|
Threat Intelligence Platform
Threat Intelligence Platform (TIP) is an emerging technology discipline that helps organizations aggregate, correlate, and analyze threat data from multiple sources in real time to support defensive actions. TIPs have evolved to address the growing amount of data generated by a variety of internal and external resources (such as system logs and threat intelligence feeds) and help security teams identify the threats that are relevant to their organization. By importing threat data from multiple sources and formats, correlating that data, and then exporting it into an organization’s existing security systems or ticketing systems, a TIP automates proactive threat management and mitigation. A true TIP differs from typical enterprise security products in that it is a system that can be programmed by outside developers, in particular, users of the platform. TIPs can also use APIs to gather data to generate configuration analysis, Whois information, reverse IP lookup, website content a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Threat (computer)
In computer security, a threat is a potential negative action or event enabled by a vulnerability that results in an unwanted impact to a computer system or application. A threat can be either a negative " intentional" event (i.e. hacking: an individual cracker or a criminal organization) or an "accidental" negative event (e.g. the possibility of a computer malfunctioning, or the possibility of a natural disaster event such as an earthquake, a fire, or a tornado) or otherwise a circumstance, capability, action, or event ( incident is often used as a blanket term). A '' threat actor'' who is an individual or group that can perform the threat action, such as exploiting a vulnerability to actualise a negative impact. An '' exploit'' is a vulnerability that a threat actor used to cause an incident. Standard definitions A more comprehensive definition, tied to an Information assurance point of view, can be found in "''Federal Information Processing Standards (FIPS) 200, Mini ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Prevention System
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recognizing bad patterns, such as exploitatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Computing
Cloud computing is "a paradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand," according to International Organization for Standardization, ISO. Essential characteristics In 2011, the National Institute of Standards and Technology (NIST) identified five "essential characteristics" for cloud systems. Below are the exact definitions according to NIST: * On-demand self-service: "A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider." * Broad network access: "Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations)." * Pooling (resource management), Resource pooling: " The provider' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
On-premises Software
On-premises software (abbreviated to on-prem, and often written as "on-premise") is installed and runs on computers on the premises of the person or organization using the software, rather than at a remote facility such as a server farm or cloud. On-premises software is sometimes referred to as " shrinkwrap" software, and off-premises software is commonly called "software as a service" ("SaaS") or "cloud computing". The software consists of database and modules that are combined to particularly serve the unique needs of the large organizations regarding the automation of corporate-wide business system and its functions. Comparison between on-premises and cloud (SaaS) Location On-premises software is established within the organisation's internal system along with the hardware and other infrastructure necessary for the software to function. Cloud-based software is usually served via internet and it can be accessed by users online regardless of the time and their location. Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Sharing And Analysis Center
An Information Sharing and Analysis Center (ISAC) is an organization that provides a central resource for gathering information on cyber and related threats to critical infrastructure and providing two-way sharing of information between the private and public sectors. Sector ISACs began forming in 1999, subsequent to the May 22, 1998 signing of U.S. Presidential Decision Directive-63 (PDD-63), when "the federal government asked each critical infrastructure sector to establish sector-specific organizations to share information about threats and vulnerabilities." Decision Directive-63 (PDD-63) was replaced by Homeland Security Presidential Directive 21 in 2013. Australia * Critical Infrastructure Information Sharing & Analysis Centre (CI-ISAC) Canada * Global Mining and Metals Information Sharing & Analysis Centre (MM-ISAC) Europe European Energy - Information Sharing & Analysis Centre (EE-ISAC) is a network of private utilities, solution providers and (semi) public institu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Programming Interface
An application programming interface (API) is a connection between computers or between computer programs. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standard that describes how to build such a connection or interface is called an ''API specification''. A computer system that meets this standard is said to ''implement'' or ''expose'' an API. The term API may refer either to the specification or to the implementation. In contrast to a user interface, which connects a computer to a person, an application programming interface connects computers or pieces of software to each other. It is not intended to be used directly by a person (the end user) other than a computer programmer who is incorporating it into software. An API is often made up of different parts which act as tools or services that are available to the programmer. A program or a programmer that uses one of these parts is said to ''call'' that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on configurable security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet or between several VLANs. Firewalls can be categorized as network-based or host-based. History The term '' firewall'' originally referred to a wall to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the 1980s. Because they already segregated networks, routers could filter packets crossing them. Before it was used in real-life comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Retrieval
Information retrieval (IR) in computing and information science is the task of identifying and retrieving information system resources that are relevant to an Information needs, information need. The information need can be specified in the form of a search query. In the case of document retrieval, queries can be based on full-text search, full-text or other content-based indexing. Information retrieval is the science of searching for information in a document, searching for documents themselves, and also searching for the metadata that describes data, and for databases of texts, images or sounds. Automated information retrieval systems are used to reduce what has been called information overload. An IR system is a software system that provides access to books, journals and other documents; it also stores and manages those documents. Web search engines are the most visible IR applications. Overview An information retrieval process begins when a user enters a query into the sys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open-source Intelligence
Open source intelligence (OSINT) is the collection and analysis of data gathered from open sources (overt sources and publicly available information) to produce actionable intelligence. OSINT is primarily used in national security, law enforcement, and competitive intelligence, business intelligence functions and is of value to analysts who use non-sensitive intelligence in answering classified information, classified, Classified information#Unclassified, unclassified, or trade secret, proprietary intelligence intelligence requirement, requirements across the previous intelligence disciplines. Categories OSINT sources can be divided up into six different categories of information flow: *Media: print newspapers, magazines, radio, and television from across and between countries. *Internet: online publications, blogs, discussion groups, citizen media (i.e. – cell phone digital video, videos, and user created content), YouTube, and other social media websites (i.e. – Facebook ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Risk Management
Risk management is the identification, evaluation, and prioritization of risks, followed by the minimization, monitoring, and control of the impact or probability of those risks occurring. Risks can come from various sources (i.e, Threat (security), threats) including uncertainty in Market environment, international markets, political instability, dangers of project failures (at any phase in design, development, production, or sustaining of life-cycles), legal liabilities, credit risk, accidents, Natural disaster, natural causes and disasters, deliberate attack from an adversary, or events of uncertain or unpredictable root cause analysis, root-cause. Retail traders also apply risk management by using fixed percentage position sizing and risk-to-reward frameworks to avoid large drawdowns and support consistent decision-making under pressure. There are two types of events viz. Risks and Opportunities. Negative events can be classified as risks while positive events are classifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
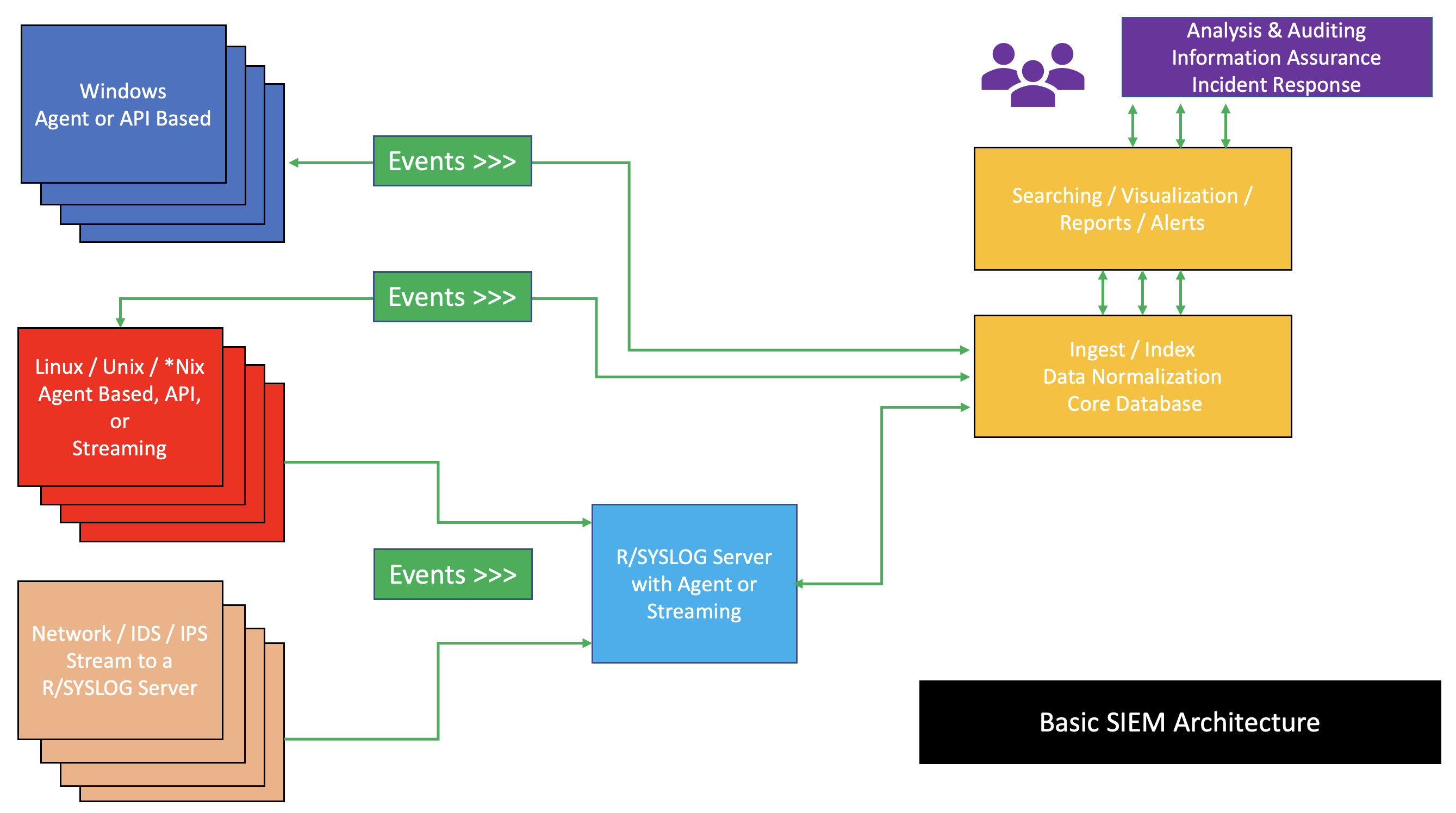
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using technique ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |