|
Mevade Botnet
The Mevade Botnet, also known as Sefnit or SBC, is a massive botnet. Its operators are unknown and its motives seems to be multi-purpose. In late 2013 the Tor anonymity network saw a very sudden and significant increase in users, from 800,000 daily to more than 5,000,000. A botnet was suspected and fingers pointed at Mevade. Trend Micro reported that its Smart Protection Network saw a tor module being distributed to Mevade Trojans. See also * * |
|
|
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more Internet bot, bots. Botnets can be used to perform distributed denial-of-service attack, distributed denial-of-service (DDoS) attacks, steal data, send Spamming, spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "Computer network, network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose Computer security, security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Tor (anonymity Network)
Tor is a free overlay network for enabling anonymous communication. It is built on free and open-source software run by over seven thousand volunteer-operated relays worldwide, as well as by millions of users who route their Internet traffic via random paths through these relays. Using Tor makes it more difficult to trace a user's Internet activity by preventing any single point on the Internet (other than the user's device) from being able to view both where traffic originated from and where it is ultimately going to at the same time. This conceals a user's location and usage from anyone performing network surveillance or traffic analysis from any such point, protecting the user's freedom and ability to communicate confidentially. History The core principle of Tor, known as onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Trend Micro
is an American-Japanese cyber security software company. The company has globally dispersed R&D in 16 locations across every continent excluding Antarctica. The company develops enterprise security software for servers, containers, and cloud computing environments, networks, and end points. Its cloud and virtualization security products provide automated security for customers of VMware, Amazon AWS, Microsoft Azure, and Google Cloud Platform. Eva Chen is a co-founder, and chief executive officer since 2005. She succeeded founding CEO Steve Chang, who now is chairman. History 1988–1999 The company was founded in 1988 in Los Angeles by Steve Chang, his wife, Jenny Chang, and her sister, Eva Chen (陳怡樺). The company was established with proceeds from Steve Chang's previous sale of a copy protection dongle to a United States–based Rainbow Technologies. Shortly after establishing the company, its founders moved headquarters to Taipei. In 1992, Trend Micro took over a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Trojan Horse (computing)
In computing, a trojan horse (or simply trojan; often capitalized, but see below) is a kind of malware that misleads users as to its true intent by disguising itself as a normal program. Trojans are generally spread by some form of social engineering. For example, a user may be duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or into clicking on a fake advertisement on the Internet. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected device. Ransomware attacks are often carried out using a trojan. Unlike computer viruses and worms, trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Origins of the term The term is derived from the ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. It is unclear where and when the comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software (MS08-067 / CVE-2008-4250) and dictionary attacks on administrator passwords to propagate while forming a botnet, and has been unusually difficult to counter because of its combined use of many advanced malware techniques. The Conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm infection since the 2003 SQL Slammer worm. Despite its wide propagation, the worm did not do much damage, perhaps because its authors – believed to have been Ukrainian citizens – did not dare use it because of the attention it drew. Four men were arrested, and one pled guilty and was sentenced to four years in prison. Prevalence Estimates of the number of infected computers were difficult because ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Command And Control (malware)
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform distributed denial-of-service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, suc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Gameover ZeuS
GameOver ZeuS (GOZ), also known as peer-to-peer (P2P) ZeuS, ZeuS3, and GoZeus, is a Trojan horse (computing), Trojan horse developed by Russian cybercriminal Evgeniy Bogachev. Created in 2011 as a successor to Jabber Zeus, another project of Bogachev's, the malware is notorious for its usage in bank fraud resulting in damages of approximately $100 million and being the main vehicle through which the CryptoLocker ransomware attack was conducted, resulting in millions of dollars of losses. At the peak of its activity in 2012 and 2013, between 500,000 and 1 million computers were infected with GameOver ZeuS. The original GameOver ZeuS was propagated through spam emails containing links to websites that would download the malware onto the victim's computer. The Zombie (computer science), infected computer was then integrated into a botnet, considered to be one of the most sophisticated and secure botnets in the world at the time. The GOZ botnet was particularly notable for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Operation Tovar
Operation Tovar was an international collaborative operation carried out by law enforcement agencies from multiple countries against the Gameover ZeuS botnet, which was believed by the investigators to have been used in bank fraud and the distribution of the CryptoLocker ransomware. In early June 2014, the U.S. Department of Justice announced that Operation Tovar had temporarily succeeded in cutting communication between Gameover ZeuS and its command-and-control servers. The criminals attempted to send a copy of their database to a safe location, but it was intercepted by agencies already in control of part of the network. Results Russian Evgeniy Bogachev, aka "lucky12345" and "Slavik", was charged by the US FBI for being the ringleader of the gang behind Gameover Zeus and Cryptolocker. The database indicates the scale of the attack, and it makes decryption of CryptoLocked files possible. Restitution and victims In August 2014 security firms involved in the shutdown, Fox-IT an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
 |
Timeline Of Computer Viruses And Worms
This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events. 1960s * John von Neumann's article on the "Theory of self-reproducing automata" is published in 1966. The article is based on lectures given by von Neumann at the University of Illinois about the "Theory and Organization of Complicated Automata" in 1949. 1970s 1970 * The first story written about a computer virus, ''The Scarred Man'' by Gregory Benford, was published in the May 1970 issue of ''Venture Science Fiction''. 1971 * The Creeper system, an experimental self-replicating program, is written by Bob Thomas at BBN Technologies to test John von Neumann's theory. Creeper infected DEC PDP-10 computers running the TENEX operating system. Creeper gained access via the ARPANET and copied itself to the remote system where the message "I'm the creeper, catch me if you can!" was displa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
Tiny Banker Trojan
Tiny Banker Trojan, also called Tinba, is a malware program that targets financial institution websites. It is a modified form of an older form of viruses known as Banker Trojans, yet it is much smaller in size and more powerful. It works by establishing man-in-the-browser attacks and network sniffing. Since its discovery, it has been found to have infected more than two dozen major banking institutions in the United States, including TD Bank, Chase, HSBC, Wells Fargo, PNC, and Bank of America. It is designed to steal users' sensitive data, such as account login information and banking codes. History Tiny Banker was first discovered in 2012 when it was found to have infected thousands of computers in Turkey. After it was discovered, the original source code for the malware was leaked online and began undergoing individual revisions, making the process of detecting it harder for the institutions. It is a highly modified version of the Zeus Trojan, which had a very similar attack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Torpig
Torpig, also known as Anserin or Sinowal is a type of botnet spread through systems compromised by the Mebroot rootkit by a variety of trojan horses for the purpose of collecting sensitive personal and corporate data such as bank account and credit card information. It targets computers that use Microsoft Windows, recruiting a network of zombies for the botnet. Torpig circumvents antivirus software through the use of rootkit technology and scans the infected system for credentials, accounts and passwords as well as potentially allowing attackers full access to the computer. It is also purportedly capable of modifying data on the computer, and can perform man-in-the-browser attacks. By November 2008, it was estimated that Torpig had stolen the details of about 500,000 online bank accounts and credit and debit cards and was described as "one of the most advanced pieces of crimeware ever created". History Torpig reportedly began development in 2005, evolving from that point to more ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
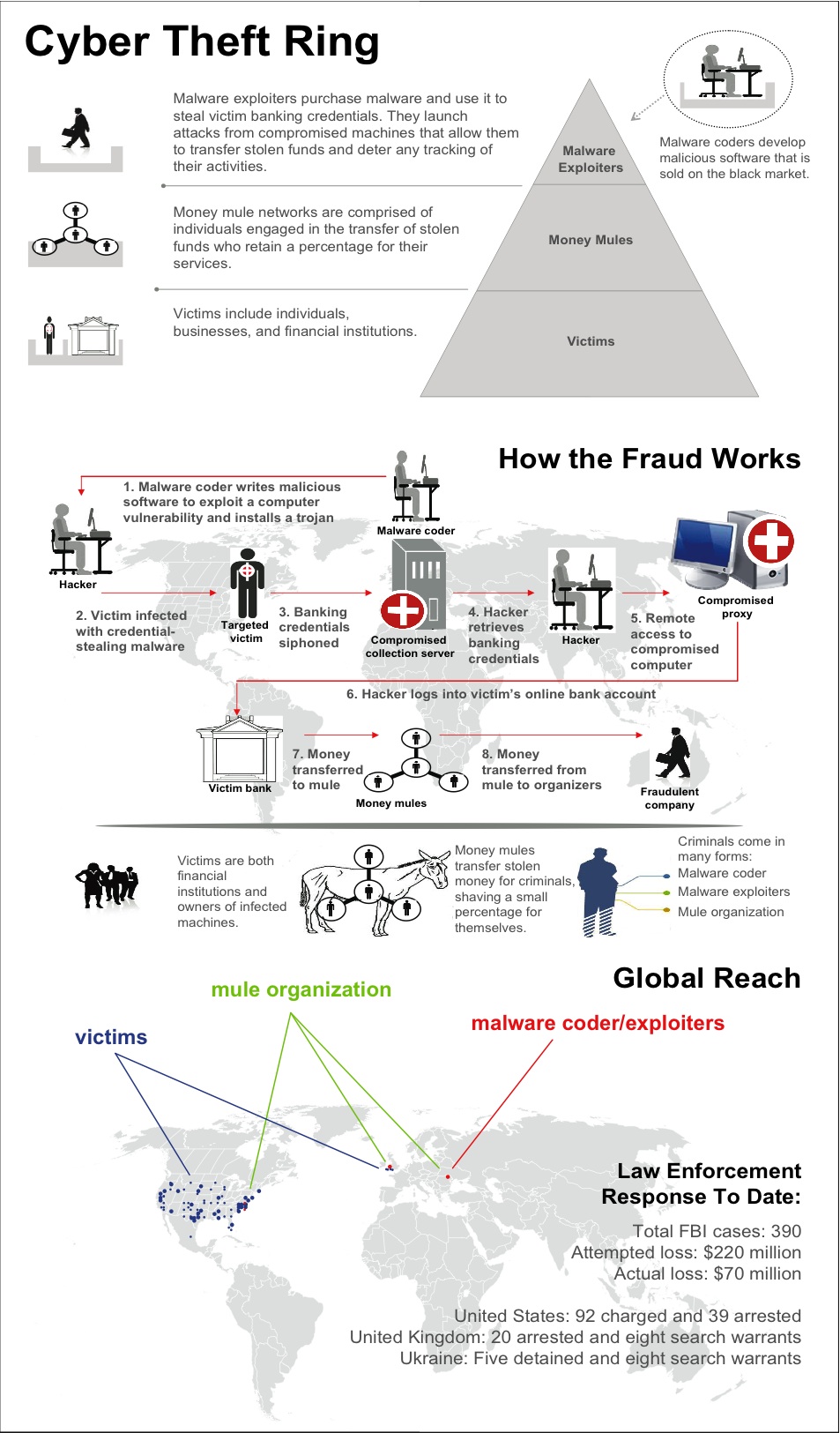 |
Zeus (malware)
Zeus is a Trojan horse (computing), Trojan horse malware package that runs on versions of Microsoft Windows. It is often used to steal Banking, banking information by man-in-the-browser keystroke logging and form grabbing. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 File Transfer Protocol, FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, American Broadcasting Company, ABC, Oracle Database, Oracle, Play.com, Cisco Systems, Cisco, Amazon.com, Amazon, and ''BusinessWeek''. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the Scam artist, scam artists money through pop-up messages that claim the user has a Computer virus, v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |