Total Information Awareness on:
[Wikipedia]
[Google]
[Amazon]
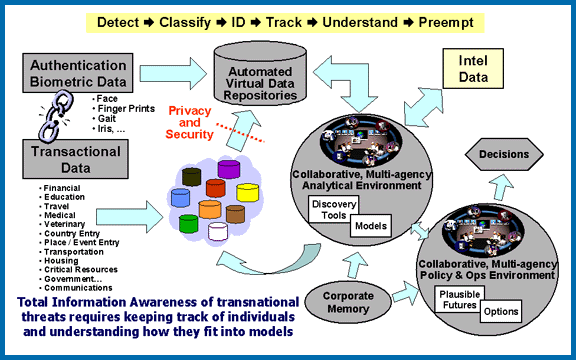
 Total Information Awareness (TIA) was a mass detection program by the United States
Total Information Awareness (TIA) was a mass detection program by the United States
 Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories". Vast amounts of information were to be collected and analyzed, and the available
Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories". Vast amounts of information were to be collected and analyzed, and the available
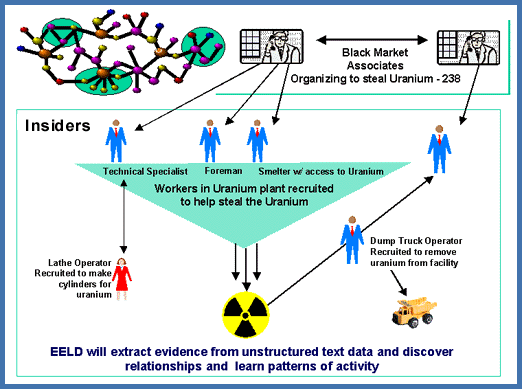 Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the NSA call database, internet histories, or bank records).
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g., financial transactions, communications, travel, etc.). It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the NSA call database, internet histories, or bank records).
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g., financial transactions, communications, travel, etc.). It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
 The human identification at a distance (HumanID) project developed automated
The human identification at a distance (HumanID) project developed automated
 The bio-surveillance project was designed to predict and respond to
The bio-surveillance project was designed to predict and respond to
''
''Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)''
Report to Congress Regarding the Terrorism Information Awareness Program
{{Authority control Counterterrorism in the United States DARPA George W. Bush administration controversies Mass surveillance Management cybernetics Privacy in the United States Privacy of telecommunications Surveillance scandals

 Total Information Awareness (TIA) was a mass detection program by the United States
Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Based on the concept of predictive policing
Predictive policing is the usage of mathematics, predictive analytics, and other analytical techniques in law enforcement to identify potential criminal activity. A report published by the RAND Corporation identified four general categories predi ...
, TIA was meant to correlate detailed information about people in order to anticipate and prevent terrorist incidents before execution. The program modeled specific information sets in the hunt for terrorists around the globe. Admiral John Poindexter called it a "Manhattan Project
The Manhattan Project was a research and development program undertaken during World War II to produce the first nuclear weapons. It was led by the United States in collaboration with the United Kingdom and Canada.
From 1942 to 1946, the ...
for counter-terrorism
Counterterrorism (alternatively spelled: counter-terrorism), also known as anti-terrorism, relates to the practices, military tactics, techniques, and strategies that governments, law enforcement, businesses, and intelligence agencies use to co ...
". According to Senator Ron Wyden
Ronald Lee Wyden ( ; born May 3, 1949) is an American politician serving as the Seniority in the United States Senate, senior United States Senate, United States senator from Oregon, a seat he has held since 1996 United States Senate special el ...
, TIA was the "biggest surveillance program in the history of the United States".
Congress defunded the Information Awareness Office in late 2003 after media reports criticized the government for attempting to establish "Total Information Awareness" over all citizens.
Although the program was formally suspended, other government agencies later adopted some of its software with only superficial changes. TIA's core architecture continued development under the code name "Basketball". According to a 2012 ''New York Times
''The New York Times'' (''NYT'') is an American daily newspaper based in New York City. ''The New York Times'' covers domestic, national, and international news, and publishes opinion pieces, investigative reports, and reviews. As one of ...
'' article, TIA's legacy was "quietly thriving" at the National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
(NSA).
Program synopsis
TIA was intended to be a five-year research project by the Defense Advanced Research Projects Agency (DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military. Originally known as the Adva ...
). The goal was to integrate components from previous and new government intelligence and surveillance programs, including Genoa
Genoa ( ; ; ) is a city in and the capital of the Italian region of Liguria, and the sixth-largest city in Italy. As of 2025, 563,947 people live within the city's administrative limits. While its metropolitan city has 818,651 inhabitan ...
, Genoa II, Genisys, SSNA, EELD, WAE, TIDES, Communicator, HumanID and Bio-Surveillance, with data mining
Data mining is the process of extracting and finding patterns in massive data sets involving methods at the intersection of machine learning, statistics, and database systems. Data mining is an interdisciplinary subfield of computer science and ...
knowledge gleaned from the private sector to create a resource for the intelligence
Intelligence has been defined in many ways: the capacity for abstraction, logic, understanding, self-awareness, learning, emotional knowledge, reasoning, planning, creativity, critical thinking, and problem-solving. It can be described as t ...
, counterintelligence
Counterintelligence (counter-intelligence) or counterespionage (counter-espionage) is any activity aimed at protecting an agency's Intelligence agency, intelligence program from an opposition's intelligence service. It includes gathering informati ...
, and law enforcement
Law enforcement is the activity of some members of the government or other social institutions who act in an organized manner to enforce the law by investigating, deterring, rehabilitating, or punishing people who violate the rules and norms gove ...
communities. These components consisted of information analysis, collaboration, decision-support tools, language translation, data-searching, pattern recognition
Pattern recognition is the task of assigning a class to an observation based on patterns extracted from data. While similar, pattern recognition (PR) is not to be confused with pattern machines (PM) which may possess PR capabilities but their p ...
, and privacy-protection technologies.
TIA research included or planned to include the participation of nine government entities: INSCOM, NSA, DIA, CIA
The Central Intelligence Agency (CIA; ) is a civilian foreign intelligence service of the federal government of the United States tasked with advancing national security through collecting and analyzing intelligence from around the world and ...
, CIFA, STRATCOM, SOCOM, JFCOM, and JWAC. They were to be able to access TIA's programs through a series of dedicated nodes. INSCOM was to house TIA's hardware in Fort Belvoir
Fort Belvoir ( ) is a United States Army installation and a census-designated place (CDP) in Fairfax County, Virginia, United States. It was developed on the site of the former Belvoir (plantation), Belvoir plantation, seat of the prominent Lord ...
, Virginia
Virginia, officially the Commonwealth of Virginia, is a U.S. state, state in the Southeastern United States, Southeastern and Mid-Atlantic (United States), Mid-Atlantic regions of the United States between the East Coast of the United States ...
.
Companies contracted to work on TIA included the Science Applications International Corporation
Science Applications International Corporation, Inc. (SAIC) is an American technology company headquartered in Reston, Virginia that provides government services and information technology support.
History 20th century
The original SAIC was cr ...
, Booz Allen Hamilton
Booz Allen Hamilton Holding Corporation (informally Booz Allen) is the parent of Booz Allen Hamilton Inc., an American company specializing in intelligence, AI, and digital transformation. It is headquartered in McLean, Virginia, in the Washing ...
, Lockheed Martin Corporation, Schafer Corporation, SRS Technologies, Adroit Systems, CACI Dynamic Systems, ASI Systems International, and Syntek Technologies.
Universities enlisted to assist with research and development included Berkeley, Colorado State, Carnegie Mellon
Carnegie may refer to:
People
*Carnegie (surname), including a list of people with the name
**Andrew Carnegie, Scottish-American industrialist and philanthropist
* Clan Carnegie, a lowland Scottish clan
Institutions Named for Andrew Carnegie
* ...
, Columbia, Cornell, Dallas
Dallas () is a city in the U.S. state of Texas and the most populous city in the Dallas–Fort Worth metroplex, the List of Texas metropolitan areas, most populous metropolitan area in Texas and the Metropolitan statistical area, fourth-most ...
, Georgia Tech
The Georgia Institute of Technology (commonly referred to as Georgia Tech, GT, and simply Tech or the Institute) is a public research university and institute of technology in Atlanta, Georgia, United States. Established in 1885, it has the lar ...
, Maryland
Maryland ( ) is a U.S. state, state in the Mid-Atlantic (United States), Mid-Atlantic region of the United States. It borders the states of Virginia to its south, West Virginia to its west, Pennsylvania to its north, and Delaware to its east ...
, MIT
The Massachusetts Institute of Technology (MIT) is a private research university in Cambridge, Massachusetts, United States. Established in 1861, MIT has played a significant role in the development of many areas of modern technology and sc ...
, and Southampton
Southampton is a port City status in the United Kingdom, city and unitary authority in Hampshire, England. It is located approximately southwest of London, west of Portsmouth, and southeast of Salisbury. Southampton had a population of 253, ...
.
Mission
TIA's goal was to revolutionize the United States' ability to detect, classify and identify foreign terrorists and decipher their plans, thereby enabling the U.S. to take timely action to preempt and disrupt terrorist activity. To that end, TIA was to create a counter-terrorism information system that: * Increased information coverage by an order of magnitude and afforded easy scaling * Provided focused warnings within an hour after a triggering event occurred or an evidence threshold was passed * Automatically queued analysts based on partial pattern matches and had patterns that covered 90% of all previously known foreign terrorist attacks * Supported collaboration, analytical reasoning and information sharing so that analysts could hypothesize, test and propose theories and mitigating strategies, so decision-makers could effectively evaluate the impact of policies and courses of action.Components
Genoa
Unlike the other program components, Genoa predated TIA and provided a basis for it. Genoa's primary function wasintelligence analysis
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of delibera ...
to assist human analysts. It was designed to support both top-down and bottom-up approaches; a policymaker could hypothesize an attack and use Genoa to look for supporting evidence of it or compile pieces of intelligence into a diagram and suggest possible outcomes. Human analysts could then modify the diagram to test various cases.
Genoa was independently commissioned in 1996 and completed in 2002 as scheduled.
Genoa II
While Genoa primarily focused on intelligence analysis, Genoa II aimed to provide means by which computers, software agents, policymakers, and field operatives could collaborate.Genisys
 Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories". Vast amounts of information were to be collected and analyzed, and the available
Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories". Vast amounts of information were to be collected and analyzed, and the available database
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and a ...
technology at the time was insufficient for storing and organizing such enormous quantities of data. So they developed techniques for virtual data aggregation to support effective analysis across heterogeneous databases, as well as unstructured public data sources, such as the World Wide Web
The World Wide Web (WWW or simply the Web) is an information system that enables Content (media), content sharing over the Internet through user-friendly ways meant to appeal to users beyond Information technology, IT specialists and hobbyis ...
. "Effective analysis across heterogenous databases" means the ability to take things from databases which are designed to store different types of data—such as a database containing criminal records, a phone call database and a foreign intelligence database. The Web is considered an "unstructured public data source" because it is publicly accessible and contains many different types of data—blogs, emails, records of visits to websites, etc.—all of which need to be analyzed and stored efficiently.
Another goal was to develop "a large, distributed system architecture for managing the huge volume of raw data input, analysis results, and feedback, that will result in a simpler, more flexible data store that performs well and allows us to retain important data indefinitely".
Scalable social network analysis
Scalable social network analysis (SSNA) aimed to develop techniques based onsocial network analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) ...
to model the key characteristics of terrorist groups and discriminate them from other societal groups.
Evidence extraction and link discovery
 Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the NSA call database, internet histories, or bank records).
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g., financial transactions, communications, travel, etc.). It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the NSA call database, internet histories, or bank records).
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g., financial transactions, communications, travel, etc.). It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
Wargaming the asymmetric environment
Wargaming the asymmetric environment (WAE) focused on developing automated technology that could identify predictive indicators of terrorist activity or impending attacks by examining individual and group behavior in broad environmental context and the motivation of specific terrorists.Translingual information detection, extraction and summarization
Translingual information detection, extraction and summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages. Outside groups (such as universities, corporations, etc.) were invited to participate in the annualinformation retrieval
Information retrieval (IR) in computing and information science is the task of identifying and retrieving information system resources that are relevant to an Information needs, information need. The information need can be specified in the form ...
, topic detection and tracking, automatic content extraction, and machine translation
Machine translation is use of computational techniques to translate text or speech from one language to another, including the contextual, idiomatic and pragmatic nuances of both languages.
Early approaches were mostly rule-based or statisti ...
evaluations run by NIST
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into physical s ...
. Cornell University
Cornell University is a Private university, private Ivy League research university based in Ithaca, New York, United States. The university was co-founded by American philanthropist Ezra Cornell and historian and educator Andrew Dickson W ...
, Columbia University
Columbia University in the City of New York, commonly referred to as Columbia University, is a Private university, private Ivy League research university in New York City. Established in 1754 as King's College on the grounds of Trinity Churc ...
, and the University of California, Berkeley
The University of California, Berkeley (UC Berkeley, Berkeley, Cal, or California), is a Public university, public Land-grant university, land-grant research university in Berkeley, California, United States. Founded in 1868 and named after t ...
were given grants to work on TIDES.
Communicator
Communicator was to develop "dialogue interaction" technology to enable warfighters to talk to computers, such that information would be accessible on the battlefield or in command centers without a keyboard-based interface. Communicator was to be wireless, mobile, and to function in a networked environment. The dialogue interaction software was to interpret dialogue's context to improve performance, and to automatically adapt to new topics so conversation could be natural and efficient. Communicator emphasized task knowledge to compensate for natural language effects and noisy environments. Unlike automated translation ofnatural language
A natural language or ordinary language is a language that occurs naturally in a human community by a process of use, repetition, and change. It can take different forms, typically either a spoken language or a sign language. Natural languages ...
speech, which is much more complex due to an essentially unlimited vocabulary and grammar, Communicator takes on task-specific issues so that there are constrained vocabularies (the system only needs to be able to understand language related to war). Research was also started on foreign-language computer interaction for use in coalition operations.
Live exercises were conducted involving small unit logistics operations with the United States Marines
The United States Marine Corps (USMC), also referred to as the United States Marines or simply the Marines, is the Marines, maritime land force service branch of the United States Department of Defense. It is responsible for conducting expedi ...
to test the technology in extreme environments.
Human identification at a distance
 The human identification at a distance (HumanID) project developed automated
The human identification at a distance (HumanID) project developed automated biometric
Biometrics are body measurements and calculations related to human characteristics and features. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used t ...
identification technologies to detect, recognize and identify humans at great distances for "force protection", crime prevention, and "homeland security/defense" purposes.
The goals of HumanID were to:
* Develop algorithms to find and acquire subjects out to 150 meters (500 ft) in range.
* Fuse face and gait
Gait is the pattern of Motion (physics), movement of the limb (anatomy), limbs of animals, including Gait (human), humans, during Animal locomotion, locomotion over a solid substrate. Most animals use a variety of gaits, selecting gait based on s ...
recognition into a 24/7 human identification system.
* Develop and demonstrate a human identification system that operates out to 150 meters (500 ft) using visible imagery.
* Develop a low-power millimeter wave radar system for wide field of view detection and narrow field of view gait classification.
* Characterize gait performance from video for human identification at a distance.
* Develop a multi-spectral infrared and visible face recognition
A facial recognition system is a technology potentially capable of matching a human face from a digital image or a Film frame, video frame against a database of faces. Such a system is typically employed to authenticate users through ID verif ...
system.
A number of universities assisted in designing HumanID. The Georgia Institute of Technology
The Georgia Institute of Technology (commonly referred to as Georgia Tech, GT, and simply Tech or the Institute) is a public university, public research university and Institute of technology (United States), institute of technology in Atlanta, ...
's College of Computing focused on gait recognition. Gait recognition was a key component of HumanID, because it could be employed on low-resolution video feeds and therefore help identify subjects at a distance. They planned to develop a system that recovered static body and stride parameters of subjects as they walked, while also looking into the ability of time-normalized joint angle trajectories in the walking plane as a way of recognizing gait. The university also worked on finding and tracking faces by expressions and speech.
Carnegie Mellon University
Carnegie Mellon University (CMU) is a private research university in Pittsburgh, Pennsylvania, United States. The institution was established in 1900 by Andrew Carnegie as the Carnegie Technical Schools. In 1912, it became the Carnegie Institu ...
's Robotics Institute (part of the School of Computer Science) worked on dynamic face recognition. The research focused primarily on the extraction of body biometric features from video and identifying subjects from those features. To conduct its studies, the university created databases of synchronized multi-camera video sequences of body motion, human faces under a wide range of imaging conditions, AU coded expression videos, and hyperspectal and polarimetric images of faces. The video sequences of body motion data consisted of six separate viewpoints of 25 subjects walking on a treadmill. Four separate 11-second gaits were tested for each: slow walk, fast walk, inclined, and carrying a ball.
The University of Maryland
The University of Maryland, College Park (University of Maryland, UMD, or simply Maryland) is a public land-grant research university in College Park, Maryland, United States. Founded in 1856, UMD is the flagship institution of the Univ ...
's Institute for Advanced Computer Studies' research focused on recognizing people at a distance by gait and face. Also to be used were infrared
Infrared (IR; sometimes called infrared light) is electromagnetic radiation (EMR) with wavelengths longer than that of visible light but shorter than microwaves. The infrared spectral band begins with the waves that are just longer than those ...
and five-degree-of-freedom cameras. Tests included filming 38 male and 6 female subjects of different ethnicities and physical features walking along a T-shaped path from various angles.
The University of Southampton
The University of Southampton (abbreviated as ''Soton'' in post-nominal letters) is a public university, public research university in Southampton, England. Southampton is a founding member of the Russell Group of research-intensive universit ...
's Department of Electronics and Computer Science was developing an "automatic gait recognition" system and was in charge of compiling a database to test it. The University of Texas at Dallas
The University of Texas at Dallas (UTD or UT Dallas) is a public research university in Richardson, Texas, United States. It is the northernmost institution of the University of Texas System. It was initially founded in 1961 as a private res ...
was compiling a database to test facial systems. The data included a set of nine static pictures taken from different viewpoints, a video of each subject looking around a room, a video of the subject speaking, and one or more videos of the subject showing facial expressions. Colorado State University
Colorado State University (Colorado State or CSU) is a Public university, public Land-grant university, land-grant research university in Fort Collins, Colorado, United States. It is the flagship university of the Colorado State University Syst ...
developed multiple systems for identification via facial recognition. Columbia University
Columbia University in the City of New York, commonly referred to as Columbia University, is a Private university, private Ivy League research university in New York City. Established in 1754 as King's College on the grounds of Trinity Churc ...
participated in implementing HumanID in poor weather.
Bio-surveillance
 The bio-surveillance project was designed to predict and respond to
The bio-surveillance project was designed to predict and respond to bioterrorism
Bioterrorism is terrorism involving the intentional release or dissemination of biological agents. These agents include bacteria, viruses, insects, fungi, and/or their toxins, and may be in a naturally occurring or a human-modified form, in mu ...
by monitoring non-traditional data sources such as animal sentinels, behavioral indicators, and pre-diagnostic medical data. It would leverage existing disease models, identify abnormal health early indicators, and mine existing databases to determine the most valuable early indicators for abnormal health conditions.
Scope of surveillance
As a "virtual, centralized, grand database", the scope of surveillance included credit card purchases, magazine subscriptions, web browsing histories, phone records, academic grades, bank deposits, gambling histories, passport applications, airline and railway tickets, driver's licenses, gun licenses, toll records, judicial records, and divorce records. Health and biological information TIA collected included drug prescriptions, medical records, fingerprints, gait, face and iris data, andDNA
Deoxyribonucleic acid (; DNA) is a polymer composed of two polynucleotide chains that coil around each other to form a double helix. The polymer carries genetic instructions for the development, functioning, growth and reproduction of al ...
.
Privacy
TIA's Genisys component, in addition to integrating and organizing separate databases, was to run an internal "privacy protection program". This was intended to restrict analysts' access to irrelevant information on private U.S. citizens, enforceprivacy law
Privacy law is a set of regulations that govern the collection, storage, and utilization of personal information from healthcare, governments, companies, public or private entities, or individuals.
Privacy laws are examined in relation to an ind ...
s and policies, and report misuses of data. There were also plans for TIA to have an application that could "anonymize" data, so that information could be linked to an individual only by court order (especially for medical records gathered by the bio-surveillance project). A set of audit logs were to be kept, which would track whether innocent Americans' communications were getting caught up in relevant data.
History
The term ''total information awareness'' was first coined at the 1999 annual DARPAtech conference in a presentation by the deputy director of the Office of Information Systems Management, Brian Sharkey. Sharkey applied the phrase to a conceptual method by which the government could sift through massive amounts of data becoming available via digitization and draw important conclusions.Early developments
TIA was proposed as a program shortly after theSeptember 11 attacks
The September 11 attacks, also known as 9/11, were four coordinated Islamist terrorist suicide attacks by al-Qaeda against the United States in 2001. Nineteen terrorists hijacked four commercial airliners, crashing the first two into ...
in 2001, by Rear Admiral John Poindexter. A former national security adviser to President Ronald Reagan
Ronald Wilson Reagan (February 6, 1911 – June 5, 2004) was an American politician and actor who served as the 40th president of the United States from 1981 to 1989. He was a member of the Republican Party (United States), Republican Party a ...
and a key player in the Iran–Contra affair
The Iran–Contra affair (; ), also referred to as the Iran–Contra scandal, the Iran Initiative, or simply Iran–Contra, was a political scandal in the United States that centered on arms trafficking to Iran between 1981 and 1986, facilitat ...
, he was working with Syntek Technologies, a company often contracted out by the government for work on defense projects. TIA was officially commissioned during the 2002 fiscal year
A fiscal year (also known as a financial year, or sometimes budget year) is used in government accounting, which varies between countries, and for budget purposes. It is also used for financial reporting by businesses and other organizations. La ...
. In January 2002 Poindexter was appointed Director of the newly created Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology ...
division of DARPA, which managed TIA's development. The office temporarily operated out of the fourth floor of DARPA's headquarters, while Poindexter looked for a place to permanently house TIA's researchers. Soon Project Genoa was completed and its research moved on to Genoa II.
Late that year, the Information Awareness Office awarded the Science Applications International Corporation
Science Applications International Corporation, Inc. (SAIC) is an American technology company headquartered in Reston, Virginia that provides government services and information technology support.
History 20th century
The original SAIC was cr ...
(SAIC) a $19 million contract to develop the "Information Awareness Prototype System", the core architecture to integrate all of TIA's information extraction, analysis, and dissemination tools. This was done through its consulting arm, Hicks & Associates, which employed many former Defense Department and military officials.
TIA's earliest version employed software called "Groove", which had been developed in 2000 by Ray Ozzie
Raymond "Ray" Ozzie (born November 20, 1955) is an American software industry entrepreneur who held the positions of Chief Technical Officer and Chief Software Architect at Microsoft between 2005 and 2010. Before Microsoft, he was best known for ...
. Groove made it possible for analysts from many different agencies to share intelligence data instantly, and linked specialized programs that were designed to look for patterns of suspicious behavior.
Congressional restrictions and termination
On 24 January 2003, theUnited States Senate
The United States Senate is a chamber of the Bicameralism, bicameral United States Congress; it is the upper house, with the United States House of Representatives, U.S. House of Representatives being the lower house. Together, the Senate and ...
voted to limit TIA by restricting its ability to gather information from emails and the commercial databases of health, financial and travel companies. According to the ''Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)'' passed in February, the Defense Department was given 90 days to compile a report laying out a schedule of TIA's development and the intended use of allotted funds or face a cutoff of support.
The report arrived on May 20. It disclosed that the program's computer tools were still in their preliminary testing phase. Concerning the pattern recognition of transaction information, only synthetic data created by researchers was being processed. The report also conceded that a full prototype of TIA would not be ready until the 2007 fiscal year. Also in May, Total Information Awareness was renamed Terrorism Information Awareness in an attempt to stem the flow of criticism on its information-gathering practices on average citizens.
At some point in early 2003, the National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and proces ...
began installing access nodes on TIA's classified network. The NSA then started running stacks of emails and intercepted communications through TIA's various programs.
Following a scandal in the Department of Defense involving a proposal to reward investors who predicted terrorist attacks, Poindexter resigned from office on 29 August.
On September 30, 2003, Congress officially cut off TIA's funding and the Information Awareness Office (with the Senate voting unanimously against it) because of its unpopular perception by the general public and the media. Senators Ron Wyden
Ronald Lee Wyden ( ; born May 3, 1949) is an American politician serving as the Seniority in the United States Senate, senior United States Senate, United States senator from Oregon, a seat he has held since 1996 United States Senate special el ...
and Byron Dorgan led the effort.
After 2003
Reports began to emerge in February 2006 that TIA's components had been transferred to the authority of the NSA. In the Department of Defenseappropriations bill
An appropriation bill, also known as supply bill or spending bill, is a proposed law that authorizes the expenditure of government funds. It is a bill that sets money aside for specific spending. In some democracies, approval of the legislature ...
for the 2004 fiscal year, a classified annex provided the funding. It was stipulated that the technologies were limited for military or foreign intelligence purposes against non-U.S. citizens. Most of the original project goals and research findings were preserved, but the privacy protection mechanics were abandoned.
Topsail
Genoa II, which focused on collaboration between machines and humans, was renamed "Topsail" and handed over to the NSA's Advanced Research and Development Activity, or ARDA (ARDA was later moved to theDirector of National Intelligence
The director of national intelligence (DNI) is a Cabinet of the United States#Current Cabinet and Cabinet-rank officials, cabinet-level Federal government of the United States, United States government intelligence and security official. The p ...
's control as the Disruptive Technologies Office). Tools from the program were used in the war in Afghanistan
War in Afghanistan, Afghan war, or Afghan civil war may refer to:
*Conquest of Afghanistan by Alexander the Great (330 BC – 327 BC), the conquest of Afghanistan by the Macedonian Empire
* Muslim conquests of Afghanistan, a series of campaigns in ...
and other parts of the War on Terror. In October 2005, the SAIC signed a $3.7 million contract for work on Topsail. In early 2006 a spokesman for the Air Force Research Laboratory
The Air Force Research Laboratory (AFRL) is a scientific research and development detachment of the United States Air Force Air Force Materiel Command, Materiel Command dedicated to leading the discovery, development, and integration of direct- ...
said that Topsail was "in the process of being canceled due to lack of funds". When asked about Topsail in a Senate Intelligence Committee hearing that February, both National Intelligence Director John Negroponte
John Dimitri Negroponte (; born July 21, 1939) is an American diplomat. In 2018, he was a James R. Schlesinger Distinguished Professor at the Miller Center for Public Affairs at the University of Virginia. He is a former J.B. and Maurice C. Shapi ...
and FBI Director
The director of the Federal Bureau of Investigation is the head of the Federal Bureau of Investigation (FBI), a United States federal law enforcement agency, and is responsible for its day-to-day operations. The FBI director is appointed for a ...
Robert Mueller
Robert Swan Mueller III (; born August 7, 1944) is an American lawyer who served as the sixth director of the Federal Bureau of Investigation (FBI) from 2001 to 2013.
A graduate of Princeton University and New York University, Mueller served a ...
said they did not know the program's status. Negroponte's deputy, former NSA director, Michael V. Hayden, said, "I'd like to answer in closed session."
Basketball
The Information Awareness Prototype System was reclassified as "Basketball" and work on it continued by SAIC, supervised by ARDA. As late as September 2004, Basketball was fully funded by the government and being tested in a research center jointly run by ARDA and SAIC.TIA Lives On''
National Journal
''National Journal'' is an advisory services company based in Washington, D.C., offering services in government affairs, advocacy communications, stakeholder mapping, and policy brands research for government and business leaders. It publishes ...
'', 23 February 2006, retrieved 14 June 2016
Criticism
Critics allege that the program could be abused by government authorities as part of their practice ofmass surveillance in the United States
The practice of mass surveillance in the United States dates back to wartime monitoring and censorship of international communications from, to, or which passed through the United States. After the First and Second World Wars, mass surveill ...
. In an op-ed
An op-ed, short for "opposite the editorial page," is a type of written prose commonly found in newspapers, magazines, and online publications. They usually represent a writer's strong and focused opinion on an issue of relevance to a targeted a ...
for ''The New York Times
''The New York Times'' (''NYT'') is an American daily newspaper based in New York City. ''The New York Times'' covers domestic, national, and international news, and publishes opinion pieces, investigative reports, and reviews. As one of ...
'', William Safire
William Lewis Safire (; Safir; December 17, 1929 – September 27, 2009Safire, William (1986). ''Take My Word for It: More on Language.'' Times Books. . p. 185.) was an American author, columnist, journalist, and presidential speechwriter. He ...
called it "the supersnoop's dream: a Total Information Awareness about every U.S. citizen".
Hans Mark, a former director of defense research and engineering at the University of Texas
The University of Texas at Austin (UT Austin, UT, or Texas) is a public research university in Austin, Texas, United States. Founded in 1883, it is the flagship institution of the University of Texas System. With 53,082 students as of fall 2 ...
, called it a "dishonest misuse of DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military. Originally known as the Adva ...
".
The American Civil Liberties Union
The American Civil Liberties Union (ACLU) is an American nonprofit civil rights organization founded in 1920. ACLU affiliates are active in all 50 states, Washington, D.C., and Puerto Rico. The budget of the ACLU in 2024 was $383 million.
T ...
launched a campaign to terminate TIA's implementation, claiming that it would "kill privacy in America" because "every aspect of our lives would be catalogued". The ''San Francisco Chronicle
The ''San Francisco Chronicle'' is a newspaper serving primarily the San Francisco Bay Area of Northern California. It was founded in 1865 as ''The Daily Dramatic Chronicle'' by teenage brothers Charles de Young and M. H. de Young, Michael H. ...
'' criticized the program for "Fighting terror by terrifying U.S. citizens".
Still, in 2013 former Director of National Intelligence
The director of national intelligence (DNI) is a Cabinet of the United States#Current Cabinet and Cabinet-rank officials, cabinet-level Federal government of the United States, United States government intelligence and security official. The p ...
James Clapper
James Robert Clapper Jr. (born March 14, 1941) is a retired lieutenant general in the United States Air Force and former Director of National Intelligence. Clapper has held several key positions within the United States Intelligence Community. ...
lied about a massive data collection on US citizens and others. Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is a former National Security Agency (NSA) intelligence contractor and whistleblower who leaked classified documents revealing the existence of global surveillance programs.
Born in 1983 in Elizabeth ...
said that because of Clapper's lie he lost hope to change things formally.
In popular culture
In the 2008 British television series ''The Last Enemy'', TIA is portrayed as a UK-based surveillance database that can be used to track and monitor anybody by putting all available government information in one place.See also
*LifeLog
A lifelog is a personal record of one's daily life in a varying amount of detail, for a variety of purposes. The record contains a comprehensive dataset of a human's activities. The data could be used to increase knowledge about how people liv ...
* Pre-crime
''Pre-crime'' (or ''precrime'') is the idea that the occurrence of a crime can be anticipated before it happens. The term was coined by science fiction author Philip K. Dick, and is increasingly used in academic literature to describe and critic ...
* Privacy laws of the United States
Privacy laws of the United States deal with several different legal concepts. One is the ''invasion of privacy'', a tort based in common law allowing an aggrieved party to bring a lawsuit against an individual who unlawfully intrudes into their ...
* Situation awareness
Situational awareness or situation awareness, often abbreviated as SA is the understanding of an environment, its elements, and how it changes with respect to time or other factors. It is also defined as the perception of the elements in the envi ...
References
External links
''Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)''
Report to Congress Regarding the Terrorism Information Awareness Program
{{Authority control Counterterrorism in the United States DARPA George W. Bush administration controversies Mass surveillance Management cybernetics Privacy in the United States Privacy of telecommunications Surveillance scandals