|
Private Information Retrieval
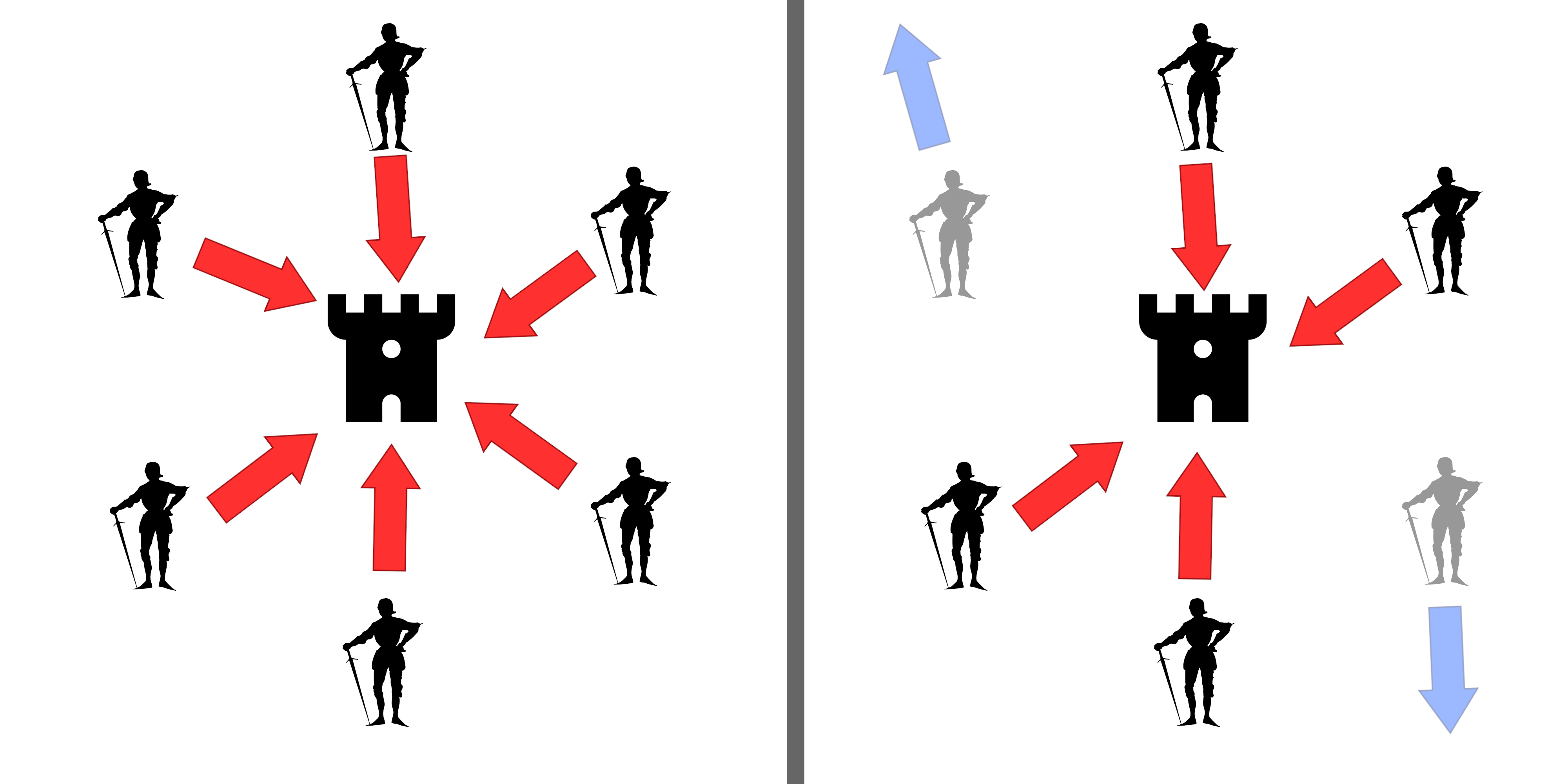
In cryptography, a private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved. PIR is a weaker version of 1-out-of-''n'' oblivious transfer, where it is also required that the user should not get information about other database items. One trivial, but very inefficient way to achieve PIR is for the server to send an entire copy of the database to the user. In fact, this is the only possible protocol (in the classical or the quantum setting) that gives the user information theoretic privacy for their query in a single-server setting. There are two ways to address this problem: make the server computationally bounded or assume that there are multiple non-cooperating servers, each having a copy of the database. The problem was introduced in 1995 by Chor, Goldreich, Kushilevitz and Sudan in the information-theoretic setting and in 1997 by Kushilevitz and Ostrov ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Yuval Ishai
Yuval (), also known as Kfar Yuval, is a moshav in northern Israel. Located in the Galilee Panhandle between Metula and the city of Kiryat Shmona, it is at the border with Lebanon and falls under the jurisdiction of Mevo'ot HaHermon Regional Council. In it had a population of . Archaeology Kfar Yuval was established on the land of the Palestinian depopulated village of al-Zūq al-Fauqānī During the Roman period, al-Zūq al-Fauqānī was called Golgol. The toponym ''Golgol'' is attested in a Late Roman boundary stone inscription discovered at Abil al-Qamḥ, and was preserved has in the Arabic ''Juneijil'' (جنيجل) near al-Zūq al-Fauqānī. Golgol has been previously misidentified with Tall al-ʿAjūl, near Abil al-Qamh, whose name is unrelated linguistically to the Roman toponym. Archaeological finds at al-Zūq al-Fauqānī point to active occupation during the Roman and Byzantine periods. Excavations have revealed a burial cave from the 2nd to 4th centuries CE, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (as for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is infeasible, ''assuming all input strings are equally likely.'' The ''resistance'' to such search is quantified as security strength: a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits, unless the space of possible input values is significantly smaller than 2^ (a practical example can be found in ); * a ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oblivious Transfer
In cryptography, an oblivious transfer (OT) protocol is a type of protocol in which a sender transfers one of potentially many pieces of information to a receiver, but remains oblivious as to what piece (if any) has been transferred. The first form of oblivious transfer was introduced in 1981 by Michael O. Rabin. In this form, the sender sends a message to the receiver with probability 1/2, while the sender remains oblivious as to whether or not the receiver received the message. Rabin's oblivious transfer scheme is based on the RSA cryptosystem. A more useful form of oblivious transfer called 1–2 oblivious transfer or "1 out of 2 oblivious transfer", was developed later by Shimon Even, Oded Goldreich, and Abraham Lempel, in order to build protocols for secure multiparty computation. It is generalized to "1 out of ''n'' oblivious transfer" where the user gets exactly one database element without the server getting to know which element was queried, and without the user know ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tal Malkin
Tal Geula Malkin (; born 1970) is an Israeli-American cryptographer who works as a professor of computer science at Columbia University, where she heads the Cryptography Lab and the Data Science Institute Cybersecurity Center. Education and career Malkin graduated summa cum laude from Bar-Ilan University in 1993, with a bachelor's degree in mathematics and computer science. She earned a master's degree in computer science from Weizmann Institute of Science in 1995, with the master's thesis ''Deductive Tableaux for Temporal Logic'' supervised by Amir Pnueli, and completed a Ph.D. in 2000 at the Massachusetts Institute of Technology with the dissertation ''A Study of Secure Database Access and General Two-Party Computation'' supervised by Shafi Goldwasser. As a doctoral student, she also worked as an intern for IBM Research at the Thomas J. Watson Research Center, and as a research scientist for AT&T Labs, continuing there through 2002. In 2003 she joined Columbia University as an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-way Function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems. This has nothing to do with whether the function is one-to-one; finding any one input with the desired image is considered a successful inversion. (See , below.) The existence of such one-way functions is still an open conjecture. Their existence would prove that the complexity classes P and NP are not equal, thus resolving the foremost unsolved question of theoretical computer science.Oded Goldreich (2001). Foundations of Cryptography: Volume 1, Basic Toolsdraft availablefrom author's site). Cambridge University Press. . See als The converse is not known to be true, i.e. the existence of a proof that P ≠ NP would not directly imply the existence of one-way functions. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SourceForge
SourceForge is a web service founded by Geoffrey B. Jeffery, Tim Perdue, and Drew Streib in November 1999. SourceForge provides a centralized software discovery platform, including an online platform for managing and hosting open-source software projects, and a directory for comparing and reviewing B2B software that lists over 104,500 business software titles. It provides source code repository hosting, bug tracking, mirroring of downloads for load balancing, a wiki for documentation, developer and user mailing lists, user-support forums, user-written reviews and ratings, a news bulletin, micro-blog for publishing project updates, and other features. SourceForge was one of the first to offer this service free of charge to open-source projects. Since 2012, the website has run on Apache Allura software. SourceForge offers free hosting and free access to tools for developers of free and open-source software. , the SourceForge repository claimed to host more than 502,00 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nadia Heninger
Nadia Heninger (born 1982) is an American cryptography, cryptographer, computer security expert, and Computational number theory, computational number theorist at the University of California, San Diego. Contributions Heninger is known for her work on freezing powered-down security devices to slow their fading memories and allow their secrets to be recovered via a cold boot attack, for her discovery that Random number generator attack, weak keys for the RSA (cryptosystem), RSA cryptosystem are in widespread use by Router (computing), internet routers and other embedded devices, for her research on how failures of forward secrecy in bad implementations of the Diffie–Hellman key exchange may have allowed the National Security Agency to decrypt large amounts of internet traffic via the Logjam (computer security), Logjam vulnerability, and for the DROWN attack, which uses servers supporting old and weak cryptography to decrypt traffic from modern clients to modern servers. Heninger' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byzantine Fault Tolerance
A Byzantine fault is a condition of a system, particularly a distributed computing system, where a fault occurs such that different symptoms are presented to different observers, including imperfect information on whether a system component has failed. The term takes its name from an allegory, the "Byzantine generals problem", developed to describe a situation in which, to avoid catastrophic failure of a system, the system's actors must agree on a strategy, but some of these actors are unreliable in such a way as to cause other (good) actors to disagree on the strategy and they may be unaware of the disagreement. A Byzantine fault is also known as a Byzantine generals problem, a Byzantine agreement problem, or a Byzantine failure. Byzantine fault tolerance (BFT) is the resilience of a fault-tolerant computer system or similar system to such conditions. Definition A Byzantine fault is any fault presenting different symptoms to different observers. A Byzantine failure is the los ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Goldwasser–Micali Cryptosystem
The Goldwasser–Micali (GM) cryptosystem is an asymmetric key encryption algorithm developed by Shafi Goldwasser and Silvio Micali in 1982. GM has the distinction of being the first probabilistic public-key encryption scheme which is provably secure under standard cryptographic assumptions. However, it is not an efficient cryptosystem, as ciphertexts may be several hundred times larger than the initial plaintext. To prove the security properties of the cryptosystem, Goldwasser and Micali proposed the widely used definition of semantic security. Basis The GM cryptosystem is semantically secure based on the assumed intractability of the quadratic residuosity problem modulo a composite ''N'' = ''pq'' where ''p, q'' are large primes. This assumption states that given (''x'', ''N'') it is difficult to determine whether ''x'' is a quadratic residue modulo ''N'' (i.e., ''x'' = ''y''2 mod ''N'' for some ''y''), when the Jacobi symbol for ''x'' is +1. The quadratic residue probl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Homomorphic Encryption
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without first having to decrypt it. The resulting computations are left in an encrypted form which, when decrypted, result in an output that is identical to that of the operations performed on the unencrypted data. While homomorphic encryption does not protect against side-channel attacks that observe behavior, it can be used for privacy-preserving outsourced storage and computation. This allows data to be encrypted and outsourced to commercial cloud environments for processing, all while encrypted. As an example of a practical application of homomorphic encryption: encrypted photographs can be scanned for points of interest, without revealing the contents of a photo. However, observation of side-channels can see a photograph being sent to a point-of-interest lookup service, revealing the fact that photographs were taken. Thus, homomorphic encryption eliminates the need ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |