|
ID-MM7
ID-MM7 is a protocol developed and promoted by the Liberty Alliance, driven by major mobile operators such as Vodafone and Telefónica Móviles, to standardize identity-based web services interfaces to mobile messaging. The ID-MM7 specification adds significant value to existing web services. MM7 has long been used by operators for relaying MMS and SMS traffic. ID-MM enables an entirely new business model wherein the content providers know their subscribers only pseudonymously - providing the capability to thwart spam, identity theft and fraud In law, fraud is intentional deception to secure unfair or unlawful gain, or to deprive a victim of a legal right. Fraud can violate civil law (e.g., a fraud victim may sue the fraud perpetrator to avoid the fraud or recover monetary compen .... Known implementations of the protocol include: SymlabsFederated Identity Platfor Computer access control protocols Mobile telecommunications standards Mobile web {{telecomm-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MM7 (MMS)
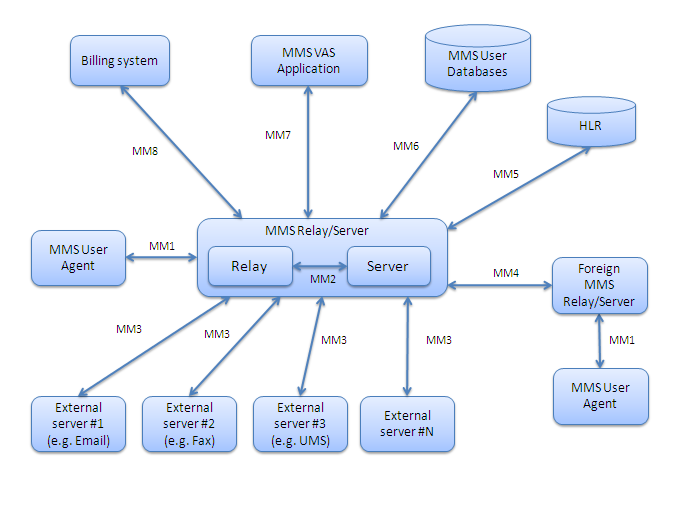
The MMS Architecture is the set of standards used by the Multimedia Messaging Service in GSM, mobile networks. The standards are prepared by 3GPP. Overview The standard consists of a number of interfaces between components found in the mobile network: * MM1: the interface between MMS User Agent and MMS Center (MMSC, the combination of the MMS Relay & Server). Delivered as HTTP over a packet switched data session. * MM2: the interface between MMS Relay and MMS Server. * MM3: the interface between MMSC and other messaging systems. Using SMTP. * MM4: the interface between MMSC and foreign network providers. Using SMTP. * MM5: the interface between MMSC and GSM core network#Home location register (HLR), HLR. * MM6: the interface between MMSC and user databases. * MM7: the interface between MMS Value-added service applications and MMSC. Typically Content Providers using HTTP / SOAP for delivery. * MM8: the interface between MMSC and the billing systems. * MM9: the interface between MMSC ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Liberty Alliance
The Liberty Alliance Project was an organization formed in September 2001 to establish standards, guidelines and best practices for identity management in computer systems. It grew to more than 150 organizations, including technology vendors, consumer-facing companies, educational organizations and governments. It released frameworks for federation, identity assurance, an Identity Governance Framework, and Identity Web Services. By 2009, the Kantara Initiative took over the work of the Liberty Alliance. History The group was originally conceived and named by Jeff Veis, at Sun Microsystems based in Menlo Park, California. The initiative's goal, which was personally promoted by Scott McNealy of Sun, was to unify technology, commercial and government organizations to create a standard for federated, identity-based Internet applications as an alternative to technology appearing in the marketplace controlled by a single entity such as Microsoft's Passport. Another Microsoft in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vodafone
Vodafone Group Public limited company, plc () is a British Multinational corporation, multinational Telephone company, telecommunications company. Its registered office and Headquarters, global headquarters are in Newbury, Berkshire, England. It predominantly operates Service (economics), services in Asia, Africa, Europe, and Oceania. , Vodafone owns and operates networks in 22 countries, with partner networks in 48 further countries. Its Vodafone Global Enterprise division provides telecommunications and IT services to corporate clients in 150 countries. Vodafone has a primary listing on the London Stock Exchange and is a constituent of the FTSE 100 Index. The company has a secondary listing on Nasdaq. Name The name Vodafone comes from ''VO''ice ''DA''ta ''FONE'' (the latter a sensational spelling of "telephone, phone"), chosen by the company to "reflect the provision of voice and data services over mobile phones". History The evolution of Vodafone started in 1981 with the es ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telefónica Móviles
Telefónica, S.A. () is a Spanish multinational telecommunications company headquartered in Madrid, Spain. It is one of the largest telephone operators and mobile network providers in the world. It provides fixed and mobile telephony, broadband, and subscription television, operating in Europe and the Americas. As well as the Telefónica brand, it also trades as Movistar, O2, and Vivo. The company is a component of the Euro Stoxx 50 stock market index. History * The company was created in Madrid in 1924 as Compañía Telefónica Nacional de España (CTNE) with ITT as one of its major shareholders. * In 1945, the state acquired by law a share of 79.6% of the company. This stake was diluted by a capital increase in 1967. * Until the liberalisation of the telecom market in 1997, Telefónica was the only telephone operator in Spain. It still holds a dominant position (over 75% in 2000). * Nowadays, Telefónica is present in more than 20 countries around Europe and America. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multimedia Messaging Service
Multimedia Messaging Service (MMS) is a standard way to send messages that include multimedia content to and from a mobile phone over a cellular network. Users and providers may refer to such a message as a PXT, a picture message, or a multimedia message. The MMS standard extends the core SMS (Short Message Service) capability, allowing the exchange of text messages greater than 160 characters in length. Unlike text-only SMS, MMS can deliver a variety of media, including up to forty seconds of video, one image, a slideshow of multiple images, or audio. The most common use involves sending photographs from camera-equipped handsets. Media companies have utilized MMS on a commercial basis as a method of delivering news and entertainment content, and retailers have deployed it as a tool for delivering scannable coupon codes, product images, videos, and other information. The 3GPP and WAP groups fostered the development of the MMS standard, which is now continued by the Open Mobile ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (electronic)
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, for any prohibited purpose (especially the fraudulent purpose of phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers hav ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Identity Theft
Identity theft occurs when someone uses another person's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term ''identity theft'' was coined in 1964. Since that time, the definition of identity theft has been statutorily defined throughout both the U.K. and the U.S. as the theft of personally identifiable information. Identity theft deliberately uses someone else's identity as a method to gain financial advantages or obtain credit and other benefits, and perhaps to cause other person's disadvantages or loss. The person whose identity has been stolen may suffer adverse consequences, especially if they are falsely held responsible for the perpetrator's actions. Personally identifiable information generally includes a person's name, date of birth, social security number, driver's license number, bank account or credit card numbers, PINs, electronic signatures, fingerprint ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fraud
In law, fraud is intentional deception to secure unfair or unlawful gain, or to deprive a victim of a legal right. Fraud can violate civil law (e.g., a fraud victim may sue the fraud perpetrator to avoid the fraud or recover monetary compensation) or criminal law (e.g., a fraud perpetrator may be prosecuted and imprisoned by governmental authorities), or it may cause no loss of money, property, or legal right but still be an element of another civil or criminal wrong. The purpose of fraud may be monetary gain or other benefits, for example by obtaining a passport, travel document, or driver's license, or mortgage fraud, where the perpetrator may attempt to qualify for a mortgage by way of false statements. Internal fraud, also known as "insider fraud", is fraud committed or attempted by someone within an organisation such as an employee. A hoax is a distinct concept that involves deliberate deception without the intention of gain or of materially damaging or depriving a v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Access Control Protocols
A computer is a machine that can be programmed to automatically carry out sequences of arithmetic or logical operations (computation). Modern digital electronic computers can perform generic sets of operations known as programs. These programs enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices such as personal computers and mobile devices such as smartphones. Computers power the Internet, which links billions of computers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Telecommunications Standards
Mobile may refer to: Places * Mobile, Alabama, a U.S. port city * Mobile County, Alabama * Mobile, Arizona, a small town near Phoenix, U.S. * Mobile, Newfoundland and Labrador Arts, entertainment, and media Music Groups and labels * Mobile (band), a Canadian rock band * Mobiles (band), a 1980s British band Other uses in music * ''Mobile'' (album), a 1999 album by Brazilian Paulinho Moska * "Mobile" (song), a 2003 song by Avril Lavigne from ''Let Go'' * "Mobile", a song by Gentle Giant from the album '' Free Hand'' Other uses in arts, entertainment, and media * Mobile (sculpture), a kinetic sculpture constructed to take advantage of the principle of equilibrium * ''Mobile'' (TV series), a British ITV drama * "Mobile", a short story by J. G. Ballard, later renamed " Venus Smiles" * Mobile, a feature of the game ''GunBound'' * '' Mobile Magazine'', a publication on portable electronics Military and law enforcement * '' Garde Mobile'', historic French military unit * Mobil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)
.jpg)
.jpg)

