|
Downgrade Attacks
A downgrade attack, also called a bidding-down attack, or version rollback attack, is a form of cryptographic attack on a computer system or communications protocol that makes it abandon a high-quality mode of operation (e.g. an encrypted connection) in favor of an older, lower-quality mode of operation (e.g. cleartext) that is typically provided for backward compatibility with older systems. An example of such a flaw was found in OpenSSL that allowed the attacker to negotiate the use of a lower version of TLS between the client and server. This is one of the most common types of downgrade attacks. Opportunistic encryption protocols such as STARTTLS are generally vulnerable to downgrade attacks, as they, by design, fall back to unencrypted communication. Websites which rely on redirects from unencrypted HTTP to encrypted HTTPS can also be vulnerable to downgrade attacks (e.g., sslstrip), as the initial redirect is not protected by encryption. Attack Downgrade attacks are often ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Protocol
A cryptographic protocol is an abstract or concrete Communications protocol, protocol that performs a information security, security-related function and applies cryptographic methods, often as sequences of cryptographic primitives. A protocol describes how the algorithms should be used and includes details about data structures and representations, at which point it can be used to implement multiple, interoperable versions of a program. Cryptographic protocols are widely used for secure application-level data transport. A cryptographic protocol usually incorporates at least some of these aspects: * Key agreement or establishment * Entity authentication * Symmetric encryption and message authentication key (cryptography), material construction * Secured application-level data transport * Non-repudiation methods * Secret sharing methods * Secure multi-party computation For example, Transport Layer Security (TLS) is a cryptographic protocol that is used to secure web (HTTPS) conne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted. Overview With the advent of computing, the term ''plaintext'' expanded beyond human-readable documents to mean any data, including binary files, in a form that can be viewed or used without requiring a key or other decryption device. Information—a message, document, file, etc.—if to be communicated or stored in an unencrypted form is referred to as plaintext. Plaintext is used as input to an encryption algorithm; the output is usually termed ciphertext, particularly when the algorithm is a cipher. Codetext is less often used, and almost always only when the algorithm involved is actually a code. Some systems use multiple layers of encryption, with the output of one encryption algorithm becoming "plaintext" input for the next. Secure handling Insecure handling of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opportunistic Encryption
Opportunistic encryption (OE) refers to any system that, when connecting to another system, attempts to encrypt communications channels, otherwise falling back to unencrypted communications. This method requires no pre-arrangement between the two systems. Opportunistic encryption can be used to combat passive wiretapping. (an ''active'' wiretapper, on the other hand, can disrupt encryption negotiation to either force an unencrypted channel or perform a man-in-the-middle attack on the encrypted link.) It does not provide a strong level of security as authentication may be difficult to establish and secure communications are not mandatory. However, it does make the encryption of most Internet traffic easy to implement, which removes a significant impediment to the mass adoption of Internet traffic security. Opportunistic encryption on the Internet is described in "Opportunistic Encryption using the Internet Key Exchange (IKE)", "Opportunistic Security: Some Protection Most of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
STARTTLS
Opportunistic TLS (Transport Layer Security) refers to extensions in plain text communication protocols, which offer a way to upgrade a plain text connection to an encrypted ( TLS or SSL) connection instead of using a separate port for encrypted communication. Several protocols use a command named "STARTTLS" or "Explicit TLS" for this purpose. It is a form of opportunistic encryption and is primarily intended as a countermeasure to passive monitoring. The STARTTLS command for IMAP and POP3 is defined in , for SMTP in , for XMPP in and for NNTP in . For IRC, the IRCv3 Working Group defined a STARTTLS extension, though it was later deprecated. FTP uses the command "AUTH TLS" defined in and LDAP defines a protocol extension OID in . HTTP uses an upgrade header. Layering TLS is application-neutral; in the words of : :One advantage of TLS is that it is application protocol independent. Higher-level protocols can layer on top of the TLS protocol transparently. The TLS standa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sslstrip
Moxie Marlinspike is an American entrepreneur, cryptographer, and computer security researcher. Marlinspike is the creator of Signal, co-founder of the Signal Technology Foundation, and served as the first CEO of Signal Messenger LLC. He is also a co-author of the Signal Protocol encryption used by Signal, WhatsApp, Google Messages, Facebook Messenger, and Skype. Marlinspike is a former head of the security team at Twitter and the author of a proposed SSL authentication system replacement called Convergence. He previously maintained a cloud-based WPA cracking service and a targeted anonymity service called GoogleSharing. Career Marlinspike began his career working for several technology companies, including enterprise infrastructure software maker BEA Systems Inc. In 2010, Marlinspike was the chief technology officer and co-founder of Whisper Systems, an enterprise mobile security startup company. In May 2010, Whisper Systems launched TextSecure and RedPhone. These were ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, where in actuality the attacker has inserted themselves between the two user parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a Wi-Fi access point hosting a network without encryption could insert themselves as a man in the middle. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
POODLE
The Poodle, called the in German () and the in French, is a breed of water dog. The breed is divided into four varieties based on size, the Standard Poodle, Medium Poodle, Miniature Poodle and Toy Poodle, although the Medium Poodle is not universally recognised. They have a distinctive thick, curly coat that comes in many colours and patterns, with only solid colours recognised by major breed registries. Poodles are active and intelligent, and are particularly able to learn from humans. Poodles tend to live 10–18 years, with smaller varieties tending to live longer than larger ones. The Poodle likely originated in Germany, although the Fédération Cynologique Internationale (FCI, International Canine Federation) and a minority of cynologists believe it originated in France. Similar dogs date back to at least the 17th century. Larger Poodles were originally used by wildfowl hunters to retrieve game from water, while smaller varieties were once commonly used as circus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backward Compatibility
In telecommunications and computing, backward compatibility (or backwards compatibility) is a property of an operating system, software, real-world product, or technology that allows for interoperability with an older legacy system, or with Input/output, input designed for such a system. Modifying a system in a way that does not allow backward compatibility is sometimes called "wikt:breaking change, breaking" backward compatibility. Such breaking usually incurs various types of costs, such as Switching barriers, switching cost. A complementary concept is ''forward compatibility''; a design that is forward-compatible usually has a Technology roadmap, roadmap for compatibility with future standards and products. Usage In hardware A simple example of both backward and forward compatibility is the introduction of FM broadcasting, FM radio in stereophonic sound, stereo. FM radio was initially monaural, mono, with only one audio channel represented by one signal (electrical engineerin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
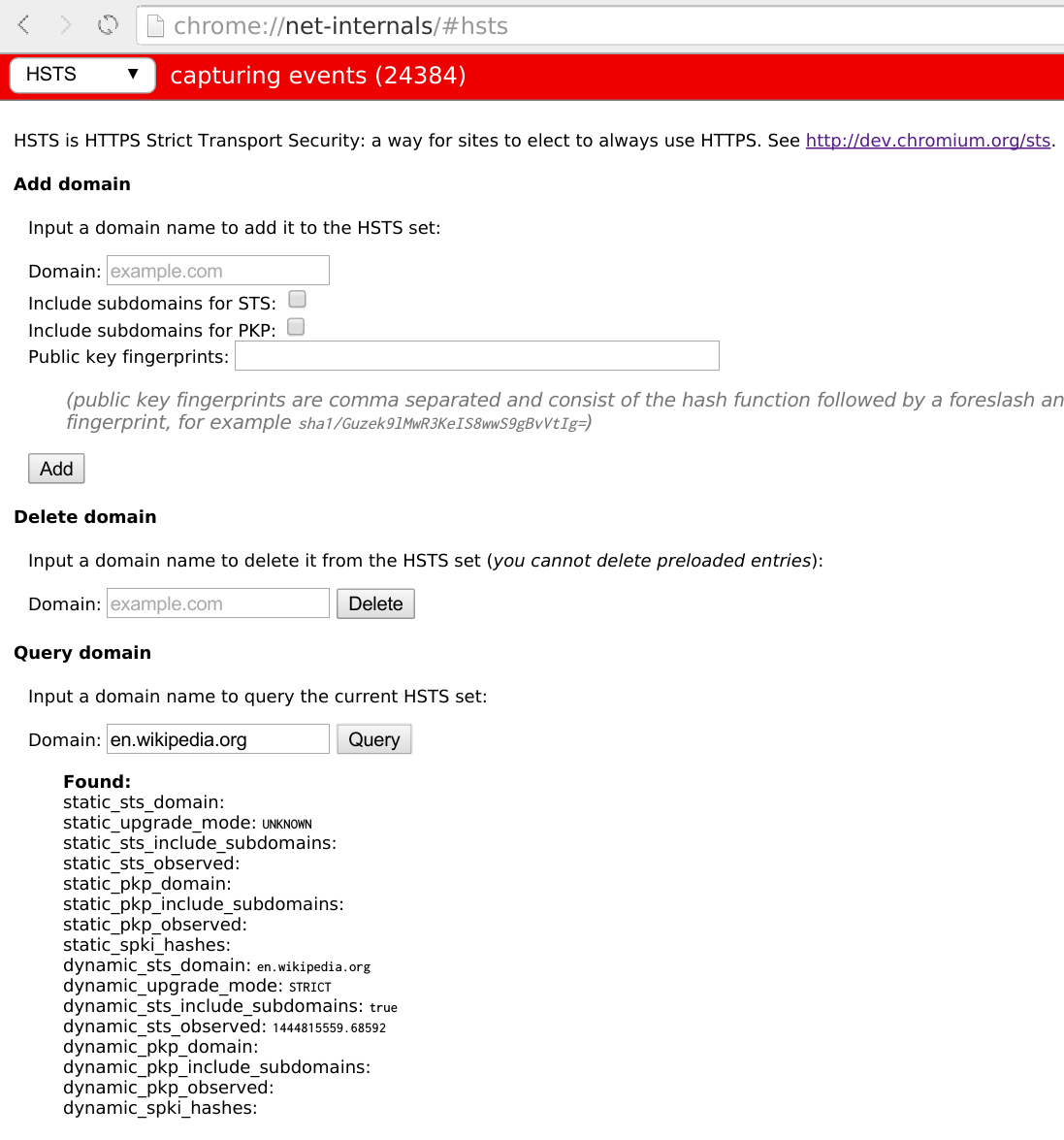
HTTP Strict Transport Security
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in . The HSTS Policy is communicated by the server to the user agent via an HTTP response header field named Strict-Transport-Security. HSTS Policy specifies a period of time during which the user agent should only access the server in a secure fashion. Websites using HSTS often do not accept clear text HTTP, either by rejecting connections over HTTP or systematically redirecting users to HTTPS (though this is not required by the specification). The consequence of this is that a user-agent not capable of do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Side-channel Attack
In computer security, a side-channel attack is a type of security exploit that leverages information inadvertently leaked by a system—such as timing, power consumption, or electromagnetic or acoustic emissions—to gain unauthorized access to sensitive information. These attacks differ from those targeting flaws in the design of cryptographic protocols or algorithms. (Cryptanalysis may identify vulnerabilities relevant to both types of attacks). Some side-channel attacks require technical knowledge of the internal operation of the system, others such as differential power analysis are effective as black-box attacks. The rise of Web 2.0 applications and software-as-a-service has also significantly raised the possibility of side-channel attacks on the web, even when transmissions between a web browser and server are encrypted (e.g. through HTTPS or WiFi encryption), according to researchers from Microsoft Research and Indiana University. Attempts to break a cryptosystem by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backward Compatibility
In telecommunications and computing, backward compatibility (or backwards compatibility) is a property of an operating system, software, real-world product, or technology that allows for interoperability with an older legacy system, or with Input/output, input designed for such a system. Modifying a system in a way that does not allow backward compatibility is sometimes called "wikt:breaking change, breaking" backward compatibility. Such breaking usually incurs various types of costs, such as Switching barriers, switching cost. A complementary concept is ''forward compatibility''; a design that is forward-compatible usually has a Technology roadmap, roadmap for compatibility with future standards and products. Usage In hardware A simple example of both backward and forward compatibility is the introduction of FM broadcasting, FM radio in stereophonic sound, stereo. FM radio was initially monaural, mono, with only one audio channel represented by one signal (electrical engineerin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |