|
X.1035
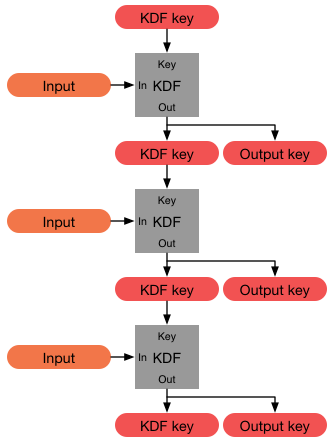
ITU-T Recommendation X.1035 specifies a password-authenticated key agreement protocol that ensures mutual authentication of two parties by using a Diffie–Hellman key exchange to establish a symmetric cryptographic key. The use of Diffie-Hellman exchange ensures perfect forward secrecy—a property of a key establishment protocol that guarantees that compromise of a session key or long-term private key after a given session does not cause the compromise of any earlier session. In X.1035, the exchange is protected from the man-in-the-middle attack. The authentication relies on a pre-shared secret (e.g., password), which is protected (i.e., remains unrevealed) to an eavesdropper preventing an off-line dictionary attack. The protocol can be used in a wide variety of applications including those with pre-shared secrets based on possibly weak passwords. X.1035 was approved on 13 February 2007 by ITU-T Study Group 17. Applications G.hn, an ITU-T standard that specifies high-speed (u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password-authenticated Key Agreement
In cryptography, a password-authenticated key agreement (PAK) method is an interactive method for two or more parties to establish cryptographic keys based on one or more parties' knowledge of a password. An important property is that an eavesdropper or man-in-the-middle cannot obtain enough information to be able to brute-force guess a password without further interactions with the parties for each (few) guesses. This means that strong security can be obtained using weak passwords. Types Password-authenticated key agreement generally encompasses methods such as: * Balanced password-authenticated key exchange * Augmented password-authenticated key exchange * Password-authenticated key retrieval * Multi-server methods * Multi-party methods In the most stringent password-only security models, there is no requirement for the user of the method to remember any secret or public data other than the password. Password-authenticated key exchange (PAKE) is a method in which two or more ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diffie–Hellman Key Exchange
Diffie–Hellman (DH) key exchangeSynonyms of Diffie–Hellman key exchange include: * Diffie–Hellman–Merkle key exchange * Diffie–Hellman key agreement * Diffie–Hellman key establishment * Diffie–Hellman key negotiation * Exponential key exchange * Diffie–Hellman protocol * Diffie–Hellman handshake is a mathematical method of securely generating a symmetric cryptographic key over a public channel and was one of the first public-key protocols as conceived by Ralph Merkle and named after Whitfield Diffie and Martin Hellman. DH is one of the earliest practical examples of public key exchange implemented within the field of cryptography. Published in 1976 by Diffie and Hellman, this is the earliest publicly known work that proposed the idea of a private key and a corresponding public key. Traditionally, secure encrypted communication between two parties required that they first exchange keys by some secure physical means, such as paper key lists transported by a tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ITU-T
The International Telecommunication Union Telecommunication Standardization Sector (ITU-T) is one of the three Sectors (branches) of the International Telecommunication Union (ITU). It is responsible for coordinating Standardization, standards for telecommunications and Information Communication Technology, such as X.509 for cybersecurity, Y.3172 and Y.3173 for machine learning, and H.264/MPEG-4 AVC for video compression, between its Member States, Private Sector Members, and Academia Members. The World Telecommunication Standardization Assembly (WTSA), the sector's governing conference, convenes every four years. ITU-T has a permanent Secretariat (administrative office), secretariat called the Telecommunication Standardization Bureau (TSB), which is based at the ITU headquarters in Geneva, Switzerland. The current director of the TSB is Seizo Onoe (of Japan), whose 4-year term commenced on 1 January 2023. Seizo Onoe succeeded Chaesub Lee of South Korea, who was director from 1 J ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Study Group 17
Study or studies may refer to: General * Education **Higher education * Clinical trial * Experiment * Field of study * Observational study * Scientific study * Research * Study skills, abilities and approaches applied to learning Other * Study (art), a drawing or series of drawings done in preparation for a finished piece * ''Study'' (film), a 2012 film by Paolo Benetazzo * ''Study'' (Flandrin), an 1835/36 painting by Hippolyte Flandrin * Study (room), a room in a home used as an office or library * ''Study'' (soundtrack), a soundtrack album from the 2012 film * The Study, a private all-girls school in Westmount, Quebec, Canada * ''Studies'' (journal), published by the Jesuits in Ireland * Eduard Study (1862–1930), German mathematician * Facebook Study, a market research app See also * Étude An étude (; ) or study is an instrumental musical composition, designed to provide practice material for perfecting a particular musical skill. The tradition of writing é ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forward Secrecy
In cryptography, forward secrecy (FS), also known as perfect forward secrecy (PFS), is a feature of specific key-agreement protocols that gives assurances that session keys will not be compromised even if long-term secrets used in the session key exchange are compromised, limiting damage. For TLS, the long-term secret is typically the private key of the server. Forward secrecy protects past sessions against future compromises of keys or passwords. By generating a unique session key for every session a user initiates, the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key. This by itself is not sufficient for forward secrecy which additionally requires that a long-term secret compromise does not affect the security of past session keys. Forward secrecy protects data on the transport layer of a network that uses common transport layer security protocols, including OpenSSL, when its long-te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, where in actuality the attacker has inserted themselves between the two user parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a Wi-Fi access point hosting a network without encryption could insert themselves as a man in the middle. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Local Area Network
A local area network (LAN) is a computer network that interconnects computers within a limited area such as a residence, campus, or building, and has its network equipment and interconnects locally managed. LANs facilitate the distribution of data and sharing network devices, such as printers. The LAN contrasts the wide area network (WAN), which not only covers a larger geographic distance, but also generally involves Leased line, leased telecommunication circuits or Internet links. An even greater contrast is the Internet, which is a system of globally connected business and personal computers. Ethernet and Wi-Fi are the two most common technologies used for local area networks; historical network technologies include ARCNET, Token Ring, and LocalTalk. Cabling Most wired network infrastructures utilize Category 5 cable, Category 5 or Category 6 cable, Category 6 twisted pair cabling with RJ45 (telecommunications), RJ45 compatible terminations. This medium provides physical ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Protocols
A cryptographic protocol is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods, often as sequences of cryptographic primitives. A protocol describes how the algorithms should be used and includes details about data structures and representations, at which point it can be used to implement multiple, interoperable versions of a program. Cryptographic protocols are widely used for secure application-level data transport. A cryptographic protocol usually incorporates at least some of these aspects: * Key agreement or establishment * Entity authentication * Symmetric encryption and message authentication material construction * Secured application-level data transport * Non-repudiation methods * Secret sharing methods * Secure multi-party computation For example, Transport Layer Security (TLS) is a cryptographic protocol that is used to secure web (HTTPS) connections. It has an entity authentication mechanism, based on the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Communication
Secure communication is when two entities are communicating and do not want a third party to listen in. For this to be the case, the entities need to communicate in a way that is unsusceptible to eavesdropping or interception. Secure communication includes means by which people can share information with varying degrees of certainty that third parties cannot intercept what is said. Other than spoken face-to-face communication with no possible eavesdropper, it is probable that no communication is guaranteed to be secure in this sense, although practical obstacles such as legislation, resources, technical issues (interception and encryption), and the sheer volume of communication serve to limit surveillance. With many communications taking place over long distance and mediated by technology, and increasing awareness of the importance of interception issues, technology and its compromise are at the heart of this debate. For this reason, this article focuses on communications mediated ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Applications Of Cryptography
Application may refer to: Mathematics and computing * Application software, computer software designed to help the user to perform specific tasks ** Application layer, an abstraction layer that specifies protocols and interface methods used in a communications network * Function application, in mathematics and computer science Processes and documents * Application for employment, a form or forms that an individual seeking employment must fill out * College application, the process by which prospective students apply for entry into a college or university * Patent application A patent application is a request pending at a patent office for the grant of a patent for an invention described in the patent specification and a set of one or more claim (patent), claims stated in a formal document, including necessary officia ..., a document filed at a patent office to support the grant of a patent Other uses * Application (virtue), a characteristic encapsulated in diligence * Topica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Standards
An open standard is a standard that is openly accessible and usable by anyone. It is also a common prerequisite that open standards use an open license that provides for extensibility. Typically, anybody can participate in their development due to their inherently open nature. There is no single definition, and interpretations vary with usage. Examples of open standards include the GSM, 4G, and 5G standards that allow most modern mobile phones to work world-wide. Definitions The terms ''open'' and ''standard'' have a wide range of meanings associated with their usage. There are a number of definitions of open standards which emphasize different aspects of openness, including the openness of the resulting specification, the openness of the drafting process, and the ownership of rights in the standard. The term "standard" is sometimes restricted to technologies approved by formalized committees that are open to participation by all interested parties and operate on a consensus bas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Standards
An international standard is a technical standard developed by one or more international standards organizations. International standards are available for consideration and use worldwide. The most prominent such organization is the International Organization for Standardization (ISO). Other prominent international standards organizations including the International Telecommunication Union (ITU) and the International Electrotechnical Commission (IEC). Together, these three organizations have formed the World Standards Cooperation alliance. Purpose International standards can be applied directly or adapted to meet local conditions. When adopted, they lead to the creation of national standards that are either equivalent to or largely align with the international standards in technical content, though they may have: (i) editorial variations, such as differences in appearance, the use of symbols, measurement units, or the choice of a point over a comma as the decimal marker, and (ii) v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |