|
EMASS
The Enterprise Mission Assurance Support Service (eMASS) is a service-oriented computer application that supports Information Assurance (IA) program management and automates the Risk Management Framework (RMF) process. Overview eMASS is a service-oriented computer application that supports Information Assurance (IA) program management and automates the Risk Management Framework (RMF).NIST CSRC Risk Management Framework Overview (publicly accessible), https://csrc.nist.gov/projects/risk-management/rmf-overview The purpose of eMASS is to help the DoD to maintain IA situational awareness, manage risk, and comply with the Federal Information Security Management Act (FISMA 2002) and the Federal Information Security Modernization Act (FISMA 2014). eMASS is owned by the U.S. Department of Defense (i.e., the software is not proprietary). The program is sponsored by the Assistant Secretary of Defense for Networks and Information Integration (ASD (NII)) and is managed by the Defense Inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Assurance
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and data transmission, transmission of information. Information assurance includes protection of the data integrity, integrity, availability, authenticity, non-repudiation and confidentiality of user data. IA encompasses both digital protections and physical techniques. These methods apply to data in transit, both physical and electronic forms, as well as data at rest. IA is best thought of as a superset of information security (i.e. umbrella term), and as the business outcome of information risk management. Overview Information assurance (IA) is the process of processing, storing, and transmitting the right information to the right people at the right time. IA relates to the business level and Strategy, strategic risk management of information and related systems, rather than the creation and application of security controls. IA is used to benefit business ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Information Security Management Act
The Federal Information Security Management Act of 2002 (FISMA, , ''et seq.'') is a United States federal law enacted in 2002 as Title III of the E-Government Act of 2002 (, ). The act recognized the importance of information security to the economic and national security interests of the United States. The act requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. FISMA has brought attention within the federal government to cybersecurity and explicitly emphasized a "risk-based policy for cost-effective security." FISMA requires agency program officials, chief information officers, and inspectors general (IGs) to conduct annual reviews of the agency's information security program and report the results to Office of Management and Budge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Information Security Modernization Act
Federal or foederal (archaic) may refer to: Politics General *Federal monarchy, a federation of monarchies *Federation, or ''Federal state'' (federal system), a type of government characterized by both a central (federal) government and states or regional governments that are partially self-governing; a union of states *Federal republic, a federation which is a republic *Federalism, a political philosophy *Federalist, a political belief or member of a political grouping *Federalization, implementation of federalism Particular governments *Government of Argentina *Government of Australia *Federal government of Brazil *Government of Canada *Cabinet of Germany *Federal government of Iraq *Government of India *Federal government of Mexico *Federal government of Nigeria *Government of Pakistan *Government of the Philippines *Government of Russia *Government of South Africa *Federal government of the United States **United States federal law **United States federal courts *Federal gover ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
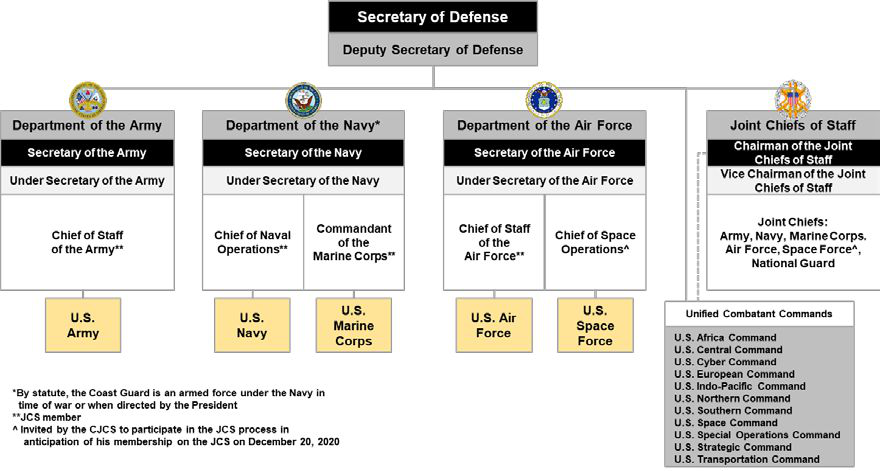
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Assistant Secretary Of Defense For Networks And Information Integration
The Assistant Secretary of Defense for Networks & Information Integration (ASD(NII)) was an appointed position that provided management and oversight of all DoD information technology, including national security systems. The ASD(NII) also served as the chief information officer (CIO) of the United States Department of Defense (DoD), a position distinct from the ASD and governed by the Clinger-Cohen Act. The ASD(NII)/DoD CIO was the principal staff assistant and advisor to the Secretary of Defense and Deputy Secretary of Defense on networks and network-centric policies and concepts; command, control and communications (C3); non-intelligence space matters; enterprise-wide integration of DoD information matters; Information Technology (IT), including National Security Systems (NSS); information resources management (IRM); spectrum management; network operations; information systems; information assurance (IA); positioning, navigation, and timing (PNT) policy, including airspace and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Defense Information Systems Agency
The Defense Information Systems Agency (DISA), known as the Defense Communications Agency (DCA) until 1991, is a United States Department of Defense (DoD) combat support agency. It is composed of military, federal civilians, and contractors. DISA provides information technology (IT) and communications support to the President, Vice President, Secretary of Defense, the Department of Defense, the combatant commands, and any individual or system contributing to the defense of the United States. History 1960s: The Defense Communications Agency DCA was established May 12, 1960, with the primary mission of operational control and management of the Defense Communications System (DCS). The initial headquarters for 34 DCA members was Wake Hall, one of a complex of three buildings (which included Midway Hall and Guam Hall) on the site where the parking lot of the Robert F. Kennedy Stadium in Washington, D.C., stands today. Navy Rear Admiral William D. Irvin became the first DCA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Global Information Grid
The Global Information Grid (GIG), now referred to as the Department of Defense Information Network (DODIN), refers to the entire network of information transmission and processing capabilities maintained by the United States Department of Defense. It is a worldwide network of information transmission, of associated processes, and of personnel serving to collect, process, safeguard, transmit, and manage this information. It is an all-encompassing communications project of the United States Department of Defense. The GIG makes this immediately available to military personnel, to those responsible for military politics, and for support personnel. It includes all infrastructure, bought or loaned, of communications, electronics, informatics (including software and databases), and security. It is the most visible manifestation of network-centric warfare. It is the combination of technology and human activity that enables warfighters to access information on demand. It is defined as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Computing
Cloud computing is "a paradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand," according to International Organization for Standardization, ISO. Essential characteristics In 2011, the National Institute of Standards and Technology (NIST) identified five "essential characteristics" for cloud systems. Below are the exact definitions according to NIST: * On-demand self-service: "A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider." * Broad network access: "Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations)." * Pooling (resource management), Resource pooling: " The provider' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |