|
Host Based Security System
Host Based Security System (HBSS) is the official name given to the United States Department of Defense (DOD) commercial off-the-shelf (COTS) suite of software applications used within the DOD to monitor, detect, and defend the DOD computer networks and systems. The Enterprise-wide Information Assurance and computer Network Defense Solutions Steering Group (ESSG) sponsored the acquisition of the HBSS System for use within the DOD Enterprise Network. HBSS is deployed on both the Non-Classified Internet Protocol Routed Network (NIPRNet) and Secret Internet Protocol Routed Network (SIPRNet) networks, with priority given to installing it on the NIPRNet. HBSS is based on McAfee, Inc's ePolicy Orchestrator (ePO) and other McAfee point product security applications such as Host Intrusion Prevention System (HIPS). History Seeing the need to supply a comprehensive, department-wide security suite of tools for DOD System Administrators, the ESSG started to gather requirements for t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States Department Of Defense
The United States Department of Defense (DoD, USDOD or DOD) is an executive branch department of the federal government charged with coordinating and supervising all agencies and functions of the government directly related to national security and the United States Armed Forces. The DoD is the largest employer in the world, with over 1.34 million active-duty service members (soldiers, marines, sailors, airmen, and guardians) as of June 2022. The DoD also maintains over 778,000 National Guard and reservists, and over 747,000 civilians bringing the total to over 2.87 million employees. Headquartered at the Pentagon in Arlington, Virginia, just outside Washington, D.C., the DoD's stated mission is to provide "the military forces needed to deter war and ensure our nation's security". The Department of Defense is headed by the secretary of defense, a cabinet-level head who reports directly to the president of the United States. Beneath the Department of Defense are t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asset Baseline Manager
In financial accounting, an asset is any resource owned or controlled by a business or an economic entity. It is anything (tangible or intangible) that can be used to produce positive economic value. Assets represent value of ownership that can be converted into cash (although cash itself is also considered an asset). The balance sheet of a firm records the monetaryThere are different methods of assessing the monetary value of the assets recorded on the Balance Sheet. In some cases, the ''Historical Cost'' is used; such that the value of the asset when it was bought in the past is used as the monetary value. In other instances, the present fair market value of the asset is used to determine the value shown on the balance sheet. value of the assets owned by that firm. It covers money and other valuables belonging to an individual or to a business. Assets can be grouped into two major classes: tangible assets and intangible assets. Tangible assets contain various subclasses, inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Defense Switched Network
The Defense Switched Network (DSN) is a primary information transfer network for the Defense Information Systems Network (DISN) of the United States Department of Defense. The DSN provides the worldwide non-secure voice, secure voice, data, facsimile, and video teleconferencing services for DOD Command and Control (C2) elements, their supporting activities engaged in logistics, personnel, engineering, and intelligence, as well as other Federal agencies. In 1982, the DSN was designated by the Office of the Secretary of Defense (OSD) and the Joint Chiefs of Staff (JCS) as the provider of long-distance communications service for the DOD. The DSN is designated as a primary system of communication during peacetime, periods of crisis, preattack, non-nuclear, and post-attack phases of war. The network assures nonblocking service for users with "flash" and "flash override" precedence capabilities. Key users include the National Command Authorities, Commanders of the Combatant Comma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Field Security Office
Field may refer to: Expanses of open ground * Field (agriculture), an area of land used for agricultural purposes * Airfield, an aerodrome that lacks the infrastructure of an airport * Battlefield * Lawn, an area of mowed grass * Meadow, a grassland that is either natural or allowed to grow unmowed and ungrazed * Playing field, used for sports or games Arts and media * In decorative art, the main area of a decorated zone, often contained within a border, often the background for motifs ** Field (heraldry), the background of a shield ** In flag terminology, the background of a flag * ''FIELD'' (magazine), a literary magazine published by Oberlin College in Oberlin, Ohio * ''Field'' (sculpture), by Anthony Gormley Organizations * Field department, the division of a political campaign tasked with organizing local volunteers and directly contacting voters * Field Enterprises, a defunct private holding company ** Field Communications, a division of Field Enterprises * Field Museum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
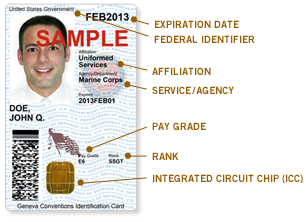
Common Access Card
The Common Access Card, also commonly referred to as the CAC is a smart card about the size of a credit card. It is the standard identification for Active Duty United States Defense personnel, to include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions (especially the Third Geneva Convention). In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption technologies: authentication, integrity and n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an aut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
INFOCON
INFOCON (short for information operations condition) is a threat level system in the United States similar to that of FPCON. It is a defense system based primarily on the status of information systems and is a method used by the military to defend against a computer network attack. Description There are five levels of INFOCON, which recently changed to more closely correlate to DEFCON levels. They are: *INFOCON 5 describes a situation where there is no apparent hostile activity against computer networks. Operational performance of all information systems is monitored, and password systems are used as a layer of protection. *INFOCON 4 describes an increased risk of attack. Increased monitoring of all network activities is mandated, and all Department of Defense end users must make sure their systems are secure. Internet usage may be restricted to government sites only, and backing up files to removable media is ideal. *INFOCON 3 describes when a risk has been identified. Security re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Government Off-the-shelf
Government off-the-shelf (GOTS) is a term for software and hardware government products that are ready to use and which were created and are owned by a government agency. Typically GOTS products are developed by the technical staff of the government agency for which it is created. It is sometimes developed by an external entity but with funding and specification from the agency. Because agencies can directly control all aspects of GOTS products, these are sometimes preferred for government purposes. GOTS software solutions can normally be shared among government agencies without additional cost. GOTS hardware solutions are typically provided at cost (i.e., R&D costs are not recouped). The government pays for all the development and maintenance costs of GOTS products. GOTS products run the risk of becoming obsolescent when the government cannot afford those costs. Since GOTS products are created by the government for government use, this limits the number of users, which is another ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
COBIT
COBIT (Control Objectives for Information and Related Technologies) is a framework created by ISACA for information technology (IT) management and IT governance. The framework is business focused and defines a set of generic processes for the management of IT, with each process defined together with process inputs and outputs, key process-activities, process objectives, performance measures and an elementary maturity model. Framework and components Business and IT goals are linked and measured to create responsibilities of business and IT teams. Five processes are identified: Evaluate, Direct and Monitor (EDM); Align, Plan and Organize (APO); Build, Acquire and Implement (BAI); Deliver, Service and Support (DSS); and Monitor, Evaluate and Assess (MEA).COBIT 2019 Framework: Introduction and Methodology from ISACA The COBIT framework ties in with COSO, ITIL, BiSL, ISO 27000, CMMI, TOGAF and PMBOK. The framework helps companies follow law, be more agile and earn more. B ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2005
File:2005 Events Collage V2.png, From top left, clockwise: Hurricane Katrina in the Gulf of Mexico; the Funeral of Pope John Paul II is held in Vatican City; "Me at the zoo", the first video ever to be uploaded to YouTube; Eris (dwarf planet), Eris was discovered in January 2005 by a Palomar Observatory–based team; Saddam Hussein sits before an Iraqi judge at a courthouse in Baghdad and is executed the 2006, next year; the shrine and resting place for Rafic Hariri in September; the Mars Reconnaissance Orbiter is launched from Cape Canaveral, Kennedy Space Center, designed to explore Mars; The Live 8 concert in the Tiergarten, Berlin., 300x300px, thumb rect 0 0 200 200 Hurricane Katrina rect 200 0 400 200 Funeral of Pope John Paul II rect 400 0 600 200 Me at the zoo rect 0 200 300 400 Live 8 rect 300 200 600 400 Eris (dwarf planet) rect 0 400 200 600 Mars Reconnaissance Orbiter rect 200 400 400 600 Rafic Hariri rect 400 400 600 600 Saddam Hussein 2005 was designated as the Int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Information Security Management Act Of 2002
The Federal Information Security Management Act of 2002 (FISMA, , ''et seq.'') is a United States federal law enacted in 2002 as Title III of the E-Government Act of 2002 (, ). The act recognized the importance of information security to the economic and national security interests of the United States. The act requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. FISMA has brought attention within the federal government to cybersecurity and explicitly emphasized a "risk-based policy for cost-effective security." FISMA requires agency program officials, chief information officers, and inspectors general (IGs) to conduct annual reviews of the agency's information security program and report the results to Office of Management and Budge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Health Insurance Portability And Accountability Act Of 1996
The Health Insurance Portability and Accountability Act of 1996 (HIPAA or the Kennedy– Kassebaum Act) is a United States Act of Congress enacted by the 104th United States Congress and signed into law by President Bill Clinton on August 21, 1996. It modernized the flow of healthcare information, stipulates how personally identifiable information maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft, and addressed some limitations on healthcare insurance coverage. It generally prohibits healthcare providers and healthcare businesses, called ''covered entities'', from disclosing protected information to anyone other than a patient and the patient's authorized representatives without their consent. With limited exceptions, it does not restrict patients from receiving information about themselves. It does not prohibit patients from voluntarily sharing their health information however they choose, nor does it require confidentiali ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |