|
Legal Instrument
Legal instrument is a law, legal term of art that is used for any formally executed written document that can be formally attributed to its author, records and formally expresses a legally enforceable act, process, or contractual duty, obligation, or right, and therefore evidences that act, process, or agreement.''Barron's Law Dictionary'', s.v. "instrument". Examples include a wikt:certificate, certificate, deed, Bond (finance), bond, contract, will (law), will, legislative act, Act (document), notarial act, court writ or process, or any law passed by a competent legislative body in domestic or international law. Many legal instruments were written Seal (contract law), ''under seal'' by affixing a wax or paper Seal (emblem), seal to the document in evidence of its legal execution and Authentication, authenticity (which often removed the need for consideration in contract law). However, today many jurisdictions have done away with the requirement of documents being under seal in or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Term Of Art
Jargon, or technical language, is the specialized terminology associated with a particular field or area of activity. Jargon is normally employed in a particular communicative context and may not be well understood outside that context. The context is usually a particular occupation (that is, a certain trade, profession, vernacular or academic field), but any ingroup can have jargon. The key characteristic that distinguishes jargon from the rest of a language is its specialized vocabulary, which includes terms and definitions of words that are unique to the context, and terms used in a narrower and more exact sense than when used in colloquial language. This can lead outgroups to misunderstand communication attempts. Jargon is sometimes understood as a form of technical slang and then distinguished from the official terminology used in a particular field of activity. The terms ''jargon'', ''slang,'' and '' argot'' are not consistently differentiated in the literature; differen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seal (emblem)
A seal is a device for making an impression in Sealing wax, wax, clay, paper, or some other medium, including an Paper embossing, embossment on paper, and is also the impression thus made. The original purpose was to authenticate a document, or to prevent interference with a package or envelope by applying a seal which had to be broken to open the container (hence the modern English verb "to seal", which implies secure closing without an actual wax seal). The seal-making device is also referred to as the seal ''matrix'' or ''die''; the imprint it creates as the seal impression (or, more rarely, the ''sealing''). If the impression is made purely as a relief resulting from the greater pressure on the paper where the high parts of the matrix touch, the seal is known as a ''dry seal''; in other cases ink or another liquid or liquefied medium is used, in another color than the paper. In most traditional forms of dry seal the design on the seal matrix is in Intaglio (sculpture), intag ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Legal Coding
Legal coding is the process of creating summary or keyword data from a document. It is widely used in the legal profession to create a fast-search index or database of documents for use in litigation. Objective Coding Definitions * The recording of basic data such as date, author, or document type, from documents into a database. * Extracting information from electronic documents such as date created, author recipient, CC and linking each image to the information in pre-defined objective fields. In direct opposition to Subjective Coding where legal interpretations of data in a document are linked to individual documents. Also called bibliographic coding. * Extracting such information from a document as its author, its mailing date, etc. Objective coding is usually done from the document text or image, because the metadata Metadata (or metainformation) is "data that provides information about other data", but not the content of the data itself, such as the text of a message ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm In mathematics and computer science, an algorithm () is a finite sequence of Rigour#Mathematics, mathematically rigorous instructions, typically used to solve a class of specific Computational problem, problems or to perform a computation. Algo ..., can Encryption, encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key's security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the pra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Message Digest
A hash function is any function that can be used to map data of arbitrary size to fixed-size values, though there are some hash functions that support variable-length output. The values returned by a hash function are called ''hash values'', ''hash codes'', (''hash/message'') ''digests'', or simply ''hashes''. The values are usually used to index a fixed-size table called a ''hash table''. Use of a hash function to index a hash table is called ''hashing'' or ''scatter-storage addressing''. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is a computationally- and storage-space-efficient form of data access that avoids the non-constant access time of ordered and unordered lists and structured trees, and the often-exponentia ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Signatures In Global And National Commerce Act
The Electronic Signatures in Global and National Commerce Act (ESIGN, , ) is a United States federal law, passed by the U.S. Congress to facilitate the use of electronic records and electronic signatures in interstate and foreign commerce. This is done by ensuring the validity and legal effect of contracts entered into electronically; the Act was signed into law by President Bill Clinton on June 30, 2000, and took effect on October 1, 2000. Although every state has at least one law pertaining to electronic signatures, it is the federal law that lays out the guidelines for interstate commerce. The general intent of the ESIGN Act is spelled out in the first section (101.a), that a contract or signature “may not be denied legal effect, validity, or enforceability solely because it is in electronic form”. This simple statement provides that electronic signatures and records are just as good as their paper equivalents, and therefore subject to the same legal scrutiny of authe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
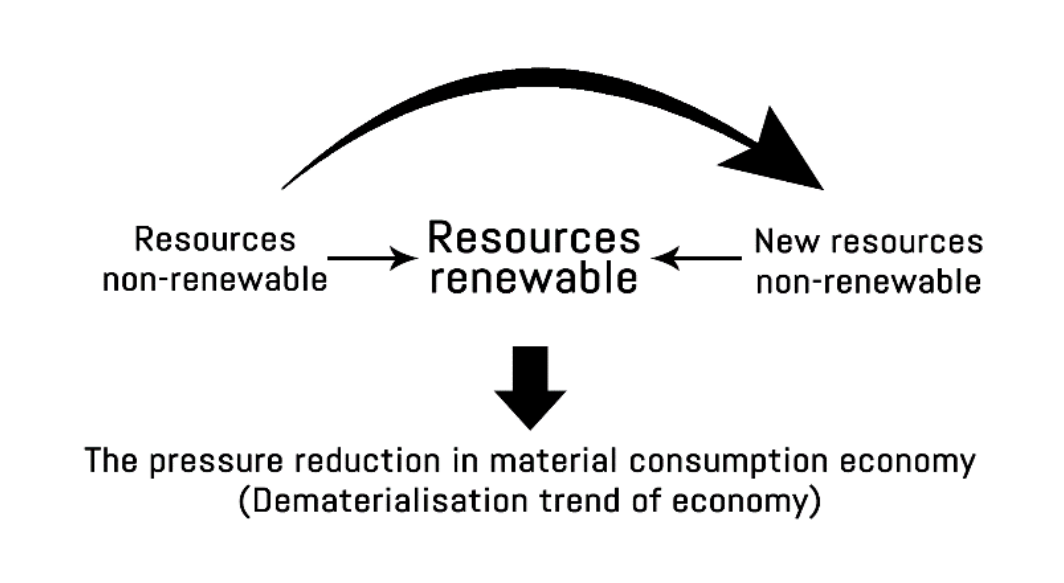
Dematerialization (economics)
Dematerialization is a term in economics and the social sciences that describes the process of making more goods with less material. The term itself possesses multi-accentuality, which allows it to be diversely explained by different fields of social science, such as Mainstream economics, which puts focus on the aspects of technological evolution and market demand shifts, and Ecological economics, which emphasizes the effect of dematerialization on the natural environment. In economics, dematerialization refers to the absolute or relative reduction in the quantity of materials required to serve economic functions in society. In common terms, dematerialization means doing more with less. This concept is similar to ephemeralization as proposed by Buckminster Fuller. Origin Dematerialization is a phenomenon occurs simultaneously with technological advancement, especially in the Digital Revolution, Third Industrial revolution products. Miniaturization and optimization of products ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Consideration
Consideration is a concept of English law, English common law and is a necessity for simple contracts but not for special contracts (contracts by deed). The concept has been adopted by other common law jurisdictions. It is commonly referred to as one of the six or seven elements of a contract. The court in ''Currie v Misa'' declared consideration to be a "Right, Interest, Profit, Benefit, or Forbearance, Detriment, Loss, Responsibility". Thus, consideration is a promise of something of value given by a promissor in exchange for something of value given by a promisee; and typically the thing of value is goods, money, or an act. Forbearance to act, such as an adult promising to refrain from smoking, is enforceable if one is thereby surrendering a legal right. Consideration may be thought of as the concept of value offered and accepted by people or organisations entering into contracts. Anything of value promised by one party to the other when making a contract can be treate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |