|
Middlebox
A middlebox is a computer networking device that transforms, inspects, filters, and manipulates traffic for purposes other than packet forwarding. Examples of middleboxes include firewalls, network address translators (NATs), load balancers, and deep packet inspection (DPI) devices. The term ''middlebox'' was coined in 1999 by UCLA computer science professor Lixia Zhang. Usage Middleboxes are widely deployed across both private and public networks. Dedicated middlebox hardware is widely deployed in enterprise networks to improve network security and performance; however, even home network routers often have integrated firewall, NAT, or other middlebox functionality. One 2017 study counted more than 1,000 deployments in autonomous systems, in both directions of traffic flows, and across a wide range networks, including mobile operators and data center networks. Examples The following are examples of commonly-deployed middleboxes: * Firewalls filter traffic based on a set o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol Ossification
Protocol ossification is the loss of flexibility, extensibility and evolvability of network protocols. This is largely due to middleboxes that are sensitive to the wire image (networking), wire image of the protocol, and which can interrupt or interfere with messages that are valid but which the middlebox does not correctly recognise. This is a violation of the end-to-end principle. Secondary causes include inflexibility in endpoint implementations of protocols. Ossification is a major issue in Internet protocol design and deployment, as it can prevent new protocols or extensions from being deployed on the Internet, or place strictures on the design of new protocols; new protocols may have to be encapsulation (networking), encapsulated in an already-deployed protocol or mimic the wire image of another protocol. Because of ossification, the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the only practical choices for transport protocols on the Internet, an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main communications protocol, protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliability (computer networking), reliable, ordered, and error detection and correction, error-checked delivery of a reliable byte stream, stream of octet (computing), octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the transport layer of the TCP/IP suite. Transport Layer Security, SSL/TLS often runs on top of TCP. TCP is Connection-oriented communication, connection-oriented, meaning that sender and receiver firstly need to establish a connection based on agreed parameters; they do this through three-way Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lixia Zhang
Lixia Zhang () is the Jonathan B. Postel Professor of Computer Science at the University of California, Los Angeles.. Her expertise is in computer networks; she helped found the Internet Engineering Task Force, designed the Resource Reservation Protocol, coined the term " middlebox", and pioneered the development of named data networking. Biography Zhang grew up in northern China, where she worked as a tractor driver on a farm when the Cultural Revolution closed the schools.. She earned a master's degree in electrical engineering in 1981 at California State University, Los Angeles, and completed her doctorate at the Massachusetts Institute of Technology in 1989, under the supervision of David D. Clark. After working as a researcher at Xerox PARC, she moved to UCLA in 1996. She and her husband, Jim Ma, have two sons. They reside in Sherman Oaks. Contributions Zhang was one of the 21 participants in the initial meeting of the Internet Engineering Task Force, in 1986, the only ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Address Translation
Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic Router (computing), routing device. The technique was initially used to bypass the need to assign a new address to every host when a network was moved, or when the upstream Internet service provider was replaced but could not route the network's address space. It is a popular and essential tool in conserving global address space in the face of IPv4 address exhaustion. One Internet-routable IP address of a NAT gateway can be used for an entire private network. As network address translation modifies the IP address information in packets, NAT implementations may vary in their specific behavior in various addressing cases and their effect on network traffic. Vendors of equipment containing NAT implementations do not commonly document the specifics of NAT behavior. History Internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AT&T
AT&T Inc., an abbreviation for its predecessor's former name, the American Telephone and Telegraph Company, is an American multinational telecommunications holding company headquartered at Whitacre Tower in Downtown Dallas, Texas. It is the world's List of telecommunications companies, third largest telecommunications company by revenue and the List of mobile network operators in the United States, third largest wireless carrier in the United States behind T-Mobile US, T-Mobile and Verizon. As of 2023, AT&T was ranked 32nd on the Fortune 500, ''Fortune'' 500 rankings of the largest United States corporations, with revenues of $122.4 billion. The modern company to bear the AT&T name began its history as the American District Telegraph Company, formed in St. Louis in 1878. After expanding services to Arkansas, Kansas, Oklahoma and Texas through a series of mergers, it became the Southwestern Bell Telephone Company in 1920. Southwestern Bell was a subsidiary of AT&T Corporation, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
T-Mobile US
T-Mobile US, Inc. is an American wireless network operator headquartered in Bellevue, Washington. Its majority shareholder and namesake is the German telecommunications company Deutsche Telekom. T-Mobile is the second largest wireless carrier in the United States, with 131 million subscribers as of March 31, 2025. The company was founded in 1994 by John W. Stanton of the Western Wireless Corporation as VoiceStream Wireless. Deutsche Telekom then gained plurality ownership in 2001 and renamed it after its global T-Mobile brand. , the German company holds a 51.4% stake in the company. T-Mobile US operates two main brands: T-Mobile and Metro by T-Mobile (acquired in a 2013 reverse takeover of MetroPCS that also led to T-Mobile's listing on the NASDAQ). In 2020, T-Mobile expanded through the acquisition of Sprint, which also made T-Mobile the operator of Assurance Wireless, a service subsidized by the federal Lifeline program. The company's growth continued in 2024 wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timeout (computing)
In telecommunications and related engineering (including computer networking and programming), the term timeout or time-out has several meanings, including: * A network parameter related to an enforced event designed to occur at the conclusion of a predetermined elapsed time. * A specified period of time that will be allowed to elapse in a system before a specified event is to take place, unless another specified event occurs first; in either case, the period is terminated when either event takes place. Note: A timeout condition can be canceled by the receipt of an appropriate time-out cancellation signal. * An event that occurs at the end of a predetermined period of time that began at the occurrence of another specified event. The timeout can be prevented by an appropriate signal. Timeouts allow for more efficient usage of limited resources without requiring additional interaction from the agent interested in the goods that cause the consumption of these resources. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Push Email
Push email is an email system that provides an always-on capability, in which when new email arrives at the mail delivery agent (MDA) (commonly called mail server), it is immediately, actively transferred ( pushed) by the MDA to the mail user agent (MUA), also called the email client, so that the end-user can see incoming email immediately. This is in contrast with systems that check for new incoming mail every so often, on a schedule. Email clients include smartphones and, less strictly, IMAP personal computer mail applications. Comparison with polling email Outgoing mail is generally ''pushed'' from the sender to the final mail delivery agent (and possibly via intermediate mail servers) using Simple Mail Transfer Protocol. If the receiver uses a polling email delivery protocol, the final step from the last mail delivery agent to the client is done using a poll. Post Office Protocol (POP3) is an example of a polling email delivery protocol. At login and later at intervals, t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
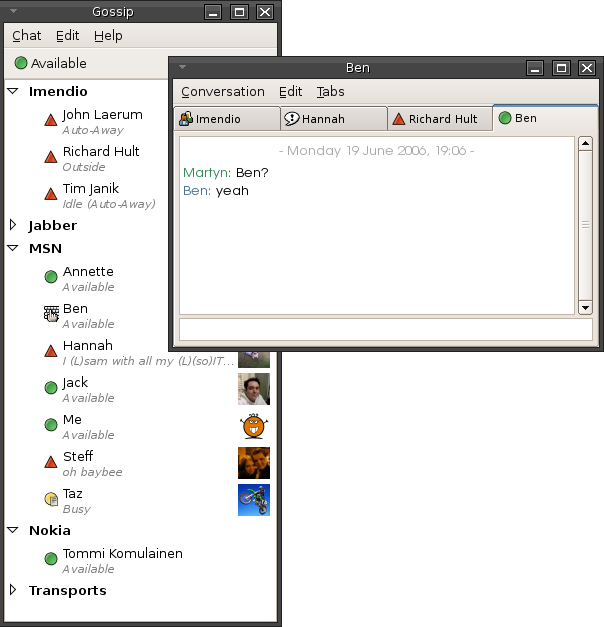
Instant Messaging
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involving simple text message exchanges, modern IM applications and services (also called "social messengers", "messaging apps", "chat apps" or "chat clients") tend to also feature the exchange of multimedia, emojis, file transfer, VoIP (voice calling), and video chat capabilities. Instant messaging systems facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list") or in chat rooms, and can be standalone apps or integrated into a wider social media platform, or in a website where it can, for instance, be used for conversational commerce. Originally the term "instant messaging" was distinguished from " text messaging" by being run on a computer network instead of a cellula ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |