|
National Counterterrorism Center
The National Counterterrorism Center (NCTC) is a United States government organization responsible for national and international counterterrorism efforts. It is based in Liberty Crossing in McLean, Virginia. The NCTC advises the United States on terrorism. Part of the Office of the Director of National Intelligence, the center brings together specialists from other federal agencies, including the CIA, the FBI, the Department of Defense, and the Department of Homeland Security. History The idea of a center to merge intelligence on terror threats was proposed by the 9/11 Commission following the completion of its investigation into the September 11 attacks, the deadliest attack in world history. Plans to create such a center were announced by President George W. Bush in his January 2003 State of the Union address. On May 1, 2003, Executive Order 13354 established the Terrorist Threat Integration Center (TTIC). In 2004, the center was renamed the NCTC and placed under the Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McLean, Virginia
McLean ( ) is an Unincorporated area#United States, unincorporated community and census-designated place in Fairfax County, Virginia, United States. The population of the community was 50,773 at the 2020 United States census, 2020 census. It is located between the Potomac River and Vienna, Virginia, Vienna within the Washington metropolitan area. McLean is home to many wealthy residents such as diplomats, military, members of Congress, and high-ranking government officials partially due to its proximity to Washington, D.C., the Pentagon and the Central Intelligence Agency. It is the location of Hickory Hill (McLean, Virginia), Hickory Hill, the former home of Ethel Kennedy, the widow of Robert F. Kennedy. It is also the location of Salona (McLean, Virginia), Salona, the former home of Henry Lee III, Light-Horse Harry Lee, the American Revolutionary War, Revolutionary War hero. History The community received its name from John Roll McLean, the former publisher and owner of ''The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence Reform And Terrorism Prevention Act
The Intelligence Reform and Terrorism Prevention Act of 2004 (IRTPA) is a 235-page Act of Congress, signed by President George W. Bush, that broadly affects United States federal terrorism laws. The act comprises several separate titles with varying subject issues. It was enacted in response to the terror attacks of September 11, 2001." Intelligence Reform and Terrorism Prevention Act of 2004." Overview This act established the position of Director of National Intelligence (DNI), the National Counterterrorism Center (NCTC), and the Privacy and Civil Liberties Oversight Board. The IRTPA requires the Department of Homeland Security (DHS) to take over the conducting of pre-flight comparisons of airline passenger information to Federal Government watch lists for international and domestic flights. The Transportation Security Administration (TSA) developed the Secure Flight program and issued rulemaking to implement this congressional mandate. Airline personnel will have the right ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Homeland Security Council
The Homeland Security Council (HSC) is an entity within the Executive Office of the President of the United States tasked with advising the president on matters relevant to Homeland Security. The current homeland security advisor is Stephen Miller. History The Homeland Security Council (HSC) is an entity within the Executive Office of the President and was created by on October 29, 2001, and subsequently expanded on by Homeland Security Presidential Directive 1. It served as the successor to the Office of Homeland Security, established on September 20, 2001, immediately after the September 11 attacks. Congress subsequently codified the HSC in the Homeland Security Act of 2002, charging it with advising the president on homeland security matters. On February 23, 2009, the Obama administration released Presidential Study Directive 1. This memorandum ordered a 60-day inter-agency review of the White House homeland security and counter-terrorism structure. The review recommend ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States National Security Council
The United States National Security Council (NSC) is the national security council used by the president of the United States for consideration of national security, military, and Foreign relations of the United States, foreign policy matters. Based in the White House, it is part of the Executive Office of the President of the United States, and composed of senior national security advisors and United States Cabinet, Cabinet officials. Since its inception in 1947 by President Harry S. Truman, the function of the council has been to advise and assist the president on national security and foreign policies. It also serves as the president's principal arm for coordinating these policies among various government agencies. The council has subsequently played a key role in most major events in Foreign policy of the United States, U.S. foreign policy, from the Korean War to the War on terror, war on terror. The NSC has counterparts in the national security councils of many other na ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
President Of The United States
The president of the United States (POTUS) is the head of state and head of government of the United States. The president directs the Federal government of the United States#Executive branch, executive branch of the Federal government of the United States, federal government and is the Powers of the president of the United States#Commander-in-chief, commander-in-chief of the United States Armed Forces. The power of the presidency has grown since the first president, George Washington, took office in 1789. While presidential power has ebbed and flowed over time, the presidency has played an increasing role in American political life since the beginning of the 20th century, carrying over into the 21st century with some expansions during the presidencies of Presidency of Franklin D. Roosevelt, Franklin D. Roosevelt and Presidency of George W. Bush, George W. Bush. In modern times, the president is one of the world's most powerful political figures and the leader of the world's ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology
Information technology (IT) is a set of related fields within information and communications technology (ICT), that encompass computer systems, software, programming languages, data processing, data and information processing, and storage. Information technology is an application of computer science and computer engineering. The term is commonly used as a synonym for computers and computer networks, but it also encompasses other information distribution technologies such as television and telephones. Several products or services within an economy are associated with information technology, including computer hardware, software, electronics, semiconductors, internet, Telecommunications equipment, telecom equipment, and e-commerce.. An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a Computer, computer system — including all Computer hardware, hardware, software, and peripheral equipment � ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence (information Gathering)
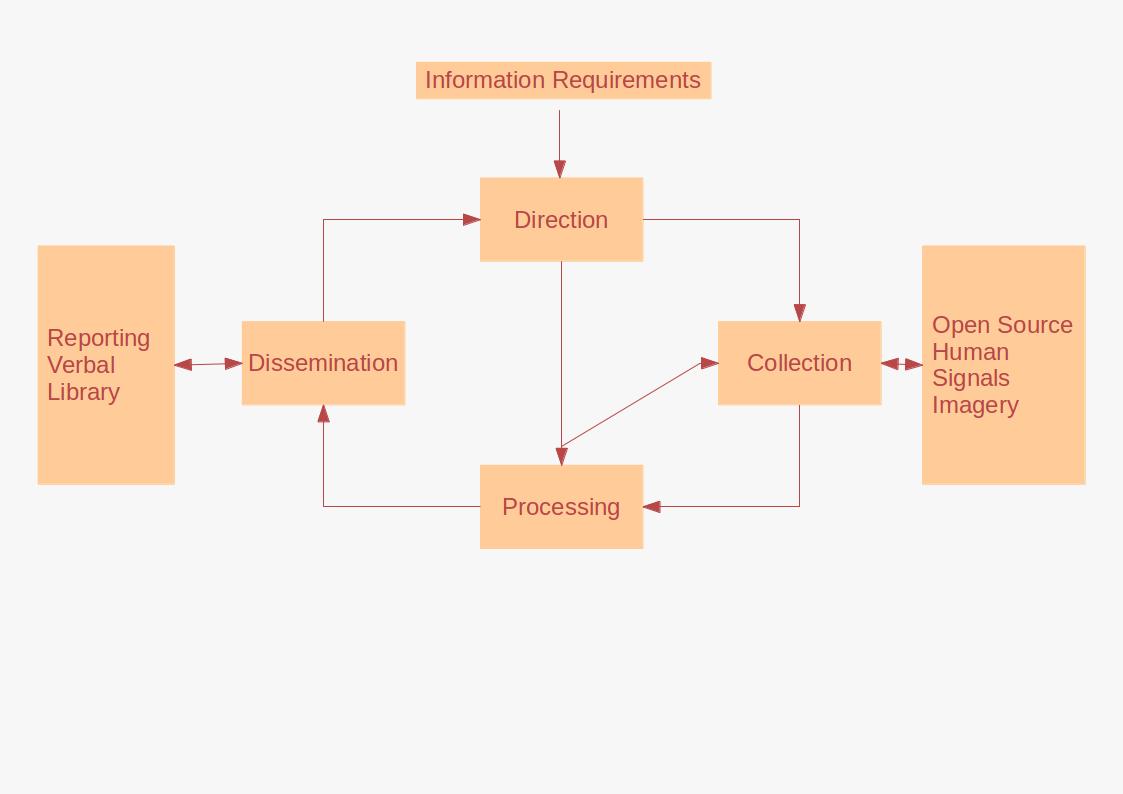
Intelligence assessment, is a specific phase of the intelligence cycle which oversees the development of behavior forecasts or recommended courses of action to the leadership of an organization, based on wide ranges of available overt and covert intelligence (also known as "intel"). There are two types of assessment; * In the beginning of the intelligence cycle, during the direction phase (also known as tasking or planning), intelligence officers assess past intelligence, identify gaps in information, and determine what new intelligence is needed. * Intelligence assessment also occurs toward the end of the intelligence cycle, during the analysis & production phase. This phase comes after collection and processing but before dissemination to policymakers. Assessments develop in response to leadership declaration requirements to inform decision-making. Assessment may be executed on behalf of a state, military or commercial organisation with ranges of information sources availa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Terrorism
Terrorism, in its broadest sense, is the use of violence against non-combatants to achieve political or ideological aims. The term is used in this regard primarily to refer to intentional violence during peacetime or in the context of war against non-combatants. There are various different definitions of terrorism, with no universal agreement about it. Different definitions of terrorism emphasize its randomness, its aim to instill fear, and its broader impact beyond its immediate victims. Modern terrorism, evolving from earlier iterations, employs various tactics to pursue political goals, often leveraging fear as a strategic tool to influence decision makers. By targeting densely populated public areas such as transportation hubs, airports, shopping centers, tourist attractions, and nightlife venues, terrorists aim to instill widespread insecurity, prompting Public policy, policy changes through Manipulation (psychology), psychological manipulation and undermining confidence ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mass Surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by Local government, local and federal governments or intelligence agency, governmental organizations, but it may also be carried out by corporations (either on behalf of governments or at their own initiative). Depending on each nation's laws and Judiciary, judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of Totalitarianism, totalitarian regimes. It is often distinguished from targeted surveillance. Mass surveillance has often been cited by agencies like the National Security Agency (NSA) as necessary to fight terrorism, prevent crime and social unrest, protect national security, and control the population. At the same time, mass surveillance has equally often been criticized for violating pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Awareness Office
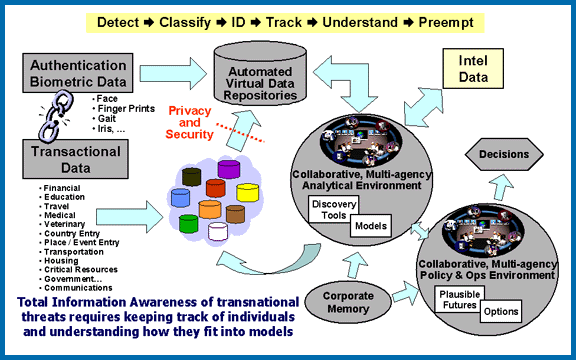
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric warfare, asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Aware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pre-crime
''Pre-crime'' (or ''precrime'') is the idea that the occurrence of a crime can be anticipated before it happens. The term was coined by science fiction author Philip K. Dick, and is increasingly used in academic literature to describe and criticise the tendency in criminal justice systems to focus on crimes not yet committed. Precrime intervenes to punish, disrupt, incapacitate or restrict those deemed to embody future crime threats. The term ''precrime'' embodies a temporal paradox, suggesting both that a crime has not yet occurred and that it is a foregone conclusion. Origins of the concept George Orwell introduced a similar concept in his 1949 novel ''Nineteen Eighty-Four'' using the term ''thoughtcrime'' to describe illegal thoughts which held banned opinions about the ruling government or intentions to act against it. A large part of how it differs from precrime is in its absolute prohibition of anti-authority ideas and emotions, regardless of the consideration of any ph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pattern Analysis
Pattern recognition is the task of assigning a Categorical variable, class to an observation based on patterns extracted from data. While similar, pattern recognition (PR) is not to be confused with pattern machines (PM) which may possess PR capabilities but their primary function is to distinguish and create emergent patterns. PR has applications in statistical data analysis, signal processing, image analysis, information retrieval, bioinformatics, data compression, computer graphics and machine learning. Pattern recognition has its origins in statistics and engineering; some modern approaches to pattern recognition include the use of machine learning, due to the increased availability of big data and a new abundance of processing power. Pattern recognition systems are commonly trained from labeled "training" data. When no labeled data are available, other algorithms can be used to discover previously unknown patterns. Data mining, KDD and data mining have a larger focus on u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |