|
Tradecraft
Tradecraft, within the intelligence community, refers to the techniques, methods, and technologies used in modern espionage (spying) and generally as part of the activity of intelligence assessment. This includes general topics or techniques ( dead drops, for example), or the specific techniques of a nation or organization (the particular form of encryption (encoding) used by the National Security Agency, for example). Examples * Agent handling is the management of espionage agents, principal agents, and agent networks (called "assets") by intelligence officers, who are typically known as case officers. * Analytic tradecraft is the body of specific methods for intelligence analysis. * Black bag operations are covert or clandestine entries into structures or locations to obtain information for human intelligence operations. This may require breaking and entering, lock picking, safe cracking, key impressions, fingerprinting, photography, electronic surveillance (includin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence Analysis
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberately deceptive information; the :wikt:analyst, analyst must correlate the similarities among deceptions and extract a common truth. Although its practice is found in its purest form inside national intelligence agency, intelligence agencies, its methods are also applicable in fields such as business intelligence or competitive intelligence. Overview Intelligence analysis is a way of reducing the ambiguity of highly ambiguous situations. Many analysts prefer the middle-of-the-road explanation, rejecting high or low probability explanations. Analysts may use their own standard of proportionality as to the risk acceptance of the opponent, rejecting that the opponent may take an extreme risk to achieve what the analyst regards as a minor gai ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage
Espionage, spying, or intelligence gathering, as a subfield of the intelligence field, is the act of obtaining secret or confidential information ( intelligence). A person who commits espionage on a mission-specific contract is called an ''espionage agent'' or ''spy''. A person who commits espionage as a fully employed officer of a government is called an intelligence officer. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
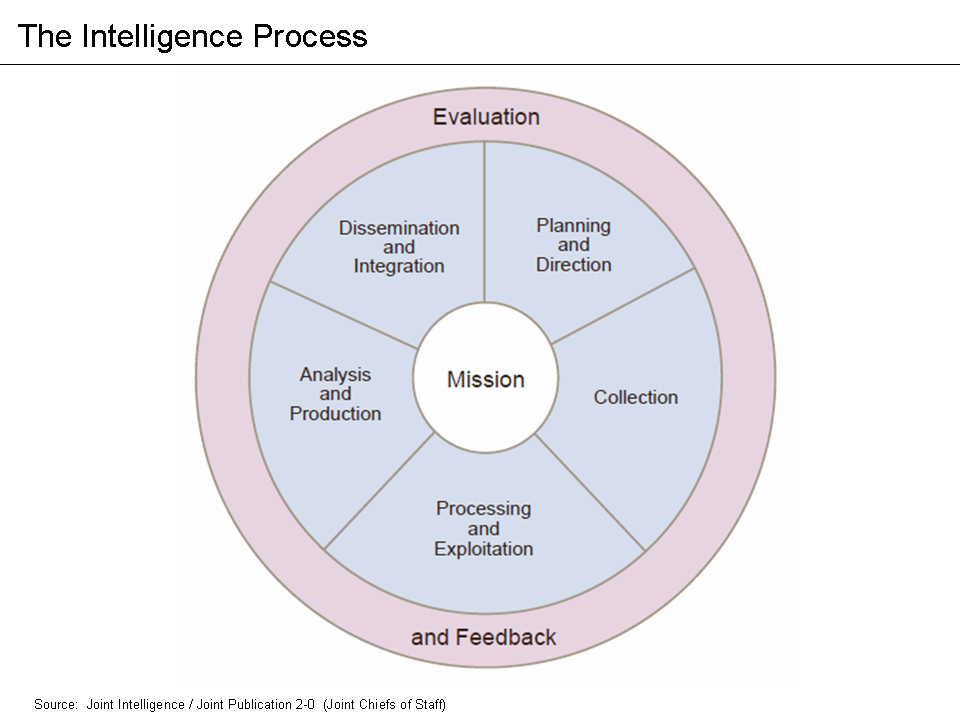
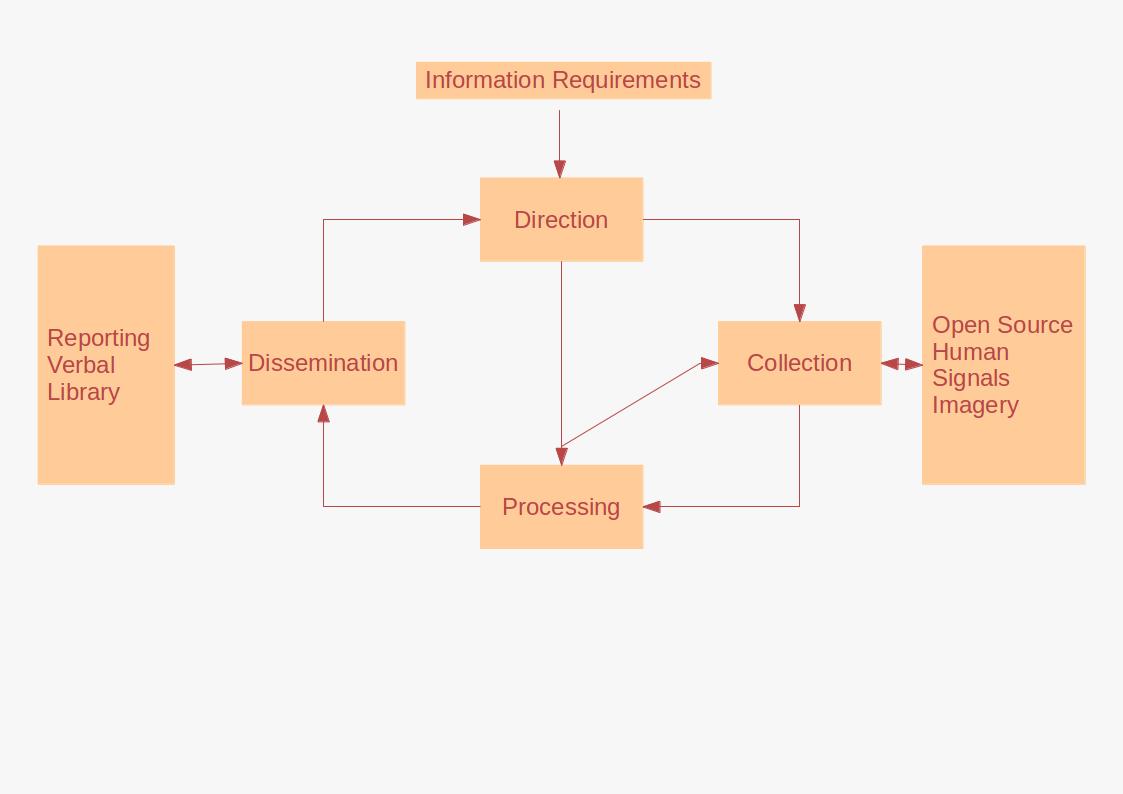
Intelligence Assessment
Intelligence assessment, is a specific phase of the intelligence cycle which oversees the development of behavior forecasts or recommended courses of action to the leadership of an organization, based on wide ranges of available overt and covert Intelligence (information), intelligence (also known as "intel"). There are two types of assessment; * In the beginning of the intelligence cycle, during the direction phase (also known as tasking or planning), intelligence officers assess past intelligence, identify gaps in information, and determine what new intelligence is needed. * Intelligence assessment also occurs toward the end of the intelligence cycle, during the analysis & production phase. This phase comes after collection and processing but before dissemination to policymakers. Assessments develop in response to leadership declaration requirements to inform decision-making. Assessment may be executed on behalf of a government, state, military or company, commercial organi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microdot Camera Markiv
A microdot is text or an image substantially reduced in size to prevent detection by unintended recipients. Microdots are normally circular and around in diameter but can be made into different shapes and sizes and made from various materials such as polyester or metal. The name comes from microdots often having been about the size and shape of a typography, typographical dot, such as a full stop, period or the tittle of a lowercase ''i'' or ''j''. Microdots are, fundamentally, a steganography, steganographic approach to message protection. History In 1870 during the Franco-Prussian War, Paris was under siege and messages were sent by carrier pigeon. Parisian photographer René Dagron used microfilm to permit each pigeon to carry a high volume of messages, as pigeons can carry little weight. Improvement in technology since then has made even smaller miniaturization possible. At the 1925 International Congress of Photography in Paris, Emanuel Goldberg presented a method of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mail
The mail or post is a system for physically transporting postcards, letter (message), letters, and parcel (package), parcels. A postal service can be private or public, though many governments place restrictions on private systems. Since the mid-19th century, national postal systems have generally been established as a government monopoly, with a fee on the article prepaid. Proof of payment is usually in the form of an adhesive postage stamp, but a postage meter is also used for bulk mailing. Postal authorities often have functions aside from transporting letters. In some countries, a Postal Telegraph and Telephone, postal, telegraph and telephone (PTT) service oversees the postal system, in addition to telephone and telegraph systems. Some countries' postal systems allow for savings accounts and handle applications for passports. The Universal Postal Union (UPU), established in 1874, includes 192 member countries and sets the rules for international mail exchanges as a List of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forgery
Forgery is a white-collar crime that generally consists of the false making or material alteration of a legal instrument with the specific mens rea, intent to wikt:defraud#English, defraud. Tampering with a certain legal instrument may be forbidden by law in some jurisdictions but such an offense is not related to forgery unless the tampered legal instrument was actually used in the course of the crime to defraud another person or entity. Copies, studio replicas, and reproductions are not considered forgeries, though they may later become forgeries through knowing and willful misrepresentations. Forging money or currency is more often called counterfeiting. But consumer goods may also be ''counterfeits'' if they are not manufactured or produced by the designated manufacturer or producer given on the label or flagged by the trademark symbol. When the object forged is a record or document it is often called a false document. This usage of "forgery" does not derive from Metalwo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Caltrop
A caltrop (also known as caltrap, galtrop, cheval trap, galthrap, galtrap, calthrop, jackrock or crow's foot''Battle of Alesia'' (Caesar's conquest of Gaul in 52 BC), Battlefield Detectives program, (2006), rebroadcast: 2008-09-08 on History Channel International (13:00-14:00 hrs EDST); Note: No mention of name caltrop at all, but illustrated and given as battle key to defend Roman lines of circumvallation per recent digs evidence.) is an area denial weapon made up of usually four, but possibly more, sharp nails or spines arranged in such a manner that one of them always points upward from a stable base (for example, a tetrahedron). Historically, caltrops were part of defences that served to slow the advance of troops, especially horses, chariots, and war elephants, and were particularly effective against the soft feet of camels. In modern times, caltrops are effective when used against wheeled vehicles with pneumatic tires. Name The modern name "caltrop" is derived from the Ol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concealment Device
Concealment devices or diversion safes are used to hide things for the purpose of secrecy or security. They are made from an ordinary household object such as a book, a soda can, a candle, a can, or something as small as a coin. The idea is that such an inconspicuous object would not be expected to contain anything of worth. Examples in espionage include dead drop spikes for transferring items to other people, and hollowed-out coins or hollowed out teeth for concealing something - such as microfilm or a suicide pill. Examples in smuggling include suitcases with false bottoms for hiding contraband. During World War II MI9 was responsible for creating many concealment devices for "escape aids" to assist prisoners of war to escape. Examples Ammunition Starting in the First World War and still continuing today, military personnel use ammunition casings to hide small amounts of critical information e.g. encryption/recognition codes or navigational grid references etc. The hidi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secrecy
Secrecy is the practice of hiding information from certain individuals or groups who do not have the "need to know", perhaps while sharing it with other individuals. That which is kept hidden is known as the secret. Secrecy is often controversial, depending on the content or nature of the secret, the group or people keeping the secret, and the motivation for secrecy. Secrecy by government entities is often decried as excessive or in promotion of poor operation; excessive revelation of information on individuals can conflict with virtues of privacy and confidentiality. It is often contrasted with social transparency. Secrecy can exist in a number of different ways: encoding or encryption (where mathematical and technical strategies are used to hide messages), true secrecy (where restrictions are put upon those who take part of the message, such as through government security classification) and obfuscation, where secrets are hidden in plain sight behind complex idiosyncrat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Suicide
Suicide is the act of intentionally causing one's own death. Risk factors for suicide include mental disorders, physical disorders, and substance abuse. Some suicides are impulsive acts driven by stress (such as from financial or academic difficulties), relationship problems (such as breakups or divorces), or harassment and bullying. Those who have previously attempted suicide are at a higher risk for future attempts. Effective suicide prevention efforts include limiting access to methods of suicide such as firearms, drugs, and poisons; treating mental disorders and substance abuse; careful media reporting about suicide; improving economic conditions; and dialectical behaviour therapy (DBT). Although crisis hotlines, like 988 in North America and 13 11 14 in Australia, are common resources, their effectiveness has not been well studied. Suicide is the 10th leading cause of death worldwide, accounting for approximately 1.5% of total deaths. In a given year, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Photography
Photography is the visual arts, art, application, and practice of creating images by recording light, either electronically by means of an image sensor, or chemically by means of a light-sensitive material such as photographic film. It is employed in many fields of science, manufacturing (e.g., photolithography), and business, as well as its more direct uses for art, film and video production, recreational purposes, hobby, and mass communication. A person who operates a camera to capture or take Photograph, photographs is called a photographer, while the captured image, also known as a photograph, is the result produced by the camera. Typically, a lens is used to focus (optics), focus the light reflected or emitted from objects into a real image on the light-sensitive surface inside a camera during a timed Exposure (photography), exposure. With an electronic image sensor, this produces an Charge-coupled device, electrical charge at each pixel, which is Image processing, electro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |