|
Wiegand Interface
The Wiegand interface is a de facto wiring standard which arose from the popularity of Wiegand effect card readers in the 1980s. It is commonly used to connect a card swipe mechanism to the rest of an access control system. The sensor in such a system is often a "Wiegand wire", based on the Wiegand effect, discovered by John R. Wiegand. A Wiegand-compatible reader is normally connected to a Wiegand-compatible security panel. Physical layer The Wiegand interface uses three wires, one of which is a common ground and two of which are data transmission wires usually called DATA0 and DATA1, alternatively labeled "D0" and "D1" or "Data Low" and "Data High". When no data is being sent, both DATA0 and DATA1 are Pull-up resistor, pulled up to the "high" voltage level — usually +5 VDC. When a 0 is sent the DATA0 wire is pulled to a low voltage while the DATA1 wire stays at a high voltage. When a 1 is sent the DATA1 wire is pulled to a low voltage while DATA0 stays at a high voltage. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Identity Document
An identity document (abbreviated as ID) is a documentation, document proving a person's Identity (social science), identity. If the identity document is a plastic card it is called an ''identity card'' (abbreviated as ''IC'' or ''ID card''). When the identity document incorporates a photographic portrait, it is called a ''Photo identification, photo ID''. In some countries, identity documents may be List of national identity card policies by country#Countries with compulsory identity cards, compulsory to have. The identity document is used to connect a person to information about the person, often in a database. The connection between the identity document and database is based on personal information present on the document, such as the bearer's full name, birth date, Address (geography), address, an identification number, card number, gender, citizenship and more. A unique national identification number is the most secure way, but some countries lack such numbers or do not s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Smart Card
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are Contactless smart card, contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proximity Card
A proximity card or prox card also known as a key card or keycard is a contactless smart card which can be read without inserting it into a reader device, as required by earlier magnetic stripe cards such as credit cards and contact type smart cards. The proximity cards are part of the contactless card technologies. Held near an electronic reader for a moment they enable the identification of an encoded number. The reader usually produces a beep or other sound to indicate the card has been read. The term "proximity card" refers to the older 125 kHz devices as distinct from the newer 13.56 MHz contactless smartcards. Second generation prox cards are used for mass and distance reading applications. Proximity cards typically have a read range of up to which is the main difference from the contactless smartcard with a range of . The card can often be left in a wallet or purse,Access Control Card Handling Guide https://www.supercircuits.com/media/docs/proxcard_hand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Engineering
Security engineering is the process of incorporating security controls into an information system so that the controls become an integral part of the system's operational capabilities. It is similar to other systems engineering activities in that its primary motivation is to support the delivery of engineering solutions that satisfy pre-defined functional and user requirements, but it has the added dimension of preventing misuse and malicious behavior. Those constraints and restrictions are often asserted as a security policy. In one form or another, security engineering has existed as an informal field of study for several centuries. For example, the fields of locksmithing and security printing have been around for many years. The concerns for modern security engineering and computer systems were first solidified in a RAND paper from 1967, "Security and Privacy in Computer Systems" by Willis H. Ware. This paper, later expanded in 1979, provided many of the fundamental information ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Physical Security
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment, and resources and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems that can include CCTV surveillance, security guards, protective barriers, locks, access control, perimeter intrusion detection, deterrent systems, fire protection, and other systems designed to protect persons and property. Overview Physical security systems for protected facilities can be intended to: * deter potential intruders (e.g. warning signs, security lighting); * detect intrusions, and identify, monitor and record intruders (e.g. security alarms, access control and CCTV systems); * trigger appropriate incident responses (e.g. by security guards and police); * delay or prevent hostile movements (e.g. door reinforcements, grilles); * protect the as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Photo Identification
Photo identification or photo ID is an identity document that includes a photograph of the holder, usually only their face. The most commonly accepted forms of photo ID are those issued by government authorities, such as driver's licenses, identity cards and passports, but special-purpose photo IDs may be also produced, such as internal security or access control cards. Photo identification may be used for face-to-face authentication of identity of a party who either is personally unknown to the person in authority or because that person does not have access to a file, a directory, a registry or an information service that contains or that can render a photograph of somebody on account of that person's name and other personal information. Types Some countries – including almost all developed nations – use a single, government-issued type of card as a proof of age or citizenship. The United States, United Kingdom, Australia, New Zealand, Ireland, and Canada do not have suc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Magnetic Stripe Card
The term digital card can refer to a physical item, such as a memory card on a camera, or, increasingly since 2017, to the digital content hosted as a virtual card or cloud card, as a digital virtual representation of a physical card. They share a common purpose: identity management, credit card, debit card or driver's license. A non-physical digital card, unlike a #Magnetic stripe card, magnetic stripe card, can Emulator, emulate (imitate) any kind of card. A smartphone or smartwatch can store content from the card issuer; discount offers and news updates can be transmitted wirelessly, via Internet. These virtual cards are used in very high volumes by the mass transit sector, replacing paper-based tickets and the earlier magnetic strip cards. History Magnetic recording on steel tape and wire was invented by Valdemar Poulsen in Denmark around 1900 for recording audio. In the 1950s, magnetic recording of digital computer data on plastic tape coated with iron oxide was invente ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Credential
A credential is a piece of any document that details a qualification, competence, or authority issued to an individual by a third party with a relevant or ''de facto'' authority or assumed competence to do so. Examples of credentials include academic diplomas, academic degrees, Professional certification, certifications, security clearances, Identity document, identification documents, badges, passwords, user names, key (lock), keys, power of attorney, powers of attorney, and so on. Sometimes publications, such as scientific papers or books, may be viewed as similar to credentials by some people, especially if the publication was peer reviewed or made in a well-known Academic journal, journal or reputable publisher. Types and documentation of credentials A person holding a credential is usually given documentation or secret knowledge (''e.g.,'' a password or key) as proof of the credential. Sometimes this proof (or a copy of it) is held by a third, trusted party. While in some c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wiegand Effect
The Wiegand effect is a nonlinear magnetic effect, named after its discoverer John R. Wiegand, produced in specially annealed and hardened wire called Wiegand wire. Wiegand wire is low-carbon Vicalloy, a ferromagnetic alloy of cobalt, iron, and vanadium. Initially, the wire is fully annealed. In this state the alloy is "soft" in the magnetic sense; that is, it is attracted to magnets and so magnetic field lines will divert preferentially into the metal, but the metal retains only a very small residual field when the external field is removed. During manufacture, to give the wire its unique magnetic properties, it is subjected to a series of twisting and untwisting operations to cold-work the outside shell of the wire while retaining a soft core within the wire, and then the wire is aged. The result is that the magnetic coercivity of the outside shell is much larger than that of the inner core. This high coercivity outer shell will retain an external magnetic field even when ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
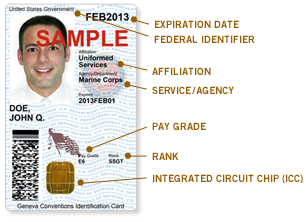
Common Access Card
The common access card, also commonly referred to as the CAC, is the standard identification for active duty United States defense personnel. The card itself is a smart card about the size of a credit card. Defense personnel that use the CAC include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions (especially the Third Geneva Convention). In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |