|
Network Security Toolkit
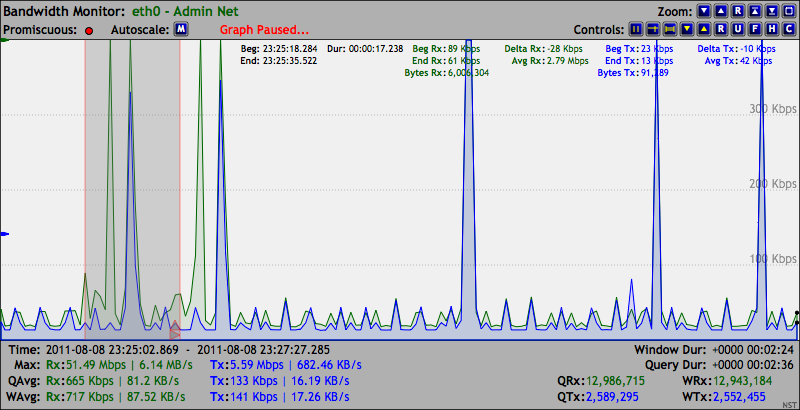
Network Security Toolkit (NST) is a Linux-based Live DVD/USB Flash Drive that provides a set of free and open-source computer security and networking tools to perform routine security and networking diagnostic and monitoring tasks. The distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines. The majority of tools published in the article "Top 125 security tools" by Insecure.org are available in the toolkit. NST has package management capabilities similar to Fedora and maintains its own repository of additional packages. Features Many tasks that can be performed within NST are available through a web interface called NST WUI. Among the tools that can be used through this interface are nmap with the vizualization tool ZenMap, ntop, a Network Interface Bandwidth Monitor, a Network Segment ARP Scanner, a session manager for VNC, a minicom-based terminal server, serial port monitoring, and WPA PSK management. Oth ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTML
The HyperText Markup Language or HTML is the standard markup language for documents designed to be displayed in a web browser. It can be assisted by technologies such as Cascading Style Sheets (CSS) and scripting languages such as JavaScript. Web browsers receive HTML documents from a web server or from local storage and render the documents into multimedia web pages. HTML describes the structure of a web page semantically and originally included cues for the appearance of the document. HTML elements are the building blocks of HTML pages. With HTML constructs, images and other objects such as interactive forms may be embedded into the rendered page. HTML provides a means to create structured documents by denoting structural semantics for text such as headings, paragraphs, lists, links, quotes, and other items. HTML elements are delineated by ''tags'', written using angle brackets. Tags such as and directly introduce content into the page. Other tags such as sur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues. Wireshark is cross-platform, using the Qt widget toolkit in current releases to implement its user interface, and using pcap to capture packets; it runs on Linux, macOS, BSD, Solaris, some other Unix-like operating systems, and Microsoft Windows. There is also a terminal-based (non-GUI) version called TShark. Wireshark, and the other programs distributed with it such as TShark, are free software, released under the terms of the GNU General Public License version 2 or any later version. Functionality Wireshark is very similar to tcpdump, but has a graphical front-end and integrated sorting and filtering options. Wireshark lets the user put network interface controllers into promiscuous mode (if supported b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ntopng
ntopng is computer software for monitoring traffic on a computer network. It is designed to be a high-performance, low-resource replacement for ntop. The name is derived from ''ntop next generation''. ntopng is open-source software released under the GNU General Public License (GPLv3) for software. Source code versions are available for the operating systems: Unix, Linux, BSD, Mac OS X, and Windows. Binary versions are available for CentOS, Ubuntu, and OS X. A demo binary is available for Windows that limits analysis to 2,000 packets. ntopng's engine is written in the programming language C++. The optional web interface is written in Lua. ntopng relies on the Redis key-value server rather than a traditional database, takes advantage of nDPI for protocol detection, supports geolocation of hosts, and is able to display real-time flow analysis for connected hosts. Sample use ntopng --dns-mode 1 --interface 5 --daemon --redis localhost:6379 --verbose Explanation: run ntopng ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pre-shared Key
In cryptography, a pre-shared key (PSK) is a shared secret which was previously shared between the two parties using some secure channel before it needs to be used. Key To build a key from shared secret, the key derivation function is typically used. Such systems almost always use symmetric key cryptographic algorithms. The term PSK is used in Wi-Fi encryption such as Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), where the method is called WPA-PSK or WPA2-PSK, and also in the Extensible Authentication Protocol (EAP), where it is known as EAP-PSK. In all these cases, both the wireless access points (AP) and all clients ''share'' the same key. The characteristics of this secret or key are determined by the system which uses it; some system designs require that such keys be in a particular format. It can be a password, a passphrase, or a hexadecimal string. The secret is used by all systems involved in the cryptographic processes used to secure the traffic between ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA), Wi-Fi Protected Access II (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security and security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, Wired Equivalent Privacy (WEP). WPA (sometimes referred to TKIP standard) became available in 2003. The Wi-Fi Alliance intended it as an intermediate measure in anticipation of the availability of the more secure and complex WPA2, which became available in 2004 and is a common shorthand for the full IEEE 802.11i (or IEEE 802.11i-2004) standard. In January 2018, Wi-Fi Alliance announced the release of WPA3 with several security improvements over WPA2. Versions WPA The Wi-Fi Alliance intended WPA as an intermediate measure to take the place of WEP pending the availability of the full IEEE 802.11i standard. WPA could be implemented throu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RS-232
In telecommunications, RS-232 or Recommended Standard 232 is a standard originally introduced in 1960 for serial communication transmission of data. It formally defines signals connecting between a ''DTE'' ('' data terminal equipment'') such as a computer terminal, and a ''DCE'' ('' data circuit-terminating equipment'' or '' data communication equipment''), such as a modem. The standard defines the electrical characteristics and timing of signals, the meaning of signals, and the physical size and pinout of connectors. The current version of the standard is ''TIA-232-F Interface Between Data Terminal Equipment and Data Circuit-Terminating Equipment Employing Serial Binary Data Interchange'', issued in 1997. The RS-232 standard had been commonly used in computer serial ports and is still widely used in industrial communication devices. A serial port complying with the RS-232 standard was once a standard feature of many types of computers. Personal computers used them for c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Minicom
Minicom is a text-based modem control and terminal emulator program for Unix-like operating systems, originally written by Miquel van Smoorenburg, and modeled somewhat after the popular MS-DOS program Telix but is open source. Minicom includes a dialing directory, ANSI and VT100 emulation, an (external) scripting language, and other features. Minicom is a menu-driven communications program. It also has an auto ZMODEM download. It now comes packaged in most major Linux distribution repositories such as Debian, Ubuntu and Arch Linux. A common use for Minicom is when setting up a remote serial console, perhaps as a last resort to access a computer if the LAN is down. This can be done using nothing more than a 386 laptop with a Minicom floppy distribution such as Pitux or Serial Terminal Linux. Minicom is useful to create console for devices having no display such as switches, routers or server blade enclosure. It is also useful for data logging output from serial devices ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ntop
ntop is computer software that probes a computer network to show network use in a way similar to what the program top does for processes. Software In interactive mode, it displays the network status on the user's terminal. In Web mode, it acts as a web server, creating a HTML dump of the network status. It supports a NetFlow-sFlow emitter-collector, a Hypertext Transfer Protocol (HTTP) based client interface for creating ntop-centric monitoring applications, and RRDtool (RRD) for persistently storing traffic statistics. ntop is available for both Unix and Win32-based platforms. It has been developed by Luca Deri, an Italian research scientist and network manager at University of Pisa. Common usage on a Linux system is to start the ntop daemon Daimon or Daemon (Ancient Greek: , "god", "godlike", "power", "fate") originally referred to a lesser deity or guiding spirit such as the daimons of ancient Greek religion and mythology and of later Hellenistic religion and philo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nmap
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym ''Fyodor Vaskovich''). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan. Nmap started as a Linux utility and was ported to other systems including Windows, macOS, and BSD. It is most popular on Linux, followed by Windows. Features Nmap features include: * Host discovery – Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open. * Port scanning – Enumerating the open ports on target host ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Interface
In the industrial design field of human–computer interaction, a user interface (UI) is the space where interactions between humans and machines occur. The goal of this interaction is to allow effective operation and control of the machine from the human end, while the machine simultaneously feeds back information that aids the operators' decision-making process. Examples of this broad concept of user interfaces include the interactive aspects of computer operating systems, hand tools, heavy machinery operator controls and process controls. The design considerations applicable when creating user interfaces are related to, or involve such disciplines as, ergonomics and psychology. Generally, the goal of user interface design is to produce a user interface that makes it easy, efficient, and enjoyable (user-friendly) to operate a machine in the way which produces the desired result (i.e. maximum usability). This generally means that the operator needs to provide minimal input to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fedora (operating System)
Fedora Linux is a Linux distribution developed by the Fedora Project. Fedora contains software distributed under various free and open-source licenses and aims to be on the leading edge of open-source technologies. Fedora is the upstream source for Red Hat Enterprise Linux. Since the release of Fedora 35, six different editions are made available tailored to personal computer, server, cloud computing, container and Internet of Things installations. A new version of Fedora Linux is released every six months. , Fedora Linux has an estimated 1.2 million users, including Linus Torvalds (), creator of the Linux kernel. Features Fedora has a reputation for focusing on innovation, integrating new technologies early on and working closely with upstream Linux communities. Making changes upstream instead of specifically for Fedora Linux ensures that the changes are available to all Linux distributions. Fedora Linux has a relatively short life cycle: each version is usually supported ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |