|
Whitelist
A whitelist or allowlist is a list or register of entities that are being provided a particular privilege, service, mobility, access or recognition. Entities on the list will be accepted, approved and/or recognized. Whitelisting is the reverse of blacklisting, the practice of identifying entities that are denied, unrecognized, or ostracized. Email whitelists Spam filters often include the ability to "whitelist" certain sender IP addresses, email addresses or domain names to protect their email from being rejected or sent to a junk mail folder. These can be manually maintained by the user or system administrator - but can also refer to externally maintained whitelist services. Non-commercial whitelists Non-commercial whitelists are operated by various non-profit organizations, ISPs, and others interested in blocking spam. Rather than paying fees, the sender must pass a series of tests; for example, their email server must not be an open relay and have a static IP address. The o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American proprietary software company focused on online protection for consumers worldwide headquartered in San Jose, California. The company was purchased by Intel in February 2011; with this acquisition, it became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a Minority interest, 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it Public company#Privatization, private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AppLocker
AppLocker is an application whitelisting technology introduced with Microsoft's Windows 7 operating system. It allows restricting which programs users can execute based on the program's path, publisher, or hash, and in an enterprise can be configured via Group Policy. Summary Windows AppLocker allows administrators to control which executable files are denied or allowed to execute. With AppLocker, administrators are able to create rules based on file names, publishers or file location that will allow certain files to execute. Unlike the earlier Software Restriction Policies, which was originally available for Windows XP and Windows Server 2003 Windows Server 2003, codenamed "Whistler Server", is the sixth major version of the Windows NT operating system produced by Microsoft and the first server version to be released under the Windows Server brand name. It is part of the Windows NT ..., AppLocker rules can apply to individuals or groups. Policies are used to group users ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ad Blocking
Ad blocking (or ad filtering) is a software capability for blocking or altering online advertising in a History of the web browser, web browser, an Application software, application or a network. This may be done using browser extensions or other methods or browsers with inside blocking. History The first ad blocker was Internet Fast Forward, a Plug-in (computing), plugin for the Netscape Navigator browser, developed by PrivNet and released in 1996. The AdBlock extension for Firefox was developed in 2002, with Adblock Plus being released in 2006. uBlock Origin, originally called "uBlock", was first released in 2014. Technologies and native countermeasures Online advertising exists in a variety of forms, including web banners, Image, pictures, Animation, animations, embedded audio and video, text, or Pop-up ad, pop-up windows, and can even employ audio and video Auto-Play, autoplay. Many browsers offer some ways to remove or alter advertisements: either by targeting technologie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
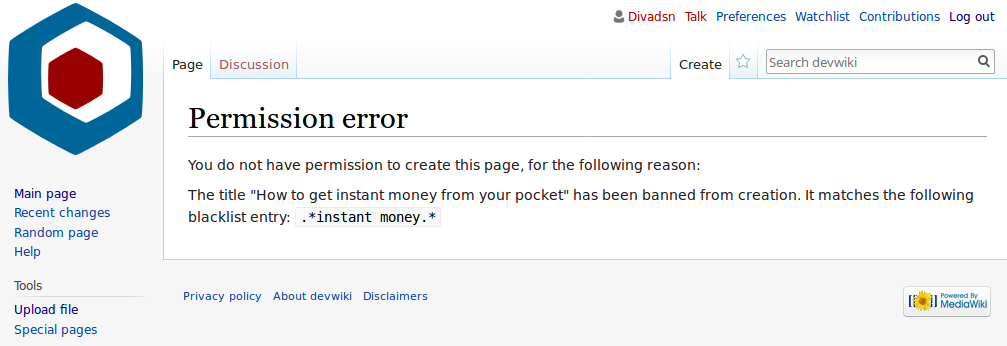
Blacklist (computing)
In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed. Blacklists can be applied at various points in a security architecture, such as a host, web proxy, DNS servers, email server, firewall, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking maliciou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam Filter
Email filtering is the processing of email to organize it according to specified criteria. The term can apply to the intervention of human intelligence, but most often refers to the automatic processing of messages at an SMTP server, possibly applying anti-spam techniques. Filtering can be applied to incoming emails as well as to outgoing ones. Depending on the calling environment, email filtering software can reject an item at the initial SMTP connection stage or pass it through unchanged for delivery to the user's mailbox. It is also possible to redirect the message for delivery elsewhere, quarantine it for further checking, modify it or 'tag' it in any other way. Motivation Common uses for mail filters include organizing incoming email and removal of spam and computer viruses. Mailbox providers filter outgoing email to promptly react to spam surges that may result from compromised accounts. A less common use is to inspect outgoing email at some companies to ensure that em ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the late–20th century as the digital version of, or counterpart to, mail (hence ''wikt:e-#Etymology 2, e- + mail''). Email is a ubiquitous and very widely used communication medium; in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. Email operates across computer networks, primarily the Internet access, Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email Server (computing), servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simultaneously; they need to connect, ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DNSWL
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual user to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some filter software includes time control functions that empowers parents to set the amount of time that child may spend accessing the Inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam Filter
Email filtering is the processing of email to organize it according to specified criteria. The term can apply to the intervention of human intelligence, but most often refers to the automatic processing of messages at an SMTP server, possibly applying anti-spam techniques. Filtering can be applied to incoming emails as well as to outgoing ones. Depending on the calling environment, email filtering software can reject an item at the initial SMTP connection stage or pass it through unchanged for delivery to the user's mailbox. It is also possible to redirect the message for delivery elsewhere, quarantine it for further checking, modify it or 'tag' it in any other way. Motivation Common uses for mail filters include organizing incoming email and removal of spam and computer viruses. Mailbox providers filter outgoing email to promptly react to spam surges that may result from compromised accounts. A less common use is to inspect outgoing email at some companies to ensure that em ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blacklisting
Blacklisting is the action of a group or authority compiling a blacklist of people, countries or other entities to be avoided or distrusted as being deemed unacceptable to those making the list; if people are on a blacklist, then they are considered to have done something wrong, or they are considered to be untrustworthy. As a verb, blacklist can mean to put an individual or entity on such a list. A blacklist is synonymous with a list of banned persons or organizations, and is the opposite of a whitelist. Origins of the term The English dramatist Philip Massinger used the phrase "black list" in his 1639 tragedy '' The Unnatural Combat''. After the restoration of the English monarchy brought Charles II of England to the throne in 1660, a list of regicides named those to be punished for the execution of his father. The state papers of Charles II say "If any innocent soul be found in this black list, let him not be offended at me, but consider whether some mistaken principle or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Static IP Address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface identification, and location addressing. Internet Protocol version 4 (IPv4) was the first standalone specification for the IP address, and has been in use since 1983. IPv4 addresses are defined as a 32-bit number, which became too small to provide enough addresses as the internet grew, leading to IPv4 address exhaustion over the 2010s. Its designated successor, IPv6, uses 128 bits for the IP address, giving it a larger address space. Although IPv6 deployment has been ongoing since the mid-2000s, both IPv4 and IPv6 are still used side-by-side . IP addresses are usually displayed in a human-readable notation, but systems may use them in various different computer number formats. CIDR notation can also be used to designate how much of the addr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
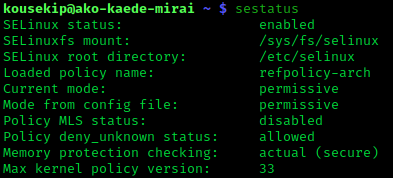
SE Linux
Security-Enhanced Linux (SELinux) is a Linux kernel Linux Security Modules, security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its software architecture, architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patch (computing), patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information base ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Privilege
Social privilege is an advantage or entitlement that benefits individuals belonging to certain groups, often to the detriment of others. Privileged groups can be advantaged based on social class, wealth, education, caste, age, height, skin color, physical fitness, nationality, geographic location, cultural differences, ethnic or racial category, gender, gender identity, neurodiversity, physical disability, sexual orientation, religion, and other differentiating factors. Individuals can be privileged in one area, such as education, and not privileged in another area, such as health. The amount of privilege any individual has may change over time, such as when a person becomes disabled, or when a child becomes a young adult. The concept of privilege is generally considered to be a theoretical concept used in a variety of subjects and often linked to social inequality. Privilege is also linked to social and cultural forms of power. It began as an academic concept, but ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |