|
Shorewall
Shorewall is an open source firewall tool for Linux that builds upon the Netfilter (iptables/ipchains) system built into the Linux kernel, making it easier to manage more complex configuration schemes by providing a higher level of abstraction for describing rules using text files. Configuration It is not a daemon since it does not run continuously, but rather configures rules in the kernel that allow and disallow traffic through the system. Shorewall is configured through a group of plain-text configuration files and does not have a graphical user interface, though a Webmin module is available separately. A monitoring utility packaged with Shorewall can be used to watch the status of the system as it operates and to assist in testing. Use Shorewall is mainly used in network installations (as opposed to a personal computer firewall), since most of its strength lies in its ability to work with "zones", such as the DMZ or a 'net' zone. Each zone would then have different r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Iptables
iptables is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall, implemented as different Netfilter modules. The filters are organized in different tables, which contain chains of rules for how to treat network traffic packets. Different kernel modules and programs are currently used for different protocols; ''iptables'' applies to IPv4, ''ip6tables'' to IPv6, ''arptables'' to ARP, and ' to Ethernet frames. iptables requires elevated privileges to operate and must be executed by user root, otherwise it fails to function. On most Linux systems, iptables is installed as and documented in its man pages, which can be opened using man iptables when installed. It may also be found in /sbin/iptables, but since iptables is more like a service rather than an "essential binary", the preferred location remains . The term ''iptables'' is also commonly used to inclusively refer to the kernel-level componen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Perl
Perl is a family of two High-level programming language, high-level, General-purpose programming language, general-purpose, Interpreter (computing), interpreted, dynamic programming languages. "Perl" refers to Perl 5, but from 2000 to 2019 it also referred to its redesigned "sister language", Perl 6, before the latter's name was officially changed to Raku (programming language), Raku in October 2019. Though Perl is not officially an acronym, there are various backronyms in use, including "Practical Data extraction, Extraction and Reporting Language". Perl was developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions. Raku, which began as a redesign of Perl 5 in 2000, eventually evolved into a separate language. Both languages continue to be developed independently by different development teams and liberally borrow ideas from each other. The Perl languages borrow featur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graphical User Interface
The GUI ( "UI" by itself is still usually pronounced . or ), graphical user interface, is a form of user interface that allows User (computing), users to Human–computer interaction, interact with electronic devices through graphical icon (computing), icons and audio indicator such as primary notation, instead of text-based user interface, text-based UIs, typed command labels or text navigation. GUIs were introduced in reaction to the perceived steep learning curve of CLIs (command-line interfaces), which require commands to be typed on a computer keyboard. The actions in a GUI are usually performed through Direct manipulation interface, direct manipulation of the graphical elements. Beyond computers, GUIs are used in many handheld mobile devices such as MP3 players, portable media players, gaming devices, smartphones and smaller household, office and Distributed control system, industrial controls. The term ''GUI'' tends not to be applied to other lower-display resolution User ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a ''internetworking, network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and mi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
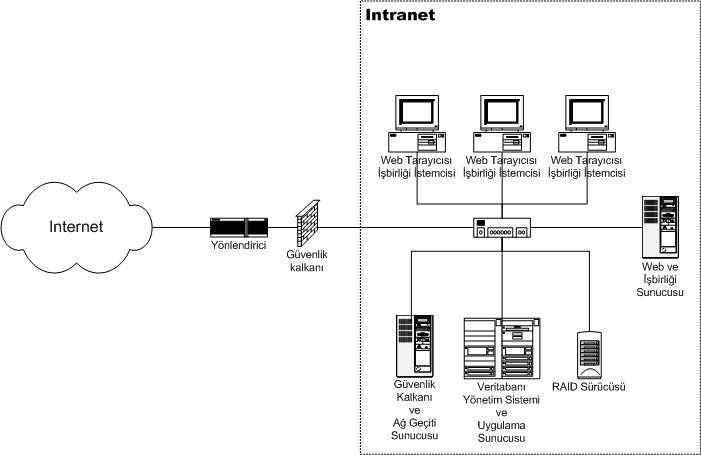
Intranet
An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite. An organization-wide intranet can constitute an important focal point of internal communication and collaboration, and provide a single starting point to access internal and external resources. In its simplest form, an intranet is established with the technologies for local area networks (LANs) and wide area networks (WANs). Many modern intranets have Web search engine, search engines, user profiles, blogs, mobile apps with notifications, and events planning within their infrastructure. An intranet is sometimes contrasted to an extranet. While an intranet is generally restricted to employees of the organization, extranets m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Demilitarized Zone (computing)
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external Node (networking), network node can access only what is exposed in the DMZ, while the rest of the organization's network is protected behind a Firewall (computing), firewall. The DMZ functions as a small, isolated network positioned between the Internet and the private network. This is not to be confused with a DMZ host, a feature present in some home routers which frequently differs greatly from an ordinary DMZ. The name is from the term ''demilitarized zone'', an area between states in which military operations are not permitted. Rationale The DMZ is seen as not belonging to eit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Personal Firewall
A personal firewall is an application which controls network traffic to and from a computer, permitting or denying communications based on a security policy. Typically it works as an application layer firewall. A personal firewall differs from a conventional firewall in terms of scale. A personal firewall will usually protect only the computer on which it is installed, as compared to a conventional firewall which is normally installed on a designated interface between two or more networks, such as a router or proxy server. Hence, personal firewalls allow a security policy to be defined for individual computers, whereas a conventional firewall controls the policy between the networks that it connects. The per-computer scope of personal firewalls is useful to protect machines that are moved across different networks. For example, a laptop computer may be used on a trusted intranet at a workplace where minimal protection is needed as a conventional firewall is already in pla ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Webmin
Webmin is a powerful and flexible web-based server management control panel for Unix-like systems. Webmin allows the user to configure operating system internals, such as users, disk quotas, services or configuration files, as well as modify and control open-source apps, such as BIND, Apache HTTP Server, PHP or MySQL. General description Webmin is largely based on Perl, running as its own process and web server. It defaults to TCP port 10000 for communicating, and can be configured to use SSL if OpenSSL is installed with additional required Perl Modules. Webmin is built around modules, which have an interface to the configuration files and the Webmin server, which makes it simple to add new functionality. Due to Webmin's modular design, it is possible for anyone who is interested to write plugins for desktop configuration. Webmin allows for controlling many machines through a single interface, or seamless login on other Webmin hosts on the same subnet or LAN. Webmi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Kernel
The Linux kernel is a free and open-source, monolithic, modular, multitasking, Unix-like operating system kernel. It was originally authored in 1991 by Linus Torvalds for his i386-based PC, and it was soon adopted as the kernel for the GNU operating system, which was written to be a free (libre) replacement for Unix. Linux is provided under the GNU General Public License version 2 only, but it contains files under other compatible licenses. Since the late 1990s, it has been included as part of a large number of operating system distributions, many of which are commonly also called Linux. Linux is deployed on a wide variety of computing systems, such as embedded devices, mobile devices (including its use in the Android operating system), personal computers, servers, mainframes, and supercomputers. It can be tailored for specific architectures and for several usage scenarios using a family of simple commands (that is, without the need of manually editing its source c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Daemon (computing)
In multitasking computer operating systems, a daemon ( or ) is a computer program that runs as a background process, rather than being under the direct control of an interactive user. Traditionally, the process names of a daemon end with the letter ''d'', for clarification that the process is in fact a daemon, and for differentiation between a daemon and a normal computer program. For example, is a daemon that implements system logging facility, and is a daemon that serves incoming SSH connections. In a Unix environment, the parent process of a daemon is often, but not always, the init process. A daemon is usually created either by a process forking a child process and then immediately exiting, thus causing init to adopt the child process, or by the init process directly launching the daemon. In addition, a daemon launched by forking and exiting typically must perform other operations, such as dissociating the process from any controlling terminal (tty). Such procedures are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
English Language
English is a West Germanic language of the Indo-European language family, with its earliest forms spoken by the inhabitants of early medieval England. It is named after the Angles, one of the ancient Germanic peoples that migrated to the island of Great Britain. Existing on a dialect continuum with Scots, and then closest related to the Low Saxon and Frisian languages, English is genealogically West Germanic. However, its vocabulary is also distinctively influenced by dialects of France (about 29% of Modern English words) and Latin (also about 29%), plus some grammar and a small amount of core vocabulary influenced by Old Norse (a North Germanic language). Speakers of English are called Anglophones. The earliest forms of English, collectively known as Old English, evolved from a group of West Germanic ( Ingvaeonic) dialects brought to Great Britain by Anglo-Saxon settlers in the 5th century and further mutated by Norse-speaking Viking settlers starting in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ipchains
Linux IP Firewalling Chains, normally called ipchains, is free software to control the packet filter or firewall capabilities in the 2.2 series of Linux kernels. It superseded ipfirewall (managed by ipfwadm command), but was replaced by iptables in the 2.4 series. Unlike iptables, ipchains is stateless. It is a rewrite of Linux's previous IPv4 firewall, ipfirewall. This newer ipchains was required to manage the packet filter in Linux kernels starting with version 2.1.102 (which was a 2.2 development release). Patches are also available to add ipchains to 2.0 and earlier 2.1 series kernels. Improvements include larger maxima for packet counting, filtering for fragmented packets and a wider range of protocols, and the ability to match packets based on the inverse of a rule. The ipchains suite also included some shell scripts for easier maintenance and to emulate the behavior of the old ipfwadm command. The ipchains software was superseded by the iptables system in Linux kerne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |