|
Trusted Data Format
The Trusted Data Format (TDF) is a data object encoding specification for the purposes of enabling data tagging and cryptographic security features. These features include assertion of data properties or tags, cryptographic binding and data encryption. The TDF is freely available with no restrictions and requires no use of proprietary or patented technology and is thus open for anyone to use. Overview The TDF Specification is based on a Trusted Data Object (TDO) which can be grouped together into a Trusted Data Collection (TDC). Each TDO consists of a data payload which can be associated with an unlimited number of metadata objects. The TDO supports the cryptographic binding of the metadata objects to the payload data object. In addition, both data and metadata objects can be associated with a block of encryption information which is used by any TDF consumer to decrypt the associated data or metadata if it had been encrypted. A TDC allows for additional metadata objects ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open TDF Icon
Open or OPEN may refer to: Music * Open (band), Australian pop/rock band * The Open (band), English indie rock band * ''Open'' (Blues Image album), 1969 * ''Open'' (Gerd Dudek, Buschi Niebergall, and Edward Vesala album), 1979 * ''Open'' (Gotthard album), 1999 * ''Open'' (Cowboy Junkies album), 2001 * ''Open'' (YFriday album), 2001 * ''Open'' (Shaznay Lewis album), 2004 * ''Open'' (Jon Anderson EP), 2011 * ''Open'' (Stick Men album), 2012 * ''Open'' (The Necks album), 2013 * Open (Kwon Eun-bi EP), 2021 * ''Open'', a 1967 album by Julie Driscoll, Brian Auger and the Trinity * ''Open'', a 1979 album by Steve Hillage * "Open" (Queensrÿche song) * "Open" (Mýa song) * "Open", the first song on The Cure album ''Wish'' Literature * ''Open'' (Mexican magazine), a lifestyle Mexican publication * ''Open'' (Indian magazine), an Indian weekly English language magazine featuring current affairs * ''OPEN'' (North Dakota magazine), an out-of-print magazine that was printed in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ODNI
The director of national intelligence (DNI) is a cabinet-level United States government intelligence and security official. The position is required by the Intelligence Reform and Terrorism Prevention Act of 2004 to serve as executive head of the United States Intelligence Community (IC) and to direct and oversee the National Intelligence Program (NIP). All 18 IC agencies, including the Central Intelligence Agency (CIA), the Defense Intelligence Agency (DIA) and the National Security Agency (NSA), report directly to the DNI. Other federal agencies with intelligence capabilities also report to the DNI, including the Federal Bureau of Investigation (FBI). The DNI also serves as the principal advisor to the president of the United States, the National Security Council, and the Homeland Security Council on all intelligence matters. The DNI, supported by the Office of the Director of National Intelligence (ODNI), produces the President's Daily Brief, a classified document inc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Logical Assertion
In mathematical logic, a judgment (or judgement) or assertion is a statement or enunciation in a metalanguage. For example, typical judgments in first-order logic would be ''that a string is a well-formed formula'', or ''that a proposition is true''. Similarly, a judgment may assert the occurrence of a free variable in an expression of the object language, or the provability of a proposition. In general, a judgment may be any inductively definable assertion in the metatheory. Judgments are used in formalizing Formal system, deduction systems: a logical axiom expresses a judgment, premises of a rule of inference are formed as a sequence of judgments, and their conclusion is a judgment as well (thus, hypotheses and conclusions of proofs are judgments). A characteristic feature of the variants of Hilbert-style deduction systems is that the ''context'' is not changed in any of their rules of inference, while both natural deduction and sequent calculus contain some context-changing rul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Signature
An electronic signature, or e-signature, is data that is logically associated with other data and which is used by the signatory to sign the associated data. This type of signature has the same legal standing as a handwritten signature as long as it adheres to the requirements of the specific regulation under which it was created (e.g., eIDAS in the European Union, NIST-DSS in the USA or ZertES in Switzerland). Electronic signatures are a legal concept distinct from digital signatures, a cryptographic mechanism often used to implement electronic signatures. While an electronic signature can be as simple as a name entered in an electronic document, digital signatures are increasingly used in e-commerce and in regulatory filings to implement electronic signatures in a cryptographically protected way. Standardization agencies like NIST or ETSI provide standards for their implementation (e.g., NIST-DSS, XAdES or PAdES). The concept itself is not new, with common law jurisdict ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States Intelligence Community
The United States Intelligence Community (IC) is a group of separate US federal government, U.S. federal government intelligence agencies and subordinate organizations that work to conduct Intelligence assessment, intelligence activities which support the foreign policy of the United States, foreign policy and national security of the United States, national security interests of the United States. Member organizations of the IC include intelligence agency, intelligence agencies, military intelligence, and civilian intelligence and analysis offices within United States federal executive departments, federal executive departments. The IC is overseen by the Office of the Director of National Intelligence (ODNI), which is headed by the Director of National Intelligence, director of national intelligence (DNI) who reports directly to the president of the United States. The IC was established by Executive Order 12333 ("United States Intelligence Activities"), signed on December 4, 1 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
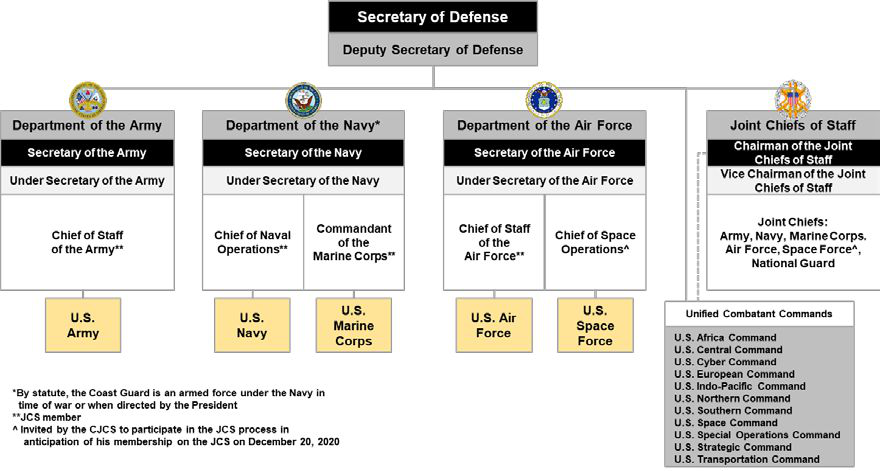
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Department Of Defense Discovery Metadata Specification
{{Redirect, DDMS, the Android debugger named Dalvik Debug Monitor Server, Dalvik (software) The Department of Defense Discovery Metadata Specification (DoD Discovery Metadata Specification or DDMS) is a Net-Centric Enterprise Services (NCES) metadata initiative. DDMS is loosely based on the Dublin Core vocabulary. DDMS defines discovery metadata elements for resources posted to community and organizational shared spaces. It is sometimes (incorrectly) referred to as ''DoD Discovery Metadata Standard''. The project focuses both on the process of developing a central taxonomy for metadata, and defining a way of discovering resources by their metadata using that taxonomy. The DDMS was created in support of the DoD Net-Centric Data Strategy (dated May 9, 2003), and specifies a set of information fields that are to be used to describe any data or service asset that is made known to the DoD Enterprise. The elements in the DDMS are designed to be platform, language, and implementation-i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography Standards
There are a number of standards related to cryptography. Standard algorithms and protocols provide a focus for study; standards for popular applications attract a large amount of cryptanalysis. Encryption standards * Data Encryption Standard (DES, now obsolete) * Advanced Encryption Standard (AES) * RSA the original public key algorithm * OpenPGP Hash standards * MD5 128-bit (obsolete) * SHA-1 160-bit (obsolete) * SHA-2 available in 224, 256, 384, and 512-bit variants * HMAC keyed hash * PBKDF2 Key derivation function (RFC 2898) Digital signature standards * Digital Signature Standard (DSS), based on the Digital Signature Algorithm (DSA) * RSA * Elliptic Curve DSA Public-key infrastructure (PKI) standards * X.509 Public Key Certificates Wireless Standards * Wired Equivalent Privacy (WEP), severely flawed and superseded by WPA * Wi-Fi Protected Access (WPA) better than WEP, a 'pre-standard' partial version of 802.11i * 802.11i a.k.a. WPA2, uses AES and other improvements o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |