|
Session (software)
Session is a cross-platform end-to-end encrypted instant messaging application emphasizing user confidentiality and anonymity. Developed and maintained by the non-profit The Session Technology Foundation, it employs a blockchain-based decentralized network for transmission. Users can send one-to-one and group messages, including various media types such as files, voice notes, images, and videos. Session provides applications for various platforms, such as macOS, Windows, and Linux, along with mobile clients available on both iOS and Android. Features Session does not require a telephone number or email address for account creation. Instead, it utilizes a randomly generated 66-digit alphanumeric number for user identification. Communication between users, including messages, voice clips, photos, and files, is end-to-end encrypted using the Session protocol. Session uses the Loki blockchain network for transmissions. In 2021, an independent review by the third-party Quarksla ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Android 6
Android Marshmallow ( codenamed Android M during development) is the sixth major version of the Android operating system developed by Google, being the successor to Android Lollipop. It was announced at Google I/O on May 28, 2015, and released the same day as a beta, before being officially released on September 29, 2015. It was succeeded by Android Nougat on August 22, 2016. Android Marshmallow primarily focuses on improving the overall user experience of its predecessor. It introduced a new opt-in permissions architecture, new APIs for contextual assistants (first used by a new feature " Now on Tap" to provide context-sensitive search results), a new power management system that reduces background activity when a device is not being physically handled, native support for fingerprint recognition and USB-C connectors, the ability to migrate data and applications to a microSD card, and other internal changes. Android Marshmallow was met by low adoption numbers, with 13.3% of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fork (software Development)
In software development, a fork is a codebase that is created by duplicating an existing codebase and, generally, is subsequently modified independently of the original. Software built from a fork initially has identical behavior as software built from the original code, but as the source code is increasingly modified, the resulting software tends to have increasingly different behavior compared to the original. A fork is a form of branching, but generally involves storing the forked files separately from the original; not in the repository. Reasons for forking a codebase include user preference, stagnated or discontinued development of the original software or a schism in the developer community. Forking proprietary software (such as Unix) is prohibited by copyright law without explicit permission, but free and open-source software, by definition, may be forked without permission. Etymology The word ''fork'' has been used to mean "to divide in branches, go separate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Privacy Software
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and applications of the World Wide Web (WWW), electronic mail, internet telephony, streaming media and file sharing. The origins of the Internet date back to research that enabled the time-sharing of computer resources, the development of packet switching in the 1960s and the design of computer networks for data communication. The set of rules (communication protocols) to enable internetworking on the Internet arose from research and development commissioned in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instant Messaging Clients Programmed In Java
In physics and the philosophy of science, instant refers to an infinitesimal interval in time, whose passage is instantaneous. In ordinary speech, an instant has been defined as "a point or very short space of time," a notion deriving from its etymological source, the Latin verb ''instare'', from ''in-'' + ''stare'' ('to stand'), meaning 'to stand upon or near.' The continuous nature of time and its infinite divisibility was addressed by Aristotle in his ''Physics'', where he wrote on Zeno's paradoxes. The philosopher and mathematician Bertrand Russell was still seeking to define the exact nature of an instant thousands of years later. , the smallest time interval certified in regulated measurements is on the order of 397 zeptoseconds (397 × 10−21 seconds). 18th and 19th century usage Instant (usually abbreviated in print to inst.) can be used to indicate "Of the current month". For example, "the 11th inst." means the 11th day of the current month, whether that date is in the p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Free Software Programmed In Java (programming Language)
Free may refer to: Concept * Freedom, the ability to act or change without constraint or restriction * Emancipate, attaining civil and political rights or equality * Free (''gratis''), free of charge * Gratis versus libre, the difference between the two common meanings of the adjective "free". Computing * Free (programming), a function that releases dynamically allocated memory for reuse * Free software, software usable and distributable with few restrictions and no payment *, an emoji in the Enclosed Alphanumeric Supplement block. Mathematics * Free object ** Free abelian group ** Free algebra ** Free group ** Free module ** Free semigroup * Free variable People * Free (surname) * Free (rapper) (born 1968), or Free Marie, American rapper and media personality * Free, a pseudonym for the activist and writer Abbie Hoffman * Free (active 2003–), American musician in the band FreeSol Arts and media Film and television * ''Free'' (film), a 2001 American dram ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Free And Open-source Android Software
Free may refer to: Concept * Freedom, the ability to act or change without constraint or restriction * Emancipate, attaining civil and political rights or equality * Free (gratis), Free (''gratis''), free of charge * Gratis versus libre, the difference between the two common meanings of the adjective "free". Computing * Free (programming), a function that releases dynamically allocated memory for reuse * Free software, software usable and distributable with few restrictions and no payment *, an emoji in the Enclosed Alphanumeric Supplement block. Mathematics * Free object ** Free abelian group ** Free algebra ** Free group ** Free module ** Free semigroup * Free variable People * Free (surname) * Free (rapper) (born 1968), or Free Marie, American rapper and media personality * Free, a pseudonym for the activist and writer Abbie Hoffman * Free (active 2003–), American musician in the band FreeSol Arts and media Film and television * Free (film), ''Free'' (film), a 200 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Software
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information on computers as well as the digital information that is sent to other computers over the Internet. Classification There are many software products which provide encryption. Software encryption uses a cipher to obscure the content into ciphertext. One way to classify this type of software is the type of cipher used. Ciphers can be divided into two categories: public key ciphers (also known as asymmetric ciphers), and symmetric key ciphers. Encryption software can be based on either public key or symmetric key encryption. Another way to classify software encryption is to categorize its purpose. Using this approach, software encryption may be classified into software which encrypts " data in transit" and software which encrypts " data at rest". Data in transit generally uses public key ciphers, and data at rest generally us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deniable Authentication
In cryptography, deniable authentication refers to message authentication between a set of participants where the participants themselves can be confident in the authenticity of the messages, but it cannot be proved to a third party after the event. In practice, deniable authentication between two parties can be achieved through the use of message authentication codes (MACs) by making sure that if an attacker is able to decrypt the messages, they would also know the MAC key as part of the protocol, and would thus be able to forge authentic-looking messages. For example, in the Off-the-Record Messaging (OTR) protocol, MAC keys are derived from the asymmetric decryption key through a cryptographic hash function. In addition to that, the OTR protocol also reveals used MAC keys as part of the next message, after they have already been used to authenticate previously received messages, and will not be re-used. See also * Deniable encryption * Plausible deniability * Malleability * Unden ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
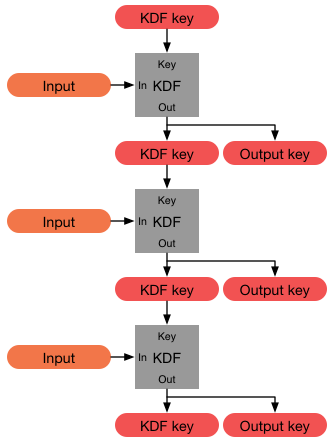
Forward Secrecy
In cryptography, forward secrecy (FS), also known as perfect forward secrecy (PFS), is a feature of specific key-agreement protocols that gives assurances that session keys will not be compromised even if long-term secrets used in the session key exchange are compromised, limiting damage. For TLS, the long-term secret is typically the private key of the server. Forward secrecy protects past sessions against future compromises of keys or passwords. By generating a unique session key for every session a user initiates, the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key. This by itself is not sufficient for forward secrecy which additionally requires that a long-term secret compromise does not affect the security of past session keys. Forward secrecy protects data on the transport layer of a network that uses common transport layer security protocols, including OpenSSL, when its long-te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multi-factor Authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more distinct types of evidence (or factors) to an authentication mechanism. MFA protects personal data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password. Usage of MFA has increased in recent years. Security issues which can cause the bypass of MFA are fatigue attacks, phishing and SIM swapping. Accounts with MFA enabled are significantly less likely to be compromised. Authentication factors Authentication takes place when someone tries to log into a computer resource (such as a computer network, device, or application). The resource requires the user to supply the identity by which the user is known to the resource, along wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |