|
Economics Of Security
The economics of information security addresses the economic aspects of privacy and computer security. Economics of information security includes models of the strictly rational “homo economicus” as well as behavioral economics. Economics of securities addresses individual and organizational decisions and behaviors with respect to security and privacy as market decisions. Economics of security addresses a core question: why do agents choose technical risks when there exists technical solutions to mitigate security and privacy risks? Economics addresses not only this question, but also inform design decisions in security engineering. Emergence of economics of security National security is the canonical public good. The economic status of information security came to the intellectual fore around 2000. As is the case with innovations it arose simultaneously in multiple venues. In 2000, Ross Anderson wroteWhy Information Security is Hard Anderson explained that a significant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data or the unlawful use, Data breach, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g., electronic or physical, tangible (e.g., Document, paperwork), or intangible (e.g., knowledge). Information security's primary focus is the balanced protection of data confidentiality, data integrity, integrity, and data availability, availability (also known as the 'CIA' triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process. To stand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Price Discrimination
Price discrimination (differential pricing, equity pricing, preferential pricing, dual pricing, tiered pricing, and surveillance pricing) is a Microeconomics, microeconomic Pricing strategies, pricing strategy where identical or largely similar goods or services are sold at different Price, prices by the same provider to different buyers based on which Market segmentation, market segment they are perceived to be part of. Price discrimination is distinguished from product differentiation by the difference in production cost for the differently priced products involved in the latter strategy. Price discrimination essentially relies on the variation in customers' willingness to pay and in the Demand elasticity, elasticity of their demand. For price discrimination to succeed, a seller must have market power, such as a dominant market share, product uniqueness, sole pricing power, etc. Some prices under price discrimination may be lower than the price charged by a single-price monopoli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jean Camp
Linda Jean Camp is an American computer scientist whose research concerns information security, with a focus on human-centered design, autonomy, and safety. She has also made important contributions to risk communication, internet governance, and the economics of security. She is a professor of informatics in the Luddy School of Informatics, Computing, and Engineering at Indiana University Bloomington, where she directs the Center for Security and Privacy in Informatics, Computing, and Engineering. Education and career Camp earned a double bachelor's degree in mathematics and electrical engineering from the University of North Carolina in 1989, also working as a nuclear power engineer in the last year of her studies. She continued at the University of North Carolina for a master's degree in electrical engineering, supported as a Patricia Harris Fellow in the university's Optical Interconnects & Computer Generated Holography Laboratory. Next, she went to Carnegie Mellon University ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Insurance
Cyber insurance is a specialty insurance product that protects businesses from risks relating to information technology infrastructure and activities. Advantages Because the cyber insurance market in many countries is relatively small compared to other insurance products, its overall impact on emerging cyber threats is difficult to quantify. As the impact to people and businesses from cyber threats is also relatively broad when compared to the scope of protection provided by insurance products, insurance companies continue to develop their services. As well as directly improving security, cyber insurance is beneficial in the event of a large-scale security breach. Insurance provides a smooth funding mechanism for recovery from major losses, helping businesses to return to normal and reducing the need for government assistance. As a side benefit, many cyber-insurance policies require entities attempting to procure cyber insurance policies to participate in an IT security audit bef ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trusted System
In the security engineering subspecialty of computer science, a trusted system is one that is relied upon to a specified extent to enforce a specified security policy. This is equivalent to saying that a trusted system is one whose failure would break a security policy (if a policy exists that the system is trusted to enforce). The word "trust" is critical, as it does not carry the meaning that might be expected in everyday usage. A trusted system is one that the user feels safe to use, and trusts to perform tasks without secretly executing harmful or unauthorized programs; trusted computing refers to whether programs can trust the platform to be unmodified from the expected, and whether or not those programs are innocent or malicious or whether they execute tasks that are undesired by the user. A trusted system can also be seen as a level-based security system where protection is provided and handled according to different levels. This is commonly found in the military, where info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Security Assurance
Software security assurance is a process that helps design and implement software that protects the data and resources contained in and controlled by that software. Software is itself a resource and thus must be afforded appropriate security. What is software security assurance? Software Security Assurance (SSA) is the process of ensuring that software is designed to operate at a level of security that is consistent with the potential harm that could result from the loss, inaccuracy, alteration, unavailability, or misuse of the data and resources that it uses, controls, and protects. The software security assurance process begins by identifying and categorizing the information that is to be contained in, or used by, the software. The information should be categorized according to its sensitivity. For example, in the lowest category, the impact of a security violation is minimal (i.e. the impact on the software owner's mission, functions, or reputation is negligible). For a top c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker or security researcher is someone who explores methods for breaching or bypassing defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, sabotage, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. Longstanding controversy surrounds the meaning of the term "hacker". In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks, and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". The subculture that has evolved around hackers is often referred to as the "co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Engineering
Security engineering is the process of incorporating security controls into an information system so that the controls become an integral part of the system's operational capabilities. It is similar to other systems engineering activities in that its primary motivation is to support the delivery of engineering solutions that satisfy pre-defined functional and user requirements, but it has the added dimension of preventing misuse and malicious behavior. Those constraints and restrictions are often asserted as a security policy. In one form or another, security engineering has existed as an informal field of study for several centuries. For example, the fields of locksmithing and security printing have been around for many years. The concerns for modern security engineering and computer systems were first solidified in a RAND paper from 1967, "Security and Privacy in Computer Systems" by Willis H. Ware. This paper, later expanded in 1979, provided many of the fundamental information ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Defensive Programming
Defensive programming is a form of defensive design intended to develop programs that are capable of detecting potential security abnormalities and make predetermined responses. It ensures the continuing function of a piece of software under unforeseen circumstances. Defensive programming practices are often used where high availability, safety, or security is needed. Defensive programming is an approach to improve software and source code, in terms of: * General quality – reducing the number of software bugs and problems. * Making the source code comprehensible – the source code should be readable and understandable so it is approved in a code audit. * Making the software behave in a predictable manner despite unexpected inputs or user actions. Overly defensive programming, however, may safeguard against errors that will never be encountered, thus incurring run-time and maintenance costs. Secure programming Secure programming is the subset of defensive programming con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Insecurity
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and networks from threats that can lead to unauthorized information disclosure, theft or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societies they support. Security is particularly crucial for systems that govern large-scale sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
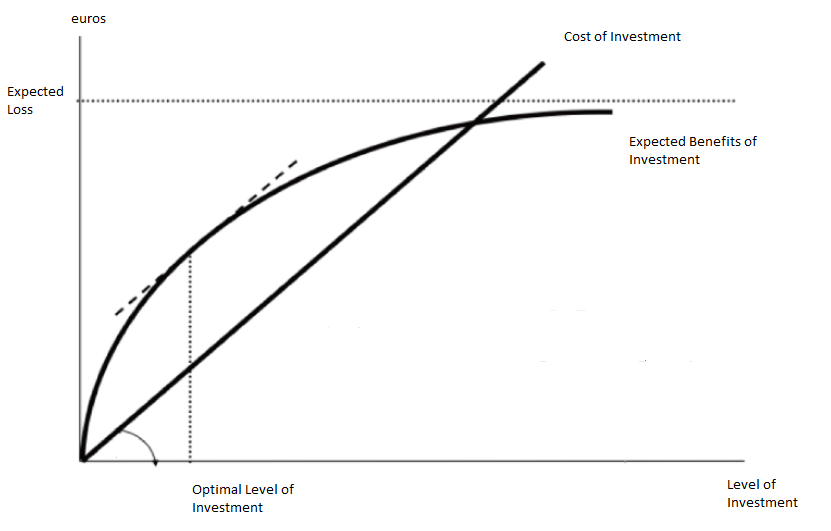
Gordon–Loeb Model
The Gordon–Loeb model is an economic model that analyzes the optimal level of investment in information security. The benefits of investing in cybersecurity stem from reducing the costs associated with cyber breaches. The Gordon-Loeb model provides a framework for determining how much to invest in cybersecurity, using a cost-benefit approach. The model includes the following key components: * Organizational data vulnerable to cyber-attacks, with vulnerability denoted by (), representing the probability of a breach occurring under current conditions. * The potential loss from a breach, represented by , which can be expressed in monetary terms. The expected loss is calculated as before additional cybersecurity investments. * Investment in cybersecurity, denoted as , reduces based on the effectiveness of the security measures, known as the security breach probability function. Gordon and Loeb demonstrated that the optimal level of security investment, , does not exceed 37% ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |