|
JSONP
JSONP, or JSON-P (JSON with Padding), is a historical JavaScript technique for requesting data by loading a element, which is an element intended to load ordinary JavaScript. It was proposed by Bob Ippolito in 2005. JSONP enables sharing of data bypassing same-origin policy, which disallows running JavaScript code to read media DOM elements or XMLHttpRequest data fetched from outside the page's originating site. The originating site is indicated by a combination of URI scheme, hostname, and port number. JSONP is vulnerable to the data source replacing the innocuous function call with malicious code, which is why it has been superseded by CORS (cross-origin resource sharing, available since 2009) in modern applications. Functionality The HTML <script> element is generally allowed to execute JavaScript code retrieved from foreign origins. Services replying with pure JSON data, however, were not able to share data from foreign origins before the adoption of CORS (Cross-ori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-origin Resource Sharing
Cross-origin resource sharing (CORS) is a mechanism to safely bypass the same-origin policy, that is, it allows a web page to access restricted resources from a server on a domain different than the domain that served the web page. A web page may freely embed cross-origin images, stylesheets, scripts, iframes, and videos. Certain "cross-domain" requests, notably Ajax requests, are forbidden by default by the same-origin security policy. CORS defines a way in which a browser and server can interact to determine whether it is safe to allow the cross-origin request. It allows for more freedom and functionality than purely same-origin requests, but is more secure than simply allowing all cross-origin requests. The specification for CORS is included as part of the WHATWG's Fetch Living Standard. This specification describes how CORS is currently implemented in browsers. An earlier specification was published as a W3C Recommendation. Technical overview For HTTP requests made from ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Same-origin Policy
In computing, the same-origin policy (SOP) is a concept in the web application security model. Under the policy, a web browser permits scripts contained in a first web page to access data in a second web page, but only if both web pages have the same ''origin''. An origin is defined as a combination of URI scheme, host name, and port number. This policy prevents a malicious script on one page from obtaining access to sensitive data on another web page through that page's Document Object Model (DOM). This mechanism bears a particular significance for modern web applications that extensively depend on HTTPS cookies to maintain authenticated user sessions, as servers act based on the HTTP cookie information to reveal sensitive information or perform state-changing actions. A strict separation between content provided by unrelated sites must be maintained on the client-side to prevent the loss of data confidentiality or integrity. The same-origin policy applies only to scripts. This m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XMLHttpRequest
XMLHttpRequest (XHR) is an API in the form of a JavaScript object whose methods transmit HTTP requests from a web browser to a web server. The methods allow a browser-based application to send requests to the server after page loading is complete, and receive information back. XMLHttpRequest is a component of Ajax programming. Prior to Ajax, hyperlinks and form submissions were the primary mechanisms for interacting with the server, often replacing the current page with another one. History The concept behind XMLHttpRequest was conceived in 2000 by the developers of Microsoft Outlook. The concept was then implemented within the Internet Explorer 5 browser (1999). However, the original syntax did not use the XMLHttpRequest identifier. Instead, the developers used the identifiers ActiveXObject("Msxml2.XMLHTTP") and ActiveXObject("Microsoft.XMLHTTP"). As of Internet Explorer 7 (2006), all browsers support the XMLHttpRequest identifier. The XMLHttpRequest identifier is now the ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Messaging
Web Messaging, or cross-document messaging, is an API introduced in the WHATWG HTML5 draft specification, allowing documents to communicate with one another across different origins, or source domains while rendered in a web browser. Prior to HTML5, web browsers disallowed cross-site scripting, to protect against security attacks. This practice barred communication between non-hostile pages as well, making document interaction of any kind difficult. Cross-document messaging allows scripts to interact across these boundaries, while providing a rudimentary level of security. Requirements and attributes Using the Messaging API's postMessage method, plain text messages can be sent from one domain to another, e.g. from a parent document to an IFRAME. This requires that the author first obtain the Window object of the receiving document. As a result, messages can be posted to the following: * other frames or iframes within the sender document's window * windows the sender document explic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-site Request Forgery
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF (sometimes pronounced ''sea-surf'') or XSRF, is a type of malicious exploit of a website or web application where unauthorized commands are submitted from a user that the web application trusts. There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript fetch or XMLHttpRequests, for example, can all work without the user's interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser. In a CSRF attack, an innocent end user is tricked by an attacker into submitting a web request that they did not intend. This may cause actions to be performed on the website that can include inadvertent client or server data leakage, change of session state, or manipulation of an end user's account. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Web Toolkit
Google Web Toolkit (GWT ), or GWT Web Toolkit, is an open-source software, open-source set of Programming tool, tools that allows web developers to create and maintain JavaScript Front and back ends, front-end applications in Java (programming language), Java. It is licensed under Apache License 2.0. GWT supports various web development tasks, such as remote procedure call, asynchronous remote procedure calls, history management, Internet bookmark, bookmarking, user interface, UI abstraction, I18N, internationalization, and cross-browser porting, portability. History GWT version 1.0 RC 1 was released on May 16, 2006. Google announced GWT at the JavaOne conference in 2006. In August 2010, Google acquired Instantiations, a company known for focusing on Eclipse Java developer tools, including GWT Designer, which is now bundled with Google Plugin for Eclipse. In 2011 with the introduction of the Dart (programming language), Dart programming language, Google stated that GWT wo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dojo Toolkit
Dojo Toolkit (stylized as dōjō toolkit) is an open-source modular JavaScript library (or more specifically JavaScript toolkit) designed to ease the rapid development of cross-platform, JavaScript/ Ajax-based applications and web sites. It was started by Alex Russell, Dylan Schiemann, David Schontzler, and others in 2004 and is dual-licensed under the modified BSD license or the Academic Free License (≥ 2.1). The Dojo Foundation was a non-profit organization created with the goal to promote the adoption of the toolkit. In 2016, the foundation merged with jQuery Foundation to become JS Foundation. Overview Dojo is a JavaScript framework targeting the many needs of large-scale client-side web development. For example, Dojo abstracts the differences among diverse browsers to provide APIs that will work on all of them (it can even run on the server under Node.js); it establishes a framework for defining modules of code and managing their interdependencies; it provides bui ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web 2
Web 2.0 (also known as participative (or participatory) web and social web) refers to websites that emphasize user-generated content, usability, ease of use, participatory culture, and interoperability (i.e., compatibility with other products, systems, and devices) for end users. The term was coined by Darcy DiNucci in 1999 and later popularized by Tim O'Reilly and Dale Dougherty at the first Web 2.0 Summit, Web 2.0 Conference in 2004. Although the term mimics the numbering of software versions, it does not denote a formal change in the nature of the World Wide Web, but merely describes a general change that occurred during this period as interactive websites proliferated and came to overshadow the older, more static websites of the original Web. A Web 2.0 website allows users to interact and collaborate through social media dialogue as creators of user-generated content in a virtual community. This contrasts the first generation of #Web 1.0, Web 1.0-era websites where people ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Michele Spagnuolo
Michele () is an Italian male given name, akin to the English male name Michael. Michele (usually pronounced ), is also an English female given name that is derived from the French Michèle. It is a variant spelling of the more common (and identically pronounced) name Michelle. Michele can also be a surname. The names are ultimately derived from the Hebrew מִיכָאֵל, through the Greek Μιχαήλ and the Latin Michael meaning "Who is like God?". Men with the given name Michele *Michele (singer) (born 1944), Italian pop singer * Michele Abruzzo (1904–1996), Italian actor *Michele Alboreto (1956–2001), Italian Grand Prix racing driver *Michele Amari (1806–1889), Italian politician and historian *Michele Andreolo (1912–1981), Italian footballer *Michele Bianchi (1883–1930), Italian journalist and revolutionary *Michele Bravi (born 1994), Italian singer *Michele Cachia (1760–1839), Maltese architect and military engineer *Michele Canini (born 1985), Italian foo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
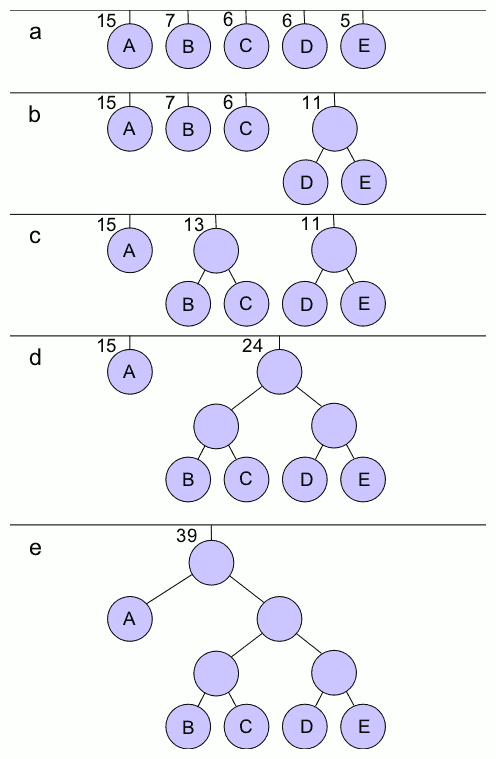
Huffman Coding
In computer science and information theory, a Huffman code is a particular type of optimal prefix code that is commonly used for lossless data compression. The process of finding or using such a code is Huffman coding, an algorithm developed by David A. Huffman while he was a Doctor of Science, Sc.D. student at Massachusetts Institute of Technology, MIT, and published in the 1952 paper "A Method for the Construction of Minimum-Redundancy Codes". The output from Huffman's algorithm can be viewed as a variable-length code table for encoding a source symbol (such as a character in a file). The algorithm derives this table from the estimated probability or frequency of occurrence (''weight'') for each possible value of the source symbol. As in other entropy encoding methods, more common symbols are generally represented using fewer bits than less common symbols. Huffman's method can be efficiently implemented, finding a code in time linear time, linear to the number of input weigh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |