ICMP Hole Punching on:
[Wikipedia]
[Google]
[Amazon]
 ICMP hole punching is a technique employed in
ICMP hole punching is a technique employed in
 ICMP hole punching is a technique employed in
ICMP hole punching is a technique employed in network address translator
Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device. The technique was initia ...
(NAT) applications for maintaining Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when com ...
(ICMP) packet streams that traverse the NAT. NAT traversal
Network address translation traversal is a computer networking technique of establishing and maintaining Internet Protocol connections across Gateway (telecommunications), gateways that implement network address translation (NAT).
NAT traversal te ...
techniques are typically required for client-to-client networking applications on the Internet
The Internet (or internet) is the Global network, global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a internetworking, network of networks ...
involving hosts connected in private network
In Internet networking, a private network is a computer network that uses a private address space of IP addresses. These addresses are commonly used for local area networks (LANs) in residential, office, and enterprise environments. Both the IPv ...
s, especially in peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node ...
and Voice over Internet Protocol
Voice over Internet Protocol (VoIP), also known as IP telephony, is a set of technologies used primarily for voice communication sessions over Internet Protocol (IP) networks, such as the Internet. VoIP enables Voice call, voice calls to be tran ...
(VoIP) deployments.
ICMP hole punching establishes connectivity between two hosts communicating across one or more network address translators in either a peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node ...
or client–server model
The client–server model is a distributed application structure that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients. Often clients and servers communicate ov ...
. Typically, third party hosts on the public transit network are used to establish UDP or TCP port
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is common ...
states that may be used for direct communications between the communicating hosts, however ICMP hole punching requires no third party involvement to pass information between one or more NATs by exploiting a NAT's loose acceptance of inbound ICMP Time Exceeded
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when com ...
packets.
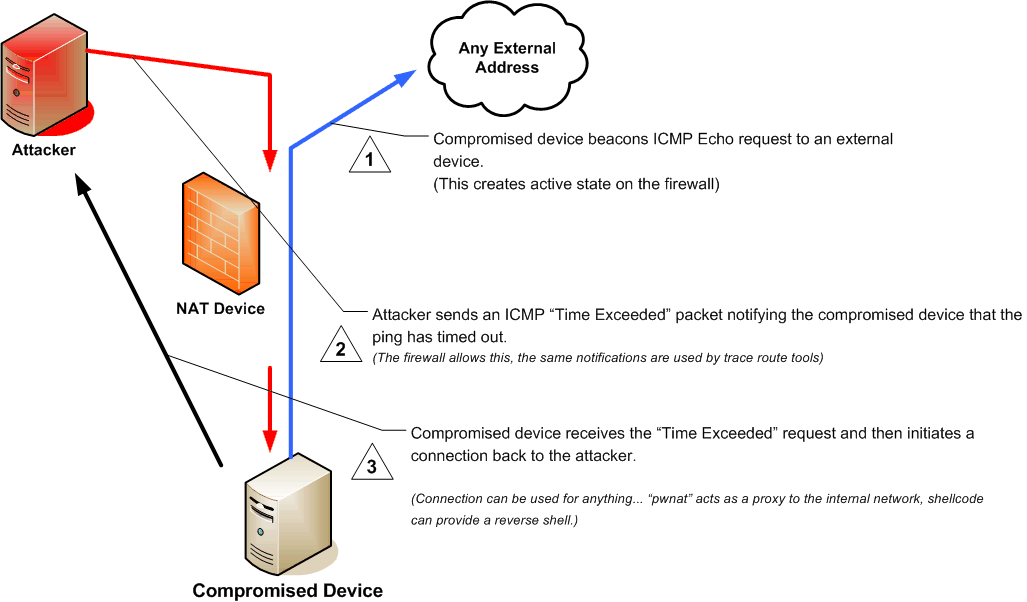
Once an ICMP Time Exceeded packet reaches the destination NAT, arbitrary data in the packet expected by the NAT allows the packet to reach the destination server, allowing the destination server to obtain the client's public IP address and other data stored in the packet from the client.
Overview
Currently the only method of ICMP hole punching or hole punching without third party involvement (autonomous NAT traversal) was developed bySamy Kamkar
Samy Kamkar (born December 10, 1985) is an American privacy and security researcher, computer hacker and entrepreneur. At the age of 16, he dropped out of high school. One year later, he co-founded Fonality, a unified communications company bas ...
on January 22, 2010 and released in the open source software pwnat, and the method was later published in the IEEE. According to the paper:
The proposed technique assumes that the client has somehow learned the current external (globally routable) IP address of the server's NAT. The key idea for enabling the server to learn the client's IP address is for the server to periodically send a message to a fixed, known IP address. The simplest approach uses ICMP ECHO REQUEST messages to an unallocated IP address, such as 1.2.3.4. Since 1.2.3.4 is not allocated, the ICMP REQUEST will not be routed by routers without a default route; ICMP DESTINATION UNREACHABLE messages that may be created by those routers can just be ignored by the server. As a result of the messages sent to 1.2.3.4, the NAT will enable routing of replies in response to this request. The connecting client will then fake such a reply. Specifically, the client will transmit an ICMP message indicating TTL_EXPIRED. Such a message could legitimately be transmitted by any Internet router and the sender address would not be expected to match the server's target IP. The server listens for (fake) ICMP replies and upon receipt initiates a connection to the sender IP specified in the ICMP reply.
See also
*Hole punching (networking)
Hole punching (or sometimes punch-through) is a technique in computer networking for establishing a direct connection between two parties in which one or both are behind firewalls or behind routers that use network address translation (NAT). To ...
* Port Control Protocol
Port Control Protocol (PCP) is a computer networking protocol that allows hosts on IPv4 or IPv6 networks to control how the incoming IPv4 or IPv6 packets are translated and forwarded by an upstream router that performs network address translat ...
(PCP)
* TCP hole punching
TCP NAT traversal and TCP hole punching (sometimes NAT punch-through) in computer networking occurs when two hosts behind a network address translation (NAT) are trying to connect to each other with outbound TCP connections. Such a scenario is pa ...
* UDP hole punching
UDP hole punching is a commonly used technique employed in network address translation (NAT) applications for maintaining User Datagram Protocol (UDP) packet streams that traverse the NAT. NAT traversal techniques are typically required for clien ...
References
{{DEFAULTSORT:Icmp Hole Punching Computer network security