|
Disruptive Technologies Office
The Disruptive Technology Office (DTO) was a funding agency within the United States Intelligence Community. It was previously known as the Advanced Research and Development Activity (ARDA). In December 2007, DTO was folded into the newly created IARPA. ARDA was created in 1998 after the model of DARPA by the Director of Central Intelligence and the Department of Defense, and took responsibility for funding some of DARPA's projects. ARDA evaluates proposals and funds speculative research, particularly in the fields of data mining, video processing, and quantum computing. There has been speculation that the DTO is continuing research efforts started under the Total Information Awareness program (TIA) in DARPA's Information Awareness Office (IAO). Data-mining activities within the US Department of Defense are controversial and have met with public and congressional disapproval. Although ARDA's budget is presumably classified as part of the intelligence budget, the ''New York Time ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fort George G
A fortification (also called a fort, fortress, fastness, or stronghold) is a military construction designed for the defense of territories in warfare, and is used to establish rule in a region during peacetime. The term is derived from Latin ("strong") and ("to make"). From very early history to modern times, defensive walls have often been necessary for cities to survive in an ever-changing world of invasion and conquest. Some settlements in the Indus Valley Civilization were the first small cities to be fortified. In ancient Greece, large cyclopean stone walls fitted without mortar had been built in Mycenaean Greece, such as the ancient site of Mycenae. A Greek '' phrourion'' was a fortified collection of buildings used as a military garrison, and is the equivalent of the Roman castellum or fortress. These constructions mainly served the purpose of a watch tower, to guard certain roads, passes, and borders. Though smaller than a real fortress, they acted as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
1998 Establishments In The United States
1998 was designated as the ''International Year of the Ocean''. Events January * January 6 – The ''Lunar Prospector'' spacecraft is launched into orbit around the Moon, and later finds evidence for frozen water, in soil in permanently shadowed craters near the Moon's poles. * January 11 – Over 100 people are killed in the Sidi-Hamed massacre in Algeria. * January 12 – Nineteen European nations agree to forbid human cloning. * January 17 – The ''Drudge Report'' breaks the story about U.S. President Bill Clinton's alleged affair with Monica Lewinsky, which will lead to the House of Representatives' impeachment of him. February * February 3 – Cavalese cable car disaster: A United States military pilot causes the deaths of 20 people near Trento, Italy, when his low-flying EA-6B Prowler severs the cable of a cable-car. * February 4 – The 5.9 Afghanistan earthquake shakes the Takhar Province with a maximum Mercalli intensity of VII (''Very strong''). With up ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Archive
The Internet Archive is an American 501(c)(3) organization, non-profit organization founded in 1996 by Brewster Kahle that runs a digital library website, archive.org. It provides free access to collections of digitized media including websites, Application software, software applications, music, audiovisual, and print materials. The Archive also advocates a Information wants to be free, free and open Internet. Its mission is committing to provide "universal access to all knowledge". The Internet Archive allows the public to upload and download digital material to its data cluster, but the bulk of its data is collected automatically by its web crawlers, which work to preserve as much of the public web as possible. Its web archiving, web archive, the Wayback Machine, contains hundreds of billions of web captures. The Archive also oversees numerous Internet Archive#Book collections, book digitization projects, collectively one of the world's largest book digitization efforts. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Computer
A quantum computer is a computer that exploits quantum mechanical phenomena. On small scales, physical matter exhibits properties of both particles and waves, and quantum computing takes advantage of this behavior using specialized hardware. Classical physics cannot explain the operation of these quantum devices, and a scalable quantum computer could perform some calculations exponentially faster than any modern "classical" computer. Theoretically a large-scale quantum computer could break some widely used encryption schemes and aid physicists in performing physical simulations; however, the current state of the art is largely experimental and impractical, with several obstacles to useful applications. The basic unit of information in quantum computing, the qubit (or "quantum bit"), serves the same function as the bit in classical computing. However, unlike a classical bit, which can be in one of two states (a binary), a qubit can exist in a superposition of its two " ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Encryption
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), SSH, S/MIME, and P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Large Scale Concept Ontology For Multimedia
The Large-Scale Concept Ontology for Multimedia project was a series of workshops held from April 2004 to September 2006Naphade, ''et al.'', "Large Scale Concept Ontology for Multimedia: VACE Workshop Report," for the purpose of defining a standard formal vocabulary for the annotation and retrieval of video. Mandate The Large-Scale Concept Ontology for Multimedia project was sponsored by the Disruptive Technology Office and brought together representatives from a variety of research communities, such as multimedia learning, information retrieval, computational linguistics, library science, and knowledge representation, as well as "user" communities such as intelligence agencies and broadcasters, to work collaboratively towards defining a set of 1,000 concepts. Individually, each concept was to meet the following criteria: *Utility: the concepts must support realistic video retrieval problems *Feasibility: the concepts are capable or will be capable of detection given the near-term ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Maryland
Maryland ( ) is a U.S. state, state in the Mid-Atlantic (United States), Mid-Atlantic region of the United States. It borders the states of Virginia to its south, West Virginia to its west, Pennsylvania to its north, and Delaware to its east, as well as with the Atlantic Ocean to its east, and the national capital and federal district of Washington, D.C. to the southwest. With a total area of , Maryland is the List of U.S. states and territories by area, ninth-smallest state by land area, and its population of 6,177,224 ranks it the List of U.S. states and territories by population, 18th-most populous state and the List of states and territories of the United States by population density, fifth-most densely populated. Maryland's capital city is Annapolis, Maryland, Annapolis, and the state's most populous city is Baltimore. Maryland's coastline was first explored by Europeans in the 16th century. Prior to that, it was inhabited by several Native Americans in the United States ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
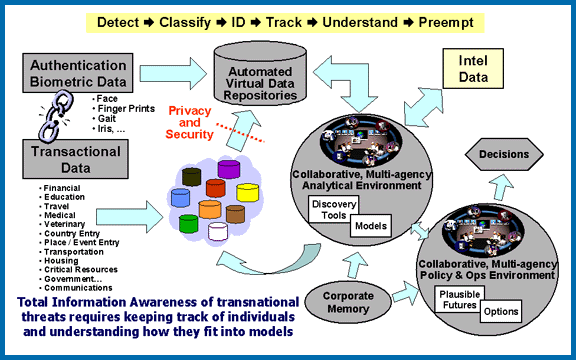
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric warfare, asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Aware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States Intelligence Community
The United States Intelligence Community (IC) is a group of separate US federal government, U.S. federal government intelligence agencies and subordinate organizations that work to conduct Intelligence assessment, intelligence activities which support the foreign policy of the United States, foreign policy and national security of the United States, national security interests of the United States. Member organizations of the IC include intelligence agency, intelligence agencies, military intelligence, and civilian intelligence and analysis offices within United States federal executive departments, federal executive departments. The IC is overseen by the Office of the Director of National Intelligence (ODNI), which is headed by the Director of National Intelligence, director of national intelligence (DNI) who reports directly to the president of the United States. The IC was established by Executive Order 12333 ("United States Intelligence Activities"), signed on December 4, 1 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |