|
Ping Flood
A ping flood is a simple denial-of-service attack where the attacker overwhelms the victim with ICMP "echo request" ( ping) packets. This is most effective by using the flood option of ping which sends ICMP packets as fast as possible without waiting for replies. Most implementations of ping require the user to be privileged in order to specify the flood option. It is most successful if the attacker has more bandwidth than the victim (for instance an attacker with a DSL line and the victim on a dial-up modem). The attacker hopes that the victim will respond with ICMP " echo reply" packets, thus consuming both outgoing bandwidth as well as incoming bandwidth. If the target system is slow enough, it is possible to consume enough of its CPU cycles for a user to notice a significant slowdown. A ping flood can also be used as a diagnostic for network packet loss and throughput issues. See also * INVITE of Death *Ping of death *Smurf attack A Smurf attack is a distributed denial- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. The range of attacks varies widely, spanning from inundating a server with millions of requests to slow its performance, overwhelming a server with a substantial amount of invalid data, to submitting requests with an illegitimate IP address. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack; simply attempting to block a single source is insuffic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address. For example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). A separate Internet Control Message Protocol (called ICMPv6) is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122). ICMP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
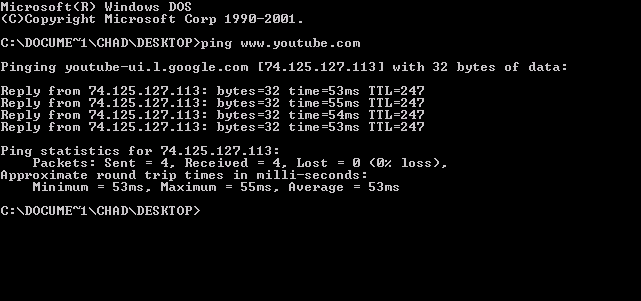
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host (network), host on an Internet Protocol (IP) network. It is available in a wide range of operating systems including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a Pulse (signal processing), pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) Network packet, packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean (average), mean round-trip times, and standard deviation of the mean. Command-line options and Comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Network Packet
In telecommunications and computer networking, a network packet is a formatted unit of Data (computing), data carried by a packet-switched network. A packet consists of control information and user data; the latter is also known as the ''Payload (computing), payload''. Control information provides data for delivering the payload (e.g., source and destination network addresses, error detection codes, or sequencing information). Typically, control information is found in packet Header (computing), headers and Trailer (computing), trailers. In packet switching, the Bandwidth (computing), bandwidth of the transmission medium is shared between multiple communication sessions, in contrast to circuit switching, in which circuits are preallocated for the duration of one session and data is typically transmitted as a continuous bit stream. Terminology In the seven-layer OSI model of computer networking, ''packet'' strictly refers to a protocol data unit at layer 3, the network layer. A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Superuser
In computing, the superuser is a special user account used for system administration. Depending on the operating system (OS), the actual name of this account might be root, administrator, admin or supervisor. In some cases, the actual name of the account is not the determining factor; on Unix-like systems, for example, the user with a user identifier (UID) of zero is the superuser .e., uid=0 regardless of the name of that account; and in systems which implement a r model, any user with the role of superuser (or its synonyms) can carry out all actions of the superuser account. The principle of least privilege recommends that most users and applications run under an ordinary account to perform their work, as a superuser account is capable of making unrestricted, potentially adverse, system-wide changes. Unix and Unix-like In Unix-like computer OSes (such as Linux), ''root'' is the conventional name of the user who has all rights or permissions (to all files and programs) in all mod ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Bandwidth (computing)
In computing, bandwidth is the maximum rate of data transfer across a given path. Bandwidth may be characterized as network bandwidth, data bandwidth, or digital bandwidth. This definition of ''bandwidth'' is in contrast to the field of signal processing, wireless communications, modem data transmission, digital communications, and electronics, in which ''bandwidth'' is used to refer to the signal bandwidth measured in hertz, meaning the frequency range between lowest and highest attainable frequency while meeting a well-defined impairment level in signal power. The actual bit rate that can be achieved depends not only on the signal bandwidth but also on the noise on the channel. Network capacity The term ''bandwidth'' sometimes defines the net bit rate ''peak bit rate'', ''information rate'', or physical layer ''useful bit rate'', channel capacity, or the maximum throughput of a logical or physical communication path in a digital communication system. For example, bandwi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Modem
The Democratic Movement (, ; MoDem ) is a centre to centre-right political party in France, whose main ideological trends are liberalism and Christian democracy, and that is characterised by a strong pro-Europeanist stance. MoDem was established by François Bayrou to succeed the Union for French Democracy (UDF) and contest the 2007 legislative election, after his strong showing in the 2007 presidential election. Initially named the Democratic Party (''Parti démocrate''), the party was renamed "Democratic Movement", because there was already a small Democratic Party in France. MoDem secured an agreement with La République En Marche! (LRM) — later Renaissance (RE) — in the 2017 legislative election after Bayrou had endorsed the candidacy of Emmanuel Macron in February. The two parties have since been in alliance, as of late named Ensemble. The party's founder and leader Bayrou has served as Prime Minister of France since December 2024. History Background MoDem tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Packet Loss
Packet loss occurs when one or more packets of data travelling across a computer network fail to reach their destination. Packet loss is either caused by errors in data transmission, typically across wireless networks, or network congestion.Kurose, J.F. & Ross, K.W. (2010). ''Computer Networking: A Top-Down Approach''. New York: Addison-Wesley. Packet loss is measured as a percentage of packets lost with respect to packets sent. The Transmission Control Protocol (TCP) detects packet loss and performs retransmissions to ensure reliable messaging. Packet loss in a TCP connection is also used to avoid congestion and thus produces an intentionally reduced throughput for the connection. In real-time applications like streaming media or online games, packet loss can affect a user's quality of experience (QoE). Causes The Internet Protocol (IP) is designed according to the end-to-end principle as a best-effort delivery service, with the intention of keeping the logic routers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Throughput
Network throughput (or just throughput, when in context) refers to the rate of message delivery over a communication channel in a communication network, such as Ethernet or packet radio. The data that these messages contain may be delivered over physical or logical links, or through network nodes. Throughput is usually measured in bits per second (, sometimes abbreviated bps), and sometimes in packets per second ( or pps) or data packets per time slot. The system throughput or aggregate throughput is the sum of the data rates that are delivered over all channels in a network. Throughput represents digital bandwidth consumption. The throughput of a communication system may be affected by various factors, including the limitations of the underlying physical medium, available processing power of the system components, end-user behavior, etc. When taking various protocol overheads into account, the useful rate of the data transfer can be significantly lower than the maximum a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
INVITE Of Death
An invitation system is a method of encouraging people to join an organization, such as a club or a website. In regular society, it refers to any system whereby new members are chosen; they cannot simply apply. In relation to websites and other technology-related organisations, the term refers to a more specific situation whereby invitations are sent, but there is never any approval needed from other members. Popular alternatives to this specific version are open registration and closed registration. Open registration is where any user can freely join. Closed registration involves an existing member recommending a new member and approval is sought amongst existing members. The basis of the invitation system is that a member can grant approval to a new user without having to consult any other members. Existing members may receive a set number of invitations (sometimes in the form of tokens) to allow others to join the service. Those invited to a website are typically sent either a s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ping Of Death
A ping of death is a type of attack on a computer system that involves sending a malformed or otherwise malicious ping to a computer. In this attack, a host sends hundreds of ping requests with a packet size that is large or illegal to another host to try to take it offline or to keep it preoccupied responding with ICMP Echo replies. A correctly formed ping packet is typically 56 bytes in size, or 64 bytes when the Internet Control Message Protocol (ICMP) header is considered, and 84 bytes including Internet Protocol (IP) version 4 header. However, any IPv4 packet (including pings) may be as large as 65,535 bytes. Some computer systems were never designed to properly handle a ping packet larger than the maximum packet size because it violates the Internet Protocol. Like other large but well-formed packets, a ping of death is fragmented into groups of 8 octets before transmission. However, when the target computer reassembles the malformed packet, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Smurf Attack
A Smurf attack is a distributed denial-of-service attack in which large numbers of Internet Control Message Protocol (ICMP) packets with the intended victim's spoofed source IP are broadcast to a computer network using an IP broadcast address. Most devices on a network will, by default, respond to this by sending a reply to the source IP address. If the number of machines on the network that receive and respond to these packets is very large, the victim's computer will be flooded with traffic. This can slow down the victim's computer to the point where it becomes impossible to work on. History The original tool for creating a Smurf attack was written by Dan Moschuk (alias TFreak) in 1997. In the late 1990s, many IP networks would participate in Smurf attacks if prompted (that is, they would respond to ICMP requests sent to broadcast addresses). The name comes from the idea of very small, but numerous attackers overwhelming a much larger opponent (see Smurfs). Today, administra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |