|
NACK-Oriented Reliable Multicast
NACK-Oriented Reliable Multicast (NORM) is a transport layer Internet protocol designed to provide reliable transport in multicast groups in data networks. It is formally defined by the Internet Engineering Task Force (IETF) in Request for Comments (RFC5740 which was published in November 2009. NORM operates on top of the User Datagram Protocol (UDP), and ensures reliable communication based upon a negative acknowledgement (NACK), selective Automatic Repeat Request (ARQ) mechanism, as opposed to the positive acknowledgement (ACK) approach that the standard Transmission Control Protocol (TCP) uses. In other words, receivers using NORM only send feedback when they do not receive a packet, as opposed to the TCP model where receivers regularly acknowledge packet receipt as part of it protocol operation. This allows NORM to support large-scale receiver groups. To support further scalability, NORM also employs packet erasure coding using forward error correction (FEC) codes coupled wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Addresses
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface identification and location addressing. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP ( IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s. IP addresses are written and displayed in human-readable notations, such as in IPv4, and in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., , which is equivalent to the historically used subnet mask . The IP address space is managed globally by the Internet Assigned Numbers Authority ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
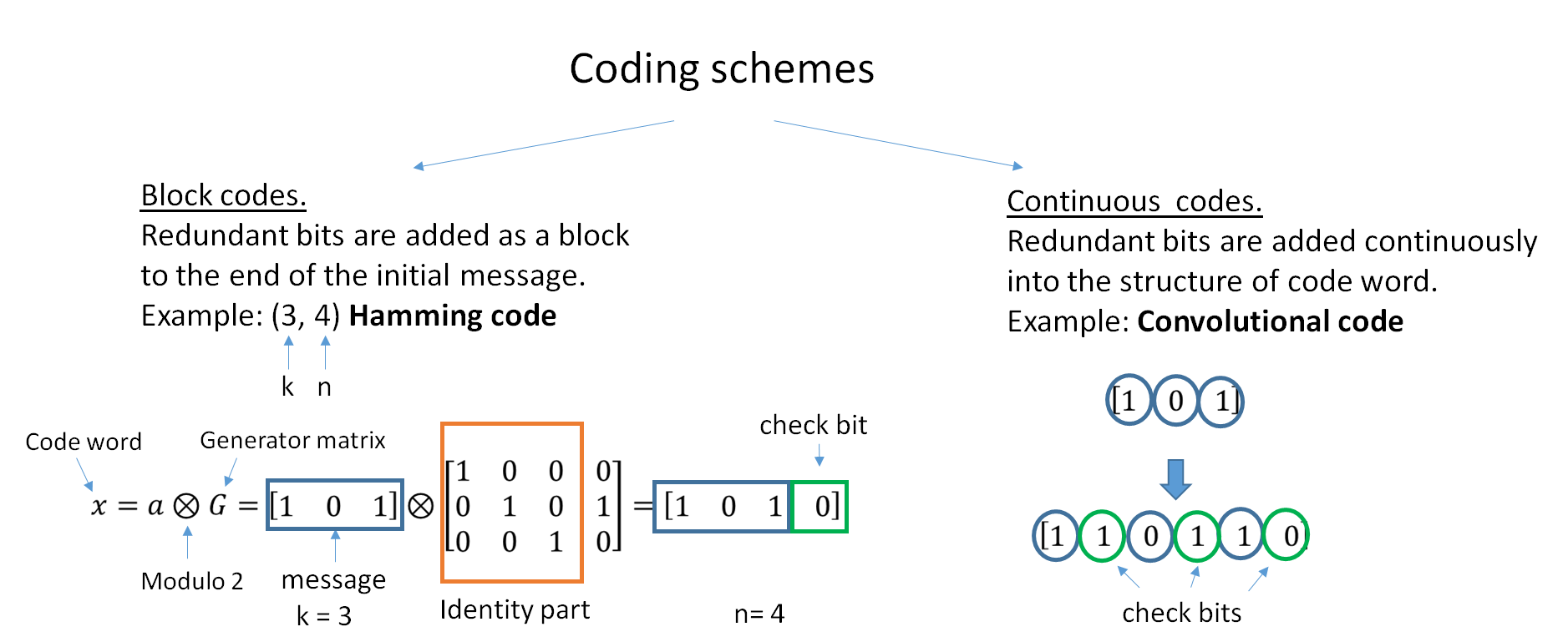
Systematic Code
In coding theory, a systematic code is any error-correcting code in which the input data is embedded in the encoded output. Conversely, in a non-systematic code the output does not contain the input symbols. Systematic codes have the advantage that the parity data can simply be appended to the source block, and receivers do not need to recover the original source symbols if received correctly – this is useful for example if error-correction coding is combined with a hash function for quickly determining the correctness of the received source symbols, or in cases where errors occur in erasures and a received symbol is thus always correct. Furthermore, for engineering purposes such as synchronization and monitoring, it is desirable to get reasonable good estimates of the received source symbols without going through the lengthy decoding process which may be carried out at a remote site at a later time. Properties Every non-systematic linear code can be transformed into a syste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forward Error Correction
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a hi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Watermark (data Synchronization)
A Watermark for data synchronization describes an object of a predefined format which provides a point of reference value for two systems/datasets attempting to establish delta/incremental synchronization; any object in the queried data source which was created, modified, or deleted after the watermark's value will be qualified as "above watermark" and should be returned to the client requesting data. This approach allows the client to retrieve only the objects which have changed since the latest watermark, and also enables the client to resume its synchronization job from where it left off in the event of some pause or downtime. Methodology Watermark term is often used in Directory Synchronization software development projects. For example, products such as Microsoft Exchange Server, Active Directory, Active Directory Application Mode (ADAM), and Microsoft Identity Integration Server 2003/ Microsoft Identity Lifecycle Manager Server 2007, as well as Cisco Unified Communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Connection-oriented Communication
Connection-oriented communication is a network communication mode in telecommunications and computer networking, where a communication session or a semi-permanent connection is established before any useful data can be transferred. The established connection ensures that data is delivered in the correct order to the upper communication layer. The alternative to connection-oriented transmission is connectionless communication, for example the datagram mode communication used by Internet Protocol (IP) and User Datagram Protocol, where data may be delivered out of order, since different network packets are routed independently and may be delivered over different paths. Connection-oriented communication may be implemented with a circuit switched connection, or a packet-mode virtual circuit connection. In the latter case, it may use either a transport layer virtual circuit protocol such as the TCP protocol, allowing data to be delivered in order. Although the lower-layer switching i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Out-of-band Data
In computer networking, out-of-band data is the data transferred through a stream that is independent from the main ''in-band'' data stream. An out-of-band data mechanism provides a conceptually independent channel, which allows any data sent via that mechanism to be kept separate from in-band data. The out-of-band data mechanism should be provided as an inherent characteristic of the data channel and transmission protocol, rather than requiring a separate channel and endpoints to be established. The term "out-of-band data" probably derives from out-of-band signaling, as used in the telecommunications industry. Example case Consider a networking application that tunnels data from a remote data source to a remote destination. The data being tunneled may consist of any bit patterns. The sending end of the tunnel may at times have conditions that it needs to notify the receiving end about. However, it cannot simply insert a message to the receiving end because that end will not be a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Session Announcement Protocol
The Session Announcement Protocol (SAP) is an experimental protocol for advertising multicast session information. SAP typically uses Session Description Protocol (SDP) as the format for Real-time Transport Protocol (RTP) session descriptions. Announcement data is sent using IP multicast and the User Datagram Protocol (UDP). Under SAP, senders periodically transmit SDP descriptions to a well-known multicast address and port number (9875). A listening application constructs a guide of all advertised multicast sessions. SAP was published by the IETF as RFC 2974. Announcement interval The announcement interval is cooperatively modulated such that all SAP announcements in the multicast delivery scope, by default, consume 4000 bits per second. Regardless, the maximum announce interval is 300 seconds (5 minutes). Announcements automatically expire after 10 times the announcement interval or one hour, whichever is greater. Announcements may also be explicitly withdrawn by the original is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Session Description Protocol
The Session Description Protocol (SDP) is a format for describing multimedia communication sessions for the purposes of announcement and invitation. Its predominant use is in support of streaming media applications, such as voice over IP (VoIP) and video conferencing. SDP does not deliver any media streams itself but is used between endpoints for negotiation of network metrics, media types, and other associated properties. The set of properties and parameters is called a ''session profile''. SDP is extensible for the support of new media types and formats. SDP was originally a component of the Session Announcement Protocol (SAP), but found other uses in conjunction with the Real-time Transport Protocol (RTP), the Real-time Streaming Protocol (RTSP), Session Initiation Protocol (SIP), and as a standalone protocol for describing multicast sessions. The IETF published the original specification as a Proposed Standard in April 1998. Revised specifications were released in 2006 (RF ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast Address
A multicast address is a logical identifier for a group of hosts in a computer network that are available to process datagrams or frames intended to be multicast for a designated network service. Multicast addressing can be used in the link layer (layer 2 in the OSI model), such as Ethernet multicast, and at the internet layer (layer 3 for OSI) for Internet Protocol Version 4 (IPv4) or Version 6 (IPv6) multicast. IPv4 IPv4 multicast addresses are defined by the most-significant bit pattern of ''1110''. This originates from the classful network design of the early Internet when this group of addresses was designated as ''Class D''. The CIDR notation for this group is . The group includes the addresses from to . Address assignments from within this range are specified in , an Internet Engineering Task Force (IETF) ''Best Current Practice'' document (BCP 51). The address range is divided into blocks each assigned a specific purpose or behavior. ;Local subnetwork :Addresses in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Numbers
In computer networking, a port is a number assigned to uniquely identify a connection endpoint and to direct data to a specific service. At the software level, within an operating system, a port is a logical construct that identifies a specific process or a type of network service. A port is identified for each transport protocol and address combination by a 16-bit unsigned number, known as the port number. The most common transport protocols that use port numbers are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). A port number is always associated with an IP address of a host and the type of transport protocol used for communication. It completes the destination or origination network address of a message. Specific port numbers are reserved to identify specific services so that an arriving packet can be easily forwarded to a running application. For this purpose, port numbers lower than 1024 identify the historically most commonly used services a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asynchronous Layered Coding
Asynchronous Layered Coding (ALC) is an Internet protocol for content delivery in a reliable, massively scalable, multiple-rate, and congestion-controlled manner. Specified iRFC 5775 it is an IETF proposed standard. The protocol is specifically designed to provide massive scalability using IP multicast as the underlying network service. Massive scalability in this context means the number of concurrent receivers for an object is potentially in the millions, the aggregate size of objects to be delivered in a session ranges from hundreds of kilobytes to hundreds of gigabytes, each receiver can initiate reception of an object asynchronously, the reception rate of each receiver in the session is the maximum fair bandwidth available between that receiver and the sender, and all of this can be supported using a single sender. Because ALC is focused on reliable content delivery, the goal is to deliver objects as quickly as possible to each receiver while at the same time remaining net ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |