|
Peer Name Resolution Protocol
Peer Name Resolution Protocol (PNRP) is a peer-to-peer protocol designed by Microsoft. PNRP enables dynamic name publication and resolution, and requires IPv6. PNRP was first mentioned during a presentation at a P2P conference in November 2001. It appeared in July 2003 in the Advanced Networking Pack for Windows XP, and was later included in the Service Pack 2 for Windows XP. PNRP 2.0 was introduced with Windows Vista and was available for download for Windows XP Service Pack 2 users. PNRP 2.1 is included in Windows Vista SP1, Windows Server 2008 and Windows XP SP3. PNRP v2 is not available for Windows XP Professional x64 Edition or any edition of Windows Server 2003. Windows Remote Assistance in Windows 7 uses PNRP, Teredo and IPv6 when connecting using the ''Easy Connect'' option. The design of PNRP is covered by US Patent #7,065,587, issued on June 20, 2006. Support for PNRP was removed in Windows 10 with version 1909. PNRP services The PNRP is a distributed name resol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer network of nodes. Peers make a portion of their resources, such as processing power, disk storage or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model in which the consumption and supply of resources are divided. While P2P systems had previously been used in many application domains, the architecture was popularized by the file sharing system Napster, originally released in 1999. The concept has inspired new structures and philosophies in many areas of human interaction. In such social contexts, peer-to-peer as a meme refers to the egalitarian ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can Encryption, encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Vista Networking Technologies
In computing, Microsoft's Windows Vista and Windows Server 2008 introduced in 2007/2008 a new networking stack named Next Generation TCP/IP stack, to improve on the previous stack in several ways. The stack includes native implementation of IPv6, as well as a complete overhaul of IPv4. The new TCP/IP stack uses a new method to store configuration settings that enables more dynamic control and does not require a computer restart after a change in settings. The new stack, implemented as a dual-stack model, depends on a strong host-model and features an infrastructure to enable more modular components that one can dynamically insert and remove. Architecture The Next Generation TCP/IP stack connects to NICs via a Network Driver Interface Specification (NDIS) driver. The network stack, implemented in tcpip.sys implements the Transport, Network and Data link layers of the TCP/IP model. The Transport layer includes implementations for TCP, UDP and unformatted RAW protocols. At ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NetBIOS
NetBIOS () is an acronym for Network Basic Input/Output System. It provides services related to the session layer of the OSI model allowing applications on separate computers to communicate over a local area network. As strictly an API, NetBIOS is not a networking protocol. Older operating systems ran NetBIOS over IEEE 802.2 and IPX/SPX using the NetBIOS Frames (NBF) and NetBIOS over IPX/SPX (NBX) protocols, respectively. In modern networks, NetBIOS normally runs over TCP/IP via the NetBIOS over TCP/IP (NBT) protocol. This results in each computer in the network having both an IP address and a NetBIOS name corresponding to a (possibly different) host name. NetBIOS is also used for identifying system names in TCP/IP (Windows). Simply saying, it is a protocol that allows communication of files and printers through the Session Layer of the OSI Model in a LAN. History and terminology NetBIOS is a non-routable OSI Session Layer 5 Protocol and a service that allows applicati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast DNS
In computer networking, the multicast DNS (mDNS) protocol resolves hostnames to IP addresses within small networks that do not include a local name server. It is a zero-configuration service, using essentially the same programming interfaces, packet formats and operating semantics as unicast Domain Name Service (DNS). It was designed to work as either a stand-alone protocol or compatibly with standard DNS servers. It uses IP multicast User Datagram Protocol (UDP) packets, and is implemented by the Apple Bonjour and open source Avahi software packages, included in most Linux distributions. Although the Windows 10 implementation was limited to discovering networked printers, subsequent releases resolved hostnames as well. mDNS can work in conjunction with DNS Service Discovery (DNS-SD), a companion zero-configuration networking technique specified separately in RFC 6763. History Multicast DNS was first proposed by Bill Woodcock and Bill Manning in the IETF in 2000, and was ev ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Features New To Windows Vista
Compared with previous versions of Microsoft Windows, features new to Windows Vista are very numerous, covering most aspects of the operating system, including Management features new to Windows Vista, additional management features, Security and safety features new to Windows Vista, new aspects of security and safety, Windows Vista I/O technologies, new I/O technologies, Windows Vista networking technologies, new networking features, and Technical features new to Windows Vista, new technical features. Windows Vista also List of features removed in Windows Vista, removed some others. Windows Shell and user interface Windows Aero Windows Vista introduces a redesigned user interface and visual style named Windows Aero (a backronym for Authentic, Energetic, Reflective, and Open) that is intended to be aesthetically pleasing and cleaner than previous versions of Windows, with features such as glass translucencies, light effects, live thumbnails, and window animations enabled by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
128-bit
While there are currently no mainstream general-purpose processors built to operate on 128-bit ''integers'' or addresses, a number of processors do have specialized ways to operate on 128-bit chunks of data. Representation 128-bit processors could be used for addressing directly up to 2128 (over ) bytes, which would greatly exceed the total data captured, created, or replicated on Earth as of 2018, which has been estimated to be around 33 zettabytes (over 274 bytes). A 128-bit register can store 2128 (over 3.40 × 1038) different values. The range of integer values that can be stored in 128 bits depends on the integer representation used. With the two most common representations, the range is 0 through 340,282,366,920,938,463,463,374,607,431,768,211,455 (2128 − 1) for representation as an ( unsigned) binary number, and −170,141,183,460,469,231,731,687,303,715,884,105,728 (−2127) through 170,141,183,460,469,231,731,687,303,715,884,105,727 (2127 − 1) for represe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pastry (DHT)
:''This article describes the Pastry Distributed Hash Table. For the food, see Pastry.'' Pastry is an overlay network and routing network for the implementation of a distributed hash table (DHT) similar to Chord. The key–value pairs are stored in a redundant peer-to-peer network of connected Internet hosts. The protocol is bootstrapped by supplying it with the IP address of a peer already in the network and from then on via the routing table which is dynamically built and repaired. It is claimed that because of its redundant and decentralized nature there is no single point of failure and any single node can leave the network at any time without warning and with little or no chance of data loss. The protocol is also capable of using a routing metric supplied by an outside program, such as ping or traceroute, to determine the best routes to store in its routing table. Overview Although the distributed hash table functionality of Pastry is almost identical to other DHTs, what se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chord Project
In computing, Chord is a protocol and algorithm for a peer-to-peer distributed hash table. A distributed hash table stores associative array, key-value pairs by assigning keys to different computers (known as "nodes"); a node will store the values for all the keys for which it is responsible. Chord specifies how keys are assigned to nodes, and how a node can discover the value for a given key by first locating the node responsible for that key. Chord is one of the four original distributed hash table protocols, along with Content addressable network, CAN, Tapestry (DHT), Tapestry, and Pastry (DHT), Pastry. It was introduced in 2001 by Ion Stoica, Robert Tappan Morris, Robert Morris, David Karger, Frans Kaashoek, and Hari Balakrishnan, and was developed at MIT. The 2001 Chord paper won a ACM SIGCOMM Test of Time award in 2011. Subsequent research by Pamela Zave has shown that the original Chord algorithm (as specified in the 2001 SIGCOMM paper, the 2001 Technical report, the 2002 P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Hash Table
A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table: key–value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys. ''Keys'' are unique identifiers which map to particular ''values'', which in turn can be anything from addresses, to documents, to arbitrary data. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows a DHT to scale to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures. DHTs form an infrastructure that can be used to build more complex services, such as anycast, cooperative web caching, distributed file systems, domain name services, inst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
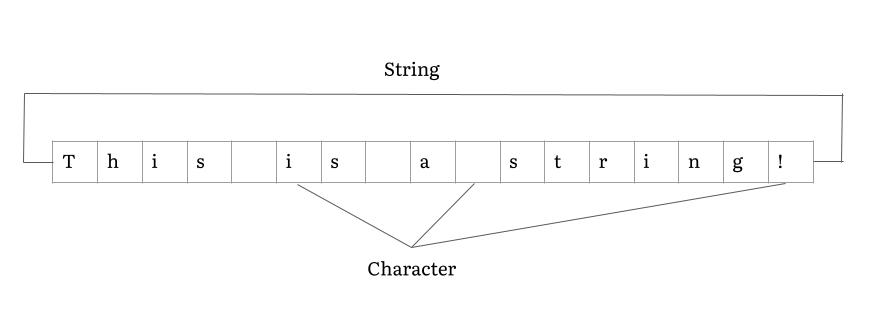
String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |