|
GigaTribe
GigaTribe is a peer-to-peer file-sharing network. Originally developed in France (2005), its American version was launched in November 2008. It offers free and paid versions; with the paid version users may restrict access to their encrypted files to a group of trusted friends. In 2010, a U.S. federal judge ruled that reasonable expectation of privacy does not extend to GigaTribe file-sharing. In the case, an informant gave police access to his GigaTribe friends' files, and child pornography was subsequently discovered. After some time, in 2015, GigaTribe announced collaborative storage with "GiGa.GG". They created a cloud service with a capability of sharing files with anyone by uploading them on the servers of the company. The amount of storage in free accounts was limited by 100 GB at first, but then, GiGa.GG decided to switch to a paid distribution model. Now, it is available to purchase an account with 100 GB, 1 TB or 2 TB (1.99 €, 5.99 € and 9.99 € respectively) with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Friend-to-friend
A friend-to-friend (or F2F) computer network is a type of peer-to-peer network in which users only make direct connections with people they know. Passwords or digital signatures can be used for authentication. Unlike other kinds of private P2P, users in a friend-to-friend network cannot find out who else is participating beyond their own circle of friends, so F2F networks can grow in size without compromising their users' anonymity. Retroshare, WASTE, GNUnet, Freenet and OneSwarm are examples of software that can be used to build F2F networks, though RetroShare is the only one of these configured for friend-to-friend operation by default. Many F2F networks support indirect anonymous or pseudonymous communication between users who do not know or trust one another. For example, a node in a friend-to-friend overlay can automatically forward a file (or a request for a file) anonymously between two friends, without telling either of them the other's name or IP address. These fr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peer-to-peer File Sharing
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program that searches for other connected computers on a P2P network to locate the desired content. The nodes (peers) of such networks are end-user computers and distribution servers (not required). The early days of file-sharing were done predominantly by client-server transfers from web pages, FTP and IRC before Napster popularised a Windows application that allowed users to both upload and download with a freemium style service. Record companies and artists called for its shutdown and FBI raids followed. Napster had been incredibly popular at its peak, spawning a grass-roots movement following from the mixtape scene of the 80's and left a significant gap in music availability with its followers. After much discussion on forums and in chat rooms ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Expectation Of Privacy
In United States constitutional law, reasonable expectation of privacy is a legal test which is crucial in defining the scope of the applicability of the privacy protections of the Fourth Amendment to the U.S. Constitution. It is related to, but is not the same as, a ''right to privacy'', a much broader concept which is found in many legal systems (see privacy law). Overall, reasonable expectations of privacy can be subjective or objective. Overview There are two types of reasonable expectations of privacy: * Subjective expectation of privacy: a certain individual's opinion that a certain location or situation is private which varies greatly from person to person * Objective expectation of privacy: legitimate and generally recognized by society and perhaps protected by law. Places where individuals expect privacy include residences, hotel rooms, or public places that have been provided by businesses or the public sector to ensure privacy, including public restrooms, private ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Child Pornography
Child pornography (also abbreviated as CP, also called child porn or kiddie porn, and child sexual abuse material, known by the acronym CSAM (underscoring that children can not be deemed willing participants under law)), is Eroticism, erotic material that depicts persons under the designated age of majority. The precise characteristics of what constitutes child pornography Legality of child pornography#Status by country, varies by criminal jurisdiction. Child pornography is often produced through online solicitation, coercion and Secret photography, covert photographing. In some cases, sexual abuse (such as forcible rape) is involved during production. Pornographic pictures of minors are also often produced by children and teenagers themselves without the involvement of an adult. Images and videos are collected and shared by online Sex offender, sex offenders. Laws regarding child pornography generally include sexual images involving prepubescents, pubescent, or post-pubescent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Service
Cloud computing is "a paradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand," according to ISO. Essential characteristics In 2011, the National Institute of Standards and Technology (NIST) identified five "essential characteristics" for cloud systems. Below are the exact definitions according to NIST: * On-demand self-service: "A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider." * Broad network access: "Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations)." * Resource pooling: " The provider's computing resources are pooled to serve multiple consumers using a multi-ten ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node (networking), nodes. In addition, a personal area network (PAN) is also in nature a type of Decentralized computing, decentralized peer-to-peer network typically between two devices. Peers make a portion of their resources, such as processing power, disk storage, or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model in which the consumption and supply of resources are divided. While P2P systems had previously been used in many application domains, the architecture was popularized by the Internet file sharing system Napster, originally released in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Private Network
Virtual private network (VPN) is a network architecture for virtually extending a private network (i.e. any computer network which is not the public Internet) across one or multiple other networks which are either untrusted (as they are not controlled by the entity aiming to implement the VPN) or need to be isolated (thus making the lower network invisible or not directly usable). A VPN can extend access to a private network to users who do not have direct access to it, such as an office network allowing secure access from off-site over the Internet. This is achieved by creating a link between computing devices and computer networks by the use of network tunneling protocols. It is possible to make a VPN secure to use on top of insecure communication medium (such as the public internet) by choosing a tunneling protocol that implements encryption. This kind of VPN implementation has the benefit of reduced costs and greater flexibility, with respect to dedicated communication li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Programming Interface
An application programming interface (API) is a connection between computers or between computer programs. It is a type of software Interface (computing), interface, offering a service to other pieces of software. A document or standard that describes how to build such a connection or interface is called an ''API specification''. A computer system that meets this standard is said to ''implement'' or ''expose'' an API. The term API may refer either to the specification or to the implementation. In contrast to a user interface, which connects a computer to a person, an application programming interface connects computers or pieces of software to each other. It is not intended to be used directly by a person (the end user) other than a computer programmer who is incorporating it into software. An API is often made up of different parts which act as tools or services that are available to the programmer. A program or a programmer that uses one of these parts is said to ''call'' that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hypertext Transfer Protocol
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, where hypertext documents include hyperlinks to other resources that the user can easily access, for example by a mouse click or by tapping the screen in a web browser. Development of HTTP was initiated by Tim Berners-Lee at CERN in 1989 and summarized in a simple document describing the behavior of a client and a server using the first HTTP version, named 0.9. That version was subsequently developed, eventually becoming the public 1.0. Development of early HTTP Requests for Comments (RFCs) started a few years later in a coordinated effort by the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C), with work later moving to the IETF. HTTP/1 was finalized and fully documented (as version 1.0) in 1996. It evolved ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
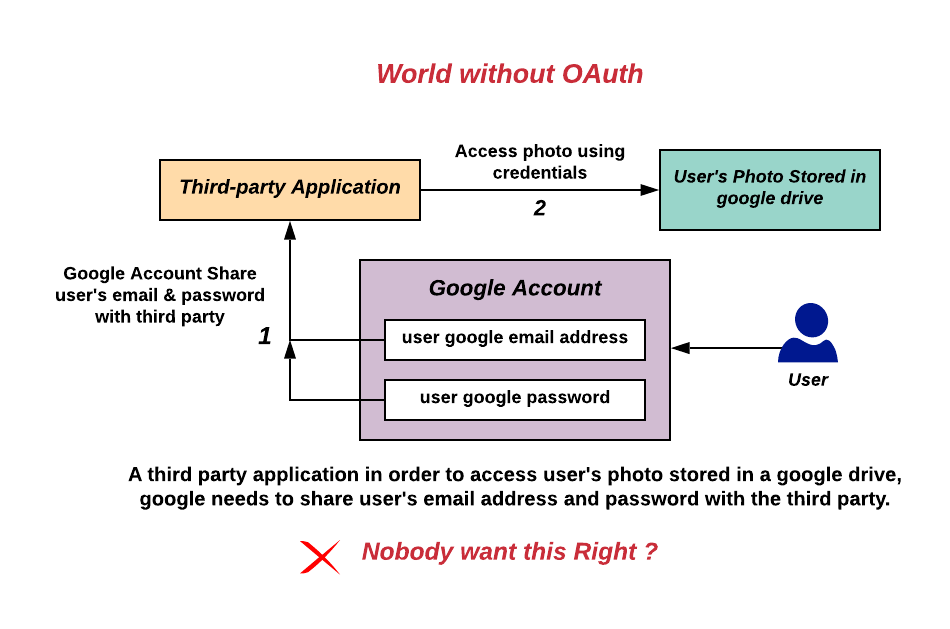
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peer-to-peer File Sharing
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program that searches for other connected computers on a P2P network to locate the desired content. The nodes (peers) of such networks are end-user computers and distribution servers (not required). The early days of file-sharing were done predominantly by client-server transfers from web pages, FTP and IRC before Napster popularised a Windows application that allowed users to both upload and download with a freemium style service. Record companies and artists called for its shutdown and FBI raids followed. Napster had been incredibly popular at its peak, spawning a grass-roots movement following from the mixtape scene of the 80's and left a significant gap in music availability with its followers. After much discussion on forums and in chat rooms ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Companies Of France
In computer technology and telecommunications, online indicates a state of connectivity, and offline indicates a disconnected state. In modern terminology, this usually refers to an Internet connection, but (especially when expressed as "on line" or "on the line") could refer to any piece of equipment or functional unit that is connected to a larger system. Being online means that the equipment or subsystem is connected, or that it is ready for use. "Online" has come to describe activities and concepts that take place on the Internet, such as online identity, online predator and online shop. A similar meaning is also given by the prefixes cyber and e, as in words ''cyberspace'', ''cybercrime'', ''email'', and ''e-commerce''. In contrast, "offline" can refer to either computing activities performed while disconnected from the Internet, or alternatives to Internet activities (such as shopping in brick-and-mortar stores). The term "offline" is sometimes used interchangeably with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |