|
High-availability Seamless Redundancy
High-availability Seamless Redundancy (HSR) is a network protocol for Ethernet that provides seamless failover against failure of any single network component. PRP and HSR are independent of the application-protocol and can be used by most Industrial Ethernet protocols in the IEC 61784 suite. HSR does not cover the failure of end nodes, but redundant nodes can be connected via HSR. HSR nodes have two ports and act as a bridge, which allows arranging them into a ring or meshed structure without dedicated switches. This is in contrast to the companion standard Parallel Redundancy Protocol (PRP), with which HSR shares the operating principle. PRP and HSR are standardized by the IEC 62439-3:2016. PRP and HSR are suited for applications that request high availability and short switchover time. For such applications, the recovery time of commonly used protocols such as the Rapid Spanning Tree Protocol (RSTP) is too long. It has been adopted for electrical substation automation in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Protocol
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses pre-determined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols are to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mesh Topology
A mesh network is a local area network topology in which the infrastructure nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate with one another to efficiently route data to and from clients. This lack of dependency on one node allows for every node to participate in the relay of information. Mesh networks dynamically self-organize and self-configure, which can reduce installation overhead. The ability to self-configure enables dynamic distribution of workloads, particularly in the event a few nodes should fail. This in turn contributes to fault-tolerance and reduced maintenance costs. Mesh topology may be contrasted with conventional star/tree local network topologies in which the bridges/switches are directly linked to only a small subset of other bridges/switches, and the links between these infrastructure neighbours are hierarchical. While star-and-tree topologi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Token Ring
Token Ring network IBM hermaphroditic connector with locking clip. Screen contacts are prominently visible, gold-plated signal contacts less so. Token Ring is a computer networking technology used to build local area networks. It was introduced by IBM in 1984, and standardized in 1989 as IEEE 802.5. It uses a special three-byte frame called a ''token'' that is passed around a logical ''ring'' of workstations or servers. This token passing is a channel access method providing fair access for all stations, and eliminating the collisions of contention-based access methods. Token Ring was a successful technology, particularly in corporate environments, but was gradually eclipsed by the later versions of Ethernet. History A wide range of different local area network technologies were developed in the early 1970s, of which one, the Cambridge Ring, had demonstrated the potential of a token passing ring topology, and many teams worldwide began working on their own implementat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links providing fault tolerance if an active link fails. As the name suggests, STP creates a spanning tree that characterizes the relationship of nodes within a network of connected layer-2 bridges, and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation. In 2001, the IEEE introduced Rapid Spanning Tree Protocol (RSTP) as 802.1w. RSTP provides significantly faster recovery in response to network changes or failures, introducing new convergence behaviors and bridge port roles to do this. RSTP was designed t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Resilient Packet Ring
Resilient Packet Ring (RPR), as defined by IEEE standard 802.17, is a protocol designed for the transport of data traffic over optical fiber ring networks. The standard began development in November 2000 and has undergone several amendments since its initial standard was completed in June 2004. The amended standards are 802.17a through 802.17d, the last of which was adopted in May 2011. It is designed to provide the resilience found in SONET and Synchronous Digital Hierarchy networks (50 ms protection) but, instead of setting up circuit oriented connections, provides a packet based transmission, in order to increase the efficiency of Ethernet and IP services. Technical details RPR works on a concept of dual counter rotating rings called ringlets. These ringlets are set up by creating RPR stations at nodes where traffic is supposed to drop, per flow (a flow is the ingress and egress of data traffic). RPR uses Media Access Control protocol (MAC) messages to direct the traff ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Redundancy (engineering)
In engineering, redundancy is the intentional duplication of critical components or functions of a system with the goal of increasing reliability of the system, usually in the form of a backup or fail-safe, or to improve actual system performance, such as in the case of GNSS receivers, or multi-threaded computer processing. In many safety-critical systems, such as fly-by-wire and hydraulic systems in aircraft, some parts of the control system may be triplicated, which is formally termed triple modular redundancy (TMR). An error in one component may then be out-voted by the other two. In a triply redundant system, the system has three sub components, all three of which must fail before the system fails. Since each one rarely fails, and the sub components are expected to fail independently, the probability of all three failing is calculated to be extraordinarily small; it is often outweighed by other risk factors, such as human error. Redundancy may also be known by the te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IEC/IEEE 61850-9-3
IEC/IEEE 61850-9-3 (Power Utility Profile) or PUP is an international standard for precise time distribution and clock synchronization in electrical grids with an accuracy of 1 μs. It supports precise time stamping of voltage and current measurement for differential protection, wide area monitoring and protection, busbar protection and event recording. Kirrmann, Hubert; Dickerson William IEC IEEE Precision Time Protocol', Pacworld, September 2016 It can be used to ensure deterministic operation of critical functions in the automation system. It belongs to the IEC 61850 standard suite for communication networks and systems for power utility automation. PTP Clocks In Substation 170203 HK.jpg, Hierarchy of PTP clocks in a substation IEC/IEEE 61850-9-3 is a profile (subset) of IEEE Std 1588 Precision Time Protocol (PTP) when clocks are singly attached. IEC/IEEE 61850-9-3 provides seamless fault tolerance by attaching clocks to duplicated networks paths and by support of simultaneousl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Precision Time Protocol Industry Profile
Industrial automation systems consisting of several distributed controllers need a precise synchronization for commands, events and process data. For instance, motors for newspaper printing are synchronized within some 5 microseconds to ensure that the color pixels in the different cylinders come within 0.1 mm at a paper speed of some 20 m/s. Similar requirements exist in high-power semiconductors (e.g. for converting between AC and DC grids) and in drive-by-wire vehicles (e.g. cars with no mechanical steering wheel). This synchronisation is provided by the communication network, in most cases Industrial Ethernet. Many ad-hoc synchronization schemes exist, so IEEE published a standard Precision Time Protocol IEEE 1588 or "PTP", which allows sub-microsecond synchronization of clocks. PTP is formulated generally, so concrete applications need a stricter profile. In particular, PTP does not specify how the clocks should operate when the network is duplicated for better resilience to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Store-and-forward
Store and forward is a telecommunications technique in which information is sent to an intermediate station where it is kept and sent at a later time to the final destination or to another intermediate station. The intermediate station, or node in a networking context, verifies the integrity of the message before forwarding it. In general, this technique is used in networks with intermittent connectivity, especially in the wilderness or environments requiring high mobility. It may also be preferable in situations when there are long delays in transmission and variable and high error rates, or if a direct, end-to-end connection is not available. Modern store and forward networking * Store and forward originates with delay-tolerant networks. No real-time services are available for these kinds of networks. * Logistical Networking is a scalable form of store and forward networking that exposes network-embedded buffers on intermediate nodes and allows flexible creation of services b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cut-through Switching
Rat running (also known as rodent running, cut-through driving, or dive-bombing) is the practice by motorists of using residential side streets or any unintended short cut such as a parking lot, delivery service lane or cemetery road instead of the intended main road in urban or suburban areas. Background Rat running is a tactic used to avoid heavy traffic and long delays at traffic signals or other obstacles, even where there are traffic calming measures to discourage its use or laws against taking certain routes. Rat runs are frequently taken by motorists familiar with the local geography. Rat running is controversial. When traffic is especially heavy on a highway or main road, rat-running vehicles may cause another traffic jam on the rat-run streets, along with accompanying problems such as collisions, pollution from exhaust, and road rage. It is sometimes opposed by residents on the affected streets, as they may regard it as a disturbance of their peace. Sometimes, it cau ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
LLDP
The Link Layer Discovery Protocol (LLDP) is a vendor-neutral link layer protocol used by network devices for advertising their identity, capabilities, and neighbors on a local area network based on IEEE 802 technology, principally wired Ethernet. The protocol is formally referred to by the IEEE as ''Station and Media Access Control Connectivity Discovery'' specified in IEEE 802.1AB with additional support in IEEE 802.3 section 6 clause 79. LLDP performs functions similar to several proprietary protocols, such as Cisco Discovery Protocol, Foundry Discovery Protocol, Nortel Discovery Protocol and Link Layer Topology Discovery. Information gathered Information gathered with LLDP can be stored in the device management information base (MIB) and queried with the Simple Network Management Protocol (SNMP) as specified in RFC 2922. The topology of an LLDP-enabled network can be discovered by ''crawling'' the hosts and querying this database. Information that may be retrieved ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
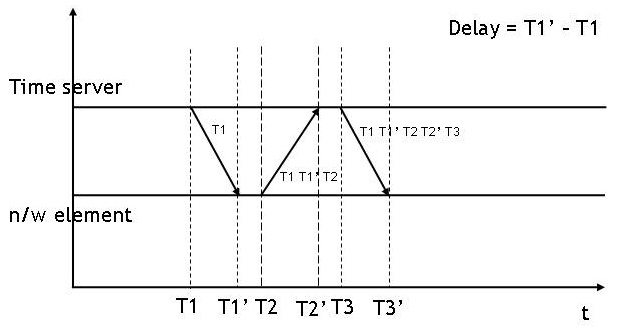
Precision Time Protocol
The Precision Time Protocol (PTP) is a protocol used to synchronize clocks throughout a computer network. On a local area network, it achieves clock accuracy in the sub-microsecond range, making it suitable for measurement and control systems. PTP is employed to synchronize financial transactions, mobile phone tower transmissions, sub-sea acoustic arrays, and networks that require precise timing but lack access to satellite navigation signals. The first version of PTP, IEEE 1588-2002, was published in 2002. IEEE 1588-2008, also known as PTP Version 2 is not backward compatible with the 2002 version. IEEE 1588-2019 was published in November 2019 and includes backward-compatible improvements to the 2008 publication. IEEE 1588-2008 includes a ''profile'' concept defining PTP operating parameters and options. Several profiles have been defined for applications including telecommunications, electric power distribution and audiovisual. is an adaptation of PTP for use with Audio V ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)