|
XDMCP
In the X Window System, an X display manager is a graphical login manager which starts a login session on an X server from the same or another computer. A display manager presents the user with a login screen. A session starts when a user successfully enters a valid combination of username and password. When the display manager runs on the user's computer, it starts the X server before presenting the user the login screen, optionally repeating when the user logs out. In this condition, the DM realizes in the X Window System the functionality of and on character-mode terminals. When the display manager runs on a remote computer, it acts like a telnet server, requesting username and password and starting a remote session. X11 Release 3 introduced display managers in October 1988 with the aim of supporting the standalone X terminals, just coming onto the market. Various display managers continue in routine use to provide a graphical login prompt on standalone computer works ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
X Window System
The X Window System (X11, or simply X) is a windowing system for bitmap displays, common on Unix-like operating systems. X originated as part of Project Athena at Massachusetts Institute of Technology (MIT) in 1984. The X protocol has been at version 11 (hence "X11") since September 1987. The X.Org Foundation leads the X project, with the current reference implementation, X.Org Server, available as free and open-source software under the MIT License and similar permissive licenses. Purpose and abilities X is an architecture-independent system for remote graphical user interfaces and input device capabilities. Each person using a networked computer terminal, terminal has the ability to interact with the display with any type of user input device. In its standard distribution it is a complete, albeit simple, display and interface solution which delivers a standard widget toolkit, toolkit and protocol stack for building graphical user interfaces on most Unix-like operating syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GNOME Display Manager
GNOME Display Manager (GDM) is a display manager (a graphical login manager) for the windowing systems X11 and Wayland. The X Window System by default uses the XDM display manager. However, resolving XDM configuration issues typically involves editing a configuration file. GDM allows users to customize or troubleshoot settings without having to resort to a command line. Users can pick their session type on a per-login basis. GDM 2.38.0 is the last version that features customization with themes; subsequent releases do not support themes. Software architecture GDM is a display manager that implements all significant features required for managing attached and remote displays. GDM was written from scratch and does not contain any XDM or X Consortium code. Components GDM comprises the following components: * Chooser – a program used to select a remote host as the source for a remote display on the attached display (gdm-host-chooser) * Greeter – the graphical login wind ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
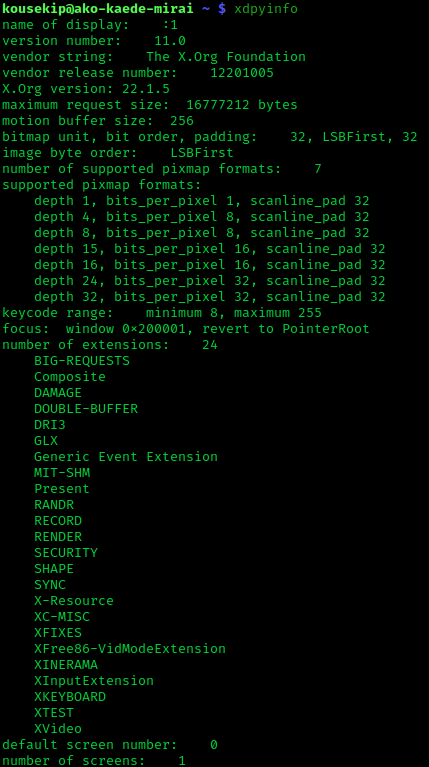
Xserver And Display Manager
X.Org Server is the free and open-source implementation of the X Window System (X11) display server stewarded by the X.Org Foundation. Implementations of the client-side X Window System protocol exist in the form of ''X11 libraries'', which serve as helpful APIs for communicating with the X server. Two such major X libraries exist for X11. The first of these libraries was Xlib, the original C language X11 API, but another C language X library, XCB, was created later in 2001. Other smaller X libraries exist, both as interfaces for Xlib and XCB in other languages, and as smaller standalone X libraries. The services with which the X.Org Foundation supports X Server include the packaging of the releases; certification (for a fee); evaluation of improvements to the code; developing the web site, and handling the distribution of monetary donations. The releases are coded, documented, and packaged by global developers. Software architecture The X.Org Server implements the serv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signal (computing)
Signals are standardized messages sent to a running program to trigger specific behavior, such as quitting or error handling. They are a limited form of inter-process communication (IPC), typically used in Unix, Unix-like, and other POSIX-compliant operating systems. A signal is an asynchronous notification sent to a process or to a specific thread within the same process to notify it of an event. Common uses of signals are to interrupt, suspend, terminate or kill a process. Signals originated in 1970s Bell Labs Unix and were later specified in the POSIX standard. When a signal is sent, the operating system interrupts the target process's normal flow of execution to deliver the signal. Execution can be interrupted during any non-atomic instruction. If the process has previously registered a signal handler, that routine is executed. Otherwise, the default signal handler is executed. Embedded programs may find signals useful for inter-process communications, as signals are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GNOME
A gnome () is a mythological creature and diminutive spirit in Renaissance magic and alchemy, introduced by Paracelsus in the 16th century and widely adopted by authors, including those of modern fantasy literature. They are typically depicted as small humanoids who live underground. Gnome characteristics are reinterpreted to suit various storytellers and artists. Paracelsus's gnome is recognized to have derived from the German miners' legend about or , the "metallurgical or mineralogical demon", according to Georg Agricola (1530), also called (literal Latinization of ''Bergmännlein'', "mountain manikin") by Agriocola in a later work (1549), and described by other names such as (sing. ; Latinization of German ). Agricola recorded that, according to the legends of that profession, these mining spirits acted as miming and laughing pranksters who sometimes threw pebbles at miners, but could also reward them by depositing a rich vein of silver ore. Paracelsus also called ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
X Display Manager (implementation)
The X Display Manager (XDM) is the default display manager for the X Window System. It is a bare-bones X display manager. It was introduced with X11 Release 3 in October 1988, to support the standalone X terminals that were just coming onto the market. It was written by Keith Packard. Functions XDM is used to boot an X.org based desktop environment In computing, a desktop environment (DE) is an implementation of the desktop metaphor made of a bundle of programs running on top of a computer operating system that share a common graphical user interface (GUI), sometimes described as a graphi .... It can control a display directly or indirectly in order to start an X session and supports remote login. XDM is initialized on system startup. It can be edited through the use of a configuration file, modules, or scripts. The configuration file is usually found in /usr/lib/X11/xdm/xdm-config. History XDM is one of the earliest display managers for Linux. It was developed by K ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tunneling Protocol
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. They can, for example, allow private network communications to be sent across a public network (such as the Internet), or for one network protocol to be carried over an incompatible network, through a process called encapsulation. Because tunneling involves repackaging the traffic data into a different form, perhaps with encryption as standard, it can hide the nature of the traffic that is run through a tunnel. Tunneling protocols work by using the data portion of a packet (the payload) to carry the packets that actually provide the service. Tunneling uses a layered protocol model such as those of the OSI or TCP/IP protocol suite, but usually violates the layering when using the payload to carry a service not normally provided by the network. Typically, the delivery protocol operates at an equal or higher level in the layered model than the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Shell
The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution. SSH was designed for Unix-like operating systems as a replacement for Telnet and unsecured remote Unix shell protocols, such as the Berkeley Remote Shell (rsh) and the related rlogin and rexec protocols, which all use insecure, plaintext methods of authentication, like passwords. Since mechanisms like Telnet and Remote Shell are designed to access and operate remote computers, sending the authentication tokens (e.g. username and password) for this access to these computers across a public network in an unsecured way poses a great risk of 3rd parties obtaining the password and achieving the same level of access to the remote system as the telnet user. Secure Shell mitigates this risk through the use of encryption mechanisms that are intended to hide th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secret Key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key's security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public and private keys, respectively. Purpose Since the key pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DHCP
The Dynamic Host Configuration Protocol (DHCP) is a network management protocol used on Internet Protocol (IP) networks for automatically assigning IP addresses and other communication parameters to devices connected to the network using a client–server architecture. The technology eliminates the need for individually configuring network devices manually, and consists of two network components, a centrally installed network DHCP server and client instances of the protocol stack on each computer or device. When connected to the network, and periodically thereafter, a client requests a set of parameters from the server using DHCP. DHCP can be implemented on networks ranging in size from residential networks to large campus networks and regional ISP networks. Many routers and residential gateways have DHCP server capability. Most residential network routers receive a unique IP address within the ISP network. Within a local network, a DHCP server assigns a local IP addres ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP And UDP Port
In computer networking, a port is a communication endpoint. At the software level within an operating system, a port is a logical construct that identifies a specific process or a type of network service. A port is uniquely identified by a number, the port number, associated with the combination of a transport protocol and the network IP address. Port numbers are 16-bit unsigned integers. The most common transport protocols that use port numbers are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). The port completes the destination and origination addresses of a message within a host to point to an operating system process. Specific port numbers are reserved to identify specific services so that an arriving packet can be easily forwarded to a running application. For this purpose, port numbers lower than 1024 identify the historically most commonly used services and are called the well-known port numbers. Higher-numbered ports are available for gene ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in Network packet, packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths. UDP is a connectionless protocol, meaning that messages are sent without negotiating a connection and that UDP does not keep track of what it has sent. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no Handshake (computing), handshaking dialogues and thus exposes the user's program to any Reliability (computer networking), unreliability of the underlying network; there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |