|
Fifth Dimension Operations
The Fifth Dimension of Warfare complements the four classical dimensions: land, sea, air, and space. It was enunciated in 1995 as information operations. Core U.S. military doctrine This is part of core U.S. Military doctrine, that recognizes at least five dimensions, or 'domains of warfare' for which it is responsible: * Land * Sea * Air * Space * Information The origin of the concept of Fifth Dimension Operations was a criticism that the 'domain approach' reflected "a failure to think beyond the normal "four" dimensions of threats, both domestic and international". Expansion of the concept In more recent times, the concept of Fifth Dimensional Operations, as a concept under military operations, has taken a wider scope than its original information operations background, focusing on "the advanced space-time manipulating capabilities cyberspace offers". This development was begun as early as 1996, in regards to Advanced Battlespace and Cybermaneuver Concepts. Historical ana ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Operations
Information Operations is a category of direct and indirect support operations for the United States Military. By definition in Joint Publication 3-13, "IO are described as the integrated employment of electronic warfare (EW), computer network operations (CNO), psychological operations (PSYOP), military deception (MILDEC), and operations security (OPSEC), in concert with specified supporting and related capabilities, to influence, disrupt, corrupt or usurp adversarial human and automated decision making while protecting our own." Information Operations (IO) are actions taken to affect adversary information and information systems while defending one's own information and information systems. In the U.S. Navy, information operations are often supervised by a Navy Information Operations Command (NIOC), for example in the United States Tenth Fleet which has several NIOCs. Information Operations (IO) Electronic Warfare (EW) * Electronic warfare (EW) refers to any action i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Military Operations
A military operation is the coordinated military actions of a state, or a non-state actor, in response to a developing situation. These actions are designed as a military plan to resolve the situation in the state or actor's favor. Operations may be of a combat or non-combat nature and may be referred to by a code name for the purpose of national security. Military operations are often known for their more generally accepted common usage names than their actual operational objectives. Types of military operations Military operations can be classified by the scale and scope of force employment, and their impact on the wider conflict. The scope of military operations can be: * Theater: this describes an operation over a large, often continental, area of operation and represents a strategic national commitment to the conflict, such as Operation Barbarossa, with general goals that encompass areas of consideration outside the military, such as the economic and political impact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Battlespace
Battlespace or battle-space is a term used to signify a unified military strategy to integrate and combine armed forces for the military theatre of operations, including air, information, land, sea, cyber and outer space to achieve military goals. It includes the environment, factors, and conditions that must be understood to successfully apply combat power, protect the force, or complete the mission. This includes enemy and friendly armed forces, infrastructure, weather, terrain, and the electromagnetic spectrum within the operational areas and areas of interest. Concept From "battlefield" to "battle-space" Over the last 25 years, the understanding of the military operational environment has transformed from primarily a time and space-driven linear understanding (a "battlefield") to a multi-dimensional system of systems understanding (a battle-space). This system of systems understanding implies that managing the battle-space has become more complex, primari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command And Control
Command and control (abbr. C2) is a "set of organizational and technical attributes and processes ... hatemploys human, physical, and information resources to solve problems and accomplish missions" to achieve the goals of an organization or enterprise, according to a 2015 definition by military scientists Marius Vassiliou, David S. Alberts, and Jonathan R. Agre. The term often refers to a military system. Versions of the United States Army ''Field Manual 3-0'' circulated circa 1999 define C2 in a military organization as the exercise of authority and direction by a properly designated commanding officer over assigned and attached forces in the accomplishment of a mission. A 1988 NATO definition is that command and control is the exercise of authority and direction by a properly designated individual over assigned resources in the accomplishment of a common goal. An Australian Defence Force definition, similar to that of NATO, emphasises that C2 is the system empowering ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command And Influence
Command and influence is a component of Military C2 ('Command and control') and is a key aspect of Terrorist Tactics, Techniques, and Procedures. Definition Chris Flaherty in 2003 distinguished the concept of command and influence is a component of Military C2 ('command and control'), in the following terms: "Influence, is fundamental to effective Command where forces manoeuvre. Thus, recognition of "Influence" is an important element in any future warfighting concept. As an alternative to relying on Command and Control (C2) based effective Command there should be utilization of command and "influence" (CI) based effective Command. Role of influence in military theory Notionally, 'influence' is definable as the effect of one person or thing on another. In particular military information operations (IO) implicitly incorporates a variety of influence strategies, in order to shape the military and political spheres in conflict. Relevance of Arquilla and Ronfeldt work The work ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Swarming (military)
Military swarming is a battlefield tactic designed to maximize target saturation, and thereby overwhelm or saturate the defences of the principal target or objective. On the other-hand, defenders can overcome attempts at swarming, by launching counter-swarming measures that are designed to neutralize or otherwise repel such attacks. Military swarming is often encountered in asymmetric warfare where opposing forces are not of the same size, or capacity. In such situations, swarming involves the use of a decentralized force against an opponent, in a manner that emphasizes mobility, communication, unit autonomy and coordination or synchronization. Historically military forces have used the principles of swarming without really examining them explicitly, but there is now active research in consciously examining military doctrines that draw ideas from swarming. In nature and nonmilitary situations, there are other various forms of swarming. Biologically driven forms are often comple ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Battlespace
Battlespace or battle-space is a term used to signify a unified military strategy to integrate and combine armed forces for the military theatre of operations, including air, information, land, sea, cyber and outer space to achieve military goals. It includes the environment, factors, and conditions that must be understood to successfully apply combat power, protect the force, or complete the mission. This includes enemy and friendly armed forces, infrastructure, weather, terrain, and the electromagnetic spectrum within the operational areas and areas of interest. Concept From "battlefield" to "battle-space" Over the last 25 years, the understanding of the military operational environment has transformed from primarily a time and space-driven linear understanding (a "battlefield") to a multi-dimensional system of systems understanding (a battle-space). This system of systems understanding implies that managing the battle-space has become more complex, primari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberwarfare
Cyberwarfare is the use of cyber attacks against an enemy state, causing comparable harm to actual warfare and/or disrupting vital computer systems. Some intended outcomes could be espionage, sabotage, propaganda, manipulation or economic warfare. There is significant debate among experts regarding the definition of cyberwarfare, and even if such a thing exists. One view is that the term is a misnomer, since no cyber attacks to date could be described as war. An alternative view is that it is a suitable label for cyber attacks which cause physical damage to people and objects in the real world. Many countries including the United States, United Kingdom, Russia, China, Israel, Iran, and North Korea have active cyber capabilities for offensive and defensive operations. As states explore the use of cyber operations and combine capabilities, the likelihood of physical confrontation and violence playing out as a result of, or part of, a cyber operation is increased. However, meet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber-attack
A cyberattack is any offensive maneuver that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies or organisations and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon. Cyber attacks have increased with an alarming rate for the last few years A cyberattack may steal, alter, or destroy a specified target by hacking into a susceptible system. Cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations. Legal experts are seeking to limit the use of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Warfare
Information warfare (IW) (as different from cyber warfare that attacks computers, software, and command control systems) is a concept involving the battlespace use and management of information and communication technology (ICT) in pursuit of a competitive advantage over an opponent. Information warfare is the manipulation of information trusted by a target without the target's awareness so that the target will make decisions against their interest but in the interest of the one conducting information warfare. As a result, it is not clear when information warfare begins, ends, and how strong or destructive it is. Information warfare may involve the collection of tactical information, assurance(s) that one's information is valid, spreading of propaganda or disinformation to demoralize or manipulate the enemy and the public, undermining the quality of the opposing force's information and denial of information-collection opportunities to opposing forces. Information warfare is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Operations
Information Operations is a category of direct and indirect support operations for the United States Military. By definition in Joint Publication 3-13, "IO are described as the integrated employment of electronic warfare (EW), computer network operations (CNO), psychological operations (PSYOP), military deception (MILDEC), and operations security (OPSEC), in concert with specified supporting and related capabilities, to influence, disrupt, corrupt or usurp adversarial human and automated decision making while protecting our own." Information Operations (IO) are actions taken to affect adversary information and information systems while defending one's own information and information systems. In the U.S. Navy, information operations are often supervised by a Navy Information Operations Command (NIOC), for example in the United States Tenth Fleet which has several NIOCs. Information Operations (IO) Electronic Warfare (EW) * Electronic warfare (EW) refers to any action i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
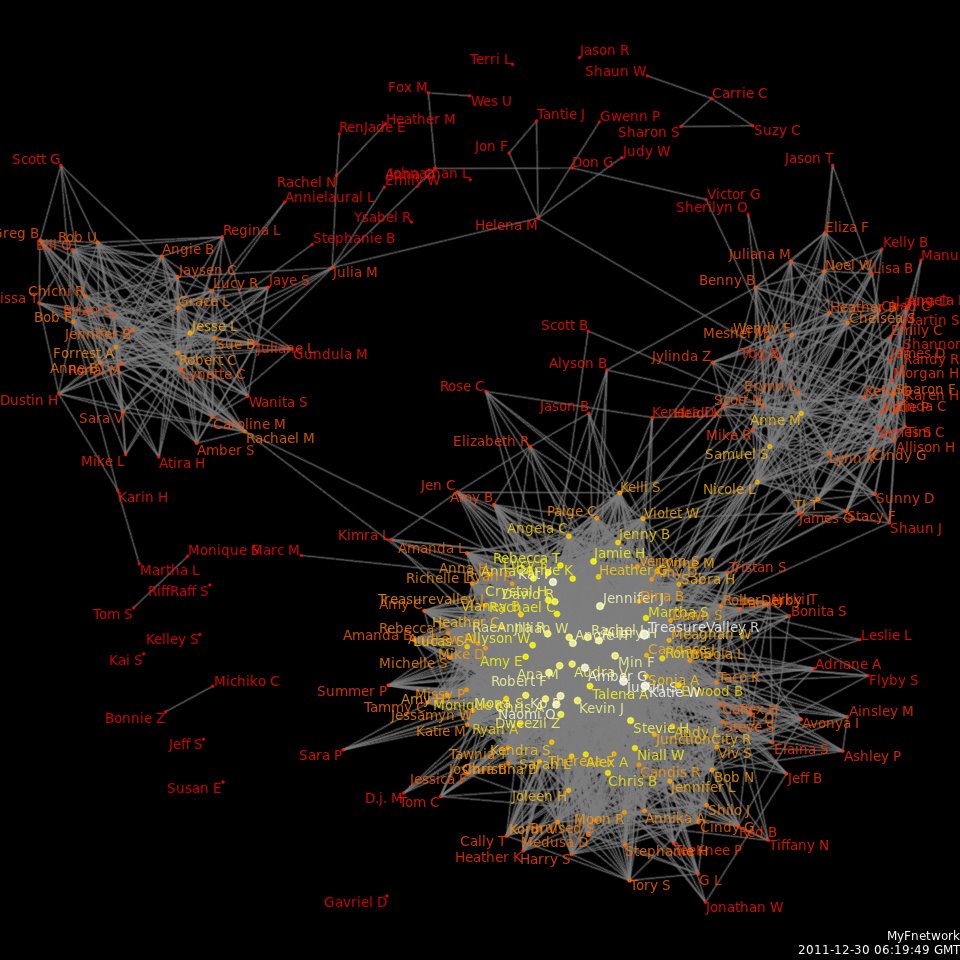
Social Network Analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) and the ''ties'', ''edges'', or ''links'' (relationships or interactions) that connect them. Examples of social structures commonly visualized through social network analysis include social media networks, memes spread, information circulation, friendship and acquaintance networks, business networks, knowledge networks, difficult working relationships, social networks, collaboration graphs, kinship, disease transmission, and sexual relationships. These networks are often visualized through '' sociograms'' in which nodes are represented as points and ties are represented as lines. These visualizations provide a means of qualitatively assessing networks by varying the visual representation of their nodes and edges to reflect attribute ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)