|
Keycloak
Keycloak is an open-source software product to allow single sign-on with identity and access management aimed at modern applications and services. Until April 2023, this WildFly community project was under the stewardship of Red Hat, who use it as the upstream project for their Red Hat build of Keycloak. In April 2023, Keycloak was donated to the CNCF and joined the foundation as an incubating project. Keycloak supports various protocols such as OpenID, OAuth version 2.0 and SAML and provides features such as user management, two-factor authentication, permissions and roles management, creating token services, etc. It is possible to integrate Keycloak with other technologies, such as front-end frameworks like React or Angular, as well as containerization solutions like Docker. History The first production release of Keycloak was in September 2014, with development having started about a year earlier. In 2016, Red Hat switched the RH SSO product from being based on the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Hat
Red Hat, Inc. (formerly Red Hat Software, Inc.) is an American software company that provides open source software products to enterprises and is a subsidiary of IBM. Founded in 1993, Red Hat has its corporate headquarters in Raleigh, North Carolina, with other offices worldwide. Red Hat has become associated to a large extent with its enterprise operating system Red Hat Enterprise Linux. With the acquisition of open-source enterprise middleware vendor JBoss, Red Hat also offers Red Hat Virtualization (RHV), an enterprise virtualization product. Red Hat provides storage, operating system platforms, middleware, applications, management products, support, training, and consulting services. Red Hat creates, maintains, and contributes to many free software projects. It has acquired the codebases of several proprietary software products through corporate mergers and acquisitions, and has released such software under open source licenses. , Red Hat is the second largest co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Native Computing Foundation
The Cloud Native Computing Foundation (CNCF) is a subsidiary of the Linux Foundation founded in 2015 to support cloud-native computing. History It was announced alongside Kubernetes 1.0, an open source container cluster manager, which was contributed to the Linux Foundation by Google as a seed technology. Founding members include Google, CoreOS, Mesosphere, Red Hat, Twitter, Huawei, Intel, RX-M, Cisco, IBM, Docker, Univa, and VMware. Today, CNCF is supported by over 450 members. In August 2018 Google announced that it was handing over operational control of Kubernetes to the community. Projects * ArgoArgois a collection of tools for getting work done with Kubernetes. Among its main features are Workflows and Events. It was accepted to CNCF on March 26, 2020 at the Incubating maturity level and then moved to the Graduated maturity level on December 6, 2022. * Cilium: Cilium provides networking, security, and observability for Kubernetes deployments using eBPF technology. I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Single Sign-on Implementations
These are some of the notable Single Sign-On (SSO) implementations available: {, class="wikitable sortable" style="text-align: center;" ! Product Name ! Project/Vendor ! License ! Identity management platform ! Description , - , Accounts & SSO , , Nokia, Intel,… , , Free software , , , , Client-side implementation with plugins for various services/protocols , - , Active Directory Federation Services, , Microsoft, , Proprietary, , , , Claims-based system and application federation using SAML 2.0 or WS-Federation , - , , Bitium, , Bitium, , Proprietary, , , , Enterprise cloud-based identity and access management solution with single sign-on, active directory integration and 2-factor authentication options , - , CAS / Central Authentication Service, , Apereo, , Free & Open Source ( Apache 2.0) , , , Protocol and open-source SSO server/client implementation with support for CAS, SAML1, SAML2, OAuth2, SCIM, OpenID Connect and WS-Fed protocols both as an identity provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
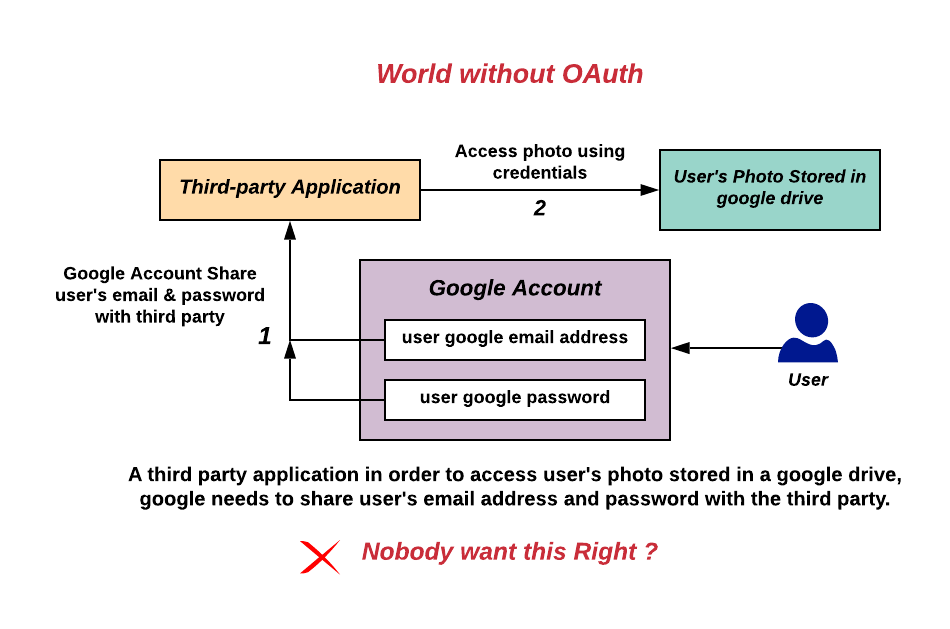
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java Enterprise Platform
Java is one of the Greater Sunda Islands in Indonesia. It is bordered by the Indian Ocean to the south and the Java Sea (a part of Pacific Ocean) to the north. With a population of 156.9 million people (including Madura) in mid 2024, projected to rise to 158 million at mid 2025, Java is the world's most populous island, home to approximately 55.7% of the Indonesian population (only approximately 44.3% of Indonesian population live outside Java). Indonesia's capital city, Jakarta, is on Java's northwestern coast. Many of the best known events in Indonesian history took place on Java. It was the centre of powerful Hindu-Buddhist empires, the Islamic sultanates, and the core of the colonial Dutch East Indies. Java was also the center of the Indonesian struggle for independence during the 1930s and 1940s. Java dominates Indonesia politically, economically and culturally. Four of Indonesia's eight UNESCO world heritage sites are located in Java: Ujung Kulon National Par ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Software
Computer security software or cybersecurity software is any computer program designed to influence information security. This is often taken in the context of defending computer systems or data, yet can incorporate programs designed specifically for subverting computer systems due to their significant overlap, and the adage that the best defense is a good offense. The defense of computers against intrusion and unauthorized use of resources is called ''computer security''. Similarly, the defense of computer networks is called '' network security''. The subversion of computers or their unauthorized use is referred to using the terms ''cyberwarfare'', ''cybercrime'', or '' security hacking'' (later shortened to ''hacking'' for further references in this article due to issues with ''hacker'', ''hacker culture'' and differences in white/grey/black 'hat' color identification). The computer security software products industry was launched in the second half of the 1970s when computer f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenAM
OpenAM is an open-source access management, entitlements and federation server platform. Now it is supported by Open Identity Platform Community. OpenAM (Open Access Management) originated as OpenSSO, (Open Single Sign-On) an access management system created by Sun Microsystems and now owned by Oracle Corporation. OpenAM is a fork which was initiated following Oracle's purchase of Sun. History Announced by Sun Microsystems in July 2005, OpenSSO was based on Sun Java System Access Manager, and was the core of Sun's commercial access management and federation product, OpenSSO Enterprise (formerly Sun Access Manager and Sun Federation Manager). In July 2008, Sun announced paid support for regular "Express" builds of OpenSSO. Sun's stated intent was that express builds would be released approximately every three months, allowing customers early access to new features. In September 2008, Sun announced OpenSSO Enterprise 8.0, the first commercial product derived from the OpenSSO ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wildfly
WildFly, formerly known as JBoss AS, or simply JBoss, is an application server written by JBoss, now developed by Red Hat. WildFly is written in Java and implements the Java Platform, Enterprise Edition (Java EE) specification. It runs on multiple platforms. WildFly is free and open-source software, subject to the requirements of the GNU Lesser General Public License (LGPL), version 2.1. Origin In 1999, Marc Fleury started a free software project named ''EJB-OSS'' (stands for ''Enterprise Java Bean Open Source Software'') implementing the EJB API from J2EE (Java 2 Enterprise Edition). Sun Microsystems asked the project to stop using the trademarked ''EJB'' within its name. ''EJB-OSS'' was then renamed to ''JBOSS'', then ''JBoss'' later. On November 20, 2014, JBoss Application Server was renamed WildFly. The JBoss Community and other Red Hat JBoss products like JBoss Enterprise Application Platform were not renamed. Features Wildfly supports a number of features: * Jaka ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Token Service
Security token service (STS) is a cross-platform open standard core component of the OASIS group's WS-Trust web services single sign-on infrastructure framework specification.. Within that claims-based identity framework, a secure token service is responsible for issuing, validating, renewing and cancelling security tokens. The tokens issued by security token services can then be used to identify the holder of the token to services that adhere to the WS-Trust standard. Security token service provides the same functionality as OpenID, but unlike OpenID is not patent encumbered. Together with the rest of the WS-Trust standard, the security token service specification was initially developed by employees of IBM, Microsoft, Nortel and VeriSign. In a typical usage scenario involving a web service that employs WS-Trust, when a client requests access to an application, the application does not authenticate the client directly (for instance, by validating the client's login credential ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Two-factor Authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or Application software, application only after successfully presenting two or more distinct types of evidence (or Authentication#Authentication factors, factors) to an authentication mechanism. MFA protects personal data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password. Usage of MFA has increased in recent years. Security issues which can cause the bypass of MFA are #Fatigue attack, fatigue attacks, phishing and SIM swap scam, SIM swapping. Accounts with MFA enabled are significantly less likely to be compromised. Authentication factors Authentication takes place when someone tries to log into a computer resource (such as a computer network, device, or application). The resource requires ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SAML
Security Assertion Markup Language (SAML, pronounced ''SAM-el'', ) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider (SAML), identity provider and a service provider (SAML), service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions). SAML is also: * A set of XML-based protocol messages * A set of protocol message bindings * A set of profiles (utilizing all of the above) An important use case that SAML addresses is web browser, web-browser single sign-on (SSO). Single sign-on is relatively easy to accomplish within a security domain (using HTTP cookie, cookies, for example) but extending SSO across security domains is more difficult and resulted in the proliferation of non-interoperable proprietary technologies. The SAML Web Browser SSO profile was specified and standardized to promote interoperability.J.&nb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |