|
Security Operations Center (computing)
An information security operations center (ISOC or SOC) is a facility where enterprise information systems (web sites, applications, databases, data centers and servers, networks, desktops and other endpoints) are monitored, assessed, and defended. Objective A SOC is related to the people, processes and technologies that provide situational awareness through the detection, containment, and remediation of IT threats in order to manage and enhance an organization's security posture. A SOC will handle, on behalf of an institution or company, any threatening IT incident, and will ensure that it is properly identified, analyzed, communicated, investigated and reported. The SOC also monitors applications to identify a possible cyber-attack or intrusion (event), and determines if it is a genuine malicious threat (incident), and if it could affect business. Regulatory requirements Establishing and operating a SOC is expensive and difficult; organisations should need a good reason ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Operations Center Photograph, C
National may refer to: Common uses * Nation or country ** Nationality – a ''national'' is a person who is subject to a nation, regardless of whether the person has full rights as a citizen Places in the United States * National, Maryland, census-designated place * National, Nevada, ghost town * National, Utah, ghost town * National, West Virginia, unincorporated community Commerce * National (brand), a brand name of electronic goods from Panasonic * National Benzole (or simply known as National), former petrol station chain in the UK, merged with BP * National Book Store, a bookstore and office supplies chain in the Philippines * National Car Rental, an American rental car company * National Energy Systems, a former name of Eco Marine Power * National Entertainment Commission, a former name of the Media Rating Council * National Motor Vehicle Company, Indianapolis, Indiana, USA 1900–1924 * National Radio Company, Malden, Massachusetts, USA 1914–1991 * National Supermarket ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Engineering
Computer engineering (CE, CoE, or CpE) is a branch of engineering specialized in developing computer hardware and software. It integrates several fields of electrical engineering, electronics engineering and computer science. Computer engineering is referred to as ''electrical and computer engineering'' or '' computer science and engineering'' at some universities. Computer engineers require training in hardware-software integration, software design, and software engineering. It can encompass areas such as electromagnetism, artificial intelligence (AI), robotics, computer networks, computer architecture and operating systems. Computer engineers are involved in many hardware and software aspects of computing, from the design of individual microcontrollers, microprocessors, personal computers, and supercomputers, to circuit design. This field of engineering not only focuses on how computer systems themselves work, but also on how to integrate them into the larger pictur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
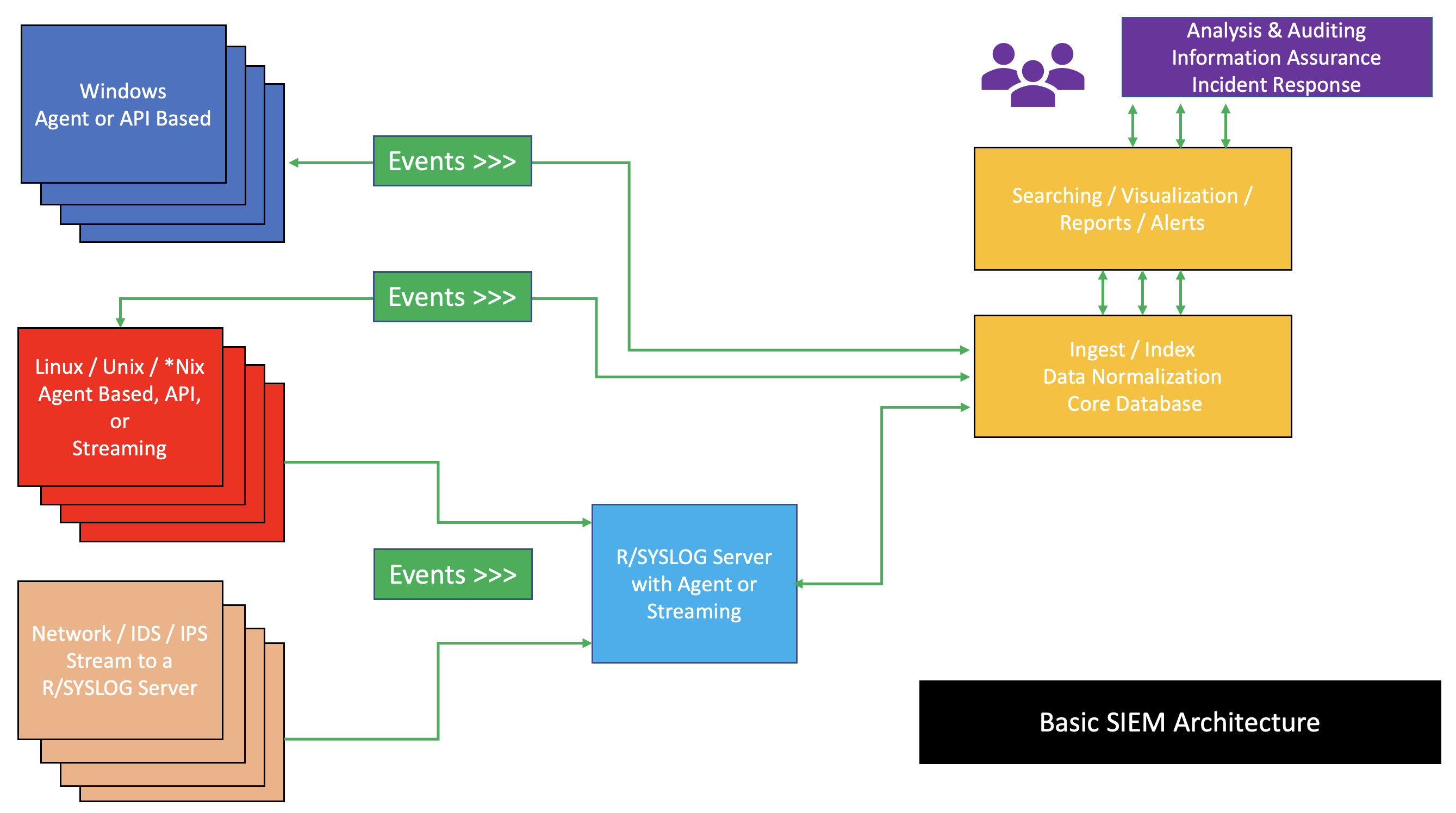
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Infrastructure
Information technology infrastructure is defined broadly as a set of information technology (IT) components that are the foundation of an IT service; typically physical components (Computer hardware, computer and networking hardware and facilities), but also various software and Computer network, network components. According to the ITIL Foundation Course Glossary, IT Infrastructure can also be termed as “All of the hardware, software, networks, facilities, etc., that are required to develop, test, deliver, monitor, control or support IT services. The term IT infrastructure includes all of the Information Technology but not the associated People, Processes and documentation.” Overview In IT Infrastructure, the above technological components contribute to and drive business functions. Leaders and managers within the IT field are responsible for ensuring that both the physical hardware and software networks and resources are working optimally. IT infrastructure can be looked at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shadow IT
In organizations, shadow IT refers to information technology (IT) systems deployed by departments other than the central IT department, to bypass limitations and restrictions that have been imposed by central information systems. While it can promote innovation and productivity, shadow IT introduces security risks and compliance concerns, especially when such systems are not aligned with corporate governance. Origins Information systems in large organizations can be a source of frustration for their users. In order to bypass limitations of solutions provided by a centralized IT department, as well as restrictions that are deemed detrimental to individual productivity, non-IT departments might develop independent IT resources and for the specific or urgent need or requirements. In some cases, IT specialists could be recruited or software solutions procured outside of the centralized IT department, sometimes without the knowledge, or approval of corporate governance channels. Ben ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Separation Of Duties
Separation of duties (SoD), also known as segregation of duties, is the concept of having more than one person required to complete a task. It is an administrative control used by organisations to prevent fraud, sabotage, theft, misuse of information, and other security compromises. In the political realm, it is known as the separation of powers, as can be seen in democracies where the government is separated into three independent branches: a legislature, an executive, and a judiciary. General description Separation of duties is a key concept of internal controls. Increased protection from fraud and errors must be balanced with the increased cost/effort required. In essence, SoD implements an appropriate level of checks and balances upon the activities of individuals. R. A. Botha and J. H. P. Eloff in the ''IBM Systems Journal'' describe SoD as follows. Separation of duty, as a security principle, has as its primary objective the prevention of fraud and errors. This objective ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Operations Center
A network operations center (NOC, pronounced like the word ''knock''), also known as a "network management center", is one or more locations from which network monitoring and control, or network management, is exercised over a computer, telecommunication or satellite network. __TOC__ History The earliest NOCs started during the 1960s. A Network Control Center was opened in New York by AT&T in 1962 which used status boards to display switch and routing information, in real-time, from AT&T's most important toll switches. AT&T later replaced this Network Control Center with a modernized NOC in 1977, located in Bedminster, New Jersey. Purpose NOCs are implemented by business organizations, public utilities, universities, and government agencies that oversee complex networking environments that require high availability. NOC personnel are responsible for monitoring one or many networks for certain conditions that may require special attention to avoid degraded service. Organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Managed Security Service
In computing, managed security services (MSS) are network security services that have been outsourced to a service provider. A company providing such a service is a managed security service provider (MSSP) The roots of MSSPs are in the Internet Service Providers (ISPs) in the mid to late 1990s. Initially, ISP(s) would sell customers a firewall appliance, as customer premises equipment (CPE), and for an additional fee would manage the customer-owned firewall over a dial-up connection. According to recent industry research, most organizations (74%) manage IT security in-house, but 82% of IT professionals said they have either already partnered with, or plan to partner with, a managed security service provider. Businesses turn to managed security services providers to alleviate the pressures they face daily related to information security such as targeted malware, customer data theft, skills shortages and resource constraints. Managed security services (MSS) are also consi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information And Communication Technology
Information and communications technology (ICT) is an extensional term for information technology (IT) that stresses the role of unified communications and the integration of telecommunications (telephone lines and wireless signals) and computers, as well as necessary enterprise software, middleware, storage and audiovisual, that enable users to access, store, transmit, understand and manipulate information. ICT is also used to refer to the convergence (telecommunications), convergence of audiovisuals and telephone networks with computer networks through a single cabling or link system. There are large economic incentives to merge the telephone networks with the computer network system using a single unified system of cabling, signal distribution, and management. ICT is an umbrella term that includes any communication device, encompassing radio, television, cell phones, computer and network hardware, satellite systems and so on, as well as the various services and appliances with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Global Information Assurance Certification
Global Information Assurance Certification (GIAC) is an information security certification entity that specializes in technical and practical certification as well as new research in the form of its GIAC Gold program. SANS Institute founded the certification entity in 1999 and the term GIAC is trademarked by The Escal Institute of Advanced Technologies. GIAC provides a set of vendor-neutral computer security Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, n ... certifications linked to the training courses provided by the SANS. GIAC is specific to the leading edge technological advancement of IT security in order to keep ahead of " black hat" techniques. Papers written by individuals pursuing GIAC certifications are presented at the SANS Reading Room on GIAC's website. Initially ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certified Information Systems Security Professional
CISSP (Certified Information Systems Security Professional) is an independent information security certification granted by the International Information System Security Certification Consortium, also known as ISC2. As of July 2022, there were 156,054 ISC2 members holding the CISSP certification worldwide. In June 2004, the CISSP designation was accredited under the ANSI ISO/IEC Standard 17024:2003.ANSI Accreditation Services - International Information Systems Security Certification Consortium, Inc. (ISC)2 . It is also formally approved by the [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |