|
Internet Real-name System In China
The Internet real-name system in China is a real-name system in which Internet service providers and Internet content providers (especially user-generated content sites) in the People's Republic of China are required to collect users' real names, ID numbers, and other information when providing services. Since the implementation of the real-name system on the Internet may lead to the infringement and narrowing of the constitutionally protected speech space of Internet users, it has attracted concerns from all sides and generated much controversy in Chinese society. Few other countries, such as South Korea, have implemented a real-name system on the Internet. History Proposal to ban anonymity in civil society The origin of the proposed ban on anonymity in mainland China is generally believed to be the proposal made by Li Xiguang, a journalism professor at Tsinghua University, in 2002, when he talked about journalism reform in the South, that "the Chinese National People's Congress sh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Real-name System
A real-name system is a system in which users can register an account on a blog, website or bulletin board system using their legal name. Users are required to provide identification credentials and their legal name. A public pseudonym can also be used, but the person's identity is available to legal authorities for use in criminal investigations. Real-name systems are employed on websites such as Facebook and Quora. History Real name systems originated from government regulations. Governments provided citizens with official surnames. This allowed them to track property ownership and inheritance, collect taxes, maintain court records, perform police work, conscript soldiers and control epidemics. Use in different countries Germany For privacy reasons, Germany’s 1997 § 13 VI Telemediengesetz (nowadays: § 19 II TTDSG) does not allow forcing people to use real-names if a real-name is not necessary for an internet service. On 27 January 2022, the highest court in civil mat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
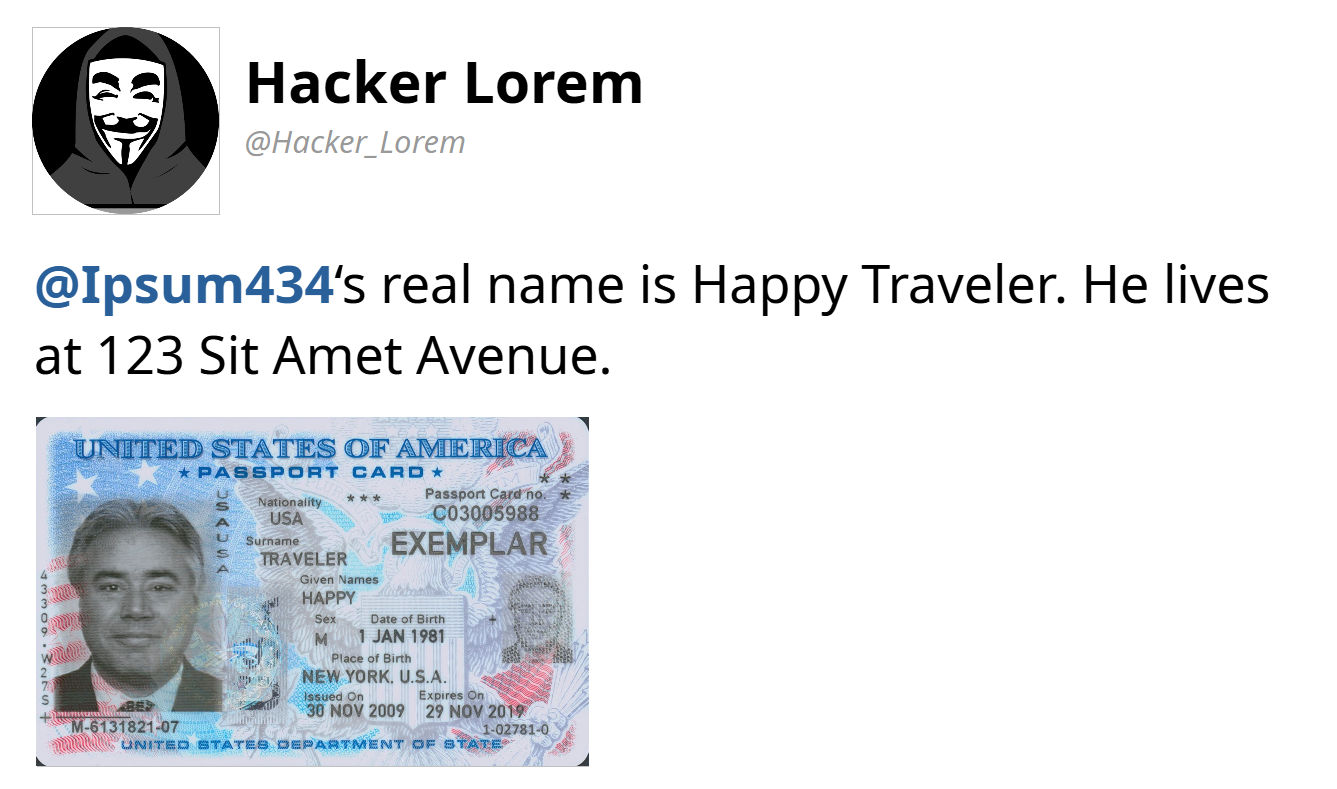
Data Breach
A data breach, also known as data leakage, is "the unauthorized exposure, disclosure, or loss of personal information". Attackers have a variety of motives, from financial gain to political activism, political repression, and espionage. There are several technical root causes of data breaches, including accidental or intentional disclosure of information by insiders, loss or theft of unencrypted devices, hacking into a system by exploiting software vulnerabilities, and social engineering attacks such as phishing where insiders are tricked into disclosing information. Although prevention efforts by the company holding the data can reduce the risk of data breach, it cannot bring it to zero. The first reported breach was in 2002 and the number occurring each year has grown since then. A large number of data breaches are never detected. If a breach is made known to the company holding the data, post-breach efforts commonly include containing the breach, investigating its scope ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Articles Containing Video Clips
Article often refers to: * Article (grammar), a grammatical element used to indicate definiteness or indefiniteness * Article (publishing) An article or piece is a written work published in a Publishing, print or electronic media, electronic medium, for the propagation of news, research results, academic analysis or debate. News A news article discusses current or recent news of e ..., a piece of nonfictional prose that is an independent part of a publication Article(s) may also refer to: Government and law * Elements of treaties of the European Union * Articles of association, the regulations governing a company, used in India, the UK and other countries; called articles of incorporation in the US * Articles of clerkship, the contract accepted to become an articled clerk * Articles of Confederation, the predecessor to the current United States Constitution * Article of impeachment, a formal document and charge used for impeachment in the United States * Article of ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet In China
China has been on the Internet intermittently since May 1989 and on a permanent basis since 20 April 1994, although with heavily Internet censorship in China, censored access. In 2008, China became the country with the largest population on the Internet and, , has remained so. 1.09 billion (77.5% of the country's total population) use internet in China. China's first foray into the global cyberspace was an email (not TCP/IP based and thus technically not internet) sent on 20 September 1987 to the Karlsruhe Institute of Technology, reading, "Across the Great Wall of China, Great Wall, towards the rest of the world" (). This later became a well-known phrase in China and , was displayed on the desktop login screen for Tencent QQ, QQ mail. History From 1995 to 2004, internet use in China was almost entirely in urban areas. By 2003, less than 0.2% of rural people had used the internet. In 2004, the Ministry of Industry and Information Technology began the Connecting Every Villag ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Human Rights Abuses In China
Humans (''Homo sapiens'') or modern humans are the most common and widespread species of primate, and the last surviving species of the genus ''Homo''. They are great apes characterized by their hairlessness, bipedalism, and high intelligence. Humans have large brains, enabling more advanced cognitive skills that facilitate successful adaptation to varied environments, development of sophisticated tools, and formation of complex social structures and civilizations. Humans are highly social, with individual humans tending to belong to a multi-layered network of distinct social groups — from families and peer groups to corporations and political states. As such, social interactions between humans have established a wide variety of values, social norms, languages, and traditions (collectively termed institutions), each of which bolsters human society. Humans are also highly curious: the desire to understand and influence phenomena has motivated humanity's development of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Human Rights In China
Human rights in the People's Republic of China are poor, as per reviews by international bodies, such as human rights treaty bodies and the United Nations Human Rights Council's Universal Periodic Review. The Chinese Communist Party (CCP), the government of the People's Republic of China (PRC), their supporters, and other proponents claim that existing policies and enforcement measures are sufficient to guard against human rights abuses. However, other countries (such as the United States and Canada), international non-governmental organizations (NGOs) including Human Rights in China and Amnesty International, and citizens, lawyers, and dissidents inside the country, state that the authorities in mainland China regularly sanction or organize such abuses. Independent NGOs such as Amnesty International and Human Rights Watch, as well as foreign governmental institutions such as the U.S. State Department, regularly present evidence of the PRC violating the freedoms of speech, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Doxxing
Doxing or doxxing is the act of publicly providing personally identifiable information about an individual or organization, usually via the Internet and without their consent. Historically, the term has been used to refer to both the aggregation of this information from public databases and social media websites (like Facebook), and the publication of previously private information obtained through criminal or otherwise fraudulent means (such as hacking and social engineering). The aggregation and provision of previously published material is generally legal, though it may be subject to laws concerning stalking and intimidation. Doxing may be carried out for reasons such as online shaming, extortion, and vigilante aid to law enforcement. Etymology " Doxing" is a neologism. It originates from a spelling alteration of the abbreviation "docs", for "documents", and refers to "compiling and releasing a dossier of personal information on someone". Essentially, doxing is revea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Human Flesh Search Engine
Human flesh search engine () is a Chinese term for the phenomenon of distributed researching using Internet media such as blogs and forums. Internet media, particularly dedicated websites and forums, serve as platforms for broadcasting requests and action plans related to human flesh search, as well as for sharing both online and offline search results. Human flesh search engine is similar to the concept of "doxing". Both human flesh search and doxing are typically viewed as identifying and exposing individuals for public humiliation, sometimes out of vigilantism, nationalist or patriotic sentiments, or the desire to circumvent Internet censorship in the People's Republic of China. However, more recent analyses have shown that it is also used for other purposes, such as exposing government corruption, identifying hit and run drivers, and exposing scientific fraud, as well as for more "entertainment"-related items such as identifying people seen in pictures. A categorization of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Real-name System
A real-name system is a system in which users can register an account on a blog, website or bulletin board system using their legal name. Users are required to provide identification credentials and their legal name. A public pseudonym can also be used, but the person's identity is available to legal authorities for use in criminal investigations. Real-name systems are employed on websites such as Facebook and Quora. History Real name systems originated from government regulations. Governments provided citizens with official surnames. This allowed them to track property ownership and inheritance, collect taxes, maintain court records, perform police work, conscript soldiers and control epidemics. Use in different countries Germany For privacy reasons, Germany’s 1997 § 13 VI Telemediengesetz (nowadays: § 19 II TTDSG) does not allow forcing people to use real-names if a real-name is not necessary for an internet service. On 27 January 2022, the highest court in civil mat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Censorship In China
The People's Republic of China (PRC) internet censorship, censors both the publishing and viewing of online material. Many controversial events are censored from news coverage, preventing many Chinese citizens from knowing about the actions of their government, and severely restricting Freedom of the press in China, freedom of the press. China's censorship includes the complete blockage of various websites, apps, and video games, inspiring the policy's nickname, the Great Firewall, Great Firewall of China, which List of websites blocked in mainland China#Table of high-ranking websites blocked in mainland China, blocks websites. Methods used to block websites and pages include DNS spoofing, blocking access to IP addresses, analyzing and filtering URLs, packet inspection, and TCP reset attack, resetting connections. The government blocks website content and monitors Internet access. As required by the government, major Internet platforms in China have established elaborate self-c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Identity Theft
Identity theft, identity piracy or identity infringement occurs when someone uses another's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term ''identity theft'' was coined in 1964. Since that time, the definition of identity theft has been legally defined throughout both the UK and the United States, U.S. as the theft of personally identifiable information. Identity theft deliberately uses someone else's personally identifiable information, identity as a method to gain financial advantages or obtain credit and other benefits. The person whose identity has been stolen may suffer adverse consequences, especially if they are falsely held responsible for the perpetrator's actions. Personally identifiable information generally includes a person's name, date of birth, social security number, driver's license number, bank account or credit card numbers, Personal identification ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |