed in the 1970s, and the Joint Surveillance Target Attack Radar System (Joint STARS), developed in the 1980s. The Electronic Systems Center served into five decades as the Air Force's organization for developing and acquiring Command and Control (C2) systems. As of December 2004, ESC managed approximately two hundred programs ranging from secure communications systems to mission planning ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenVMS
OpenVMS, often referred to as just VMS, is a multi-user, multiprocessing and virtual memory-based operating system. It is designed to support time-sharing, batch processing, transaction processing and workstation applications. Customers using OpenVMS include banks and financial services, hospitals and healthcare, telecommunications operators, network information services, and industrial manufacturers. During the 1990s and 2000s, there were approximately half a million VMS systems in operation worldwide. It was first announced by Digital Equipment Corporation (DEC) as VAX/VMS (''Virtual Address eXtension/Virtual Memory System'') alongside the VAX-11/780 minicomputer in 1977. OpenVMS has subsequently been ported to run on DEC Alpha systems, the Itanium-based HPE Integrity Servers, and select x86-64 hardware and hypervisors. Since 2014, OpenVMS is developed and supported by VMS Software Inc. (VSI). OpenVMS offers high availability through computer cluster, clustering—the ability t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mandatory Access Control
In computer security, mandatory access control (MAC) refers to a type of access control by which a secured environment (e.g., an operating system or a database) constrains the ability of a ''subject'' or ''initiator'' to access or modify on an ''object'' or ''target''. In the case of operating systems, the subject is a process or thread, while objects are files, directories, TCP/ UDP ports, shared memory segments, or IO devices. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, the operating system kernel examines these security attributes, examines the authorization rules (aka ''policy'') in place, and decides whether to grant access. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects are tables, views, procedures, etc. In mandatory access control, the security policy is centrally controlled by a policy administrator and is guaranteed (in p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HP-UX
HP-UX (from "Hewlett Packard Unix") is a proprietary software, proprietary implementation of the Unix operating system developed by Hewlett Packard Enterprise; current versions support HPE Integrity Servers, based on Intel's Itanium architecture. It is based on Unix System V (initially Unix System III, System III) and first released in 1984. Earlier versions of HP-UX supported the HP Integral PC and HP 9000 Series 200, 300, and 400 computer systems based on the Motorola 68000 series of processors, the HP 9000 Series 500 computers based on HP's proprietary HP FOCUS, FOCUS architecture, and later HP 9000 Series models based on HP's PA-RISC instruction set architecture. HP-UX was the first Unix to offer access-control lists for file access permissions as an alternative to the standard Unix permissions system. HP-UX was also among the first Unix systems to include a built-in logical volume management, logical volume manager. HP has had a long partnership with Veritas Software, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discretionary Access Control
In computer security, discretionary access control (DAC) is a type of access control defined by the Trusted Computer System Evaluation Criteria (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). Discretionary access control is commonly discussed in contrast to mandatory access control (MAC). Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access control. On the other hand, systems can implement both MAC and DAC simultaneously, where DAC refers to one category of access controls that subjects can transfer among each other, and MAC refers to a second category of access controls that imposes constr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Audit Trail
An audit trail (also called audit log) is a security-relevant chronological record, set of records, and/or destination and source of records that provide documentary evidence of the sequence of activities that have affected at any time a specific operation, procedure, event, or device. Audit records typically result from activities such as financial transactions, scientific research and health care data transactions, or communications by individual people, systems, accounts, or other entities. The process that creates an audit trail is typically required to always run in a privileged mode, so it can access and supervise all actions from all users; a normal user should not be allowed to stop/change it. Furthermore, for the same reason, the trail file or database table with a trail should not be accessible to normal users. Another way of handling this issue is through the use of a role-based security model in the software. The software can operate with the closed-looped controls, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control
In physical security and information security, access control (AC) is the action of deciding whether a subject should be granted or denied access to an object (for example, a place or a resource). The act of ''accessing'' may mean consuming, entering, or using. It is often used interchangeably with authorization, although the authorization may be granted well in advance of the access control decision. Access control on digital platforms is also termed admission control. The protection of external databases is essential to preserve digital security. Access control is considered to be a significant aspect of privacy that should be further studied. Access control policy (also access policy) is part of an organization’s security policy. In order to verify the access control policy, organizations use an access control model. General security policies require designing or selecting appropriate security controls to satisfy an organization's risk appetite - access policies ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Central Intelligence Agency
The Central Intelligence Agency (CIA; ) is a civilian foreign intelligence service of the federal government of the United States tasked with advancing national security through collecting and analyzing intelligence from around the world and conducting covert operations. The agency is headquartered in the George Bush Center for Intelligence in Langley, Virginia, and is sometimes metonymously called "Langley". A major member of the United States Intelligence Community (IC), the CIA has reported to the director of national intelligence since 2004, and is focused on providing intelligence for the president and the Cabinet. The CIA is headed by a director and is divided into various directorates, including a Directorate of Analysis and Directorate of Operations. Unlike the Federal Bureau of Investigation (FBI), the CIA has no law enforcement function and focuses on intelligence gathering overseas, with only limited domestic intelligence collection. The CIA is responsible for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
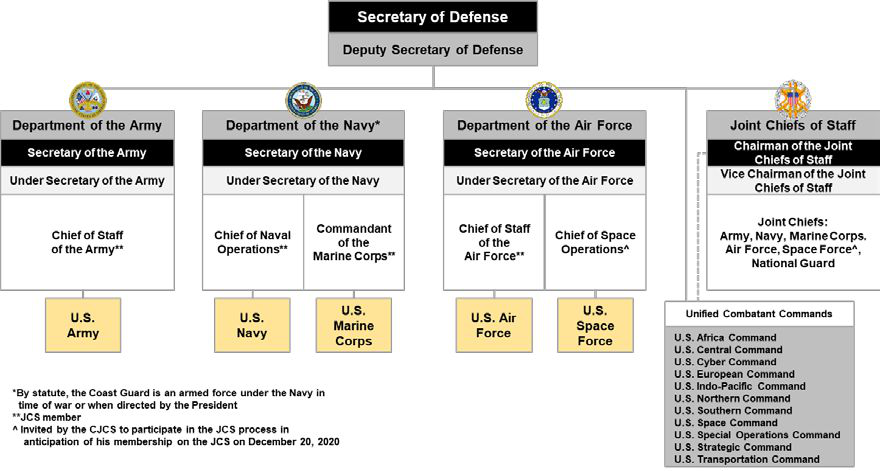
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an executive department of the U.S. federal government charged with coordinating and supervising the six U.S. armed services: the Army, Navy, Marines, Air Force, Space Force, the Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provide the military forces needed to deter war and ensure our nation's security". The current Secretary of Defense is Pete Hegseth. The Department of Defense is headed by the secretary of defense, a cabinet-level head who reports directly to the president of the Unit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Univac
UNIVAC (Universal Automatic Computer) was a line of electronic digital stored-program computers starting with the products of the Eckert–Mauchly Computer Corporation. Later the name was applied to a division of the Remington Rand company and successor organizations. The BINAC, built by the Eckert–Mauchly Computer Corporation, was the first general-purpose computer for commercial use, but it was not a success. The last UNIVAC-badged computer was produced in 1986. History and structure J. Presper Eckert and John Mauchly built the ENIAC (Electronic Numerical Integrator and Computer) at the University of Pennsylvania's Moore School of Electrical Engineering between 1943 and 1946. A 1946 patent rights dispute with the university led Eckert and Mauchly to depart the Moore School to form the Electronic Control Company, later renamed Eckert–Mauchly Computer Corporation (EMCC), based in Philadelphia, Pennsylvania. That company first built a computer called BINAC (BINary Automat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Commercial Off-the-shelf
Commercial-off-the-shelf or commercially available off-the-shelf (COTS) products are packaged or canned (ready-made) hardware or software, which are adapted aftermarket to the needs of the purchasing organization, rather than the commissioning of custom-made, or bespoke, solutions. A related term, Mil-COTS, refers to COTS products for use by the U.S. and Canadian militaries. In the context of the Federal government of the United States, U.S. government, the Federal Acquisition Regulation (FAR) has defined "COTS" as a formal term for commercial items, including services, available in the commercial marketplace that can be bought and used under government contract. For example, Microsoft is a COTS software provider. Goods and construction materials may qualify as COTS but bulk cargo does not. Services associated with the commercial items may also qualify as COTS, including installation services, training services, and cloud services. COTS purchases are alternatives to custom softwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |