|
Firewall Pinhole
In computer networking, a firewall pinhole is a port that is not protected by a firewall to allow a particular application to gain access to a service on a host in the network protected by the firewall. Leaving ports open in firewall configurations exposes the protected system to potentially malicious abuse. A fully closed firewall prevents applications from accessing services on the other side of the firewall. For protection, the mechanism for opening a pinhole in the firewall should implement user validation and authorization. For firewalls performing a network address translation (NAT) function, the mapping between the external IP address, port socket and the internal IP address, port socket is often called a pinhole. Pinholes can be created manually or programmatically. They can be temporary, created dynamically for a specific duration such as for a dynamic connection, or permanent, such as for signaling functions. Firewalls sometimes automatically close pinholes after a per ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NAT Hole Punching
Hole punching (or sometimes punch-through) is a technique in computer networking for establishing a direct connection between two parties in which one or both are behind firewalls or behind routers that use network address translation (NAT). To punch a hole, each client connects to an unrestricted third-party server that temporarily stores external and internal address and port information for each client. The server then relays each client's information to the other, and using that information each client tries to establish direct connection; as a result of the connections using valid port numbers, restrictive firewalls or routers accept and forward the incoming packets on each side. Hole punching does not require any knowledge of the network topology to function. ICMP hole punching, UDP hole punching and TCP hole punching respectively use Internet Control Message, User Datagram and Transmission Control Protocols. Overview Networked devices with public or globally accessibl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP Hole Punching
TCP NAT traversal and TCP hole punching (sometimes NAT punch-through) in computer networking occurs when two hosts behind a network address translation (NAT) are trying to connect to each other with outbound TCP connections. Such a scenario is particularly important in the case of peer-to-peer communications, such as Voice-over-IP (VoIP), file sharing, teleconferencing, chat systems and similar applications. TCP hole punching is an experimentally used NAT traversal technique for establishing a TCP connection between two peers on the Internet behind NAT devices. ''NAT traversal'' is a general term for techniques that establish and maintain TCP/IP network and/or TCP connections traversing NAT gateways. Terminology In the following, the terms host, client and peer are used almost interchangeably. ; ''local endpoint'', ''internal endpoint'' : the local IP:port as seen locally by the host and the internal part of the NAT. ; ''public endpoint'', ''external endpoint'' : the externa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Triggering
Port triggering is a configuration option on a NAT-enabled router that controls communication between internal and external host machines in an IP network. It is similar to port forwarding in that it enables incoming traffic to be forwarded to a specific internal host machine, although the forwarded port is not open permanently and the target internal host machine is chosen dynamically. Description When two networks communicate through a NAT-router, the host machines on the internal network behave as if they have the IP address of the NAT-router from the perspective of the host machines on the external network. Without any traffic forwarding rules, it is impossible for a host machine on an external network (host B) to open a connection to a host machine in the internal network (host A). This is because the connection can only be targeted to the IP of the NAT-router, since the internal network is hidden behind NAT. With port triggering, when some host A opens a connection to a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Forwarding
In computer networking, port forwarding or port mapping is an application of network address translation (NAT) that redirects a communication request from one address and port number combination to another while the packets are traversing a network gateway, such as a router or firewall. This technique is most commonly used to make services on a host residing on a protected or masqueraded (internal) network available to hosts on the opposite side of the gateway (external network), by remapping the destination IP address and port number of the communication to an internal host. Purpose Port forwarding facilitates the connection by remote computers, for example, Internet hosts, to a specific computer or service within a local area network (LAN). In a typical residential network, nodes obtain Internet access through a DSL or cable modem connected to a router or network address translator (NAT/NAPT). Hosts on the private network are connected to an Ethernet switch or communicate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Control Protocol
Port Control Protocol (PCP) is a computer networking protocol that allows hosts on IPv4 or IPv6 networks to control how the incoming IPv4 or IPv6 packets are translated and forwarded by an upstream router that performs network address translation (NAT) or packet filtering. By allowing hosts to create explicit port forwarding rules, handling of the network traffic can be easily configured to make hosts placed behind NATs or firewalls reachable from the rest of the Internet (so they can also act as network servers), which is a requirement for many applications. Additionally, explicit port forwarding rules available through PCP allow hosts to reduce the amount of generated traffic by eliminating workarounds in form of outgoing NAT keepalive messages, which are required for maintaining connections to servers and for various NAT traversal techniques such as TCP hole punching. At the same time, less generated traffic reduces the power consumption, directly improving the battery ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NAT Traversal
Network address translation traversal is a computer networking technique of establishing and maintaining Internet Protocol connections across Gateway (telecommunications), gateways that implement network address translation (NAT). NAT traversal techniques are required for many network applications, such as peer-to-peer file sharing and voice over IP. Network address translation Network address translation typically uses private IP addresses on private networks with a single public IP address for the router facing the Internet. The network address translator changes the source address in network protocols for outgoing requests from that of an internal device to its external address, so that internal devices can communicate with hosts on the external network, while relaying replies back to the originating device. This leaves the internal network ill-suited for hosting services, as the NAT device has no automatic method for determining the internal host for which incoming packets fr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NAT Port Mapping Protocol
NAT Port Mapping Protocol (NAT-PMP) is a network protocol for establishing network address translation (NAT) settings and port forwarding configurations automatically without user effort. The protocol automatically determines the external IPv4 address of a NAT gateway, and provides means for an application to communicate the parameters for communication to peers. Apple introduced NAT-PMP in 2005 by as part of the Bonjour specification, as an alternative to the more common ISO Standard Internet Gateway Device Protocol implemented in many NAT routers. The protocol was published as an informational Request for Comments (RFC) by the Internet Engineering Task Force (IETF) in RFC 6886. NAT-PMP runs over the User Datagram Protocol (UDP) and uses port number 5351 on the server, whilst port 5350 is used on the client, as per spec. It has no built-in authentication mechanisms because forwarding a port typically does not allow any activity that could not also be achieved using STUN metho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Gateway Device Protocol
Internet Gateway Device (UPnP IGD) Control Protocol is a protocol based on Universal Plug and Play, UPnP for mapping Port (computer networking), ports in network address translation (NAT) setups, supported by some NAT-enabled Router (computing), routers. It is a common communications protocol for automatically configuring port forwarding, and is part of an International Organization for Standardization, ISO/International Electrotechnical Commission, IEC Standard ISO/IEC 29341, http://www.iso.org/iso/home/news_index/news_archive/news.htm?refid=Ref1185 rather than an Internet Engineering Task Force standard. Usage Applications using peer-to-peer networks, multiplayer gaming, and remote assistance programs need a way to communicate through home and business gateways. Without IGD one has to manually configure the gateway to allow traffic through, a process which is error-prone and time-consuming. Universal Plug and Play, UPnP comes with a solution for network address translation tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP And UDP Port
In computer networking, a port is a communication endpoint. At the software level within an operating system, a port is a logical construct that identifies a specific process or a type of network service. A port is uniquely identified by a number, the port number, associated with the combination of a transport protocol and the network IP address. Port numbers are 16-bit unsigned integers. The most common transport protocols that use port numbers are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). The port completes the destination and origination addresses of a message within a host to point to an operating system process. Specific port numbers are reserved to identify specific services so that an arriving packet can be easily forwarded to a running application. For this purpose, port numbers lower than 1024 identify the historically most commonly used services and are called the well-known port numbers. Higher-numbered ports are available for gene ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
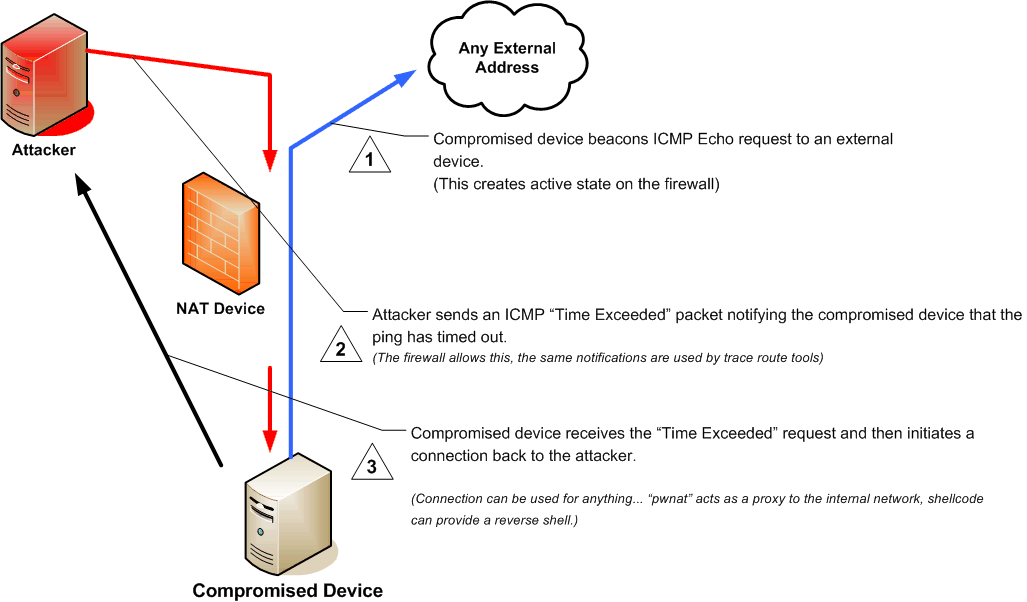
ICMP Hole Punching
ICMP hole punching is a technique employed in network address translator (NAT) applications for maintaining Internet Control Message Protocol (ICMP) packet streams that traverse the NAT. NAT traversal techniques are typically required for client-to-client networking applications on the Internet involving hosts connected in private networks, especially in peer-to-peer and Voice over Internet Protocol (VoIP) deployments. ICMP hole punching establishes connectivity between two hosts communicating across one or more network address translators in either a peer-to-peer or client–server model. Typically, third party hosts on the public transit network are used to establish UDP or TCP port states that may be used for direct communications between the communicating hosts, however ICMP hole punching requires no third party involvement to pass information between one or more NATs by exploiting a NAT's loose acceptance of inbound ICMP Time Exceeded packets. Once an ICMP Time Exceeded pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signaling (telecommunications)
In telecommunications, signaling is the use of signals for controlling communications. This may constitute an information exchange concerning the establishment and control of a telecommunication circuit and the management of the network. Classification Signaling systems may be classified based on several principal characteristics. In-band and out-of-band signaling In the public switched telephone network (PSTN), in-band signaling is the exchange of call control information within the same physical channel, or within the same frequency band, that the message (the callers' voice) is using. An example is dual-tone multi-frequency signaling (DTMF), which is used on most telephone lines to customer premises. Out-of-band signaling is telecommunication signaling on a dedicated channel separate from that used for the message. Out-of-band signaling has been used since Signaling System No. 6 (SS6) was introduced in the 1970s, and also in Signalling System No. 7 (SS7) in 1980 whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |