 |
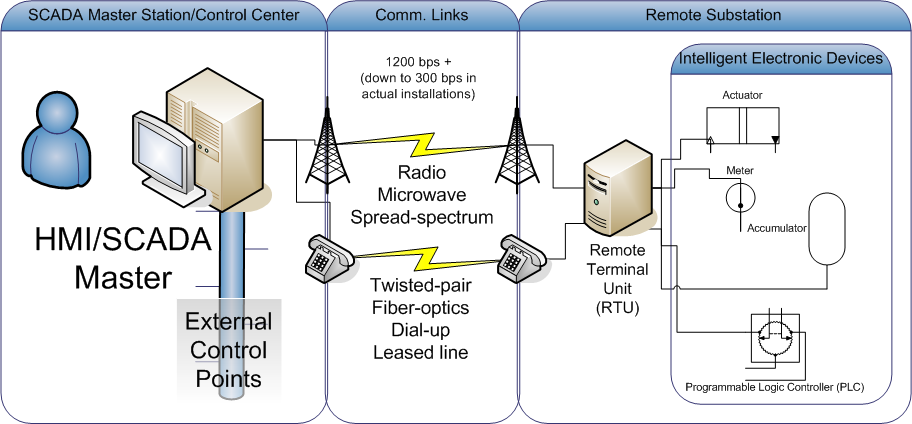
Distributed Network Protocol
Distributed Network Protocol 3 (DNP3) is a set of communications protocols used between components in process automation systems. Its main use is in utilities such as electric and water companies. Usage in other industries is not common. It was developed for communications between various types of data acquisition and control equipment. It plays a crucial role in SCADA systems, where it is used by SCADA Master Stations (a.k.a. Control Centers), Remote Terminal Units (RTUs), and Intelligent Electronic Devices (IEDs). It is primarily used for communications between a master station and RTUs or IEDs. ICCP, the Inter-Control Center Communications Protocol (a part of IEC 60870-6), is used for inter-master station communications. Competing standards include the older Modbus protocol and the newer IEC 61850 protocol. History While IEC 60870-5 was still under development and had not been standardized, there was a need to create a standard that would allow interoperability between ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Communications Protocol
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of a physical quantity. The protocol defines the rules, syntax, semantics (computer science), semantics, and synchronization of communication and possible Error detection and correction, error recovery methods. Protocols may be implemented by Computer hardware, hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses predetermined for that particular situation. The specified behavior is typically independent of how it is to be Implementation, implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
IEEE
The Institute of Electrical and Electronics Engineers (IEEE) is an American 501(c)(3) organization, 501(c)(3) public charity professional organization for electrical engineering, electronics engineering, and other related disciplines. The IEEE has a corporate office in New York City and an operations center in Piscataway, New Jersey. The IEEE was formed in 1963 as an amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers. History The IEEE traces its founding to 1884 and the American Institute of Electrical Engineers. In 1912, the rival Institute of Radio Engineers was formed. Although the AIEE was initially larger, the IRE attracted more students and was larger by the mid-1950s. The AIEE and IRE merged in 1963. The IEEE is headquartered in New York City, but most business is done at the IEEE Operations Center in Piscataway, New Jersey, opened in 1975. The Australian Section of the IEEE existed between 1972 and 1985, after which it s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Pre-shared Key
In cryptography, a pre-shared key (PSK) is a shared secret which was previously shared between the two parties using some secure channel before it needs to be used. Key To build a key from shared secret, the key derivation function is typically used. Such systems almost always use symmetric key cryptographic algorithms. The term PSK is used in Wi-Fi encryption such as Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), where the method is called WPA-PSK or WPA2-PSK, and also in the Extensible Authentication Protocol (EAP), where it is known as EAP-PSK. In all these cases, both the wireless access points (AP) and all clients ''share'' the same key. The characteristics of this secret or key are determined by the system which uses it; some system designs require that such keys be in a particular format. It can be a password, a passphrase, or a hexadecimal string. The secret is used by all systems involved in the cryptographic processes used to secure the traffic between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
IEEE Power & Energy Society
The IEEE Power & Energy Society (IEEE PES), formerly the IEEE Power Engineering Society, is the oldest society of the Institute of Electrical and Electronics Engineers (IEEE) focused on the scientific and engineering knowledge about electric power and electrical energy, energy. "... effective April 22, 2008 ... is the oldest IEEE Society, and will celebrate its 125th anniversary in 2009". PES Technical Council On 14 January 2016, the IEEE PES Governing Board approved the PES Technical Committee reorganization. This resulted in twenty coordinating and technical committees as follows: *Intelligent Grid and Emerging Technologies Coordinating Committee *Marine Systems Coordinating Committee *Wind and Solar Power Coordinating Committee Technical Committees *Analytics Methods for Power Systems Committee *Electric Machinery Committee *Energy Development and Power Generation Committee *Energy Storage and Stationary Battery Committee *Insulated Conductors Committee *Nuclear Power ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Endianness
file:Gullivers_travels.jpg, ''Gulliver's Travels'' by Jonathan Swift, the novel from which the term was coined In computing, endianness is the order in which bytes within a word (data type), word of digital data are transmitted over a data communication medium or Memory_address, addressed (by rising addresses) in computer memory, counting only byte Bit_numbering#Bit significance and indexing, significance compared to earliness. Endianness is primarily expressed as big-endian (BE) or little-endian (LE), terms introduced by Danny Cohen (computer scientist), Danny Cohen into computer science for data ordering in an Internet Experiment Note published in 1980. Also published at The adjective ''endian'' has its origin in the writings of 18th century Anglo-Irish writer Jonathan Swift. In the 1726 novel ''Gulliver's Travels'', he portrays the conflict between sects of Lilliputians divided into those breaking the shell of a boiled egg from the big end or from the little end. By analogy, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Data Reporting
Data reporting is the process of collecting and submitting data. The effective management of any organization relies on accurate data. Inaccurate data reporting can lead to poor decision-making based on erroneous evidence. Data reporting is different from data analysis which transforms data and information into insights. Data reporting is the previous step that translates raw data into information. When data is not reported, the problem is known as underreporting; the opposite problem leads to false positives. Data reporting can be difficult. Census bureaus may hire perhaps hundreds of thousands of workers to achieve the task of counting all of the residents of a country. Teachers use data from student assessments to determine grades; manufacturers rely on sales data from retailers to indicate which products should have increased production, and which should be curtailed or discontinued. See also *Data processing Data processing is the collection and manipulation of digita ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Cyclic Redundancy Check
A cyclic redundancy check (CRC) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data. Blocks of data entering these systems get a short ''check value'' attached, based on the remainder of a polynomial division of their contents. On retrieval, the calculation is repeated and, in the event the check values do not match, corrective action can be taken against data corruption. CRCs can be used for error correction (see bitfilters). CRCs are so called because the ''check'' (data verification) value is a ''redundancy'' (it expands the message without adding information) and the algorithm is based on ''cyclic'' codes. CRCs are popular because they are simple to implement in binary hardware, easy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels. Because the check value has a fixed length, the function that generates it is occasionally used as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Frame (networking)
A frame is a digital data transmission unit in computer networking and telecommunications. In packet switched systems, a frame is a simple container for a single network packet. In other telecommunications systems, a frame is a repeating structure supporting time-division multiplexing. A frame typically includes frame synchronization features consisting of a sequence of bits or symbols that indicate to the receiver the beginning and end of the payload data within the stream of symbols or bits it receives. If a receiver is connected to the system during frame transmission, it ignores the data until it detects a new frame synchronization sequence. Packet switching In the OSI model of computer networking, a frame is the protocol data unit at the data link layer. Frames are the result of the final layer of encapsulation before the data is transmitted over the physical layer. A frame is "the unit of transmission in a link layer protocol, and consists of a link layer header follo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Layer 7
The Open Systems Interconnection (OSI) model is a reference model developed by the International Organization for Standardization (ISO) that "provides a common basis for the coordination of standards development for the purpose of systems interconnection." In the OSI reference model, the components of a communication system are distinguished in seven abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. The model describes communications from the physical implementation of transmitting bits across a transmission medium to the highest-level representation of data of a distributed application. Each layer has well-defined functions and semantics and serves a class of functionality to the layer above it and is served by the layer below it. Established, well-known communication protocols are decomposed in software development into the model's hierarchy of function calls. The Internet protocol suite as defined in and is a model of net ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
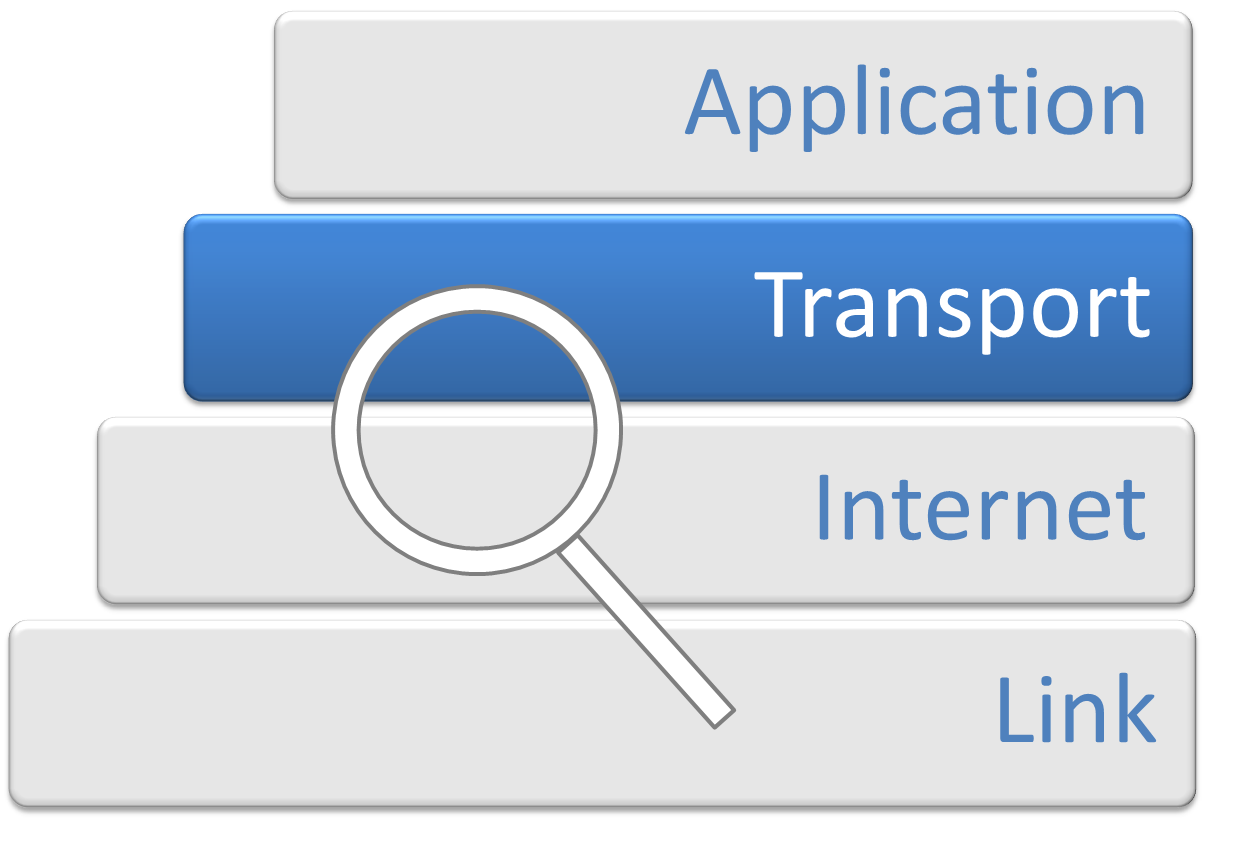 |
Layer 4
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the conne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Layer 2
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect and possibly correct errors that can occur in the physical layer. The data link layer is concerned with local delivery of frames between nodes on the same level of the network. Data-link frames, as these protocol data units are called, do not cross the boundaries of a local area network. Inter-network routing and global addressing are higher-layer functions, allowing data-link protocols to focus on local delivery, addressing, and media arbitration. In this way, the data link layer is analogous to a neighborhood traffic cop; it endeavors to arbitrate between parties contending for access to a medium, without con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
OSI Model
The Open Systems Interconnection (OSI) model is a reference model developed by the International Organization for Standardization (ISO) that "provides a common basis for the coordination of standards development for the purpose of systems interconnection." In the OSI reference model, the components of a communication system are distinguished in seven abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. The model describes communications from the physical implementation of transmitting bits across a transmission medium to the highest-level representation of data of a distributed application. Each layer has well-defined functions and semantics and serves a class of functionality to the layer above it and is served by the layer below it. Established, well-known communication protocols are decomposed in software development into the model's hierarchy of function calls. The Internet protocol suite as defined in and is a model of net ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |