|
Loren Kohnfelder
Loren Kohnfelder is a computer scientist working in public key cryptography. Work Kohnfelder invented what is today called public key infrastructure (PKI) in his May 1978 MIT S.B. (BSCSE) thesis, which described a practical means of using public key cryptography to secure network communications. The Kohnfelder thesis introduced the terms "certificate" and "certificate revocation list" as well as numerous other concepts now established as important parts of PKI. The X.509 certificate specification that provides the basis for SSL, S/MIME and most modern PKI implementations are based Kohnfelder's thesis. He was also the co-creator, with Praerit Garg, of the STRIDE model of security threats, widely used in threat modeling. In 2021 he published the book ''Designing Secure Software'' with No Starch Press No Starch Press is an American publishing company, specializing in technical literature often geared towards the geek, hacker, and DIY subcultures. Popular titles include '' Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, information, and automation. Computer science spans Theoretical computer science, theoretical disciplines (such as algorithms, theory of computation, and information theory) to Applied science, applied disciplines (including the design and implementation of Computer architecture, hardware and Software engineering, software). Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of computational problem, problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and preventing security vulnerabilities. Computer graphics (computer science), Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), SSH, S/MIME, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a Key authentication, public key. The certificate includes the public key and information about it, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the device examining the certificate trusts the issuer and finds the signature to be a valid signature of that issuer, then it can use the included public key to communicate securely with the certificate's subject. In email encryption, code signing, and Electronic signature, e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core rol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
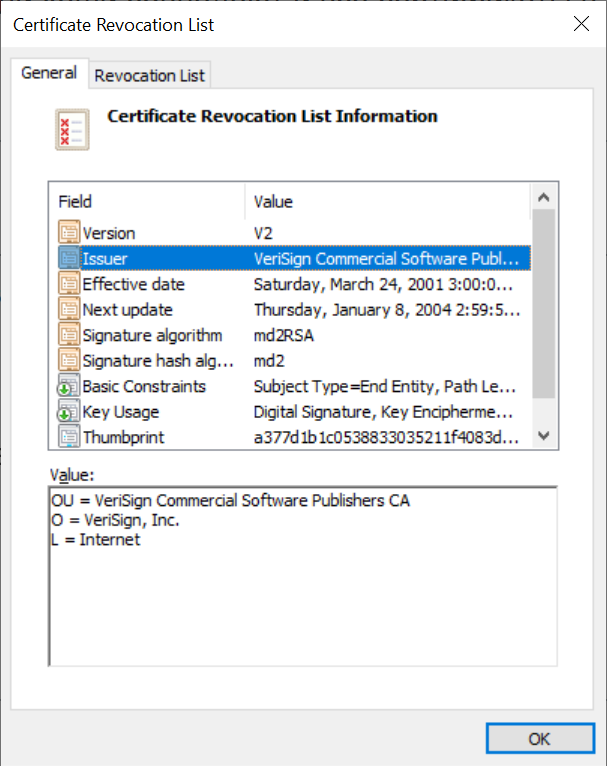
Certificate Revocation List
In cryptography, a certificate revocation list (CRL) is "a list of digital certificates that have been revoked by the issuing certificate authority (CA) before their scheduled expiration date and should no longer be trusted". Publicly trusted CAs in the Web PKI are required (including by the CA/Browser forum) to issue CRLs for their certificates, and they widely do. Browsers and other relying parties might use CRLs, or might use alternate certificate revocation technologies (such as Online Certificate Status Protocol, OCSP) or CRLSets (a dataset derived from CRLs) to check certificate revocation status. Note that OCSP is falling out of favor due to privacy and performance concerns. Subscribers and other parties can also use ARI. Revocation states There are two different states of revocation defined in RFC 5280: ; Revoked: A certificate is irreversibly revoked if, for example, it is discovered that the certificate authority (CA) had improperly issued a certificate, or if a pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Royal Holloway
Royal Holloway, University of London (RH), formally incorporated as Royal Holloway and Bedford New College, is a public university, public research university and a constituent college, member institution of the federal University of London. It has six schools, 21 academic departments and approximately 10,500 undergraduate and postgraduate students from more than 100 countries. The campus is located west of Egham, Surrey, from central London. The Egham campus was founded in 1879 by the Victorian entrepreneur and philanthropist Thomas Holloway. Royal Holloway College was officially opened in 1886 by Queen Victoria as an Single-sex education, all-women college. It became a member of the University of London in 1900. In 1945, the college admitted male postgraduate students, and in 1965, around 100 of the first male undergraduates. In 1985, Royal Holloway merged with Bedford College (London), Bedford College (another former all-women's college in London). The merged college was nam ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of London
The University of London (UoL; abbreviated as Lond or more rarely Londin in Post-nominal letters, post-nominals) is a collegiate university, federal Public university, public research university located in London, England, United Kingdom. The university was established by royal charter in 1836 as a degree-awarding examination board for students holding certificates from University College London, King's College London and "other such institutions, corporate or unincorporated, as shall be established for the purpose of Education, whether within the Metropolis or elsewhere within our United Kingdom". It is one of three institutions to have claimed the title of the Third-oldest university in England debate, third-oldest university in England. It moved to a federal structure with constituent colleges in 1900. It is now incorporated by its fourth (1863) royal charter and governed by the University of London Act 2018 (c. iii). The university consists of Member institutions of the Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Sockets Layer
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol that provides security to datagram-based applications. In technical writing, references to "(D)TLS" are often seen when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first def ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for public-key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly . It was originally developed by RSA Data Security, and the original specification used the IETF MIME specification with the de facto industry standard PKCS #7 secure message format. Change control to S/MIME has since been vested in the IETF, and the specification is now layered on Cryptographic Message Syntax (CMS), an IETF specification that is identical in most respects with PKCS #7. S/MIME functionality is built into the majority of modern email software and interoperates between them. Since it is built on CMS, MIME can also hold an advanced digital signature. Function S/MIME provides the following cryptographic security services for electronic messaging applications: * Authentication * Message integrity * Non-repudiation of origin (using digital signa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simson L
Simson may refer to: * Simson (name) * Simson (artist) Music Producer based out of Milwaukee, Wisconsin. * Simson (company), a German company that produced firearms, automobiles, motorcycles, and mopeds * Simson line in geometry, named for Robert Simson * Simson Provincial Park in Canada * KSV Simson Bremen, German football club See also * Samson (other) Samson is a Biblical figure known for his exceptional strength. Samson may also refer to: Arts and entertainment Fictional characters Film and television * Samson Clogmeyer, from the Cartoon Network series ''Camp Lazlo'' * Brock Samson, from the ... * Simpson (other) {{disambiguation, geo, math ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
STRIDE (security)
STRIDE is a model for identifying computer security threats developed by Praerit Garg and Loren Kohnfelder at Microsoft. It provides a mnemonic for security threats in six categories. The threats are: * Spoofing * Tampering * Repudiation * Information disclosure ( privacy breach or data leak) * Denial of service * Elevation of privilege The STRIDE was initially created as part of the process of threat modeling. STRIDE is a model of threats, used to help reason and find threats to a system. It is used in conjunction with a model of the target system that can be constructed in parallel. This includes a full breakdown of processes, data stores, data flows, and trust boundaries. Today it is often used by security experts to help answer the question "what can go wrong in this system we're working on?" Each threat is a violation of a desirable property for a system: Notes on the threats Repudiation is unusual because it's a threat when viewed from a security perspect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
No Starch Press
No Starch Press is an American publishing company, specializing in technical literature often geared towards the geek, hacker, and DIY subcultures. Popular titles include '' Hacking: The Art of Exploitation'', Andrew Huang's ''Hacking the Xbox'', and '' How Wikipedia Works''. Topics No Starch Press publishes books with a focus on networking, computer security, hacking, Linux, programming, technology for kids, Lego, math, and science. The publisher also releases educational comics like ''Super Scratch Programming Adventure'' and ''The Manga Guide to Science'' series. History No Starch Press was founded in 1994 by Bill Pollock. It is headquartered in San Francisco. The company has published titles that have received recognition in the Communication Arts Design Annual and STEP inside 100 competition, and have been awarded the Independent Publisher Book Award (the IPPYs) from Independent Publisher magazine. Availability No Starch Press titles are available online and in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |