|
Proxmox Virtual Environment
Proxmox Virtual Environment (PVE, or simply Proxmox) is a virtualization platform designed for the provisioning of hyper-converged infrastructure. Proxmox allows deployment and management of virtual machines and containers. It is based on a modified Debian LTS kernel. Two types of virtualization are supported: container-based with LXC (starting from version 4.0 replacing OpenVZ used in version up to 3.4, included), and full virtualization with KVM. It includes a web-based management interface. There is also a mobile application available for controlling PVE environments. Proxmox is released under the terms of the GNU Affero General Public License, version 3. History Development of Proxmox VE started in 2005 when Dietmar Maurer and Martin Maurer, two Linux developers, discovered OpenVZ had no backup tool or management GUI. KVM was also appearing at the same time in Linux, and was added shortly afterwards. The first public release took place in April 2008. It supported contai ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, packaged as a Linux distribution (distro), which includes the kernel and supporting system software and library (computing), libraries—most of which are provided by third parties—to create a complete operating system, designed as a clone of Unix and released under the copyleft GPL license. List of Linux distributions, Thousands of Linux distributions exist, many based directly or indirectly on other distributions; popular Linux distributions include Debian, Fedora Linux, Linux Mint, Arch Linux, and Ubuntu, while commercial distributions include Red Hat Enterprise Linux, SUSE Linux Enterprise, and ChromeOS. Linux distributions are frequently used in server platforms. Many Linux distributions use the word "Linux" in their name, but the Free ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenVZ
OpenVZ (Open Virtuozzo) is an operating-system-level virtualization technology for Linux. It allows a physical server to run multiple isolated operating system instances, called containers, virtual private servers (VPSs), or virtual environments (VEs). OpenVZ is similar to Solaris Containers and LXC. OpenVZ compared to other virtualization technologies While virtualization technologies such as VMware, Xen and Kernel-based Virtual Machine, KVM provide full virtualization and can run multiple operating systems and different kernel versions, OpenVZ uses a single Linux kernel and therefore can run only Linux. All OpenVZ containers share the same architecture and kernel version. This can be a disadvantage in situations where guests require different kernel versions than that of the host. However, as it does not have the overhead of a true hypervisor, it is very fast and efficient. Memory allocation with OpenVZ is soft in that memory not used in one virtual environment can be used ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proxmox Backup Server
Proxmox Backup Server (Proxmox BS) is an open-source backup software project supporting virtual machines, containers, and physical hosts. The bare-metal server is based on the Debian Linux distribution, with some extended features, such as out-of-the-box ZFS support and Linux kernel 5.4 LTS. Proxmox Backup Server is licensed under the GNU Affero General Public License, version 3. Technology Proxmox Backup Server is written mostly in Rust and implements data deduplication to reduce the storage space needed. Data is split into chunks. History Development of Proxmox Backup originally began in October 2018 to provide more efficient backup for the virtualization platform Proxmox Virtual Environment than the integrated vzdump backup tool which only allows full backups. In July 2020, the first public beta was announced. Its first stable release was announced in November, 2020. Operation Proxmox Backup uses a client-server model where the server stores the backup data. The client too ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Boot
Unified Extensible Firmware Interface (UEFI, as an acronym) is a specification for the firmware architecture of a computing platform. When a computer is powered on, the UEFI implementation is typically the first that runs, before starting the operating system. Examples include AMI Aptio, Phoenix SecureCore, TianoCore EDK II, and InsydeH2O. UEFI replaces the BIOS that was present in the boot ROM of all personal computers that are IBM PC compatible, although it can provide backwards compatibility with the BIOS using CSM booting. Unlike its predecessor, BIOS, which is a de facto standard originally created by IBM as proprietary software, UEFI is an open standard maintained by an industry consortium. Like BIOS, most UEFI implementations are proprietary. Intel developed the original ''Extensible Firmware Interface'' (''EFI'') specification. The last Intel version of EFI was 1.10 released in 2005. Subsequent versions have been developed as UEFI by the UEFI Forum. UEFI is inde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
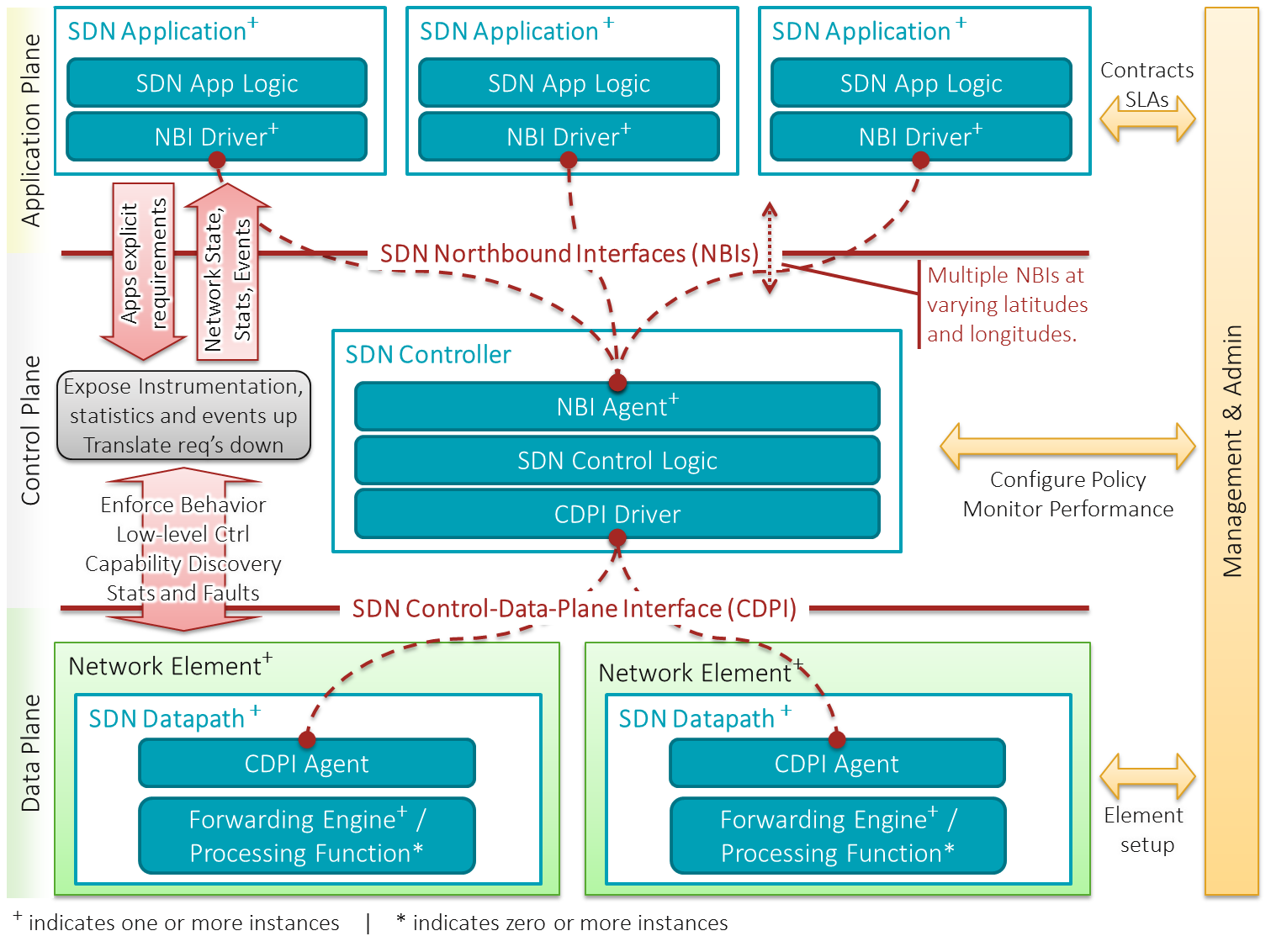
Software-defined Networking
Software-defined networking (SDN) is an approach to network management that uses abstraction to enable dynamic and programmatically efficient network configuration to create grouping and segmentation while improving network performance and monitoring in a manner more akin to cloud computing than to traditional network management. SDN is meant to improve the static architecture of traditional networks and may be employed to centralize network intelligence in one network component by disassociating the forwarding process of network packets ( data plane) from the routing process ( control plane). The control plane consists of one or more controllers, which are considered the brains of the SDN network, where the whole intelligence is incorporated. However, centralization has certain drawbacks related to security, scalability and elasticity. SDN was commonly associated with the OpenFlow protocol for remote communication with network plane elements to determine the path of network pac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WebAuthn
Web Authentication (WebAuthn) is a web standard published by the World Wide Web Consortium (W3C). Its primary purpose is to build a system of authentication for web-based applications that solves or mitigates the issues of traditional password-based authentication. Zero-knowledge proofs based on public-key signature schemes are used to register and authenticate users without the need to transmit or store private authenticating information (such as passwords) on servers. Passwords are replaced by the so-called WebAuthn Credentials which are generated client-side and stored in so-called Authenticators. WebAuthn supports both roaming authenticators (such as physical security keys) and platform authenticators (such as smartphones). While different types of credentials are supported, synced discoverable credentials (also known as Passkeys) are the most common ones. WebAuthn is a core component of the FIDO2 Project under the guidance of the FIDO Alliance. On the client side, aut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time-based One-time Password
Time-based one-time password (TOTP) is a computer algorithm that generates a one-time password (OTP) using the current time as a source of uniqueness. As an extension of the HMAC-based one-time password (HOTP) algorithm, it has been adopted as Internet Engineering Task Force (IETF) standard . TOTP is a cornerstone of the Initiative for Open Authentication (OATH) and is used in a number of two-factor authentication (2FA) systems. History Through the collaboration of several OATH members, a TOTP draft was developed in order to create an industry-backed standard. It complements the event-based one-time standard HOTP, and it offers end user organizations and enterprises more choice in selecting technologies that best fit their application requirements and security guidelines. In 2008, OATH submitted a draft version of the specification to the IETF. This version incorporates all the feedback and commentary that the authors received from the technical community based on the prior v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. Windows Server operating systems include it as a set of processes and services. Originally, only centralized domain management used Active Directory. However, it ultimately became an umbrella title for various directory-based identity-related services. A domain controller is a server running the Active Directory Domain Services (AD DS) role. It authenticates and authorizes all users and computers in a Windows domain-type network, assigning and enforcing security policies for all computers and installing or updating software. For example, when a user logs into a computer which is part of a Windows domain, Active Directory checks the submitted username and password and determines whether the user is a system administrator or a non-admin user. Furthermore, it allows the management and storage of information, provides authentication and authorization mechanisms, and establishes a f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lightweight Directory Access Protocol
The Lightweight Directory Access Protocol (LDAP ) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory services play an important role in developing intranet and Internet applications by allowing the sharing of information about users, systems, networks, services, and applications throughout the network. As examples, directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate email directory. Similarly, a telephone directory is a list of subscribers with an address and a phone number. LDAP is specified in a series of Internet Engineering Task Force (IETF) Standard Track publications known as Request for Comments (RFCs), using the description language ASN.1. The latest specification is Version 3, published aRFC 4511ref name="gracion Gracion.com. Retrieved on 2013-07-17. (a road map to t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenID
OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider (IDP) service, eliminating the need for webmasters to provide their own ''ad hoc'' login systems, and allowing users to log in to multiple unrelated websites without having to have a separate identity and password for each. Users create accounts by selecting an OpenID identity provider, and then use those accounts to sign on to any website that accepts OpenID authentication. Several large organizations either issue or accept OpenIDs on their websites. The OpenID standard provides a framework for the communication that must take place between the identity provider and the OpenID acceptor (the " relying party"). An extension to the standard (the OpenID Attribute Exchange) facilitates the transfer of user attributes, such as name and ge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pluggable Authentication Module
A pluggable authentication module (PAM) is a mechanism to integrate multiple low-level authentication schemes into a high-level application programming interface (API). PAM allows programs that rely on authentication to be written independently of the underlying authentication scheme. It was first proposed by Sun Microsystems in an Open Software Foundation Request for Comments (RFC) 86.0 dated October 1995. It was adopted as the authentication framework of the Common Desktop Environment. As a stand-alone open-source infrastructure, PAM first appeared in Red Hat Linux 3.0.4 in August 1996 in the Linux PAM project. PAM is currently supported in the AIX operating system, DragonFly BSD, FreeBSD, HP-UX, Linux, macOS, NetBSD and Solaris. Since no central standard of PAM behavior exists, there was a later attempt to standardize PAM as part of the X/Open UNIX standardization process, resulting in the X/Open Single Sign-on (XSSO) standard. This standard was not ratified, but the standar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |