|
Data Anonymization
Data anonymization is a type of Sanitization (classified information), information sanitization whose intent is privacy protection. It is the process of removing personally identifiable information from data sets, so that the people whom the data describe remain anonymity, anonymous. Overview Data anonymization has been defined as a "process by which personal data is altered in such a way that a data subject can no longer be identified directly or indirectly, either by the data controller alone or in collaboration with any other party." Data anonymization may enable the transfer of information across a boundary, such as between two departments within an agency or between two agencies, while reducing the risk of unintended disclosure, and in certain environments in a manner that enables evaluation and analytics post-anonymization. In the context of Medical record, medical data, anonymized data refers to data from which the patient cannot be identified by the recipient of the info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sanitization (classified Information)
Redaction or sanitization is the process of removing information sensitivity, sensitive information from a document so that it may be distributed to a broader audience. It is intended to allow the selective disclosure of information. Typically, the result is a document that is suitable for publication or for dissemination to others rather than the intended audience of the original document. When the intent is secrecy, secrecy protection, such as in dealing with classified information, redaction attempts to reduce the document's classification level, possibly yielding an unclassified document. When the intent is privacy, privacy protection, it is often called data anonymization. Originally, the term ''sanitization'' was applied to printed documents; it has since been extended to apply to computer files and the problem of data remanence. Government secrecy In the context of government documents, redaction (also called sanitization) generally refers more specifically to the process ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PDF Files
Portable document format (PDF), standardized as ISO 32000, is a file format developed by Adobe in 1992 to present documents, including text formatting and images, in a manner independent of application software, hardware, and operating systems. Based on the PostScript language, each PDF file encapsulates a complete description of a fixed-layout flat document, including the text, fonts, vector graphics, raster images and other information needed to display it. PDF has its roots in "The Camelot Project" initiated by Adobe co-founder John Warnock in 1991. PDF was standardized as ISO 32000 in 2008. The last edition as ISO 32000-2:2020 was published in December 2020. PDF files may contain a variety of content besides flat text and graphics including logical structuring elements, interactive elements such as annotations and form-fields, layers, rich media (including video content), three-dimensional objects using U3D or PRC, and various other data formats. The PDF specificati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Masking And Unmasking By Intelligence Agencies
Unmasking by U.S. intelligence agencies typically occurs after the United States conducts eavesdropping or other intelligence gathering aimed at foreigners or foreign agents, and the name of a U.S. citizen or entity is incidentally collected. Intelligence reports are then disseminated within the U.S. government, with such names masked to protect those U.S. citizens from invasion of privacy. The names can subsequently be unmasked upon request by authorized U.S. government officials under certain circumstances. Unmaskings occur thousands of times each year, totaling 10,012 in 2019. Jargon When an intelligence agency spies on foreign citizens or agents, and information about innocent domestic citizens is uncovered even though they are not targets of investigation, that is called "incidental collection". If the intelligence agency is operating in a manner designed to protect privacy rights, then it normally addresses incidental collection by using a process called "minimization" wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
L-diversity
''l''-diversity, also written as ''ℓ''-diversity, is a form of group based anonymization that is used to preserve privacy in data sets by reducing the granularity of a data representation. This reduction is a trade off that results in some loss of effectiveness of data management or mining algorithms in order to gain some privacy. The ''l''-diversity model is an extension of the ''k''-anonymity model which reduces the granularity of data representation using techniques including generalization and suppression such that any given record maps onto at least ''k-1'' other records in the data. The ''l''-diversity model handles some of the weaknesses in the ''k''-anonymity model where protected identities to the level of ''k''-individuals is not equivalent to protecting the corresponding sensitive values that were generalized or suppressed, especially when the sensitive values within a group exhibit homogeneity. The ''l''-diversity model adds the promotion of intra-group diversity for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
K-anonymity
''k''-anonymity is a property possessed by certain anonymized data. The term ''k''-anonymity was first introduced by Pierangela Samarati and Latanya Sweeney in a paper published in 1998, although the concept dates to a 1986 paper by Tore Dalenius. ''k''-anonymity is an attempt to solve the problem "Given person-specific field-structured data, produce a release of the data with scientific guarantees that the individuals who are the subjects of the data cannot be re-identified while the data remain practically useful." A release of data is said to have the ''k''-anonymity property if the information for each person contained in the release cannot be distinguished from at least k - 1 individuals whose information also appear in the release. The guarantees provided by ''k''-anonymity are aspirational, not mathematical. Methods for ''k''-anonymization To use ''k''-anonymity to process a dataset so that it can be released with privacy protection, a data scientist must first examine ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fillet (redaction)
To fillet in the sense of literary editing is a form of censorship or redaction effected by "cutting out" central letters of a word or name, as if the skeleton of a fish, and replacing them with dashes, to prevent full disclosure (e.g. ' for " William Pitt"). It was frequently practiced in publications of the 18th century in England. Its purpose was to inform interested readers in an obfuscated manner whilst at the same time avoiding the risk of being sued for illegal publication or defamation or libel by the overt naming of persons as having committed certain acts or spoken certain words. It was used in parliamentary reports published in ''The Gentleman's Magazine'' from 1738 onwards under the title of the "Debates in the Senate of Magna Lilliputia" in which in order to circumvent the prohibition of the publication of parliamentary debates of the English Parliament the real names of the various orators were filleted or replaced by pseudonyms or anagrams; for example, Sir Rober ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
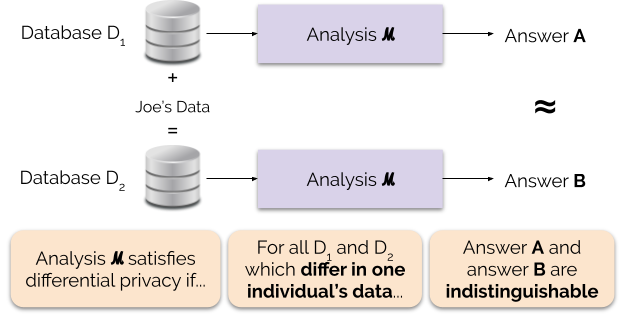
Differential Privacy
Differential privacy (DP) is a mathematically rigorous framework for releasing statistical information about datasets while protecting the privacy of individual data subjects. It enables a data holder to share aggregate patterns of the group while limiting information that is leaked about specific individuals. This is done by injecting carefully calibrated noise into statistical computations such that the utility of the statistic is preserved while provably limiting what can be inferred about any individual in the dataset. Another way to describe differential privacy is as a constraint on the algorithms used to publish aggregate information about a statistical database which limits the disclosure of private information of records in the database. For example, differentially private algorithms are used by some government agencies to publish demographic information or other statistical aggregates while ensuring confidentiality of survey responses, and by companies to collect informa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
De-identification
De-identification is the process used to prevent someone's personal identity from being revealed. For example, data produced during human subject research might be de-identified to preserve the privacy of research participants. Biological data may be de-identified in order to comply with HIPAA regulations that define and stipulate patient privacy laws. When applied to metadata or general data about identification, the process is also known as data anonymization. Common strategies include deleting or masking personal identifiers, such as personal name, and suppressing or generalizing quasi-identifiers, such as date of birth. The reverse process of using de-identified data to identify individuals is known as data re-identification. Successful re-identifications cast doubt on de-identification's effectiveness. A systematic review of fourteen distinct re-identification attacks found "a high re-identification rate ��dominated by small-scale studies on data that was not de-ide ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity
Anonymity describes situations where the acting person's identity is unknown. Anonymity may be created unintentionally through the loss of identifying information due to the passage of time or a destructive event, or intentionally if a person chooses to withhold their identity. There are various situations in which a person might choose to remain anonymous. Acts of charity have been performed anonymously when benefactors do not wish to be acknowledged. A person who feels threatened might attempt to mitigate that threat through anonymity. A witness to a crime might seek to avoid retribution, for example, by anonymously calling a crime tipline. In many other situations (like conversation between strangers, or buying some product or service in a shop), anonymity is traditionally accepted as natural. Some writers have argued that the term "namelessness", though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metadata Removal Tool
Metadata removal tool or metadata scrubber is a type of privacy software built to protect the privacy of its users by removing potentially privacy-compromising metadata from files before they are shared with others, e.g., by sending them as e-mail attachments or by posting them on the Web. Overview Metadata can be found in many types of files such as documents, spreadsheets, presentations, images, and audio files. They can include information such as details on the file authors, file creation and modification dates, geographical location, document revision history, thumbnail images, and comments. Metadata may be added to files by users, but some metadata is often automatically added to files by authoring applications or by devices used to produce the files, without user intervention. Since metadata is sometimes not clearly visible in authoring applications (depending on the application and its settings), there is a risk that the user will be unaware of its existence or will forg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Files
A computer file is a resource for recording data on a computer storage device, primarily identified by its filename. Just as words can be written on paper, so too can data be written to a computer file. Files can be shared with and transferred between computers and mobile devices via removable media, networks, or the Internet. Different types of computer files are designed for different purposes. A file may be designed to store a written message, a document, a spreadsheet, an image, a video, a program, or any wide variety of other kinds of data. Certain files can store multiple data types at once. By using computer programs, a person can open, read, change, save, and close a computer file. Computer files may be reopened, modified, and copied an arbitrary number of times. Files are typically organized in a file system, which tracks file locations on the disk and enables user access. Etymology The word "file" derives from the Latin ''filum'' ("a thread, string"). "File ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |