|
Oblivious Data Structure
: In computer science, an oblivious data structure is a data structure that gives no information about the sequence or pattern of the operations that have been applied except for the final result of the operations.Xiao Wang, Kartik Nayak, Chang Liu, Hubert Chan, Elaine Shi, Emil Stefanov and Yan Huang. Oblivious Data Structures. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security In most conditions, even if the data is encrypted, the access pattern can be achieved, and this pattern can leak some important information such as encryption keys. And in the outsourcing of cloud data, this leakage of access pattern is still very serious. An access pattern is a specification of an access mode for every attribute of a relation schema. For example, the sequences of user read or write the data in the cloud are access patterns. We say a machine is oblivious if the sequence in which it accesses is equivalent for any two inputs with the same running time. So th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, information theory, and automation) to practical disciplines (including the design and implementation of hardware and software). Computer science is generally considered an area of academic research and distinct from computer programming. Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and for preventing security vulnerabilities. Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of repositories ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elaine Shi
Elaine Runting Shi is a Chinese and American computer scientist and cryptographer, whose research has included work on blockchain and smart contracts, secure distributed systems, and the oblivious RAM model, and cryptographic techniques for encrypted computation. She is an associate professor of computer science and electrical engineering at Carnegie Mellon University. Education and career Shi is originally from Hangzhou, and did her undergraduate studies at Tsinghua University before completing her doctorate in 2008 at Carnegie Mellon University. Her dissertation, ''Evaluating Predicates over Encrypted Data'', was supervised by Adrian Perrig. She worked as a researcher at PARC and the University of California, Berkeley, as an assistant professor at the University of Maryland, College Park, and as an associate professor at Cornell University before coming back to Carnegie Mellon University Carnegie Mellon University (CMU) is a private research university in Pittsburgh, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud
In meteorology, a cloud is an aerosol consisting of a visible mass of miniature liquid droplets, frozen crystals, or other particles suspended in the atmosphere of a planetary body or similar space. Water or various other chemicals may compose the droplets and crystals. On Earth, clouds are formed as a result of saturation of the air when it is cooled to its dew point, or when it gains sufficient moisture (usually in the form of water vapor) from an adjacent source to raise the dew point to the ambient temperature. They are seen in the Earth's homosphere, which includes the troposphere, stratosphere, and mesosphere. Nephology is the science of clouds, which is undertaken in the cloud physics branch of meteorology. There are two methods of naming clouds in their respective layers of the homosphere, Latin and common name. Genus types in the troposphere, the atmospheric layer closest to Earth's surface, have Latin names because of the universal adoption of L ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Outsourcing
Outsourcing is an agreement in which one company hires another company to be responsible for a planned or existing activity which otherwise is or could be carried out internally, i.e. in-house, and sometimes involves transferring employees and assets from one firm to another. The term ''outsourcing'', which came from the phrase ''outside resourcing'', originated no later than 1981. The concept, which '' The Economist'' says has "made its presence felt since the time of the Second World War", often involves the contracting of a business process (e.g., payroll processing, claims processing), operational, and/or non-core functions, such as manufacturing, facility management, call center/call center support. The practice of handing over control of public services to private enterprises ( privatization), even if conducted on a limited, short-term basis, may also be described as outsourcing. Outsourcing includes both foreign and domestic contracting, and sometimes includes offsh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
In computing, a server is a piece of computer hardware or software (computer program) that provides functionality for other programs or devices, called " clients". This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or ackn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases spans formal techniques and practical considerations, including data modeling, efficient data representation and storage, query languages, security and privacy of sensitive data, and distributed computing issues, including supporting concurrent access and fault tolerance. A database management system (DBMS) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS software additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an appli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in milit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oblivious Ram
An oblivious RAM (ORAM) simulator is a compiler that transforms algorithms in such a way that the resulting algorithms preserve the input-output behavior of the original algorithm but the distribution of memory access pattern of the transformed algorithm is independent of the memory access pattern of the original algorithm. The use of ORAMs is motivated by the fact that an adversary can obtain nontrivial information about the execution of a program and the nature of the data that it is dealing with, just by observing the pattern in which various locations of memory are accessed during its execution. An adversary can get this information even if the data values are all encrypted. The definition suits equally well to the settings of protected programs running on unprotected shared memory as well as a client running a program on its system by accessing previously stored data on a remote server. The concept was formulated by Oded Goldreich and Rafail Ostrovsky in 1996. Definiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
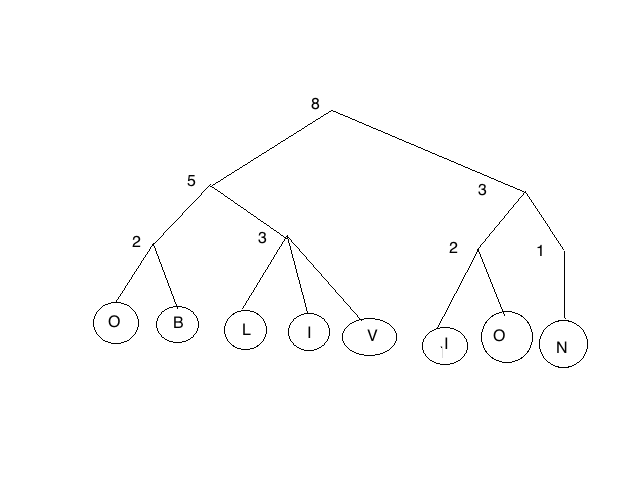
2–3 Tree
In computer science, a 2–3 tree is a tree data structure, where every node with children (internal node) has either two children (2-node) and one data element or three children (3-nodes) and two data elements. A 2–3 tree is a B-tree of order 3. Nodes on the outside of the tree (leaf nodes) have no children and one or two data elements. 2–3 trees were invented by John Hopcroft in 1970. 2–3 trees are required to be balanced, meaning that each leaf is at the same level. It follows that each right, center, and left subtree of a node contains the same or close to the same amount of data. Definitions We say that an internal node is a 2-node if it has ''one'' data element and ''two'' children. We say that an internal node is a 3-node if it has ''two'' data elements and ''three'' children. A 4-node, with three data elements, may be temporarily created during manipulation of the tree but is never persistently stored in the tree. Image:2-3-4 tree 2-node.svg, 2 node Image:2-3-4-t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)
