 |
Kernel Panic
A kernel panic (sometimes abbreviated as KP) is a safety measure taken by an operating system's Kernel (operating system), kernel upon detecting an internal Fatal system error, fatal error in which either it is unable to safely recover or continuing to run the system would have a higher risk of major data loss. The term is largely specific to Unix and Unix-like systems. The equivalent on Microsoft Windows operating systems is a Blue screen of death, stop error, often called a "blue screen of death". The Kernel (operating system), kernel routines that handle panics, known as panic() in AT&T Corporation, AT&T-derived and Berkeley Software Distribution, BSD Unix source code, are generally designed to output an error message to the system console, console, dump an image of kernel memory to disk for post-mortem debugging, and then either wait for the system to be manually rebooted, or initiate an automatic reboot. The information provided is of a highly technical nature and aims t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
 |
Ubuntu 4
Ubuntu ( ) is a Linux distribution based on Debian and composed primarily of free and open-source software. Developed by the British company Canonical (company), Canonical and a community of contributors under a Meritocracy, meritocratic governance model, Ubuntu is released in multiple official editions: ''Desktop computer, Desktop'', ''Server (computing), Server'', and ''Core'' for Internet of things, IoT and robotic devices. Ubuntu is published on a six-month release cycle, with long-term support (LTS) versions issued every two years. Canonical provides security updates and support until each release reaches its designated end-of-life (product), end-of-life (EOL), with optional extended support available through the Ubuntu Pro and Expanded Security Maintenance (ESM) services. , the latest stable release is Ubuntu version history#Ubuntu 25.04 (Plucky Puffin), 25.04 ("Plucky Puffin"), and the current LTS release is Ubuntu version history#Ubuntu 24.04 LTS (Noble Numbat), 24.04 ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
 |
System Administrator
An IT administrator, system administrator, sysadmin, or admin is a person who is responsible for the upkeep, configuration, and reliable operation of computer systems, especially multi-user computers, such as Server (computing), servers. The system administrator seeks to ensure that the uptime, Computer performance, performance, System resource, resources, and Computer security, security of the computers they manage meet the needs of the User (computing), users, without exceeding a set budget when doing so. To meet these needs, a system administrator may acquire, install, or upgrade computer components and software; provide routine automation; maintain security policies; troubleshoot; train or supervise staff; or offer technical support for projects. Related fields Many organizations staff offer jobs related to system administration. In a larger company, these may all be separate positions within a computer support or Information Services (IS) department. In a smaller group ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
 |
Software Bug
A software bug is a design defect ( bug) in computer software. A computer program with many or serious bugs may be described as ''buggy''. The effects of a software bug range from minor (such as a misspelled word in the user interface) to severe (such as frequent crashing). In 2002, a study commissioned by the US Department of Commerce's National Institute of Standards and Technology concluded that "software bugs, or errors, are so prevalent and so detrimental that they cost the US economy an estimated $59 billion annually, or about 0.6 percent of the gross domestic product". Since the 1950s, some computer systems have been designed to detect or auto-correct various software errors during operations. History Terminology ''Mistake metamorphism'' (from Greek ''meta'' = "change", ''morph'' = "form") refers to the evolution of a defect in the final stage of software deployment. Transformation of a ''mistake'' committed by an analyst in the early stages of the softw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
Codebase
In software development, a codebase (or code base) is a collection of source code used to build a particular software system, application, or software component. Typically, a codebase includes only human-written source code system files; thus, a codebase usually does not include source code files generated by tools (generated files) or binary library files (object files), as they can be built from the human-written source code. However, it generally does include configuration and property files, as they are the data necessary for the build. A codebase is typically stored in a source control repository in a version control system. A source code repository is a place where large amounts of source code are kept, either publicly or privately. Source code repositories are used most basically for backups and versioning, and on multi-developer projects to handle various source code versions and to provide aid in resolving conflicts that arise from developers submitting overlapping ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
 |
Dennis Ritchie
Dennis MacAlistair Ritchie (September 9, 1941 – October 12, 2011) was an American computer scientist. He created the C programming language and the Unix operating system and B language with long-time colleague Ken Thompson. Ritchie and Thompson were awarded the Turing Award from the Association for Computing Machinery (ACM) in 1983, the IEEE Richard W. Hamming Medal from the Institute of Electrical and Electronics Engineers (IEEE) in 1990, and the National Medal of Technology from President Bill Clinton in 1999. Ritchie was the head of Lucent Technologies System Software Research Department when he retired in 2007. Early life and education Dennis Ritchie was born in Bronxville, New York. His father was Alistair E. Ritchie, a longtime Bell Labs scientist and co-author of ''The Design of Switching Circuits'' on switching circuit theory. As a child, Dennis moved with his family to Summit, New Jersey, where he graduated from Summit High School. He graduated from Harvard Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
Tom Van Vleck
Tom Van Vleck is an American computer software engineer. Life and work Van Vleck graduated from MIT in 1965 with a BS in Mathematics. He worked on CTSS at MIT, and co-authored its first email program with Noel Morris. In 1965, he joined Project MAC, the predecessor of the MIT Computer Science and Artificial Intelligence Laboratory.''A Marriage of Convenience: THE FOUNDING OF THE MIT ARTIFICIAL INTELLIGENCE LABORATORY'' Chiou, Stefanie; et al. (2001) He worked on the development of for more than 16 years at and at [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Multics
Multics ("MULTiplexed Information and Computing Service") is an influential early time-sharing operating system based on the concept of a single-level memory.Dennis M. Ritchie, "The Evolution of the Unix Time-sharing System", Communications of the ACM, Vol. 17, 1984, pp. 365-375. It has been written that Multics "has influenced all modern operating systems since, from microcomputers to mainframes." Initial planning and development for Multics started in 1964, in Cambridge, Massachusetts. Originally it was a cooperative project led by MIT ( Project MAC with Fernando Corbató) along with General Electric and Bell Labs. It was developed on the GE 645 computer, which was specially designed for it; the first one was delivered to MIT in January 1967. GE offered their earlier 635 systems with the Dartmouth Time-Sharing System which they called "Mark I" and intended to offer the 645 with Multics as a larger successor. Bell withdrew from the project in 1969 as it became clear it would ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
 |
Fault Detection And Isolation
Fault detection, isolation, and recovery (FDIR) is a subfield of control engineering which concerns itself with monitoring a system, identifying when a Fault (technology), fault has occurred, and pinpointing the type of fault and its location. Two approaches can be distinguished: A direct pattern recognition of sensor readings that indicate a fault and an analysis of the discrepancy between the sensor readings and expected values, derived from some model. In the latter case, it is typical that a fault is said to be detected if the discrepancy or ''residual'' goes above a certain threshold. It is then the task of fault isolation to categorize the type of fault and its location in the machinery. Fault detection and isolation (FDI) techniques can be broadly classified into two categories. These include model-based FDI and signal processing based FDI. Model-based FDI In model-based FDI techniques some model of the system is used to decide about the occurrence of fault. The sys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
Assertion (software Development)
In computer programming, specifically when using the imperative programming paradigm, an assertion is a predicate (a Boolean-valued function over the state space, usually expressed as a logical proposition using the variables of a program) connected to a point in the program, that always should evaluate to true at that point in code execution. Assertions can help a programmer read the code, help a compiler compile it, or help the program detect its own defects. For the latter, some programs check assertions by actually evaluating the predicate as they run. Then, if it is not in fact true – an assertion failure – the program considers itself to be broken and typically deliberately crashes or throws an assertion failure exception. Details The following code contains two assertions, x > 0 and x > 1, and they are indeed true at the indicated points during execution: x = 1; assert x > 0; x++; assert x > 1; Programmers can use assertions to help specify programs and to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
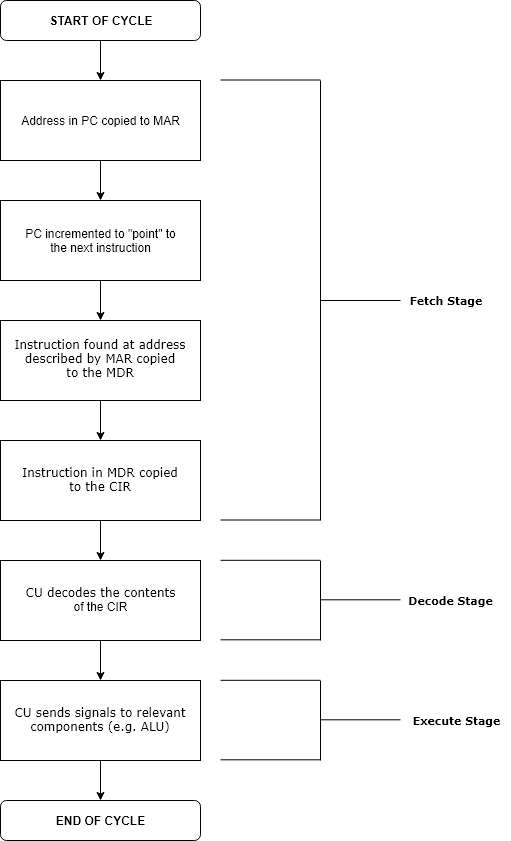 |
Runtime (program Lifecycle Phase)
Execution in computer engineering, computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a "Instruction cycle, fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the Formal semantics of programming languages, semantics of those instructions. Programs for a computer may be executed in a Batch processing, batch process without human interaction or a User (computing), user may type Command (computing), commands in an Session (computer science), interactive session of an Interpreter (computing), interpreter. In this case, the "commands" are simply program instructions, whose executio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
User Space And Kernel Space
A modern computer operating system usually uses virtual memory to provide separate address spaces or regions of a single address space, called user space and kernel space. This separation primarily provides memory protection and hardware protection from malicious or errant software behaviour. Kernel space is strictly reserved for running a privileged operating system kernel, kernel extensions, and most device drivers. In contrast, user space is the memory area where application software and some drivers execute, typically with one address space per process. Overview The term user space (or userland) refers to all code that runs outside the operating system's kernel. User space usually refers to the various programs and libraries that the operating system uses to interact with the kernel: software that performs input/output, manipulates file system objects, application software, etc. Each user space process usually runs in its own virtual memory space, and, unless explicitl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |