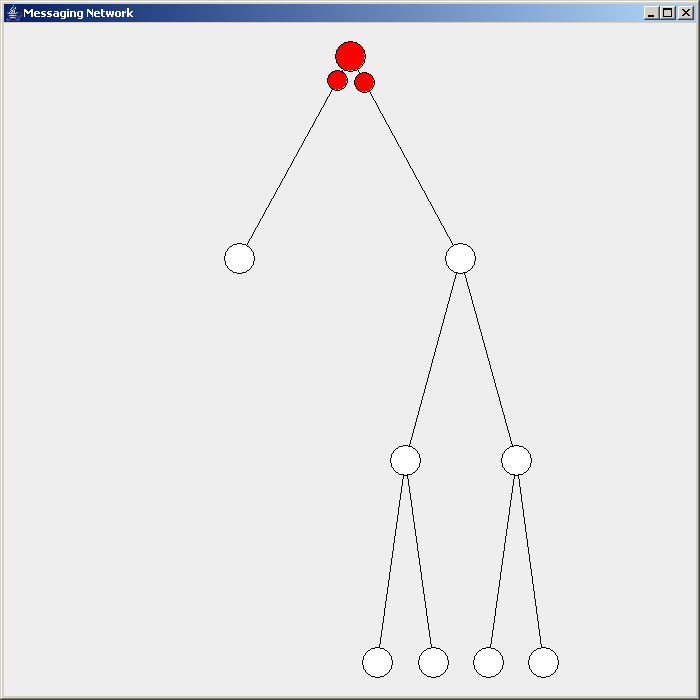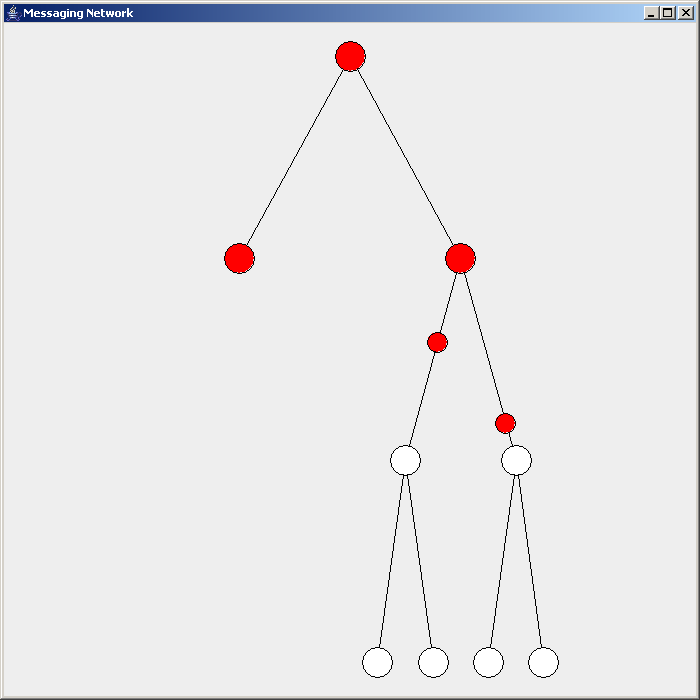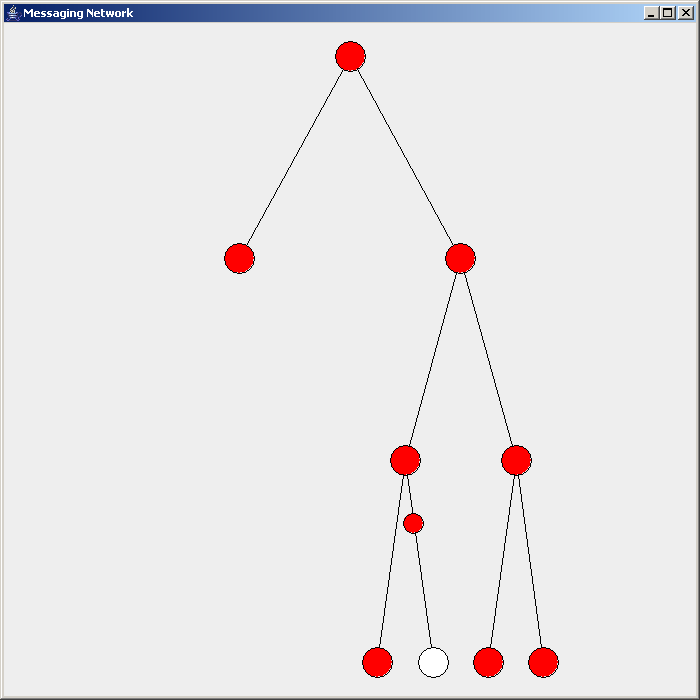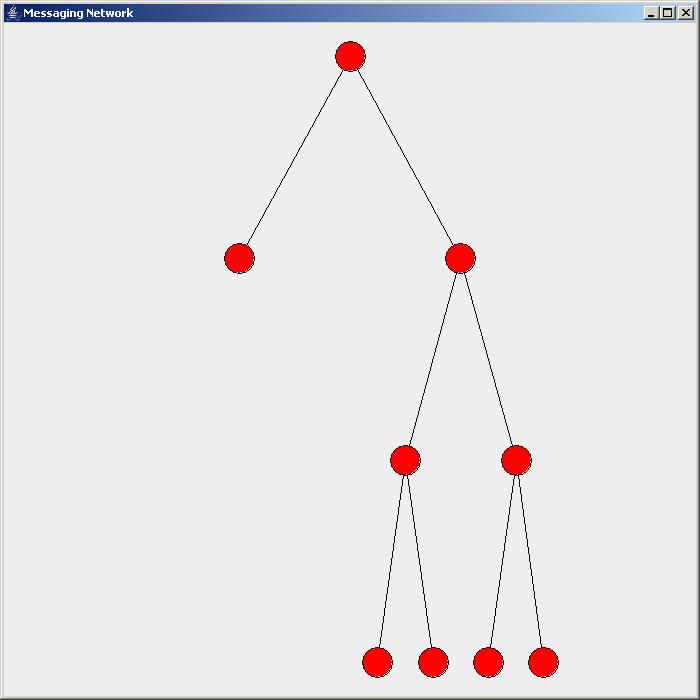
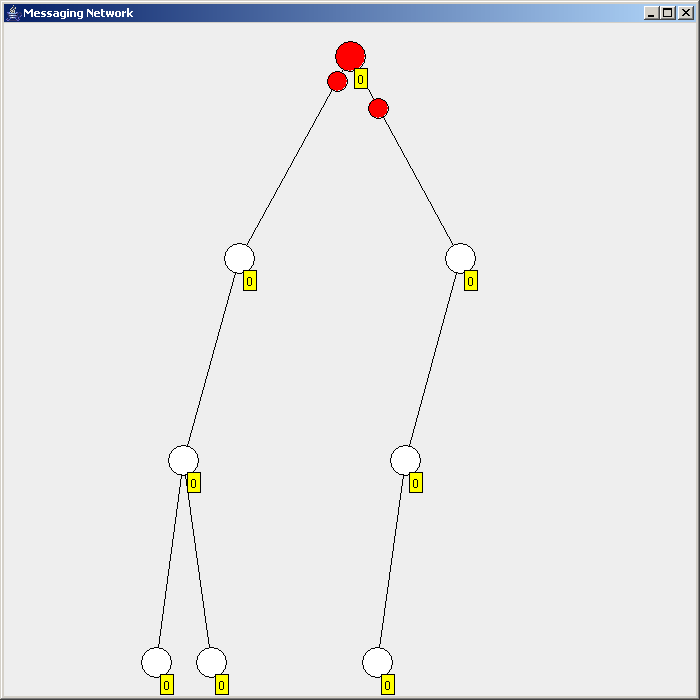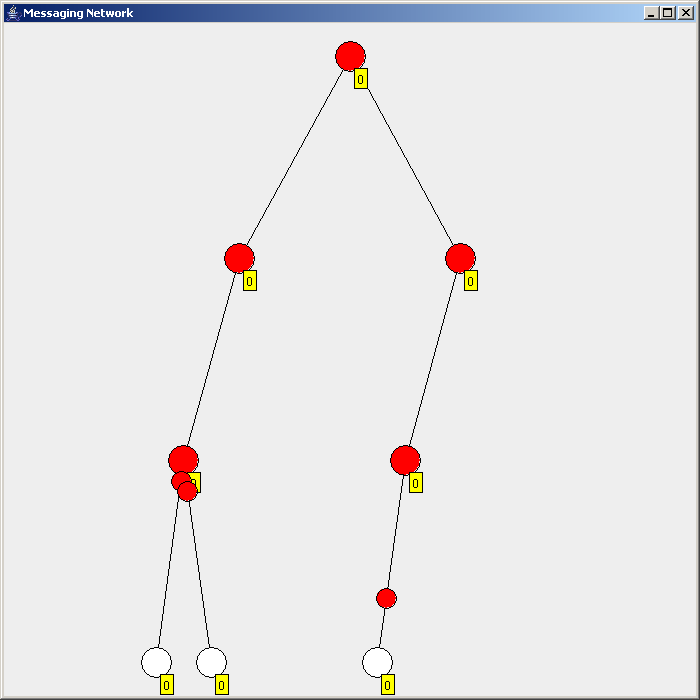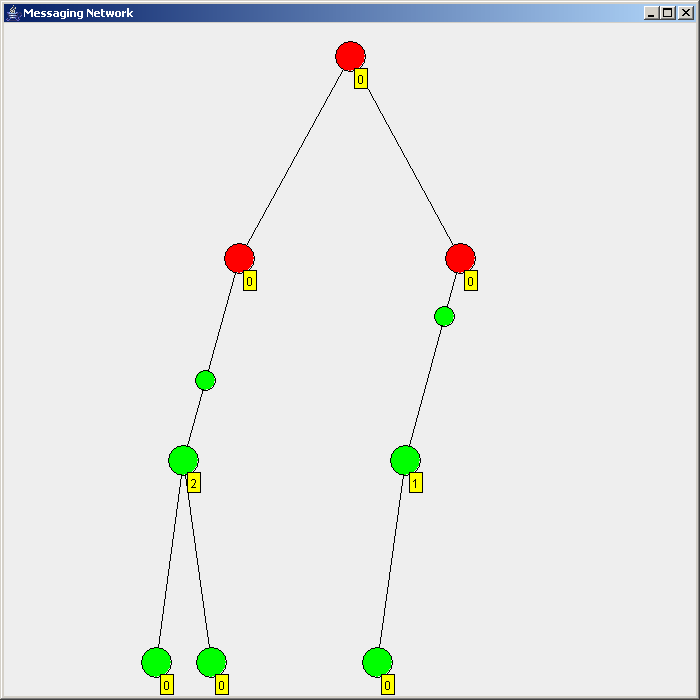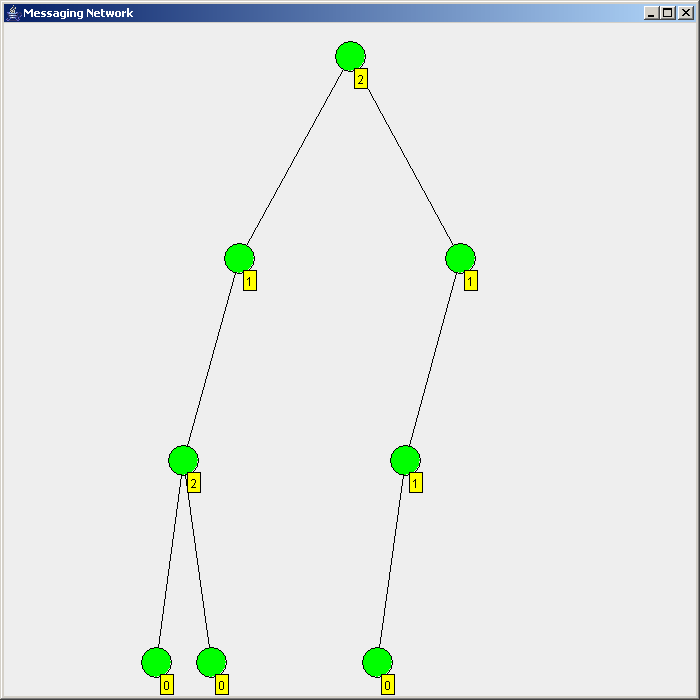
 Flooding is used in computer network
Flooding is used in computer network routing algorithms
Routing is the process of selecting a path for traffic in a network or between or across multiple networks. Broadly, routing is performed in many types of networks, including circuit-switched networks, such as the public switched telephone net ...
in which every incoming packet
Packet may refer to:
* A small container or pouch
** Packet (container), a small single use container
** Cigarette packet
** Sugar packet
* Network packet, a formatted unit of data carried by a packet-mode computer network
* Packet radio, a form ...
is sent through every outgoing link except the one it arrived on.
Flooding is used in bridging and in systems such as Usenet
Usenet (), a portmanteau of User's Network, is a worldwide distributed discussion system available on computers. It was developed from the general-purpose UUCP, Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Elli ...
and peer-to-peer file sharing
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program th ...
and as part of some routing protocol
A routing protocol specifies how routers communicate with each other to distribute information that enables them to select paths between nodes on a computer network. Routers perform the traffic directing functions on the Internet; data packet ...
s, including OSPF
Open Shortest Path First (OSPF) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous sys ...
, DVMRP The Distance Vector Multicast Routing Protocol (DVMRP), defined in , is a routing protocol used to share information between routers to facilitate the transportation of IP multicast packets among networks. It formed the basis of the Internet's hist ...
, and those used in ad-hoc wireless network
A wireless ad hoc network (WANET) or mobile ad hoc network (MANET) is a decentralized type of wireless network. The network is ad hoc because it does not rely on a pre-existing infrastructure, such as routers or wireless access points. Instead, ...
s (WANETs).
Types
There are generally two types of flooding available, uncontrolled flooding and controlled flooding. In ''uncontrolled flooding'' each node unconditionally distributes packets to each of its neighbors. Without conditional logic to prevent indefinite recirculation of the same packet,broadcast storm
A broadcast storm or broadcast radiation is the accumulation of broadcast and multicast traffic on a computer network. Extreme amounts of broadcast traffic constitute a ''broadcast storm''. It can consume sufficient network resources so as to re ...
s are a hazard.
''Controlled flooding'' has its own two algorithms to make it reliable, SNCF ( Sequence Number Controlled Flooding) and RPF (reverse-path forwarding
Reverse-path forwarding (RPF) is a technique used in modern routers for the purposes of ensuring loop-free forwarding of multicast packets in multicast routing and to help prevent IP address spoofing in unicast routing.
In standard unicast IP ...
). In SNCF, the node attaches its own address and sequence number to the packet, since every node has a memory of addresses and sequence numbers. If it receives a packet in memory, it drops it immediately while in RPF, the node will only send the packet forward. If it is received from the next node, it sends it back to the sender.
Algorithms
There are several variants of flooding algorithms. Most work roughly as follows: #Each node acts as both a transmitter and a receiver. #Each node tries to forward every message to every one of its neighbors except the source node. This results in every message eventually being delivered to all reachable parts of the network. Algorithms may need to be more complex than this, since, in some case, precautions have to be taken to avoid wasted duplicate deliveries and infinite loops, and to allow messages to eventually expire from the system.Selective flooding
A variant of flooding called selective flooding partially addresses these issues by only sending packets to routers in the same direction. In selective flooding, the routers don't send every incoming packet on every line but only on those lines which are going approximately in the right direction.Advantages
The advantages of this method are that it is very simple to implement, if a packet can be delivered then it will (probably multiple times), and since flooding naturally utilizes every path through the network it will also use the shortest path.Disadvantages
Flooding can be costly in terms of wasted bandwidth. While a message may only have one destination it has to be sent to every host. In the case of aping flood
A ping flood is a simple denial-of-service attack where the attacker overwhelms the victim with ICMP "echo request" ( ping) packets. This is most effective by using the flood option of ping which sends ICMP packets as fast as possible without wa ...
or a denial of service attack
In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host co ...
, it can be harmful to the reliability of a computer network
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or b ...
.
Messages can become duplicated in the network further increasing the load on the network as well as requiring an increase in processing complexity to disregard duplicate messages. Duplicate packets may circulate forever, unless certain precautions are taken:
* Use a hop count
In wired computer networking a hop occurs when a packet is passed from one network segment to the next. Data packets pass through routers as they travel between source and destination. The hop count refers to the number of network devices thro ...
or a time to live
Time to live (TTL) or hop limit is a mechanism which limits the lifespan or lifetime of data in a computer or network. TTL may be implemented as a counter (digital), counter or timestamp attached to or embedded in the data. Once the prescribed ev ...
(TTL) count and include it with each packet. This value should take into account the number of nodes that a packet may have to pass through on the way to its destination.
* Have each node keep track of every packet seen and only forward each packet once.
* Enforce a network topology
Network topology is the arrangement of the elements (Data link, links, Node (networking), nodes, etc.) of a communication network. Network topology can be used to define or describe the arrangement of various types of telecommunication networks, ...
without loop
Loop or LOOP may refer to:
Brands and enterprises
* Loop (mobile), a Bulgarian virtual network operator and co-founder of Loop Live
* Loop, clothing, a company founded by Carlos Vasquez in the 1990s and worn by Digable Planets
* Loop Mobile, an ...
s.
Examples
InOpen Shortest Path First
Open Shortest Path First (OSPF) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single Autonomous syste ...
(OSPF), flooding is used for transferring updates to the topology ( LSAs).
In low data rate communications, flooding can achieve fast and robust data communications in dedicated protocols such as VEmesh,virtual-extension.com which operates in the Sub-1 GHz frequency band and Bluetooth mesh networking
Bluetooth Mesh is a computer mesh networking standard based on Bluetooth Low Energy that allows for many-to-many communication over Bluetooth radio. The Bluetooth Mesh specifications were defined in the Mesh Profile and Mesh Model specification ...
, which operates in the 2.4 GHz frequency band. Both these protocols serve as underlying technologies in the Digital Addressable Lighting Interface
Digital Addressable Lighting Interface (DALI) is a trademark for network-based products that control lighting. The underlying technology was established by a consortium of lighting equipment manufacturers as a successor for 1-10 V/ lighting ...
in use in professional and commercial lighting control.
See also
*Broadcasting (networking)
In computer networking, telecommunication and information theory, broadcasting is a method of transferring a message to all recipients simultaneously. Broadcasting can be performed as a high-level operation in a program, for example, broadcast ...
*Flood search routing In a telephone network, flood search routing is non-deterministic routing in which a dialed number received at a switch is transmitted to all switches, ''i.e.,'' flooded, in the area code directly connected to that switch; if the dialed number is no ...
*Multicast
In computer networking, multicast is a type of group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast differs from ph ...
*Spanning Tree Protocol
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree al ...
References
{{reflist, refs= {{cite book , author-first1=Andrew S. , author-last1=Tanenbaum , author-link1=Andrew S. Tanenbaum , author-first2=David J. , author-last2=Wetherall , title=Computer Networks , edition=5th , date=2010-03-23 , publisher=Pearson Education
Pearson Education, known since 2011 as simply Pearson, is the educational publishing and services subsidiary of the international corporation Pearson plc. The subsidiary was formed in 1998, when Pearson plc acquired Simon & Schuster's educatio ...
, isbn=978-0-13-212695-3 , pages=368–370
{{cite web , title=Controlled Flooding in Wireless Ad-hoc Networks , author-first1=Ashikur , author-last1=Rahman , author-first2=Wlodek , author-last2=Olesinski , author-first3=Pawel , author-last3=Gburzynski , publisher=University of Alberta
The University of Alberta (also known as U of A or UAlberta, ) is a public research university located in Edmonton, Alberta, Canada. It was founded in 1908 by Alexander Cameron Rutherford, the first premier of Alberta, and Henry Marshall Tory, t ...
, Department of Computing Science , location=Edmonton, Alberta, Canada , date=2004 , work=International Workshop on Wireless Ad-Hoc Networks , url=http://www.senserf.com/pg/PAPERS/tarp1.pdf , access-date=2015-10-15 , url-status=live , archive-url=https://web.archive.org/web/20170210205207/http://www.senserf.com/pg/PAPERS/tarp1.pdf , archive-date=2017-02-10
Routing algorithms
Flooding algorithms